- What is log analysis?
- How to analyze log files?
- Why should businesses choose a log analyzer tool?
- What are the key features of a log analysis tool?
- Best practices to make the most out of your log analysis tool
What is log analysis?
Log analysis (or log file analysis) is the process of examining log data generated across your network. Log data gets generated from various sources including perimeter devices, workstations, servers, applications, and other hardware and software components. Collecting them in a central location and analyzing them provides insights for understanding network operations, troubleshooting issues, and maintaining network security.
How to analyze log files?
Performing log analysis can be done in two ways—manually sifting through log data or using a log analyzer tool.
Manual log analysis
Manual log analysis involves a person or team physically reviewing the log files. This can be a time-consuming process due to the volume and complexity of log data. The manual approach requires a high level of expertise and understanding of the systems generating the logs along with knowledge of the types of events and anomalies to look out for.
Automatic analysis using log analyzer tools
Log analyzer tools are used to streamline and automate the entire process of handling your system's log data. These tools can help to filter, aggregate, visualize, and manage every aspect of your log data operations from a centralized location and provide powerful features like the correlation engine, advanced analytics, data visualization, and automated alerts. They provide invaluable insights into network security to allow you to respond swiftly to any potential issues.
Given the large volume of logs often generated by systems, log analysis is usually facilitated by log analysis tools in an organizational network.
Why should businesses choose a log analyzer tool?
Enhanced security
By employing real-time monitoring, correlating events, and performing comprehensive log analysis, network security can be significantly improved. This approach allows for the swift detection of potential threats and unusual activities like multiple failed login attempts, unusual user access patterns, or irregular network activities. Timely detection and remediation of issues like these can prevent unauthorized access, protect confidential data, and enhance the overall security of an organization.
Effective attack mitigation
In the event of a security incident, a log analysis tool can provide real-time alerts and detailed insights that enable swift and effective attack mitigation. It can pinpoint the source and extent of an attack and help security teams understand the attack vector, affected systems, and potential vulnerabilities. This allows teams to respond rapidly, minimizing the duration and impact of the attack, mitigating any attack effectively.
Regulatory compliance
Businesses are subject to regulatory compliance mandates that require them to maintain and review log files. For example, IT regulations like HIPAA for healthcare, the PCI DSS for the payment card industry, and the GDPR for data protection for consumers require detailed records of activities for auditing purposes. A log analysis tool can automate this process and generate reports that demonstrate compliance and maintain a record of all activities for audits.
Cost savings
While there's a cost associated with implementing a log analysis tool, the return on investment can be substantial. By automating the log management processes, these tools save a significant amount of time and resources that would otherwise be spent on manual log management. Additionally, by protecting their network from cyberattacks, organizations can save themselves the much larger costs associated with data breaches.
Scalability
Log analysis tools are capable of efficiently handling and analyzing large volumes of data from a wide range of sources, offering flexible storage and processing options. This means that as your organization expands, the log analysis tool can scale up to meet increased data requirements and eliminate any disruption in analyzing log data.
What are the key features of a log analysis tool?
Key capabilities:
Log aggregation

A log analysis tool effectively gathers logs from various sources such as servers, databases, applications, network devices, security systems, and cloud services. The tool can collect logs in real-time or on a predefined schedule. Once the logs are collected, the tool aggregates the data, centralizes it to one location, and provides a comprehensive view of the network activities.
