Direct Inward Dialing: +1 408 916 9393
The Lightweight Directory Access Protocol (LDAP) is a widely adopted open standard for accessing and maintaining information in a directory service like Active Directory (AD). A directory service is like an organized phone book for your network, storing information about users, devices, and resources. LDAP is the protocol that apps use to communicate with directory services, allowing them to authenticate users, authorize access, search for information, and manage directory data. Despite being around for decades, LDAP still remains relevant due to several key factors, like its support for centralized identity management; legacy system compatibility; and its open, vendor-neutral nature.
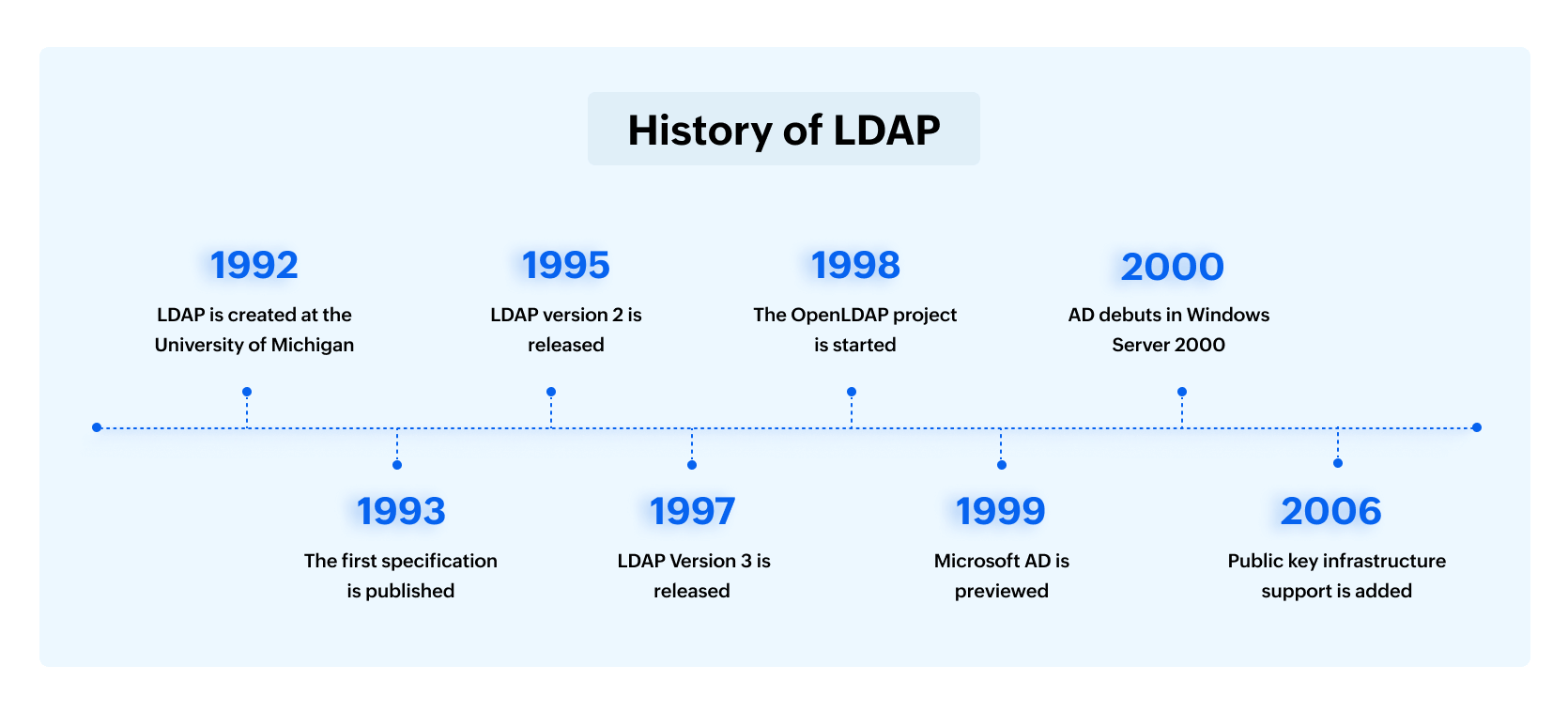
The timeline below highlights some important milestones in LDAP's development. Each event marks a step forward in features, security, and reliability, reflecting LDAP's growing role in directory services over the years.
