The IT industry has seen an unshakable surge in malware attacks. According to a SonicWall cyber threat report, approximately 2.8 billion malware attacks were identified in 2022. Roughly 30% of these malware attacks were carried out through emails with malicious links and attachments. One such malware—Dark Crystal, a.k.a DCRat—shook Ukraine on June 10, 2022. It is a remote access Trojan (RAT) that has acquired recurring updates and new modules since 2018. The malware, DCRat, has its own integrated development environment (IDE), which enables remote access and control over an infected device.
In this blog we will cover:
A remote access Trojan (RAT) is a malware program that helps in opening a backdoor on a compromised system. RATs are considered to be a particularly perilous Trojan because they excavate the opportunities for administrative control of the compromised systems. RATs can be established as a malicious payload using exploit toolkits such as Metasploit.
Once a user installs a RAT, it will connect with a hacker-controlled command-and-control (C&C) server. An open TCP port on the target device is compromised to achieve this connection. Once the attacker compromises the host system, they use a backdoor to control the host or they may disseminate the RATs to other vulnerable devices and establish a botnet.
This rip-roaring Trojan is found to be developed and nurtured by a solitary person representing themselves by the pseudonyms "boldenis44" and "crystalcoder". These were chiefly sold in the Russian cybercrime forums. DCRat is found to be one of the cheapest RATs available for purchase, priced at 500 RUB for a two-month subscription. Thus, unsurprisingly, these RATs are celebrated by the professional threat actors for its pricing and efficiency.
In June 2022, according to Ukraine's Computer Emergency Response Team (CERT-UA) report, Ukrainian utility and telecommunication companies were infected with DCRat through pirated software and phishing campaigns leveraging real stolen email accounts of the Ukrainian govt (.gov.ua) and well-spoofed knock-off accounts.
In the morning of June 10th, 2022, Ukraine's media outlets were flooded with mails from unknown accounts with malicious documents. These documents were named as “СПИСОК_посилань_на_інтерактивні_карти.docx” (translated to English as “LIST_of_links_interactive_maps.docx”) and contained malicious links. When this document was opened, it began exploiting a zero day vulnerability in the Microsoft support diagnostic tool (MSDT), CVE-2022-30190 (Follina). Mysterious remote files were downloaded and executed on the compromised machine as a result.These files perform various functions such as stealing sensitive information, executing remote command, and importing additional malware. Ultimately, the malicious code that was employed was not able to be identified as the file was not available at the time of execution.
The flowchart below represents the working of a spear phishing attack.
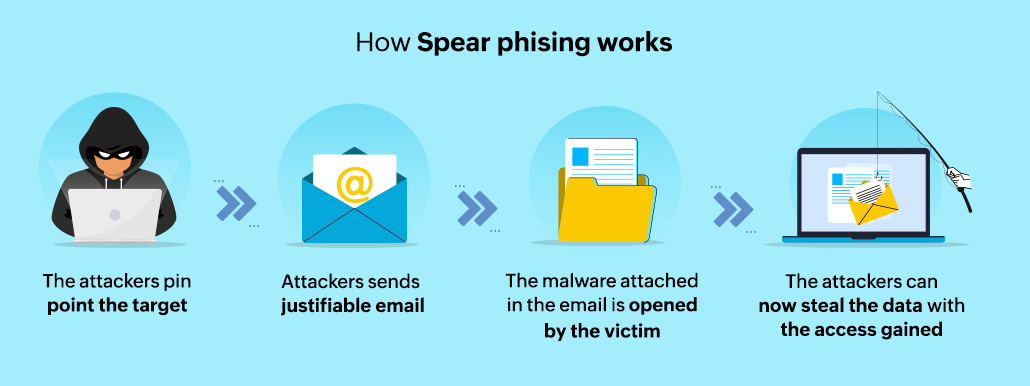 Figure 1: Spear Phishing attack
Figure 1: Spear Phishing attack
The DCRats generally follow a series of devious stratagem which include malspam, phishing, spear-phishing, pirated commercial software such as rouge updaters, and compromised anti-virus software such as Microsoft Defender to ultimately fetch and execute DCRat’s .NET payload on the victim’s computer.