Learn more about log collectionLog normalization
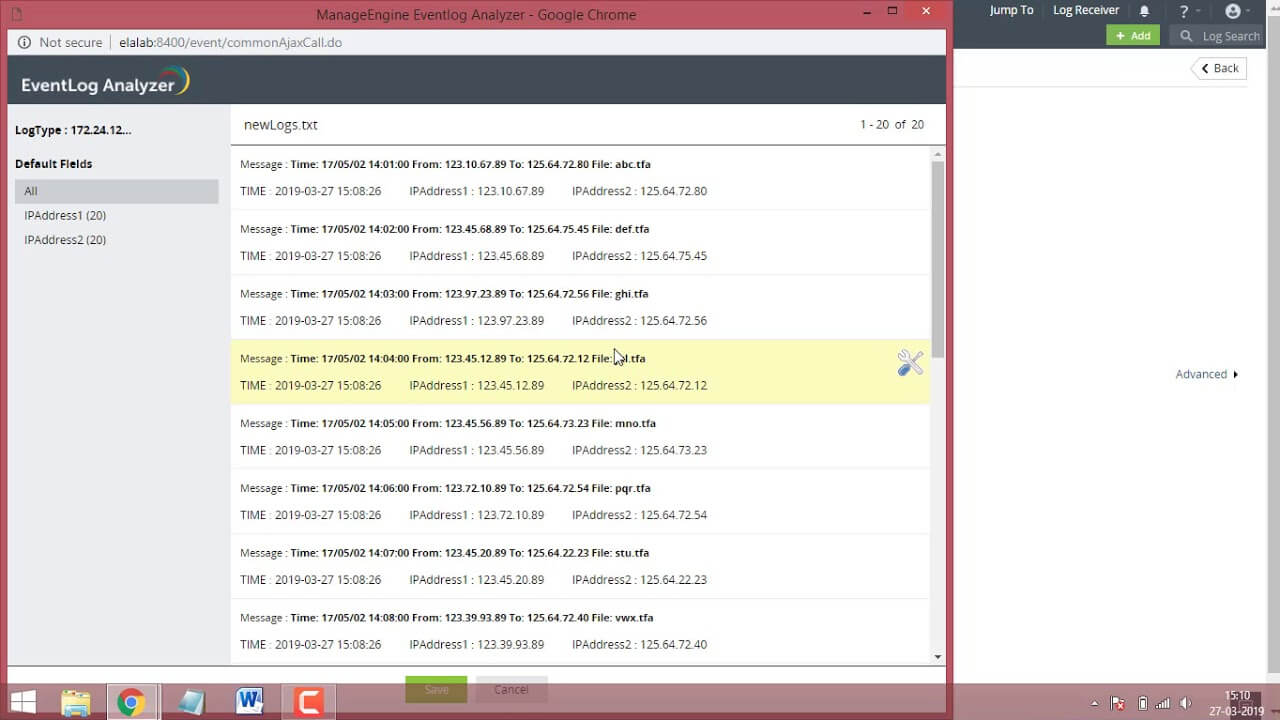
Considering the varied nature of log sources, a log analysis tool normalizes the data into a uniform format. It parses logs to extract key details like the timestamp, event type, source IP, and organizes this information for precise and efficient analysis. An efficient log analysis solution also comes with a custom log parser to create new fields to extract even more information from logs.
Learn more about log parsing and normalizationLog analysis
Once the log data is standardized and centralized, the tool conducts a detailed analysis involving:
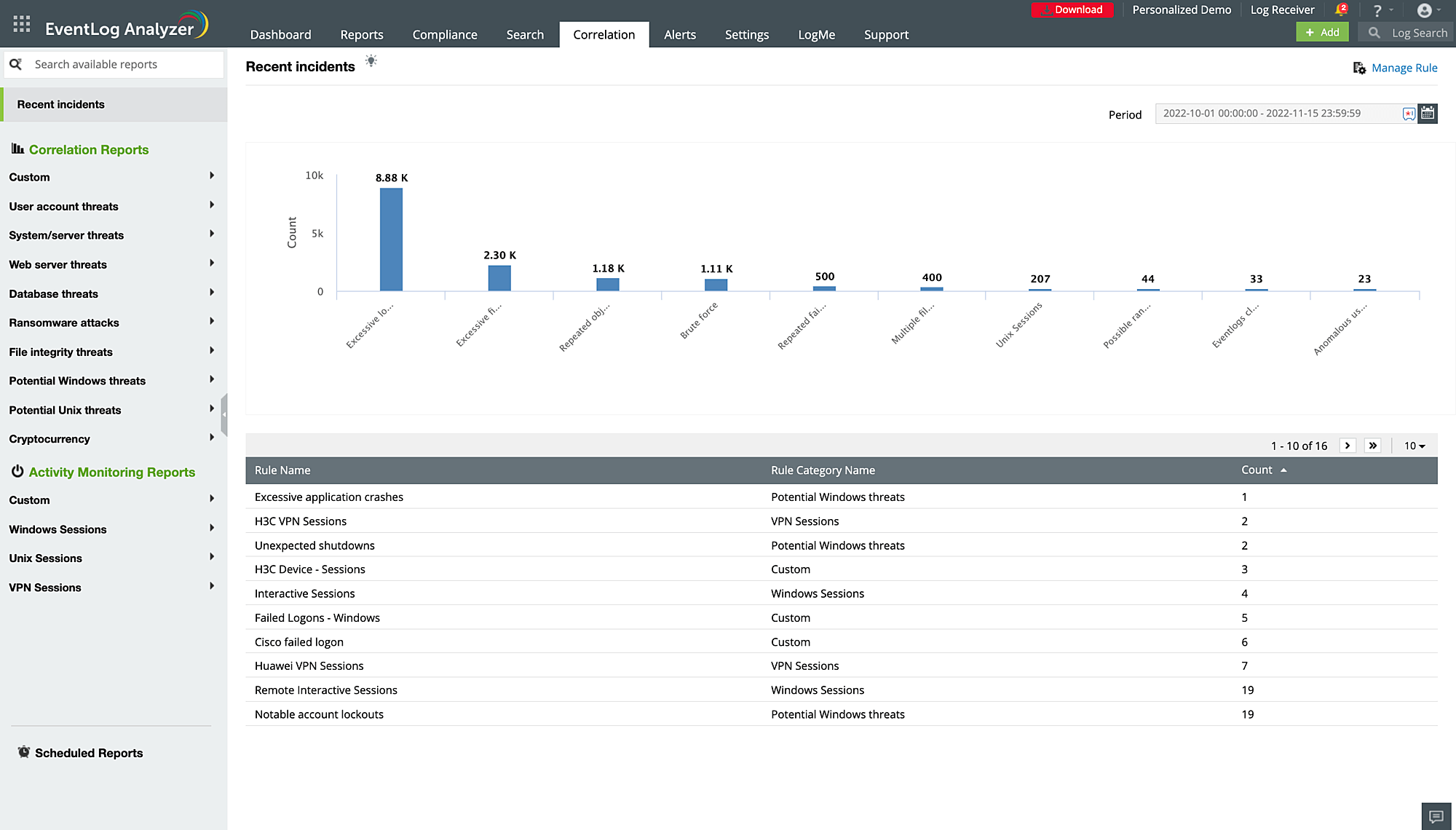
- Pattern recognition analysis: The tool identifies recurring patterns or trends over time, such as regular system activities, usage patterns, and security event trends.
- Anomaly detection: It compares the current log entries with established patterns to spot anomalies or unusual activities that could signal known security threats.
- Event log correlation: It correlates logs from multiple sources to detect complex patterns, anomalies, and potential security threats.
Incident response and management
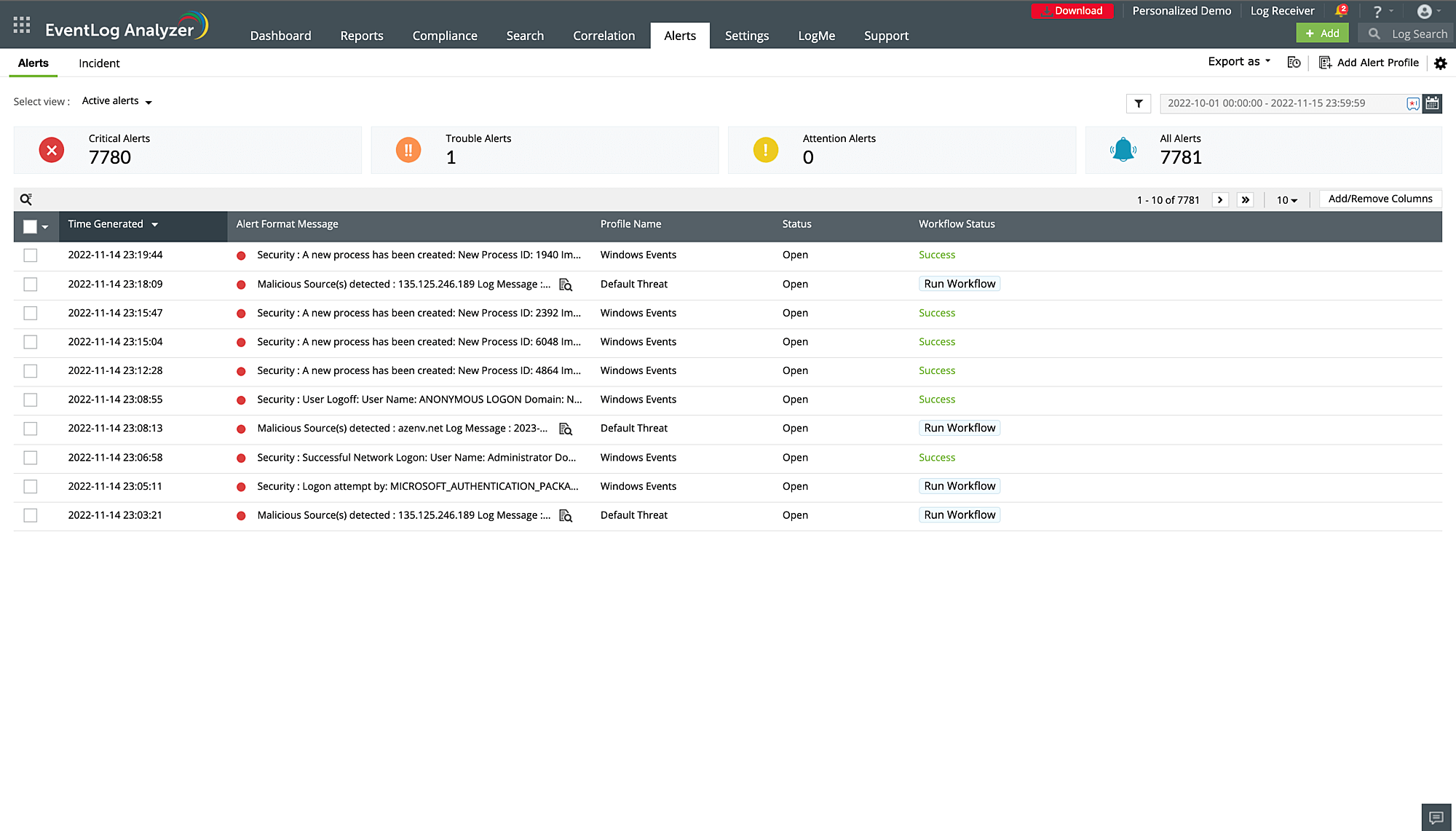
When a significant security event is detected, a log analyzer tool plays a crucial role in incident response and management by ensuring that potential security threats are addressed promptly and efficiently. The process involves several key steps:
- Threat detection: The first step in the process is the identification of a potential security threat. The log analyzer tool monitors log data and has access to updated threat data in the cybersecurity landscape, enabling it to quickly detect anomalies or unusual activities that may indicate a security threat.
- Alerting: Upon detection of a potential threat, the tool generates an alert. This alert is sent to the appropriate teams to ensure that they are immediately aware of the potential issue and can begin to address it.
- Predefined workflows: In addition to alerting the relevant teams, a log analyzer tool can also initiate predefined workflows in response to the detected threat. These workflows represent a series of steps or actions that are automatically executed to contain the situation as the alerted teams looks into the issue.
This structured approach helps in minimizing the impact of any security incidents. It also enables the organization to maintain a high level of security, even in the face of unexpected or complex threats.
Learn more about incident response and management hereReporting and visualization

Once log analysis is complete, the tool provides detailed reports with data visualization features to convert complex log data into easy-to-understand graphical representations to help you understand network activities, anomalies, and breach patterns.
Learn more about log visualization hereLog retention and archiving

Following the analysis, logs need to be securely stored for future reference and to comply with regulatory standards. A log analyzer tool manages this retention process by storing the logs for the required duration, archiving them in a secure manner, and keeping them readily accessible when needed. Some tools also offer features to manage archived logs efficiently, such as log compression, advanced search options, and more.
Learn more about log retention and archiving hereBest practices to make the most out of your log analysis tool
Define your objectives
Before implementing a log analyzer tool, it's crucial to define what you want to achieve with it. Whether it's enhancing network security, meeting compliance requirements, or improving system performance, having clear objectives will guide your implementation and usage.
Centralize log management
Implement a centralized log management approach, aggregating logs from all sources into a single, unified platform. This simplifies log analysis, provides a holistic view of your environment, and facilitates cross-platform correlation and comprehensive analysis.
Prioritize log sources
Identify systems, applications, or devices that are most crucial for your objectives, and prioritize their logs for analysis. This can help you focus on the most significant data and reduce noise.
Automate where possible
Use automation capabilities offered by an effective log analyzer tool. This could include automated log collection, scheduled reporting, real-time alerts, or automated responses to specific events. Automation can significantly enhance the efficiency of your log analysis process.
Implement real-time monitoring
Real-time log monitoring can help in identifying and addressing suspicious events promptly. This will drive your attention to the event as and when it happens, mitigating a full-blown attack.
Keep compliance in mind
If your organization is subject to regulatory standards, ensure your log analyzer tool supports the necessary compliance features. This may include secure log storage, log retention for specified periods, generation of compliance reports, and triggering alerts on compliance violations.
Review and adjust
Regularly review the performance and effectiveness of your log analyzer tool. Adjust configurations as needed, update alert criteria, and ensure that the tool continues to meet your evolving needs. Regular audits of the tool can also help identify any areas for improvement.