Telnet Usage Report
How does Firewall Analyzer help track Telnet usage?
Firewall Analyzer tracks Telnet usage from firewall syslogs and provides a detailed traffic report on the following:
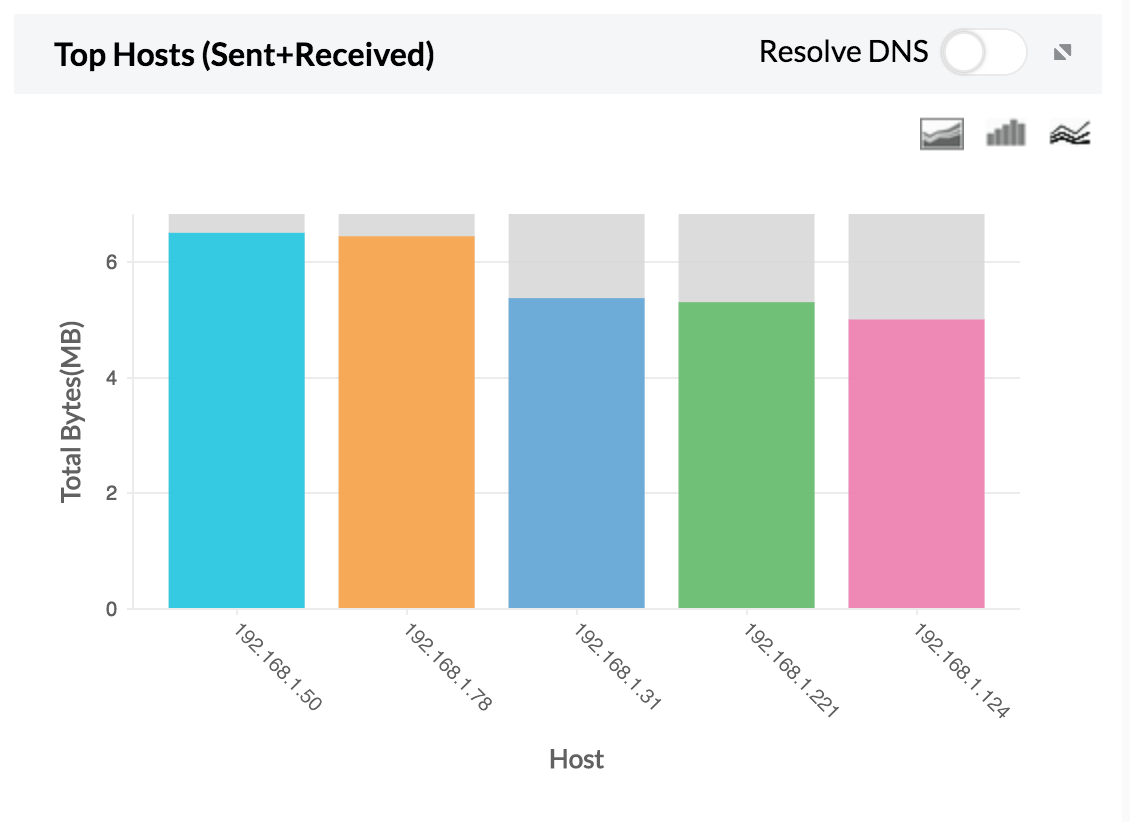
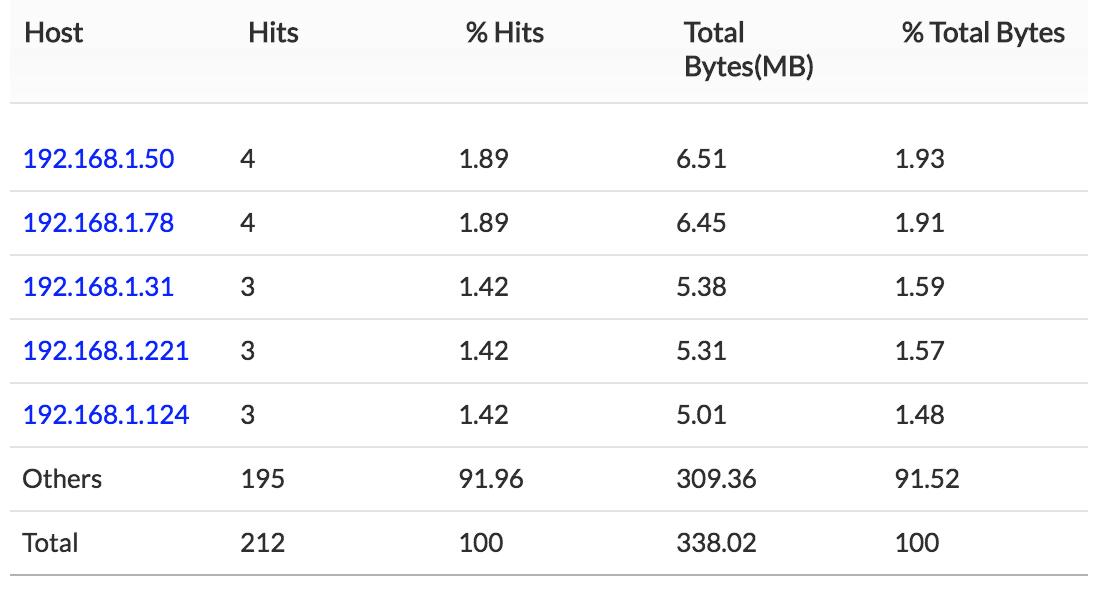
1. Top Host — Total host traffic sent and received using Telnet.
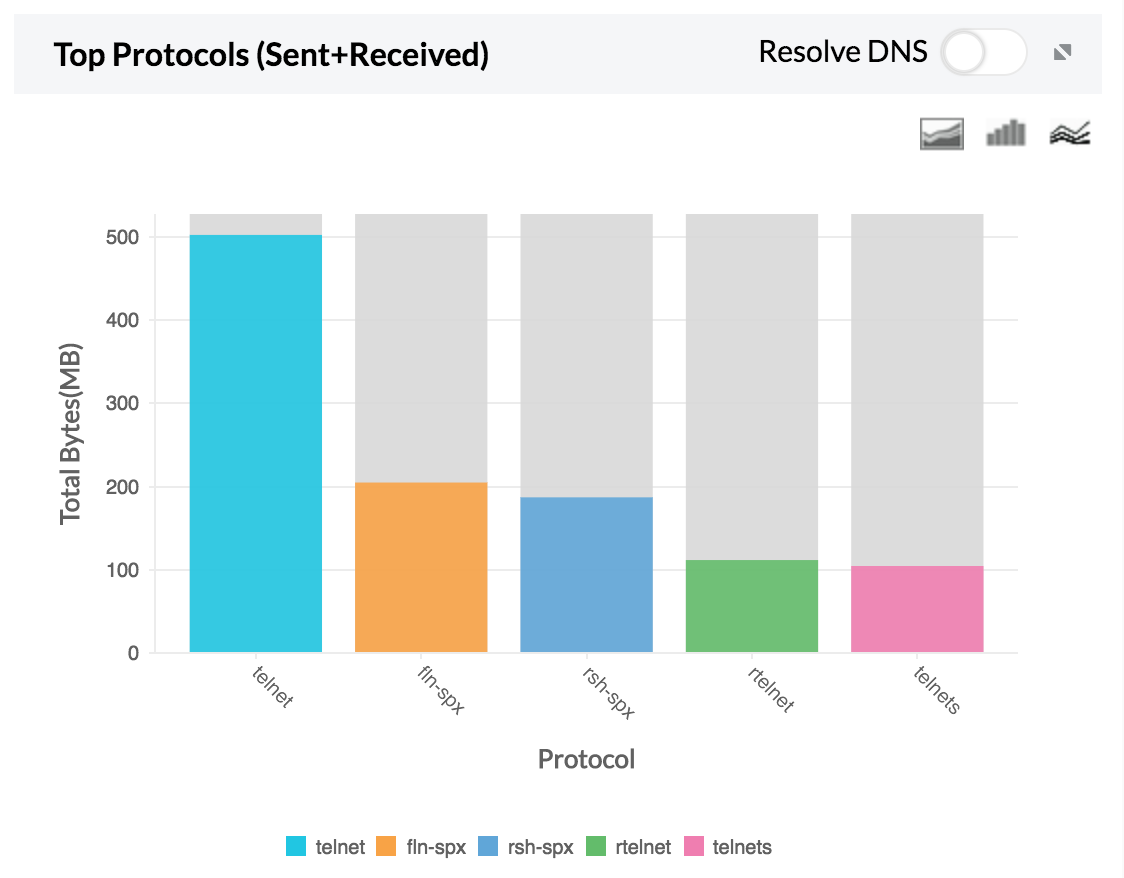
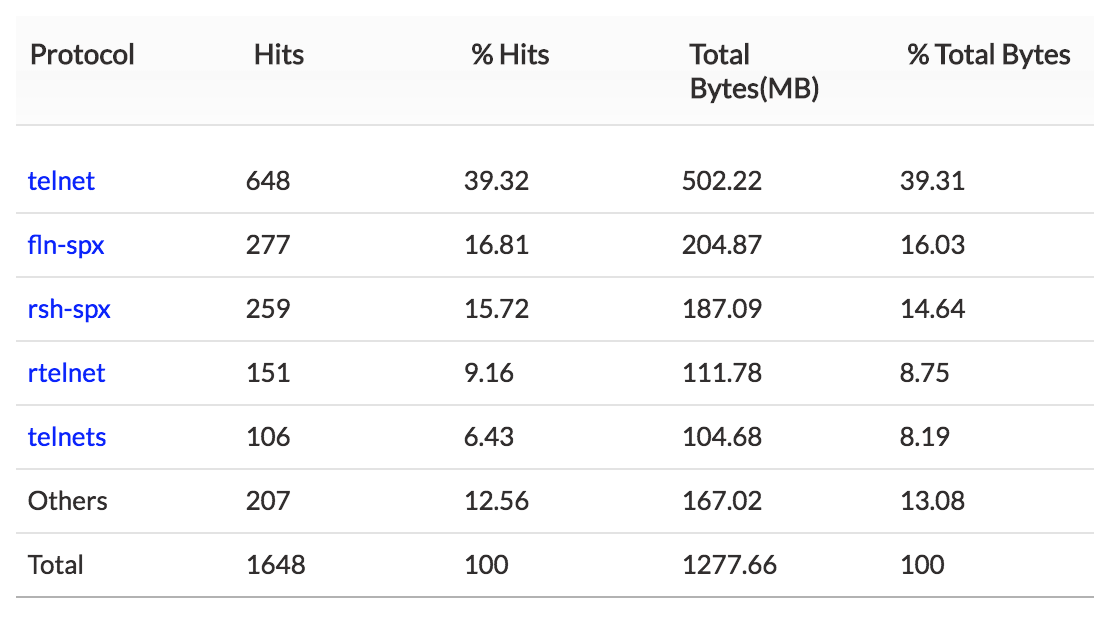
2. Top Protocol — Top protocol group traffic sent and received using Telnet.
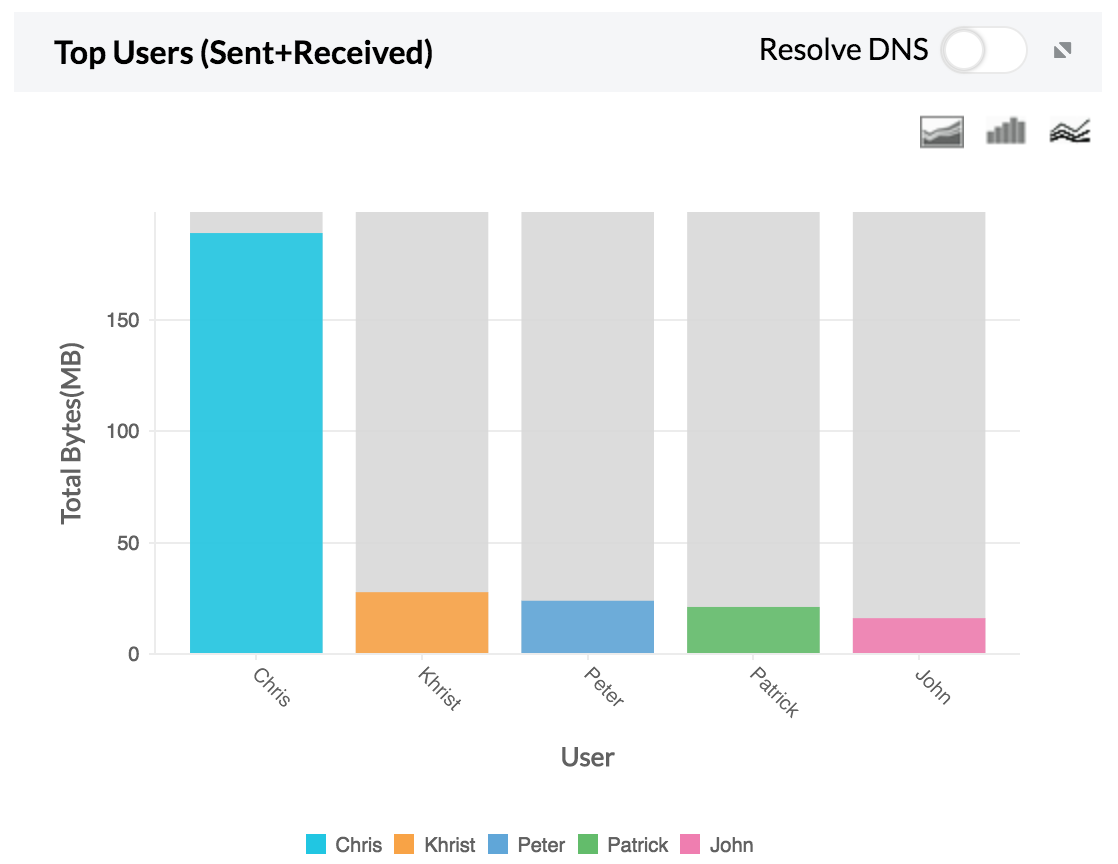
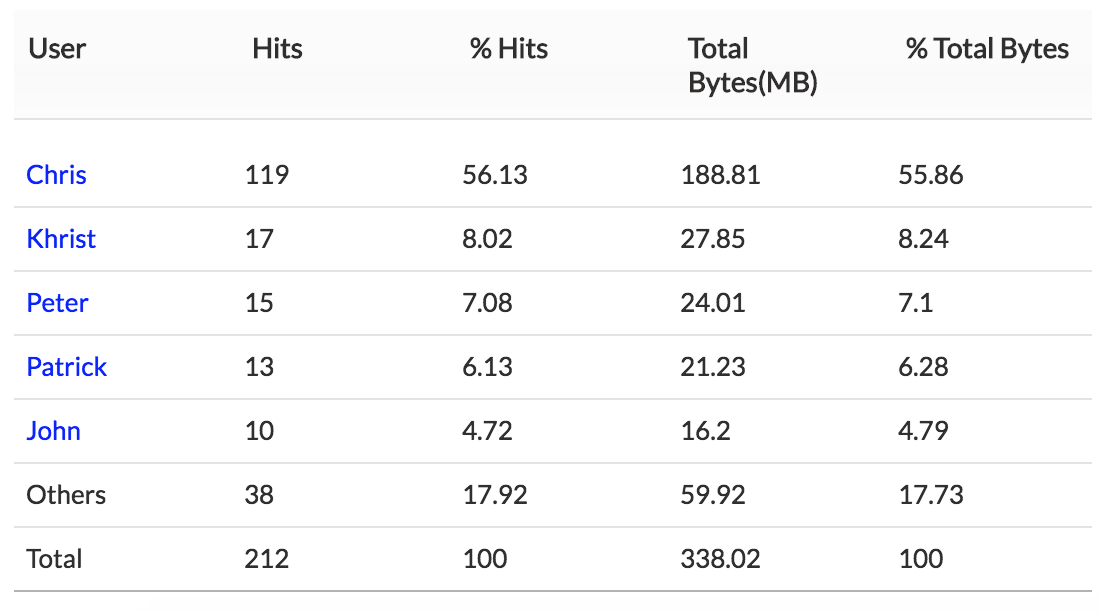
3. Top Users — Top user traffic sent and received using Telnet.
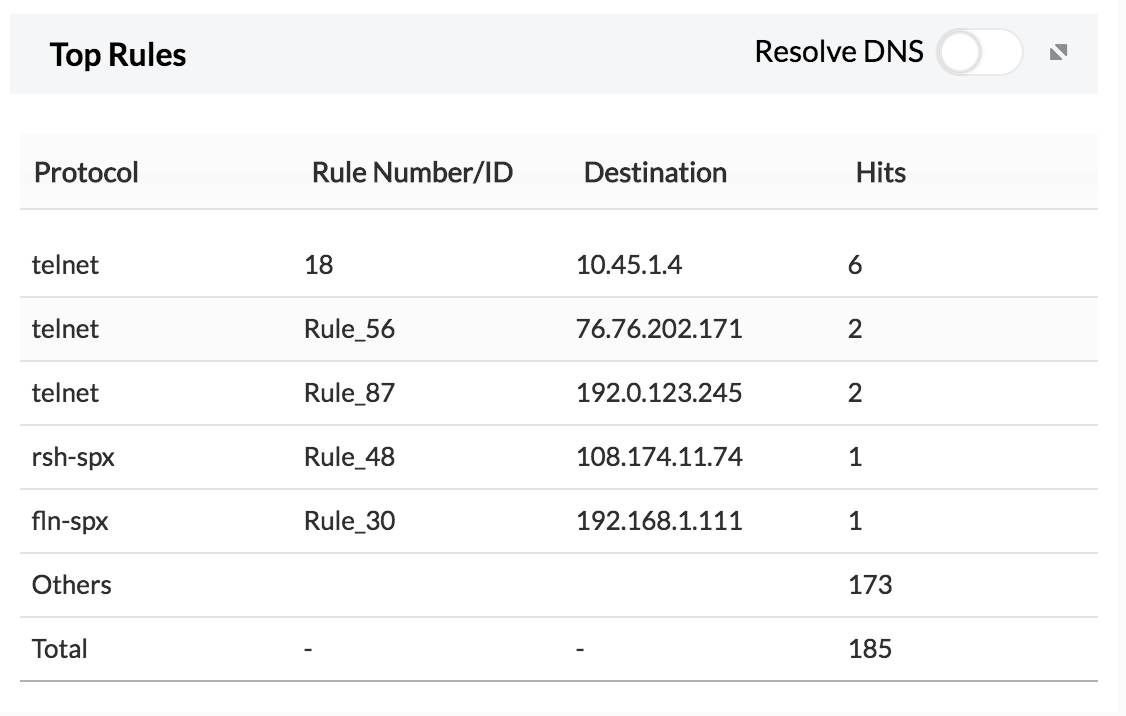
4. Top Rules — The top rules used to access Telnet.
If any one of the hosts or users show unusual traffic, the security admin can investigate and secure that specific IP.
Telnet
Telnet is a protocol used on the Internet or a local area network to provide a bidirectional, interactive, text-oriented communication facility using a virtual terminal connection. Using Telnet, one can connect to a remote computer over the Internet and use applications on the remote computer as if it were a local machine.
Why track Telnet usage?
Telnet allows you to gain access to a remote computer, which can be dangerous if your computer is taken over by a hacker—an all too real possibility. If Telnet usage goes unmonitored, hackers can use a port scanner to gain access to your network and then use Telenet as an extremely potent hacking tool to execute commands in a remote machine. With a Telnet client program, hackers can.
- Read and send emails from the system.
- Download source codes from web sites.
- Probe the services offered by the system.
- Send unexpected input to web servers.
Featured links
Firewall Rule Management
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Log Management
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
Thank you for your feedback!