The ubiquitous distribution method relies upon spam campaigns, where thousands of scam emails are sent. A malevolent Microsoft office document attachment is sent to the potential victims. This document will contain a macro code that will drop and execute a batch script named "c:\user\public\new.bat". Once a victim opens the document, the script is executed in PowerShell to download the second phase payload that is responsible for downloading and executing the actual DCRat malware.
DCRat utilizes a modular architecture that integrates a plugin framework, allowing affiliates to create their own client plugins. These plugins can be easily downloaded and utilized by the subscribers (attackers).
The design of DCRat malware involves 3 major parts as listed below.
The administrator tool is an executable written in JPHP programming language, a PHP running on Java Virtual Machine (JVM). These are used by the paid subscribers (here, the attackers) to log on, monitor, and control their bots remotely.
The JVM bytecode generated by this implementation, according to the JPHP documentation, compiles PHP sources to JVM bytecode, which can then execute on the JVM.
The JPHP project also offers DevelNext, a specific IDE in the Russian language. The DCRat administrator tool and several of the initial DCRat client versions were created using this IDE.
The PHP page serves as a C&C endpoint or interface; i.e. the page controlled by the attacker which is used to send commands to the compromised systems.
The DCRat client, or stealer, is perfectly suited for delivering to the victim's machine and is written in .NET binaries programmed in C#. Most likely, this was done to simplify and improve the client component.
The .NET is a compiled format of discrete executables. One binary, for instance, is keylogger.exe. This records a user's keystrokes and transmits them to the C&C server and admin panel.
Thus, once the DCRat's .NET payload is installed in the victim's device, the attacker can upload various modules created to the infected host, execute commands, and exfiltrate data with the help of the PHP page.
The following is the basic process through which the DCRat works:
Infection: This involves the transmission of the malware through malicious websites, email attachments, or third-party app stores. Once the victim downloads the malicious payload unknowingly, the malware gains access to the device.
Establish control: In order to control the compromised device remotely, the DCRat establishes a connection between the victim's device and the attacker's C&C server.
Stealth: By employing various techniques—such as concealing its presence in the background, disguising its network traffic, and eluding antivirus or security software—DCRats stay undetectable to the victim.
Command and control: The attacker can now send commands from a C&C server to the compromised device to access and modify the data present in that particular device.
Data exfiltration: The attacker can steal sensitive information from the compromised device such as login credentials, financial information, or any other personal data.
Persistence: To make sure that the DCRat reconnects to the C&C server—even after reboots and attempts to remove malware—the DCRat tries to prolong its presence and maintain persistence on the compromised device.
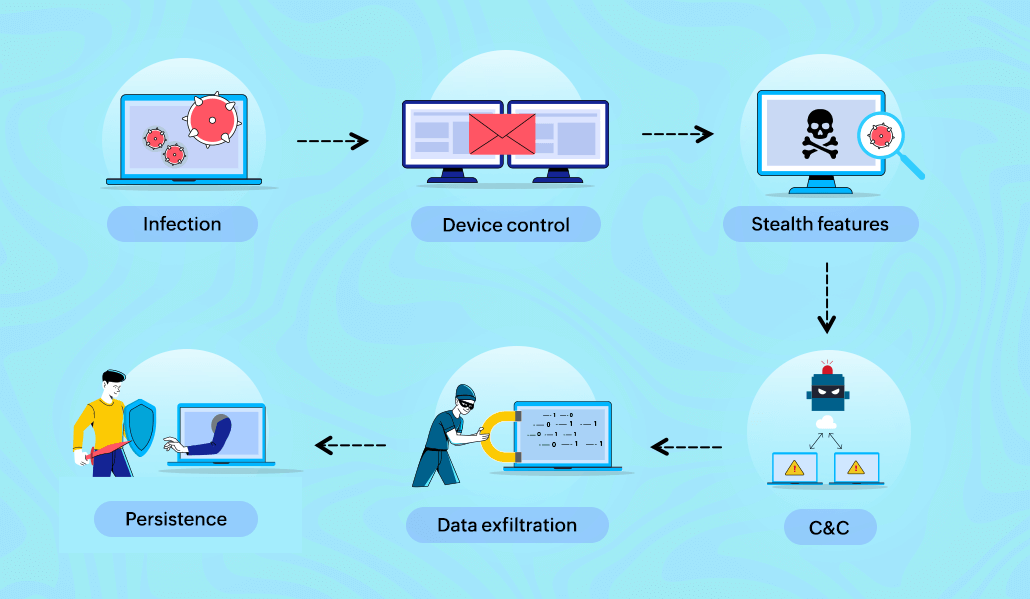 Figure 2: DCRat attack working flowchart
Figure 2: DCRat attack working flowchart
The DCRat can manipulate the hardware, software, and data of the compromised device.
