FTP Usage Report
How does Firewall Analyzer help track FTP usage?
Firewall Analyzer tracks FTP usage from the firewall syslog and provides a detailed traffic report on:
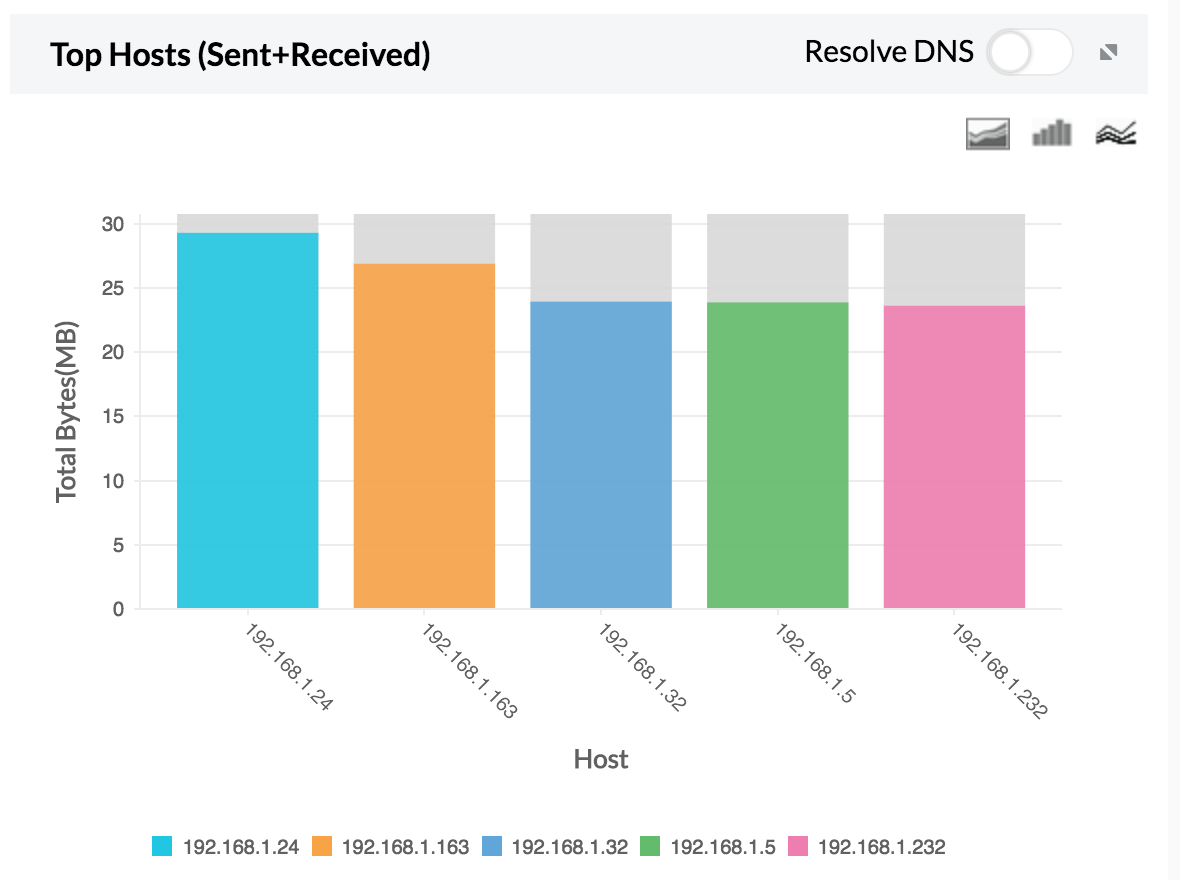
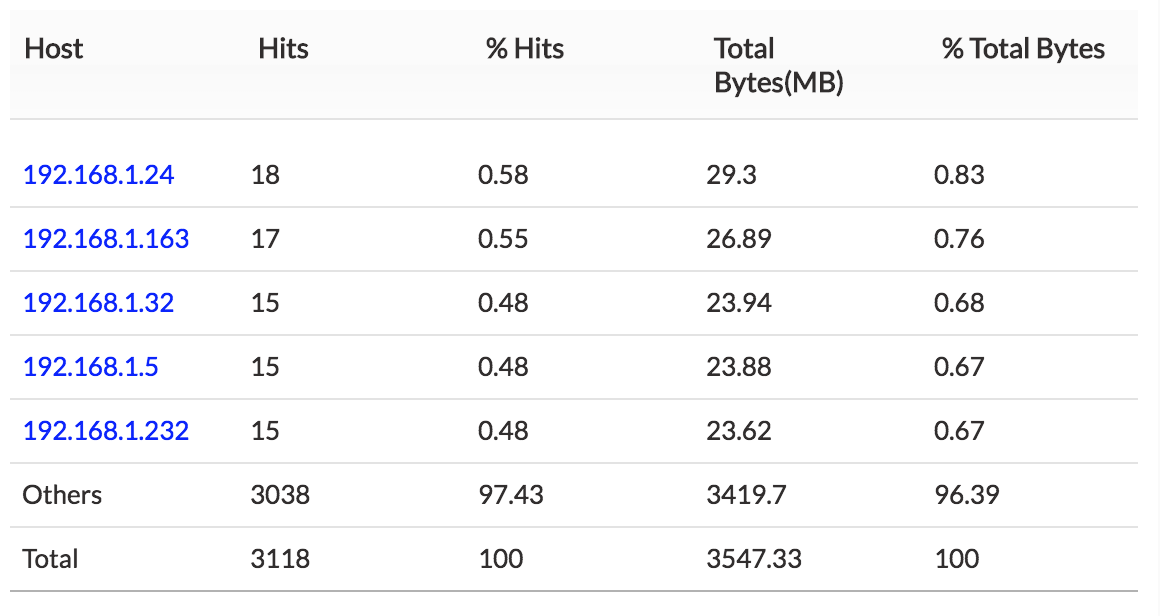
1. Top Host — Total host traffic sent and received using FTP.
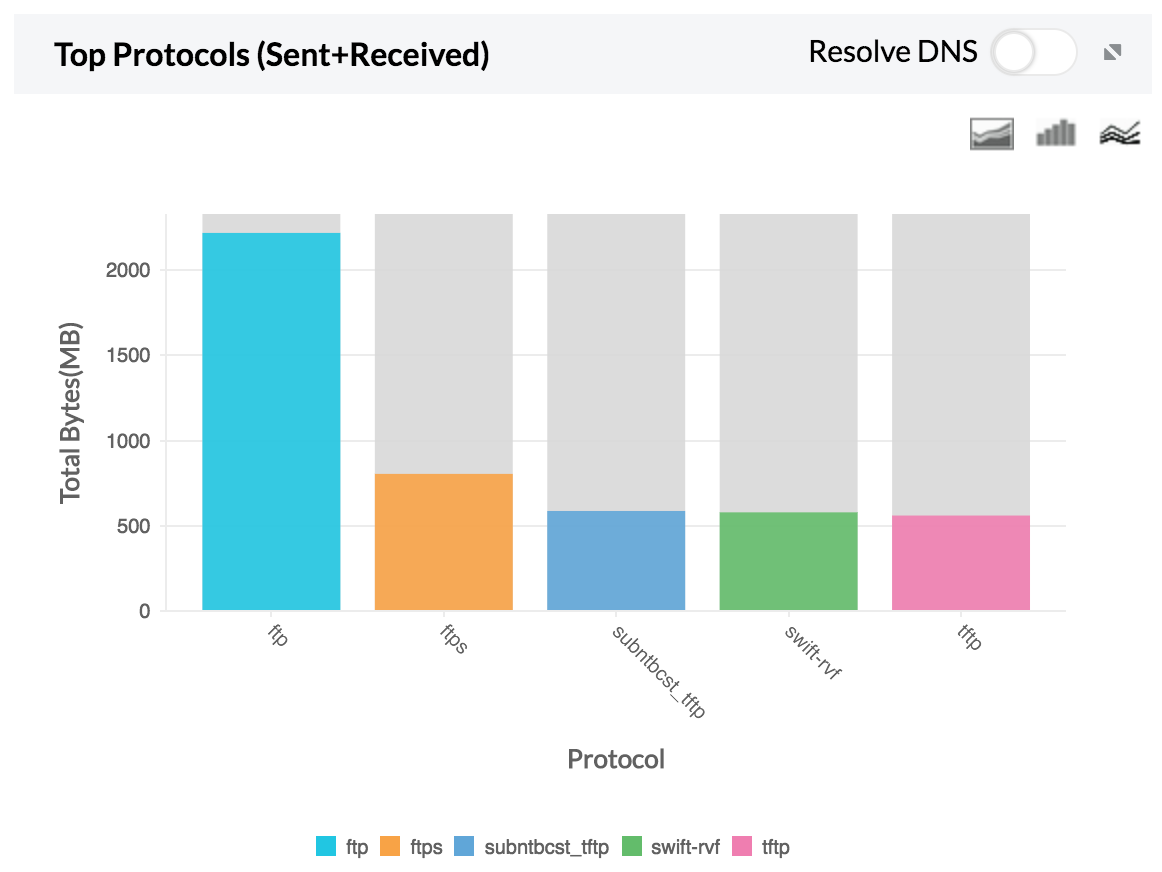
