Have you come across chaos theory? Chaos theory, summarized by Edward Lorenz, an American mathematician, addresses the behavior of complex systems like weather and the stock market. It can also be applicable to the human brain, another complex system. The theory articulates that the slightest of changes in the initial conditions of these complex systems can lead to substantial impact at the later stages. Building upon that, you can postulate that if you fail to record the slightest of changes in these complex systems and neglect their consequences, it becomes impossible for you to predict and control the consequences of those changes in the future.
This principle holds true for your Active Directory (AD) environment too, which is a complex system increasingly susceptible to cyberattacks. Neglecting to notice or address changes in your AD could lead to network disasters. Uninvited changes might prompt threats to your network, putting your entire network at risk. Witness the United N ations data breach of 2019.
The United N ations experienced an espionage attack in 2019. Three UN offices in Europe were targeted by attackers who exploited a known but unpatched vulnerability in Microsoft SharePoint to gain access to the Active Directory environment of three UN offices. The attackers then moved laterally to the entire UN network to compromise 42 critical servers. They breached the admin accounts to exploit user and password management systems, system controls, and security firewalls. The United N ations tried to contain the damages, but critical user accounts and credentials were already exposed. The attack could have been prevented if the UN's AD infrastructure was well reinforced. Conversely, security gaps in its AD infrastructure paved the way for several attack paths, leading to chaos in its AD environment.