The functions it can perform on hardware include:
Open and close the CD-ROM drive door.
Record audio via integrated microphones.
Record videos and stills through webcams.
The functions it can perform on files and folders include:
Rename, move, delete, and create new files or folders.
Download and upload files.
Execute or run files and close already running files.
Additionally, the Trojan can:
| Tactic | Technique | Description |
|---|---|---|
| Reconnaissance |
Gather Victim Host Information (T1592.001) (T1592.002) Gather Victim Network Information (T1590.005) |
The adversaries gain access to information about the target device. This information might be gathered via various techniques, including phishing and active scanning. Attackers try to gather the victim's IP address that can be used during targeting. |
| Initial access | Phishing: Spearphishing attachment (T1566.001) | Attackers try to gain access to the compromised device through spear phishing emails. |
| Execution |
Command and Scripting Interpreter: PowerShell (T1059.001) Command and Scripting Interpreter: Windows Command Shell (T1059.003) |
Attackers would now abuse PowerShell commands and scripts for execution. The attackers may abuse the Windows command prompt in order to control any aspects of your system with different level of permissions. |
| Execution, Persistence, and Privilege execution | Scheduled Task/Job: Scheduled Task (T1053.005) | Attackers will abuse the Windows task scheduler to execute malicious code. They use the .NET wrapper for the task scheduling. |
| Defense Evasion | Masquerading (T1036) | Attackers will manipulate their features to appear legitimate to the user. |
| Defense Evasion | Obfuscated Files or Information (T1027) | The attackers try to make the file difficult to analyze by encrypting its content. |
| Defense Evasion | System Binary Proxy Execution: Mshta (T1218.005) | Adversaries may abuse mshta.exe to proxy execution of malicious .hta files and Javascript through a trusted Windows utility. |
| Discovery | System Time Discovery (T1124) | The attacker will try to gain the time zone of the remote system with the help of .NET executables. |
| Command and Control | Ingress Tool Transfer (T1105) | The attackers transfer the tool or files from the external system to the compromised system. |
| Impact | Data Destruction (T1485) | The attackers try to destroy, modify, create, or overwrite the files on the specific systems. |
| Impact | System Shutdown/Reboot (T1529) | The attackers may try to reboot/ shutdown systems to interrupt access to the systems. |
Update your OSs, programs, and antivirus software frequently. Security fixes that fix flaws that RATs could exploit are frequently included in software updates.
Make sure the firewall is activated on each of your devices to prevent unapproved incoming and outgoing connections.
Avoid downloading from unidentified or dubious websites because they can house malicious files. Use trustworthy antivirus or antimalware software. Run system scans frequently to find and get rid of any potential RATs or malware.
Adopt safe browsing practices and remain cautious during online interactions. Watch out for phishing emails, phishing messages, and suspicious links.
Make regular backups of important files and store them in a safe place. In the event of a RAT infection or other security incident, backups allow you to restore your data without paying a ransom or suffering significant losses.
An effective SIEM solution will have capabilities to detect, prioritize, investigate, and respond to security threats. It can detect and help mitigate various malware attacks including DCRat.
The following actions can be performed with an effective SIEM:
If you want to protect your organization from malware such as DCRat, sign up for a personalized demo of ManageEngine Log360, a unified SIEM solution with data security and cloud security capabilities.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.