Firewall rule order - Firewall Analyzer
Firewall policies and rules ensure network security. Optimized firewall rules strengthen IT security. Anomalous rules can create security holes in the firewall. Unused rules and new rules created without studying the impact on the existing rule set will lead to an anomaly. All of the above will make the network vulnerable to attacks.
The impact of rule anomalies on network security
Anomalous rule sets allows hackers to penetrate the network to harvest the data and cripple the servers. The categories of anomalies are:
- Redundancy
A redundant rule performs the same action on the same packets as another rule, such that if the redundant rule is removed, the security policy will not be affected. - Generalization
A rule is a generalization of another rule if the first rule matches all the packets that the second one could match, but not the opposite. - Correlation
Two rules are correlated if they have different filtering actions; the first rule matches some packets that match the second rule, and the second rule matches some packets that match the first rule. - Shadow
A rule is shadowed when a previous rule matches all the packets that match this rule, such that the shadowed rule will never be evaluated. If the shadowed rule is removed, the security policy will not be affected.
You can see that anomalies make the rules weaker and put network security at risk. More than one rule may allow or filter the same packets in the same way, when the rules are anomalous. Two rules may allow or deny the same type of packets to be passed. Out of two rules, first and second rules will allow or deny one packet, but the rules in the reverse order will not allow, or will deny the same packet. These anomalies can be overcome by rearranging the firewall rule order.
Thorough analysis and reconfiguration of rules will remove rule anomalies. However, a quick fix solution is arranging the rules in a specific order. This order of rules will reduce the anomaly to a great extent. Configuring a correct order of rules will reduce the impact of the anomaly to a great extent.
How Firewall Analyzer helps remove rule anomalies
ManageEngine Firewall Analyzer is a perfect tool for rule order recommendations. If you implement the recommended reorder, it will remove the rule anomalies.
The tool fetches all the rules from the firewall device. It analyzes the rules for anomalies and recommends the reorder of rules. You have to implement the order recommendations into the device manually.
Rule anomaly reports
Firewall Analyzer generates rule anomaly reports. This report classifies the rule anomalies and groups the rules with the same anomaly classification. You will see the number of rules under each anomaly classification.

Policy Optimization report
Firewall rules order recommendations
The tool generates the firewall rule order report. In this report, you will see the current order and the recommended reorder of the rules. You can change the firewall rule order in the device as recommended in the report. This will remove the rule anomalies and optimize the firewall policies.

Rule Reorder Recommendation - Suggested Changes

Rule Reorder Recommendation - Complete Changes
Rule clean up recommendation
This tool also provides a rule cleanup report. With this rule clean up recommendation, you can remove the unused firewall rules to make the firewall performance more efficient.
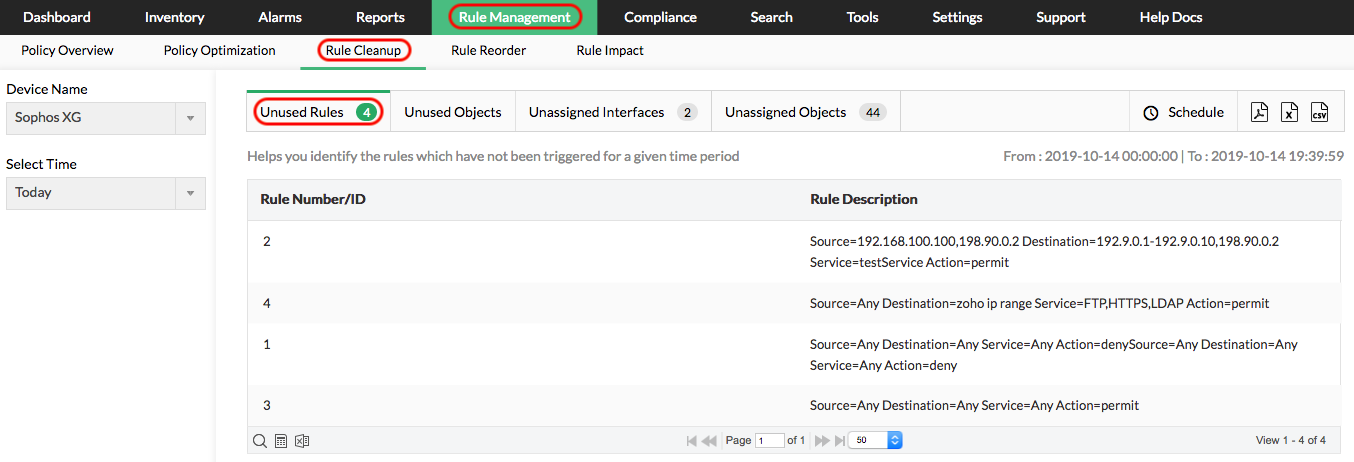
Rule Cleanup Recoomendation report
Use Firewall Analyzer, the firewall rule order solution, to ensure that there are no anomalies in your firewall rules.
Refer Configure Firewall Rules page to know how to configure firewall rules.
Refer Firewall Management Stategy page to know more about management strategy.
Sign up for your free 30-day trial!
Thank you for your feedback!