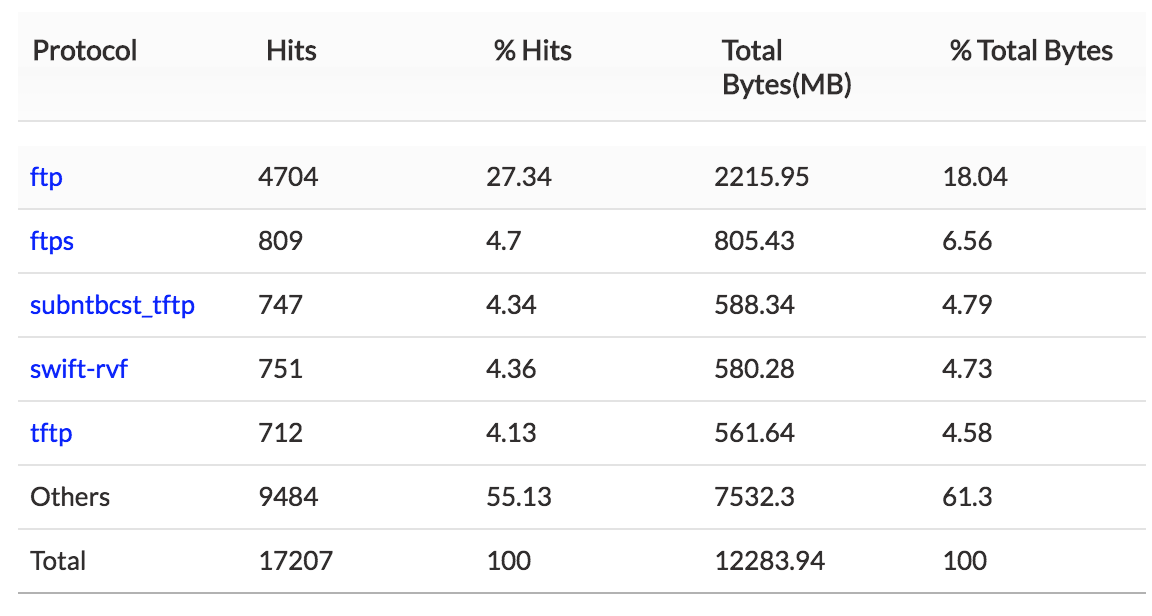
2. Top Protocol — Top protocol group traffic sent and received using FTP.
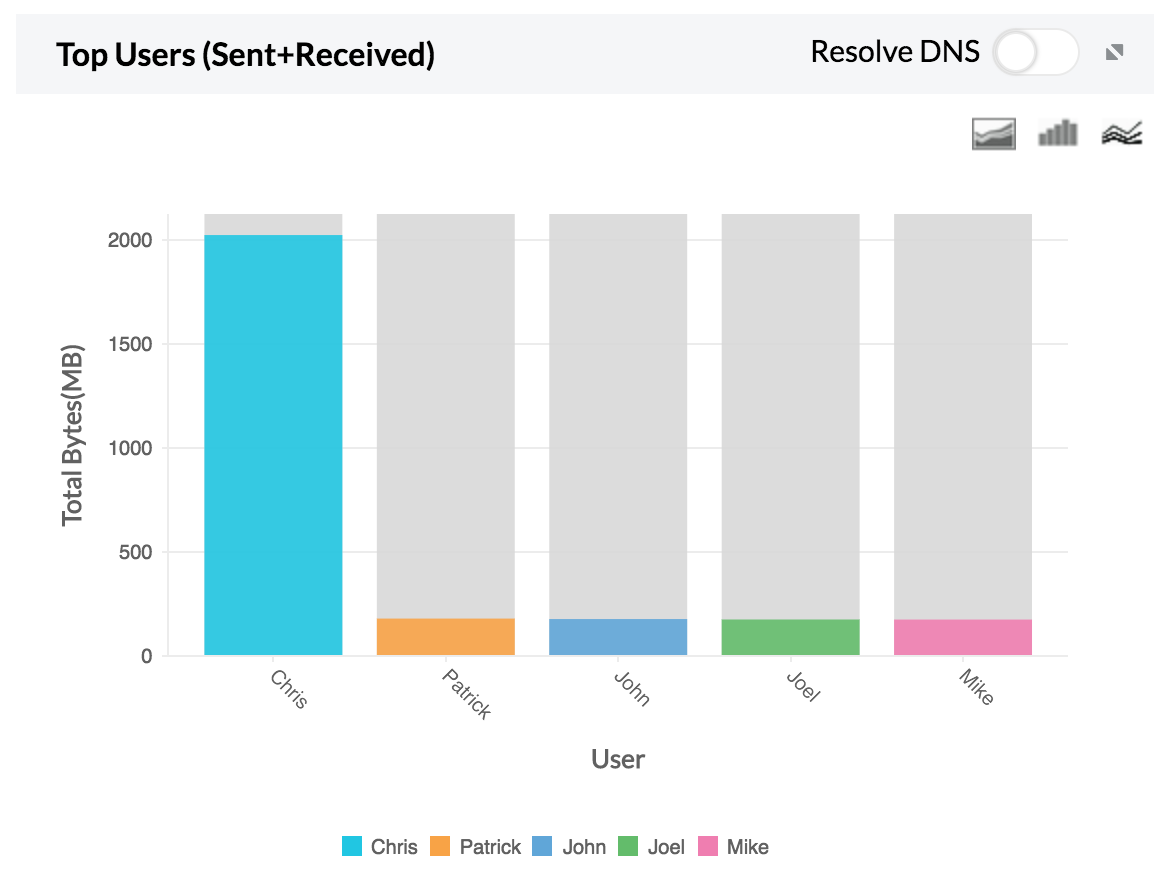
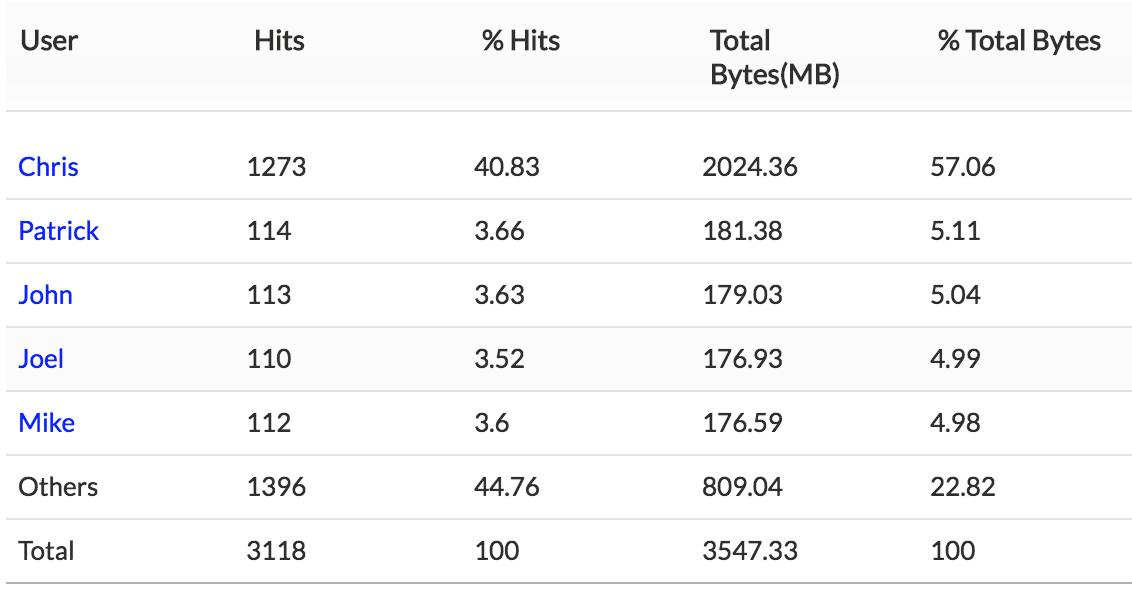
3. Top Users — Top user traffic sent and received using FTP.
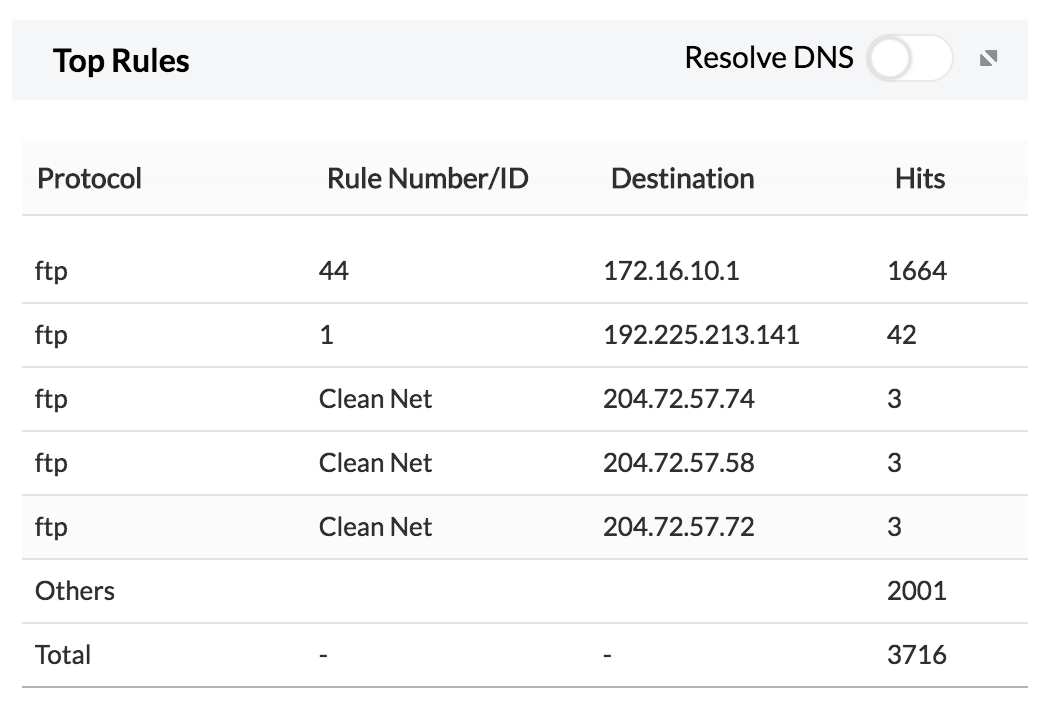
4. Top Rules — The top rules used to access FTP.
If either the host or the user shows unusual traffic, the security admin can investigate and secure that specific IP.
Why should you track FTP usage?
FTP or The File Transfer Protocol is a standard network protocol used for transferring files between any two computers on a network. No system is 100 percent secure and this applies to FTP servers as well. Although the chances of a properly secured FTP server getting hacked is low, but the possibility is still there. Tracking FTP usage, allows one to overcome its shortcomings.
By default, there is a provision that allows local commands to be executed in FTP servers built in Linux and Windows servers. A malicious user might be able to elevate privileges by exploiting this security flaw.
FTP is based on plain text. During login, the user name and password are sent across as plain text without encryption; this makes the protocol vulnerable to hackers who can use different tools to obtain these credentials.
Featured links
Firewall Rule Management
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Log Management
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
Thank you for your feedback!