Direct Inward Dialing: +1 408 916 9393
Picture this: you're running a busy restaurant kitchen with multiple chefs. Everyone can cook, but imagine if they all tried to change the same recipe at the same time. Chaos, right? That's essentially what Active Directory faced in its early days — multiple domain controllers trying to make conflicting changes simultaneously.
FSMO (pronounced "fiz-mo") stands for Flexible Single Master Operations, and it's Microsoft's elegant solution to this coordination problem. Think of FSMO roles as specialized job assignments within your Active Directory kitchen. While every domain controller can handle the day-to-day cooking (such as authentication andbasic queries), only specific controllers get to be the head chef for certain critical recipes.
These aren't just random assignments either. Each FSMO role represents a unique responsibility that cannot have conflicts. When you need to update the Active Directory schema or create a new domain, there can be only one authority making that decision. That's where FSMO roles shine — they prevent the digital equivalent of too many cooks spoiling the broth.
The beauty of this flexibility is that these roles can move around. If your current schema master needs maintenance, you can transfer the role to another domain controller. It's like having backup head chefs who can step in when needed, ensuring your directory services never skip a beat.
Let's rewind to understand why Microsoft created this system in the first place. Early Windows domains used a single-master model — imagine one all-powerful domain controller handling every single change while others sat around doing basic tasks. Sure, there were no conflicts, but if that master controller went down, your entire domain ground to a halt:no password changes, no new users, no group modifications — nothing.
Microsoft's next attempt was the multi-master approach, where every domain controller could make changes. Sounds perfect, right? Well, not quite. Imagine two administrators creating user accounts at the exact same moment — or worse, one admin deleting a group while another adds members to it. The system would have to play referee using a last writer wins rule, which worked for simple conflicts but became a nightmare for complex operations.
Here's where it gets interesting: some operations are simply too important to leave to chance. When you're updating the fundamental structure of your directory (the schema), or ensuring that every security identifier is absolutely unique, you can't afford conflicts. Even a tiny mistake could cascade into a domain-wide disaster.
That's when Microsoft had their eureka moment. Instead of choosing between single-master limitations and multi-master chaos, they created a hybrid approach. Most operations could happen on any domain controller, but the really critical stuff would be handled by designated specialists — the FSMO role holders.
Think of it like a democracy with specialized committees. Everyone gets a vote on daily matters, but constitutional changes require a specific constitutional committee. Budget decisions need the finance committee; it's controlled flexibility that prevents both bottlenecks and conflicts.
The inguinity of FSMO roles is that they solve both problems simultaneously. You get the redundancy and distributed processing of multi-master replication for routine operations, but you also get the conflict-free certainty of single-master control for critical changes; it's the best of both worlds.
These five roles are split into two categories: two that are Forest-wide (there's only one of each for the entire AD forest, no matter how many domains you have) and three that are Domain-wide (each domain in your forest has its own set).
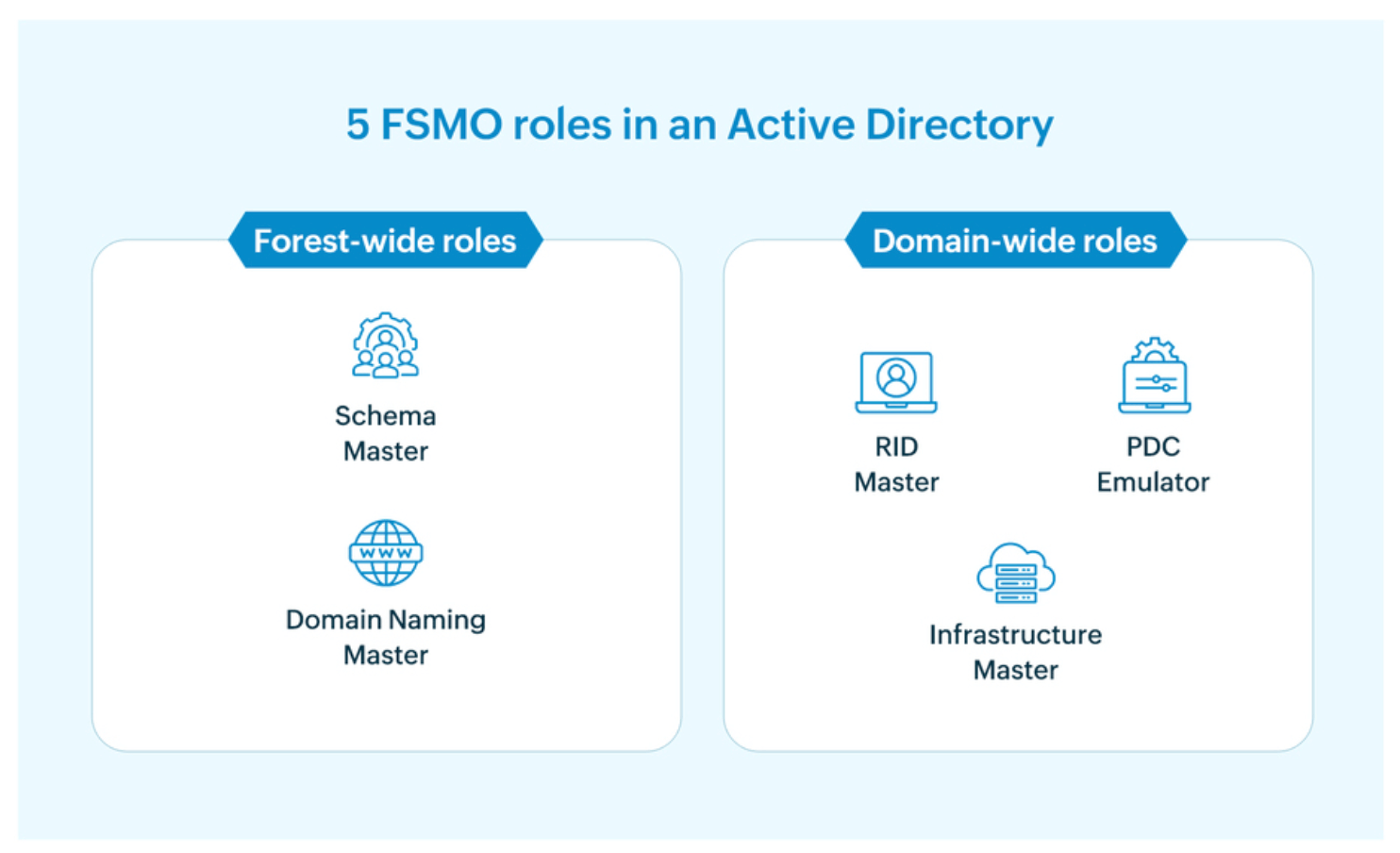
1. Schema Master: The keeper of the blueprint