AD attack paths originate from a series of security gaps in the AD infrastructure. These are a chain of abusable privileges and actions that are easily made available for the attackers to exploit. The most common ones are overprivileged user accounts, admin accounts with concealed privileges, and nested group memberships.
Let us consider a user, Tim. Tim is a workstation admin who solves technical support issues for users as and when they arise. For this, he has been added to the Workstation Admin security group and has been delegated the necessary permission to edit GPOs. The Workstation Admin group is a nested group within the Sysadmin security group, which has local administrator permissions. This allows Tim to avail local admin privileges even though he doesn't require them. This grants Tim excessive permissions, making him an over privileged user. On being compromised, Tim's account allows attackers to exploit the privileges, leading to these attack paths.
The above are a few of the numerous possible attack paths that can be traversed by the attackers. But attackers are way ahead of us in cracking new attack paths to exploit AD environments.
On applying the chaos theory here, identifying the actual attack paths in the complex AD system is impossible without monitoring the changes and tracking anomalous activities. This makes AD auditing an obvious solution for identifying the attack paths and preventing AD attacks.
ManageEngine Log360 Cloud is a cloud SIEM solution with Active Directory auditing capabilities. It can help you track AD changes in real time and map the possible attack paths to prevent chaos in your Active Directory. Here is a glimpse of how it can help you gain complete visibility into your AD environment to prevent the propagation of an attack:
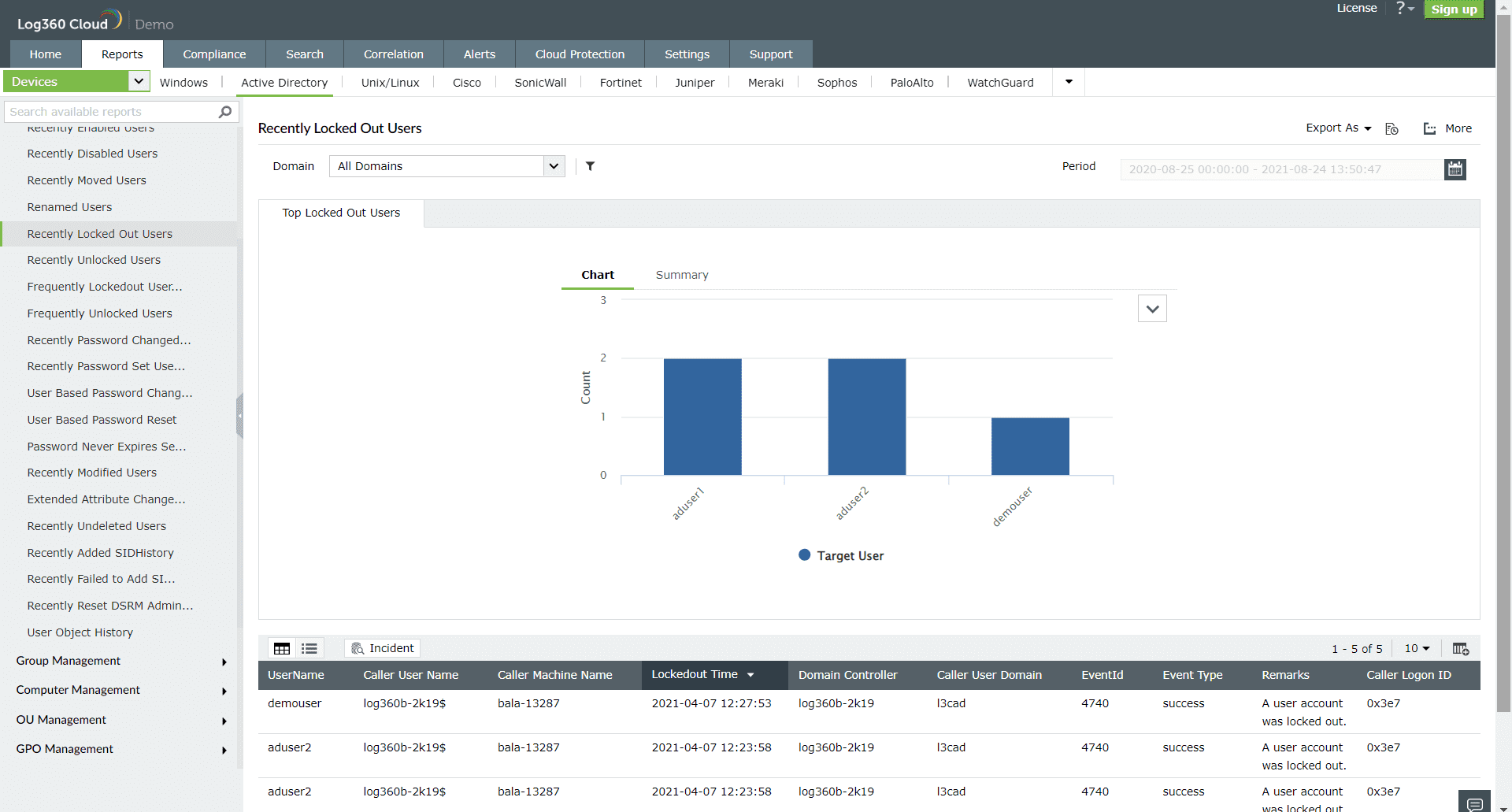 Figure 1: User lockout report in Log360 Cloud
Figure 1: User lockout report in Log360 Cloud
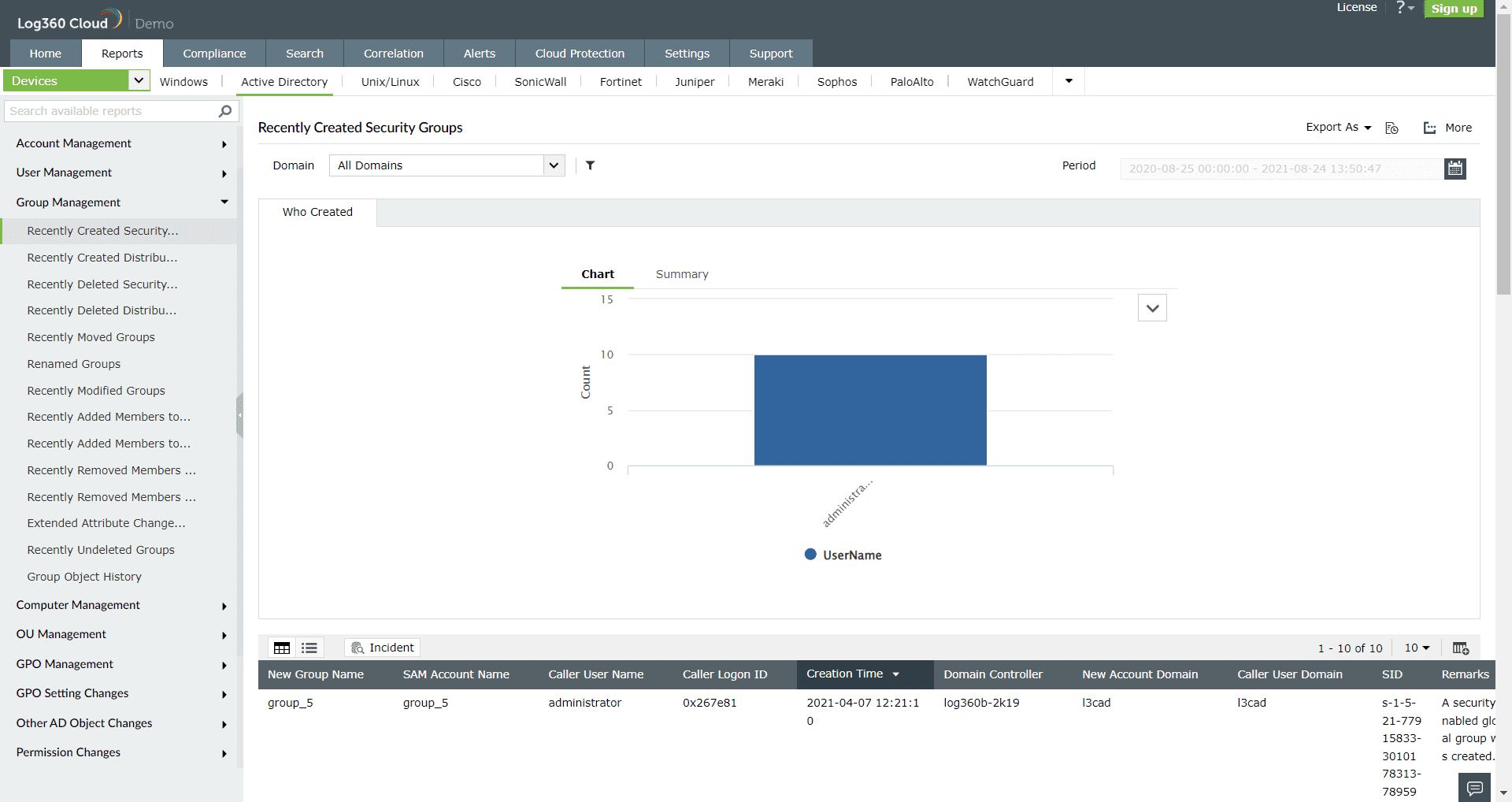 Figure 2: Group management report in Log360 Cloud
Figure 2: Group management report in Log360 Cloud
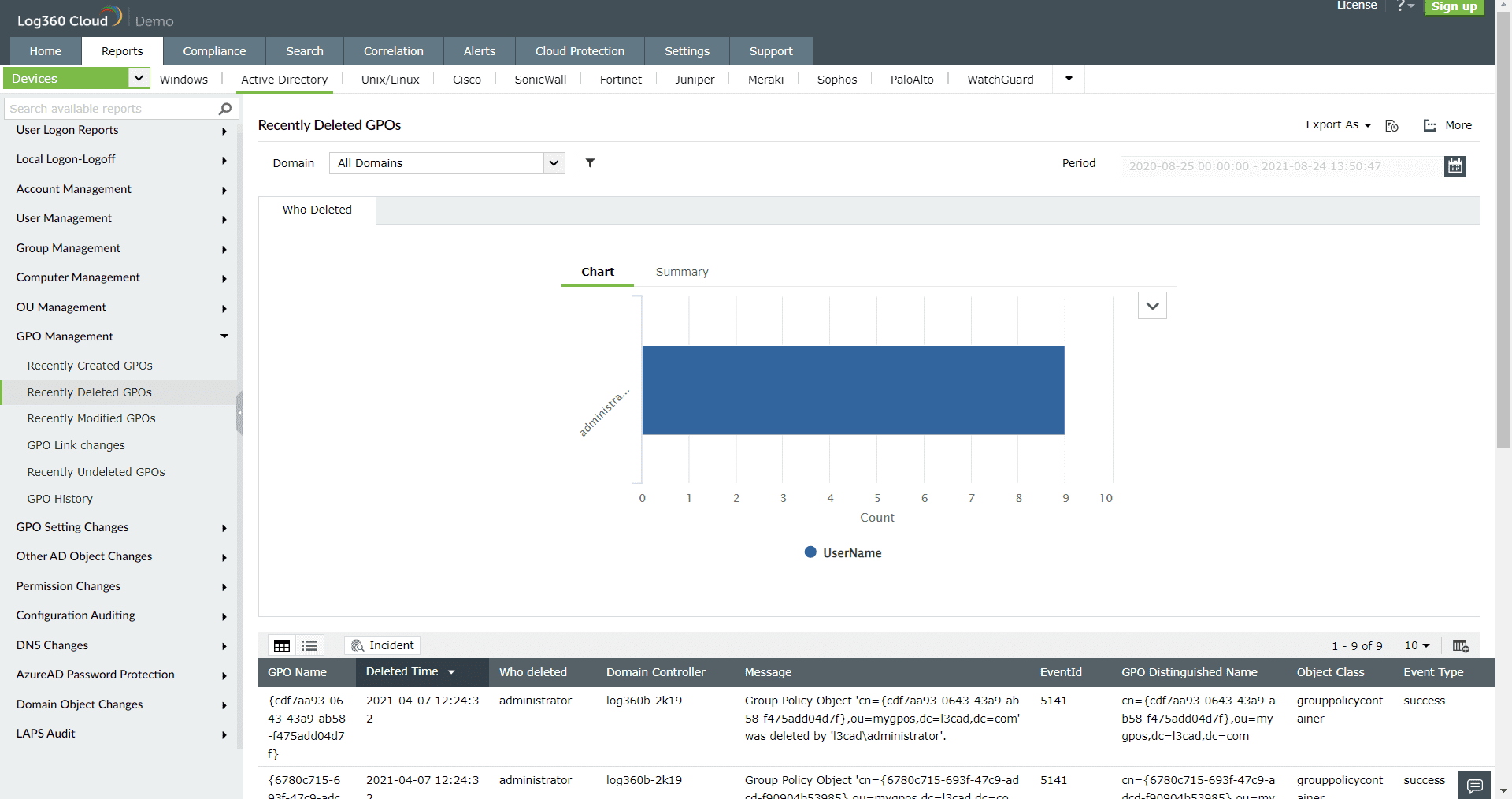 Figure 3: GPO management report in Log360 Cloud
Figure 3: GPO management report in Log360 Cloud
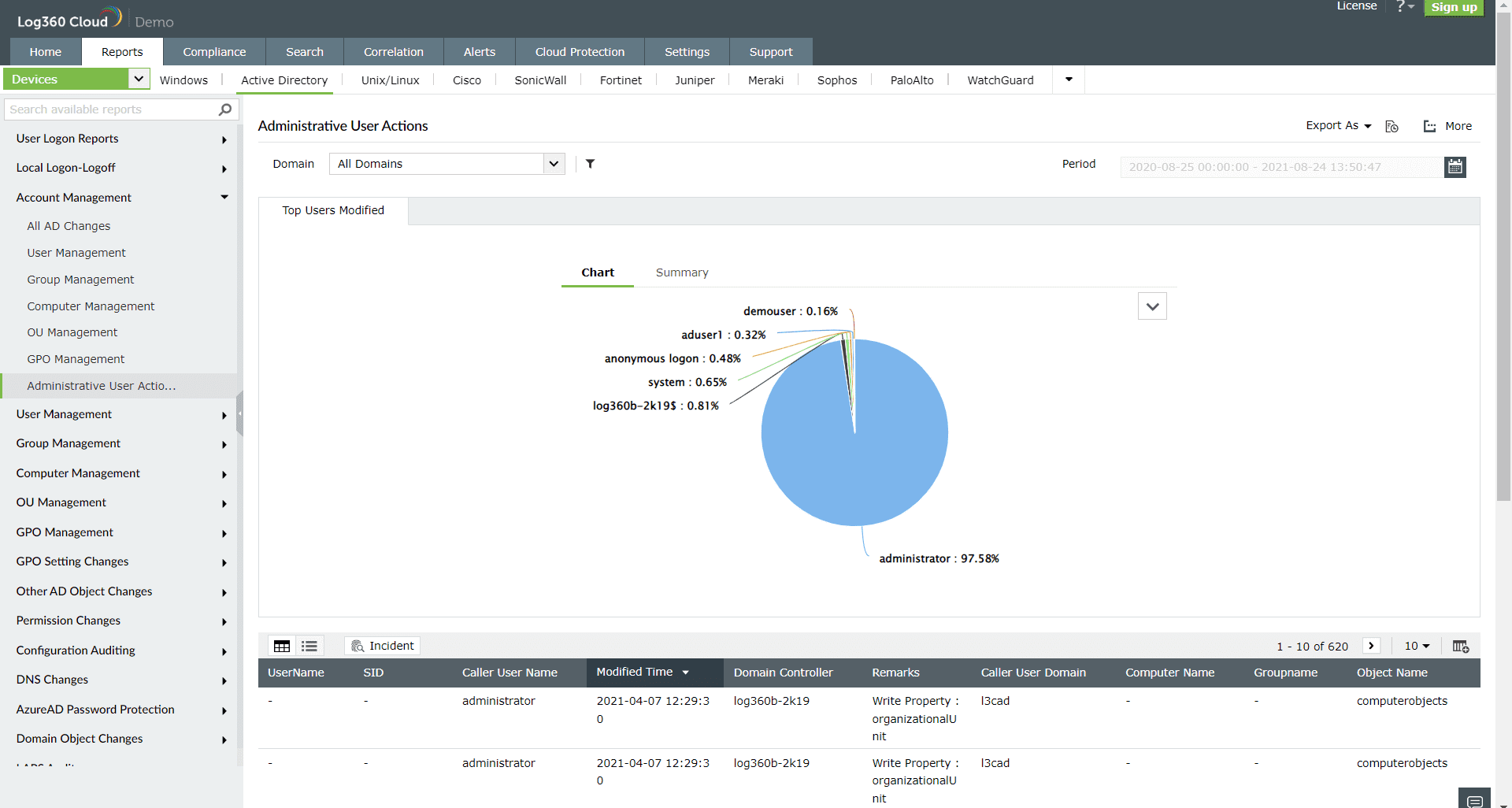 Figure 4: Administrative user actions report in Log360 Cloud
Figure 4: Administrative user actions report in Log360 Cloud
Prevention is better than cure. Now, you can nip the attack paths in the bud with Log360 Cloud to stay ahead of attackers and defend AD attacks. Log360 Cloud further enables you to track AD changes from the cloud and stage your defense against AD chaos from anywhere and everywhere.
To discover more about Log360 Cloud, sign up to evaluate a free trial today. You can also schedule a free, personalized demo with one of our solution experts.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.