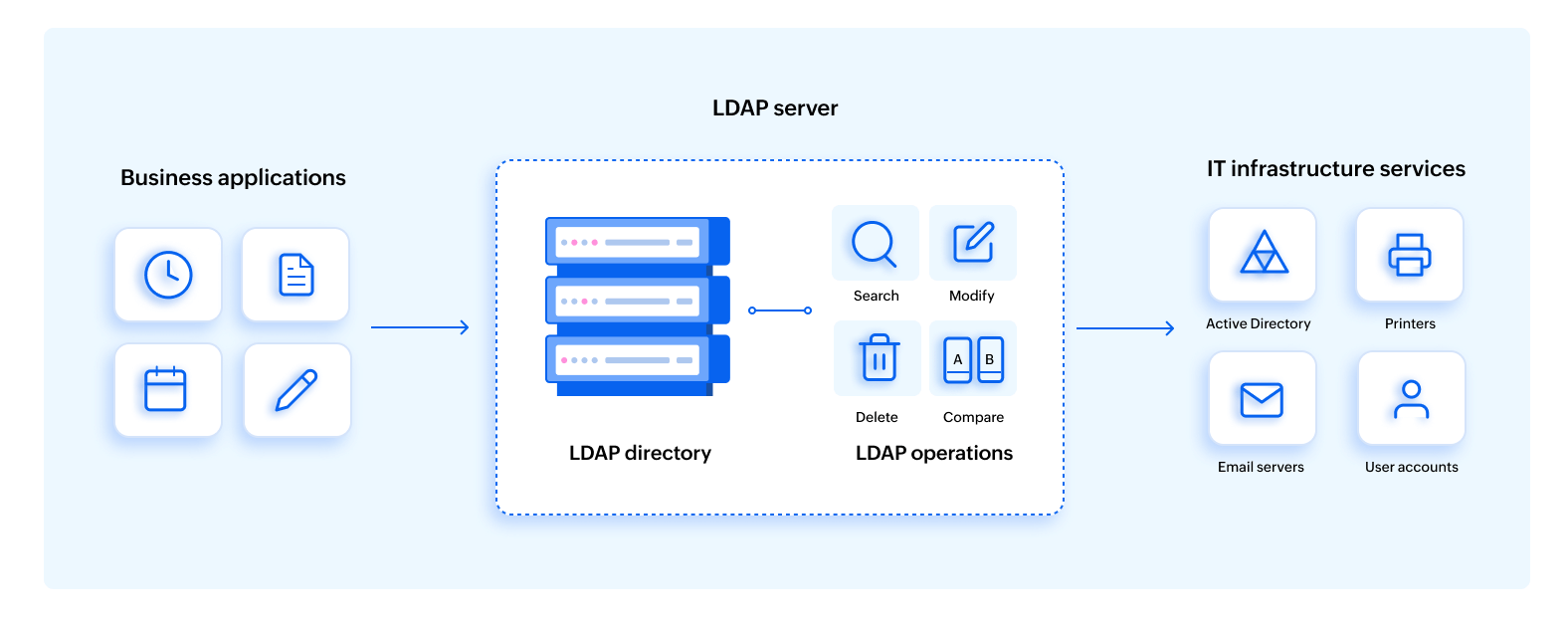
LDAP works as a client-server model. The table below is a breakdown of the core LDAP terms and components that form the foundation of how directory services operate, enabling structured data storage, querying, and secure access in enterprise environments.
| LDAP term | Description |
|---|---|
| Client | Any application that needs to query or modify information in the directory. Examples include OS login processes, email clients, web apps, VPN appliances, and SSO systems. |
| Server | Also known as the Directory System Agent, the LDAP server stores directory information. It waits for the client requests, processes them, and returns responses. |
| Schema | Defines rules and structure for entries in an LDAP directory, which includes attribute syntaxes, object classes, and matching rules that specify required attributes and data types for objects. |
| Operation types | Core actions that clients perform in LDAP, such as Bind (authenticate), Search (find entries), Add, Delete, Modify, Modify DN (rename/move), Compare, Unbind (disconnect), Abandon (cancel operation), and Extended (miscellaneous or custom operations). |
| Distinguished name | A distinguished name (DN) is a name that uniquely identifies an LDAP entry by specifying its full path in the directory tree. Each DN consists of one or more relative DNs, which are components like cn=John Doe or ou=Sales and form a hierarchical structure to the entry. |
| Filter | Expressions used to find or match specific entries in the directory, using an attribute-value pair (e.g., (objectClass=person)). |
| URL | Structured strings that point to LDAP resources and include information about the server, what to look for, and search conditions. They are used for queries, referrals, and connections.
Format: ldap[s]://host:port/base-dn?attributes?scope?filter. |
| Result code | Numeric and named codes returned by LDAP after an operation to indicate status or errors (e.g., success, entry not found, or insufficient access). These codes clarify the success of or the nature of problems in directory operations. |
| Directory information tree | A hierarchical tree structure where data is organized within an LDAP directory. Each node in the tree is called an entry, which has a DN that specifies the exact location in the directory information tree. |
| DNS SRV record | DNS service (SRV) records are DNS entries that help clients automatically find and connect to LDAP servers (like locating LDAP on default port 389 or LDAPS on 636) by telling them which servers are available and how to reach them. |
Here's the typical process an application follows to authenticate and interact with LDAP.
LDAP also relies on specific ports for communication. Ensuring these are properly configured is crucial for reliable LDAP operations.
LDAP servers serve as the central repository for user accounts, passwords, group memberships, and other identity attributes. This centralizes user management and streamlines onboarding and offboarding.
While SSO is achieved through SAML or OAuth, LDAP directories often serve as the back-end identity store that SSO solutions query to verify user credentials.
Because LDAP has been around for a long time, many enterprise systems were built with LDAP integration. Maintaining LDAP support helps these systems to keep running without needing expensive changes.
LDAP benefits from a wide community of developers, admins, and researchers. This leads to continuous improvement and an abundance of online resources
LDAP and AD are closely related but are not the same.
Think of AD like a massive library that stores millions of books while LDAP is the versatile "card catalog" system or search engine you use to find those specific items within. In enterprise environments, it's common for both to be used together. LDAP is a core protocol that AD supports and helps clients query information. LDAP also helps AD integrate non-Microsoft apps, enabling you to communicate with them without maintaining separate databases.
LDAP stands for Lightweight Directory Access Protocol. It was designed to be a simplified and lightweight version of an earlier, heavier protocol called Directory Access Protocol (DAP), which was part of the X.500 directory service standard.
LDAP is neither a database nor a server but a protocol used to access and manage directory information. An LDAP server is the software that implements this protocol, like AD. These servers store data in a specialized directory, which is a hierarchical, database-like structure optimized for identity data and fast lookups.
LDAP authentication is a process where an application (client) performs a bind operation to an LDAP server using a user's DN and password. The server verifies the credentials, and if successful, it establishes an authenticated session, allowing the client to perform authorized LDAP operations like search, add, modify, or delete.