The United States healthcare sector has experienced a steady rise in both volume and cost of data breaches in recent years. This is shown by the 61% increase in the number of HIPAA violations in 2020 over the previous year, with penalties totaling $13 million in the US healthcare sector. As of 2023, a single healthcare data breach incident cost US businesses an average of $9.3 million.
The Office for Civil Rights (OCR) has reported that the heathcare industry is struggling to meet HIPAA compliance clauses and violations are on the rise.
If you're a security manager endeavoring to make your organization HIPAA compliant, then this blog is for you. Get to know the most crucial HIPAA standards that your organization should comply with to secure electronic protected health information (ePHI), and estimate your HIPAA compliance score with our checklist.
Part 164, subpart C, of the Health Insurance Portability and Accountability Act, 1996 enumerates the security standards for the protection of ePHI. These standards are applicable to all covered entities and business associates as defined by HIPAA. The administrative safeguards to be practiced by healthcare organizations include:
Do you remember the CIA triad? The model is the foundation for information security. It requires your team of security analysts to ensure the confidentiality, integrity and availability of information. Based on the CIA triad, this HIPAA standard requires you to implement policies to monitor, detect, prevent, and mitigate information security breaches by effective risk management. HIPAA puts forth the following checklist while establishing your security management process.
The most dangerous threats while managing ePHI are those that come from insiders. In order to ensure the integrity of information against insider threats, this HIPAA standard requires that you implement specific controls over user access, permissions, and privileges of the workforce members who manage ePHI. HIPAA directs you to ensure the following checklist while implementing policies to monitor the workforce.
As the name suggests, HIPAA requires you to set up policies and procedures to authorize and authenticate access to all network resources that deal with ePHI. HIPAA requires you to check the following list during access management.
Any event that indicates an impending threat is considered a security incident. HIPAA requires you to monitor, record, and analyze such security incidents in the beginning stages to detect and prevent potential breaches. For this, you have to adhere to the below standard.
Are you ready to assess your organization's HIPAA compliance readiness? Use the checklist below to find out your score.
 HIPAA compliance using SIEM
HIPAA compliance using SIEM
(Disclaimer: The scores are estimated based on the information provided and should not be considered a definitive measure of your organization's compliance with HIPAA.)
ManageEngine Log360, a unified SIEM solution, can help in your journey towards HIPAA compliance with:
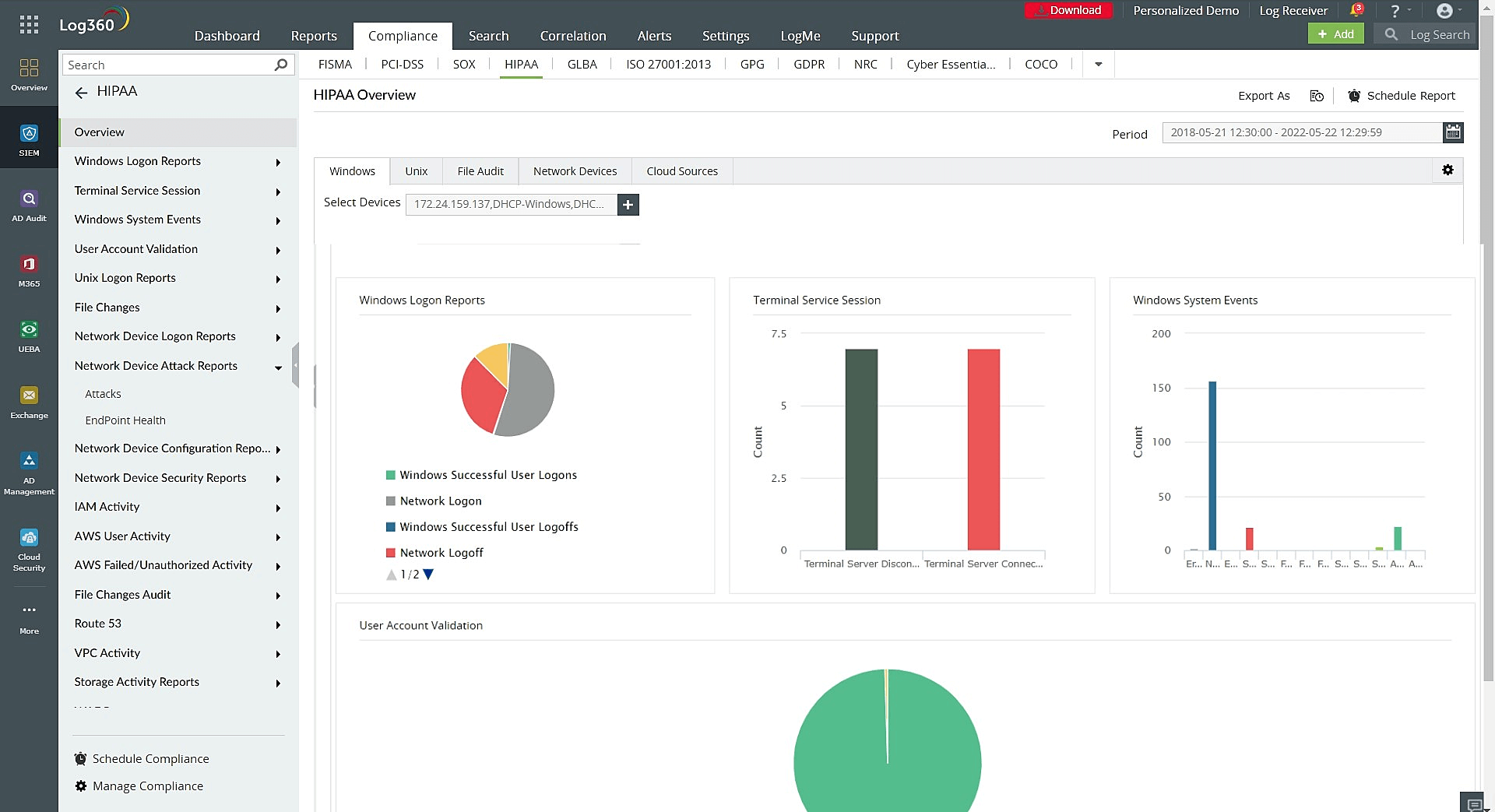 Figure 1: HIPAA Overview dashboard in Log360.
Figure 1: HIPAA Overview dashboard in Log360.
In 2015, a major healthcare organization in the US fell victim to a massive data breach affecting 78.8 million patient records. A phishing email was the point of initial access for the attackers. The attackers then moved laterally to escalate privileges and access patient databases. The damage was devastating, and the organization had to pay a sum triple its cybersecurity budget.
In addition to achieving HIPAA compliance, proactive security is now the need of the hour in the healthcare industry. Log360 can help you surpass your quest for HIPAA compliance and become proactive against cyberattacks.
Here is a glimpse of how Log360 can help you:
As today's threat landscape evolves, embattling cyberattacks is easier said than done. So get it done with help from Log360. Sign up for a personalized demo today.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.