This is the most sensitive role, often left untouched for long periods. The Schema Master DC is the only one permitted to make changes to the AD schema — the fundamental definition of every object type (user, computer, printer) and their attributes. When you install a new application that needs to extend the schema, such as Exchange Server, it must communicate with the Schema Master. Think of it as the city's head architect who alone can approve changes to the building code.
2. Domain Naming Master: The cartographer of the forest
This DC controls the addition and removal of domains within the forest. If you want to create a new child domain or remove an existing one, the request must be validated by the Domain Naming Master. It ensures that every domain has a unique name, preventing you from accidentally creating two domains with the same identity. It's the official mapmaker, ensuring no two cities in the kingdom share the same name
3. PDC Emulator: The master of time and urgency
This is arguably the busiest and most critical role for day-to-day operations. The Primary Domain Controller (PDC) Emulator has several key jobs:
4. RID Master: The dispenser of unique identity
Every object in AD (user, group, computer) has a unique Security Identifier (SID). A SID consistsof a domain identifier (the same for all objects in the domain) and a Relative Identifier (RID). The RID Master allocates pools of RIDs to each Domain Controller in the domain. When a DC creates a new object, it uses an RID from its pool. When the pool runs low, the DC requests a new block from the RID Master. This system guarantees that no two objects in the domain will ever have the same SID.
5. Infrastructure Master: The relationship manager
This role is primarily important in multi-domain environments. The Infrastructure Master is responsible for updating an object's SID and distinguished name in a cross-domain reference. For example, if you have a group in Domain A that contains a user from Domain B, and that user is renamed or moved, the Infrastructure Master in Domain A ensures the group's membership list is accurately updated. It maintains the integrity of these cross-domain relationships.
Knowing which domain controllers hold your FSMO roles is like knowing where you keep your spare keys — you might not need the information often, but when you do, it's absolutely critical. Fortunately, there are several ways to identify your current role holders, each with its own advantages.
From any server or workstation with AD tools installed:
netdom query fsmo
Split into forest-level and domain-level queries:
Get-ADForest | fl SchemaMaster, DomainNamingMaster
Get-ADDomain | fl RIDMaster, PDCEmulator, InfrastructureMaster
A transfer is a planned, graceful operation. You do this during routine maintenance, like when you are decommissioning an old Domain Controller or upgrading hardware. The role is moved smoothly from one DC to another with no service interruption.
Use the Move-ADDirectoryServerOperationMasterRole cmdlet.
Example:
Move-ADDirectoryServerOperationMasterRole -Identity "TargetDCName" SchemaMaster
Move-ADDirectoryServerOperationMasterRole -Identity "TargetDCName" DomainNamingMaster
Move-ADDirectoryServerOperationMasterRole -Identity "TargetDCName" PDCEmulator
Move-ADDirectoryServerOperationMasterRole -Identity "TargetDCName" RIDMaster
Move-ADDirectoryServerOperationMasterRole -Identity "TargetDCName" InfrastructureMaster
Run this on (or authenticated to) the target DC.
Think of ADManager Plus as your dedicated Active Directory auditor. While you already know which server holds your precious Schema Master or PDC Emulator roles, the real question is: How healthy and secure is that server right now? This is where ADManager Plus moves beyond simple role checking and delivers a crucial risk assessment report. It gives you a centralized report for your entire DC fleet, directly impacting the safety of your FSMO roles.
The tool actively scans your domain controllers to generate reports that flag potential risks, such as: