The increased adoption of the cloud can potentially increase the risk of insider threat due to employee negligence in an organization. This is because employees are more likely to lose control when switching between numerous personal and corporate cloud applications. According to a Ponemon Institute report from 2022, employee negligence is responsible for 56% of insider threats and its annual average cost is a whooping $6.6 million. In 2020, 17% of data breaches were caused by an employee error, double that of the previous year, according to Verizon. In a nutshell, unintentionally exposed enterprise data is rising with cloud adoption.
Negligence leading to insider incidents can happen for two reasons: 1) Prioritizing convenience over compliance, and 2) Not keeping personal accounts and devices protected with the best security measures.
Here are three scenarios that might sound relatable:
- An employee sends work files to their personal email account so that they can work on their laptop over the weekend.
- An employee uploads customer data to an unsanctioned analytics SaaS application to perform better analysis.
- A new employee uploads sensitive data to their personal Google Drive or Box account to download and access on their mobile device or share it with colleagues.
These examples could be common practices in many organizations. Consider an employee's personal cloud account or device being compromised due to misconfigured settings, weak passwords, or phishing. This could expose sensitive enterprise data by bad actors. The security analyst must identify malicious insiders while minimizing false positives. Gaining visibility into the cloud app usage and user behaviors will help mitigate such security concerns.
Cloud application security best practices
Here are a few strategies that can greatly improve your cloud security posture and reduce the risk of cyberthreats.
1. Employ strong authentication: Use multi-factor authentication (MFA) to gain access to cloud apps. This provides an additional degree of security beyond passwords, making it more difficult for attackers to gain unauthorized access. Monitor all user login activity to identify any anomalies.
Log360 offers detailed information on recent successful and unsuccessful login events. This allows IT security administrators to evaluate user activities and detect misuse of privileges and unauthorized access attempts. Log360 also constantly monitors suspicious activity and alerts you in real-time through email and SMS notifications.
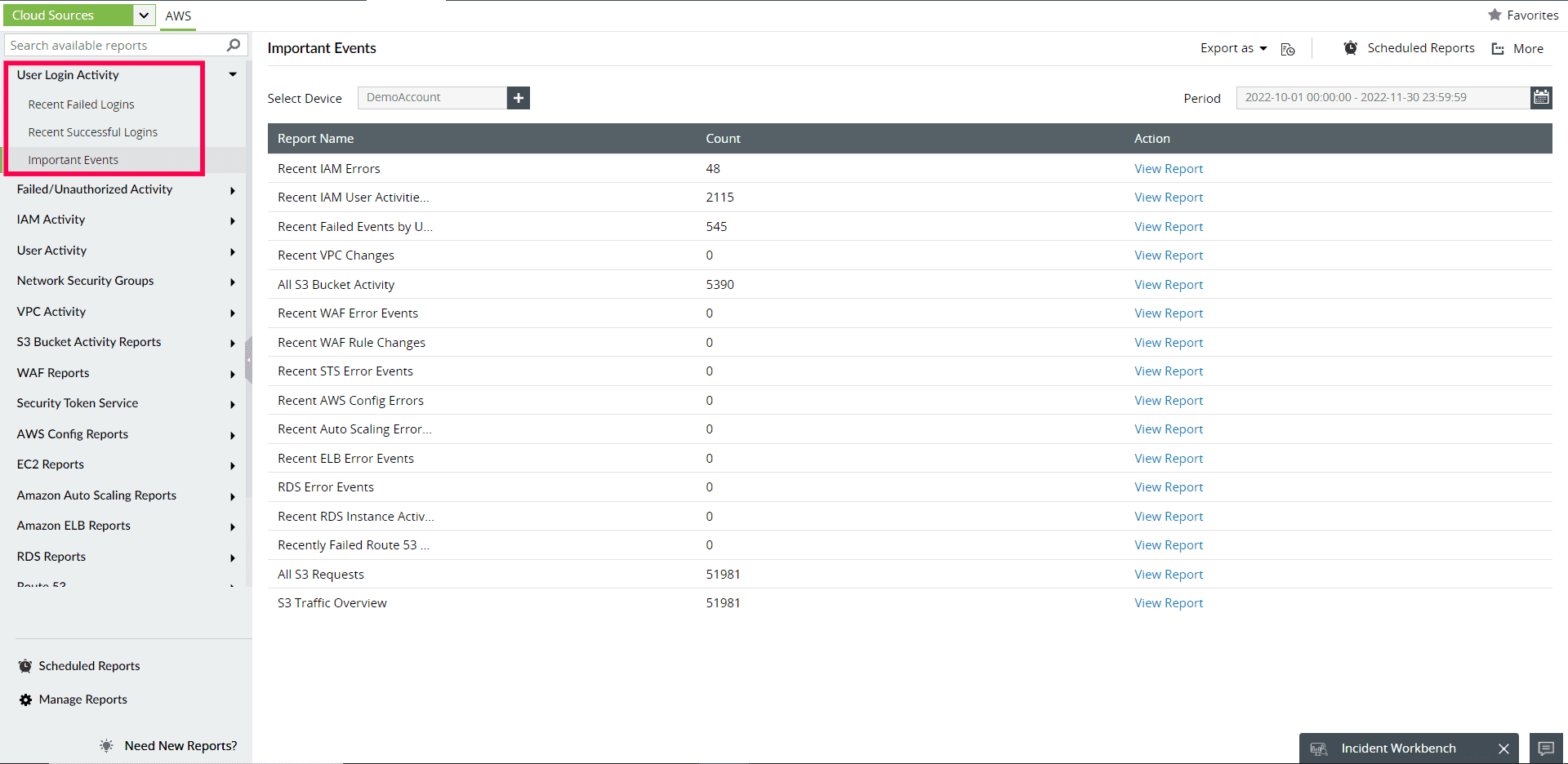
Figure 1: Cloud sources user login activity report in Log360
2. Detect cloud misconfigurations:Cloud misconfigurations occur when a user sets up cloud services improperly or specifies settings that do not provide adequate security for the data stored in the cloud. Cloud misconfigurations are arguably the leading cause of data breaches that take place on the cloud. And in the majority of cases, it is only due to a single misconfiguration that the breach occurs. This challenge is made more difficult due to the shared responsibility model inherent in cloud computing. For example, a misconfigured Amazon Web Services S3 bucket could result in the exposure of critical data to the public.
Therefore regular and comprehensive security audits of the cloud infrastructure should be done so these misconfigurations can be rectified and vulnerabilities can be detected. SIEM solutions like ManageEngine Log360 come with out-of-the-box reports for monitoring cloud sources. Figure 2 depicts a comprehensive report on AWS S3 bucket changes in Log360.
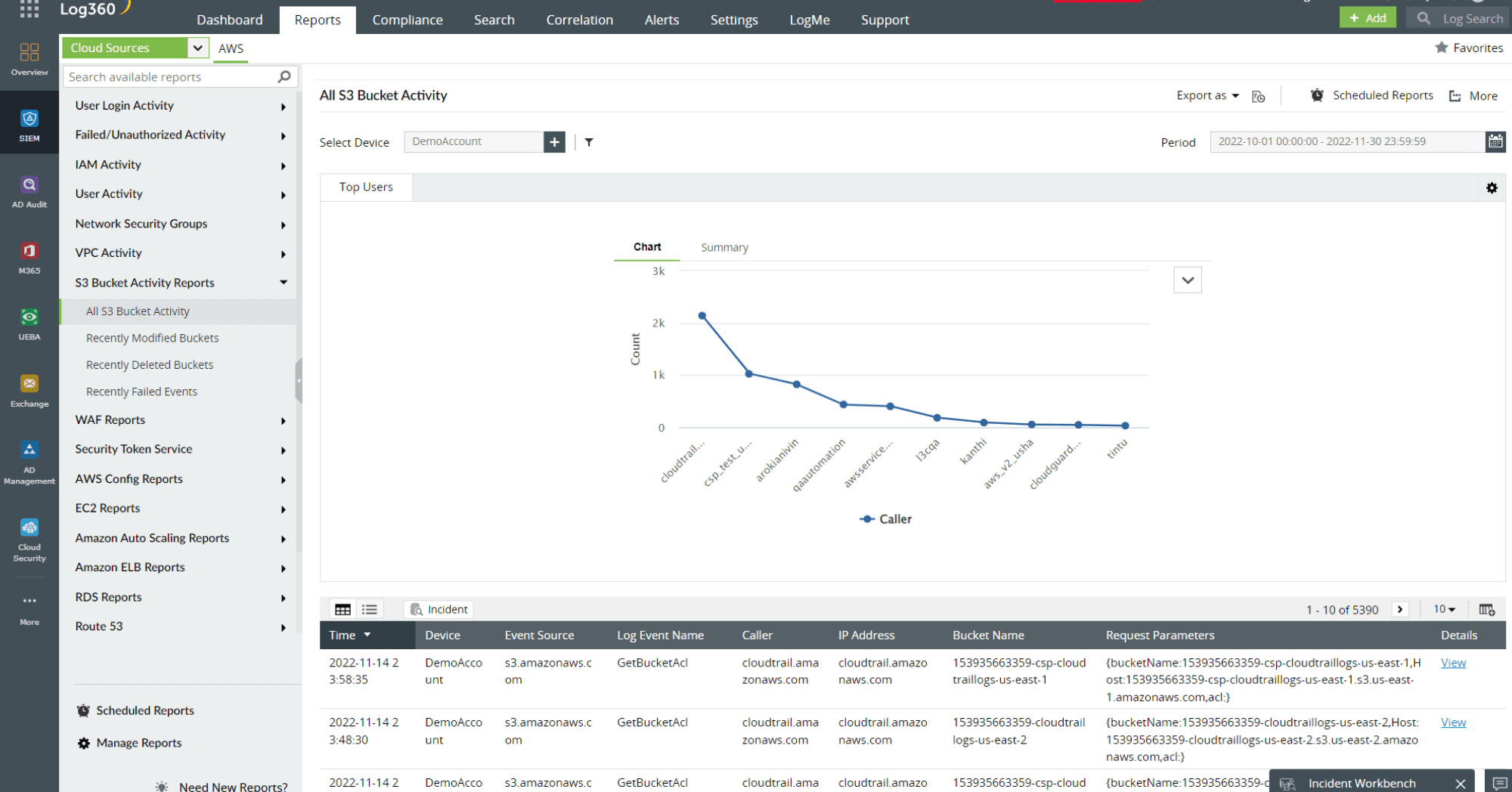
Figure 2: AWS S3 bucket activity report in Log360
3. Use Identity and Access Management (IAM): Implement IAM solutions for managing user identities, roles, and permissions. Ensure that users have only the permissions necessary to perform their tasks and regularly review and update permissions.
To maintain a safe cloud environment, IAM activities must be closely monitored. Vigilance helps to avoid security incidents, such as the unauthorized or unintentional creation of a privileged user with complete access to AWS resources
The out-of-the-box reports in ManageEngine Log360 provide a comprehensive picture of IAM activity, ensuring that no IAM activities go undetected. These reports document actions involving IAM users, groups, roles, MFA devices, and access keys.
IAM activity reports in Log360 includes the following information:
- When an event occurred
- Which user was responsible for an event
- The source IP address of the request
- The source region in which the event took place
- Request parameters
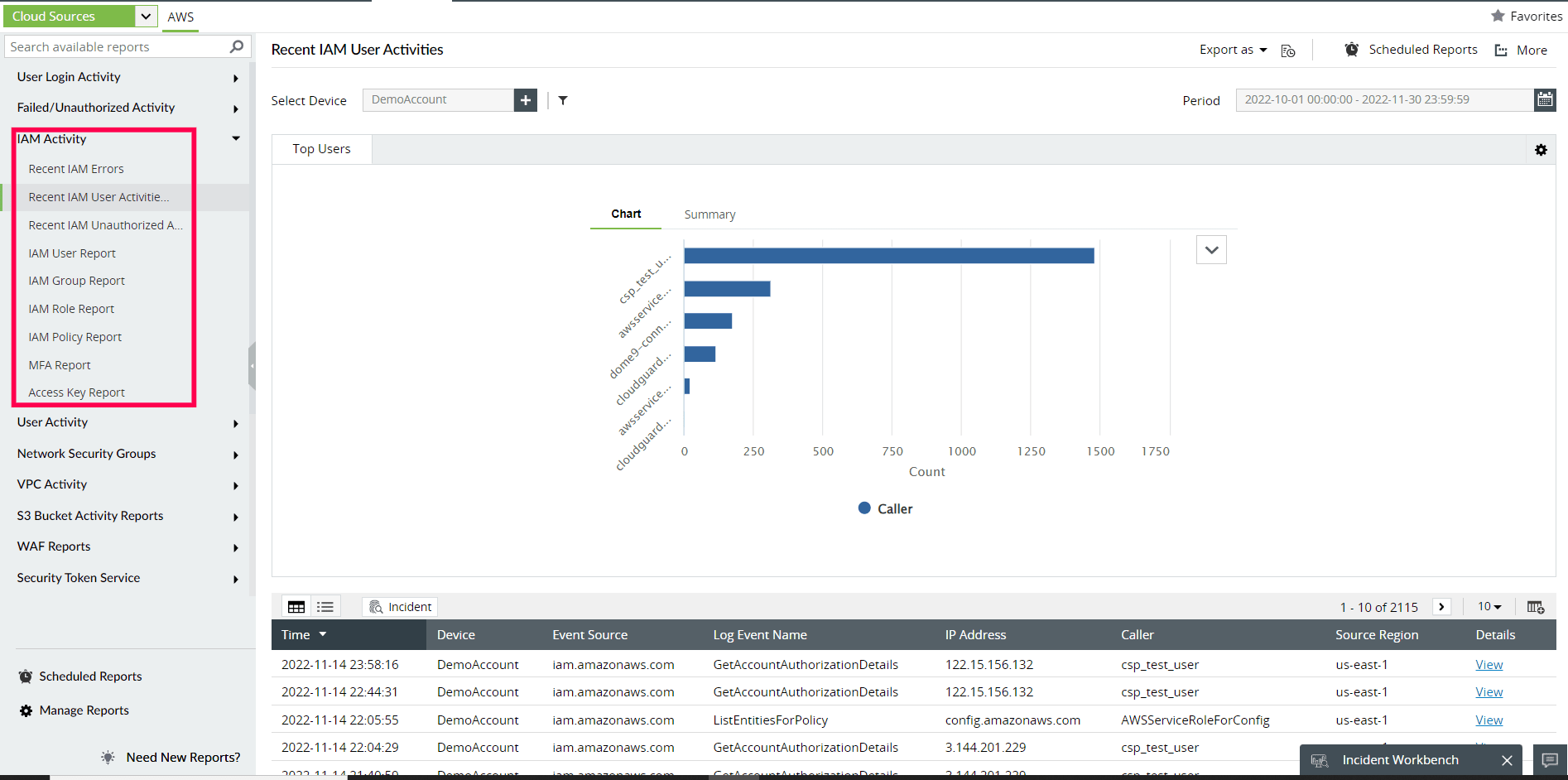
Figure 3: Cloud sources IAM Activity report in Log360
4. Encrypt Data: Encrypt data in transit and at rest to prevent unauthorized access. Use SSL/TLS encryption protocols for data in transit, and your cloud provider's encryption mechanisms for data at rest. CASB solutions can employ deep packet inspection (DPI) to securely analyze outbound HTTPS traffic. API-based CASB solutions analyze data at rest in cloud applications and can encrypt or revoke access to any sensitive data found that violates policy.
5. Utilize Network Security Controls: Use firewalls, intrusion detection/prevention systems, and web application firewalls to defend your cloud infrastructure against network-based threats. Segment your network to protect vital assets and restrict lateral movement in the event of a data breach.
ManageEngine Log360 generates thorough reports on actions performed on the cloud environment. The reports can be exported in CSV and PDF formats and also scheduled to be emailed at specific intervals for periodic review by the administrators.
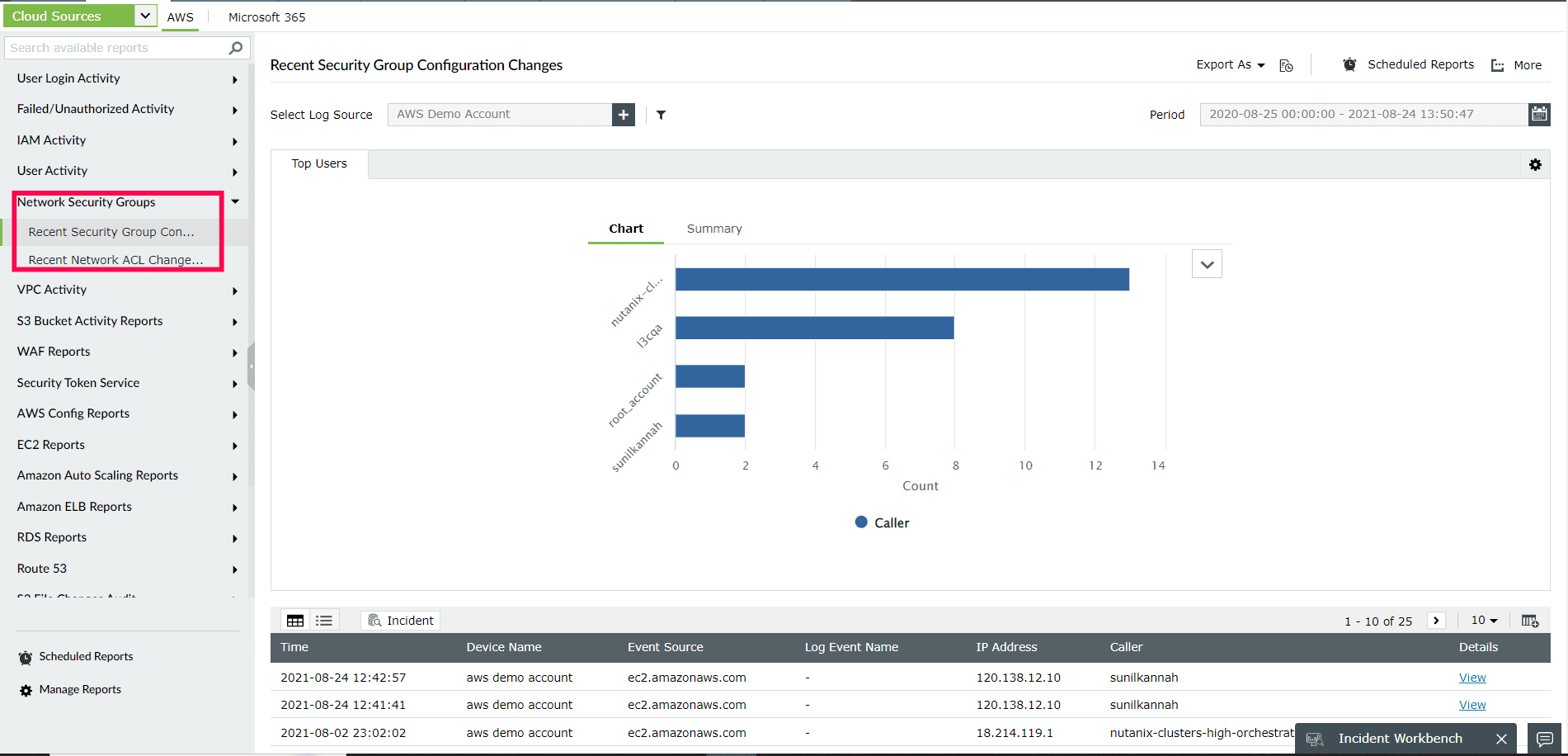
Figure 4: Network Security reports in Log360
6. Regularly update and patch: Update all software and programs with the latest security fixes. Cloud service providers issue patches to correct vulnerabilities on a regular basis; therefore, ensure that these fixes are applied as soon as possible.
7. Monitor for anomalies: Use security information and event management (SIEM) systems with UEBA capabilities to gather and analyze logs from various cloud sources to identify indications of compromise. These services provide continuous monitoring, threat detection, and mitigation for your cloud infrastructure.
Log360 detects anomalies by identifying suspicious changes in user activity. It assists you in identifying, qualifying, and investigating threats that would otherwise go undetected.
It provides detailed reports to assist in identifying anomalies in device and database activities. The anomalies are classified as time-based, count-based, or pattern-based.
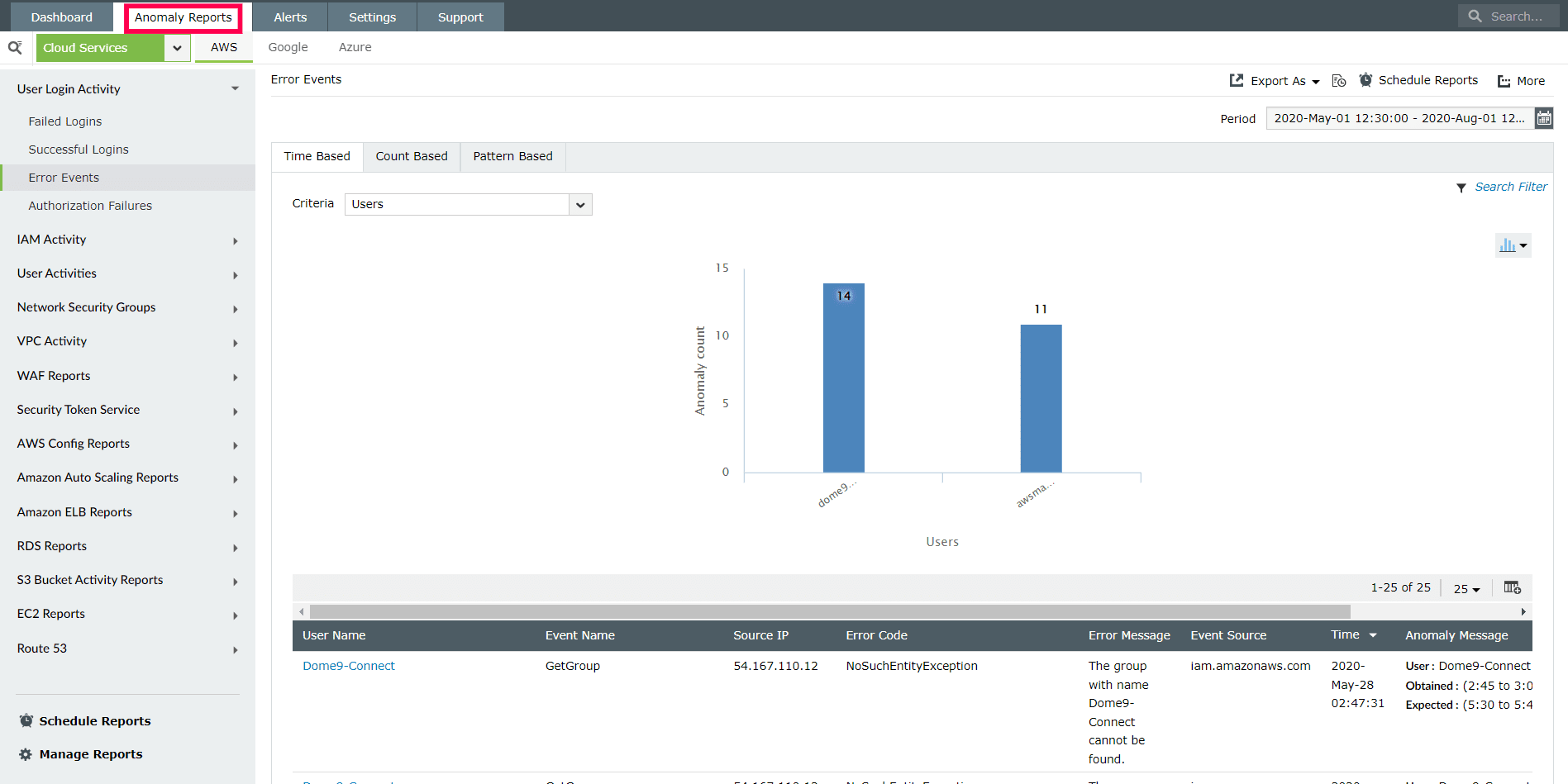
Figure 5: Anomaly reports in Log360
8. Conduct regular security audits and assessments: Conduct frequent security audits, vulnerability assessments, and penetration testing to uncover and correct flaws in your cloud infrastructure. This aids in proactively resolving security vulnerabilities before they are exploited by attackers.
A cloud access security broker (CASB) is a policy control and cloud visibility mechanism that sits between the cloud service users and the cloud applications. This software monitors all the activities that users do in the cloud and also enforces security policies. The CASB could either be an on-premises deployment or a Software as a Service application. A CASB can help a company monitor all user activity in the cloud. When a CASB is integrated with a SIEM solution, a security analyst can get deeper context surrounding a user’s cloud activity for an investigation.
For instance, you can conduct regular audits to discover risky shadow applications and monitor user activity with the help of Cloud access security brokers (CASBs).This can go a long way in helping admins by giving contextual information about the unsanctioned and unsafe cloud application used by employees, and file uploaded activities.
With ManageEngine Log360, you can monitor the use of cloud applications across your enterprise network, examine both successful and unsuccessful accesses to cloud applications with low reputation andlocate and block unnecessary or malicious websites.
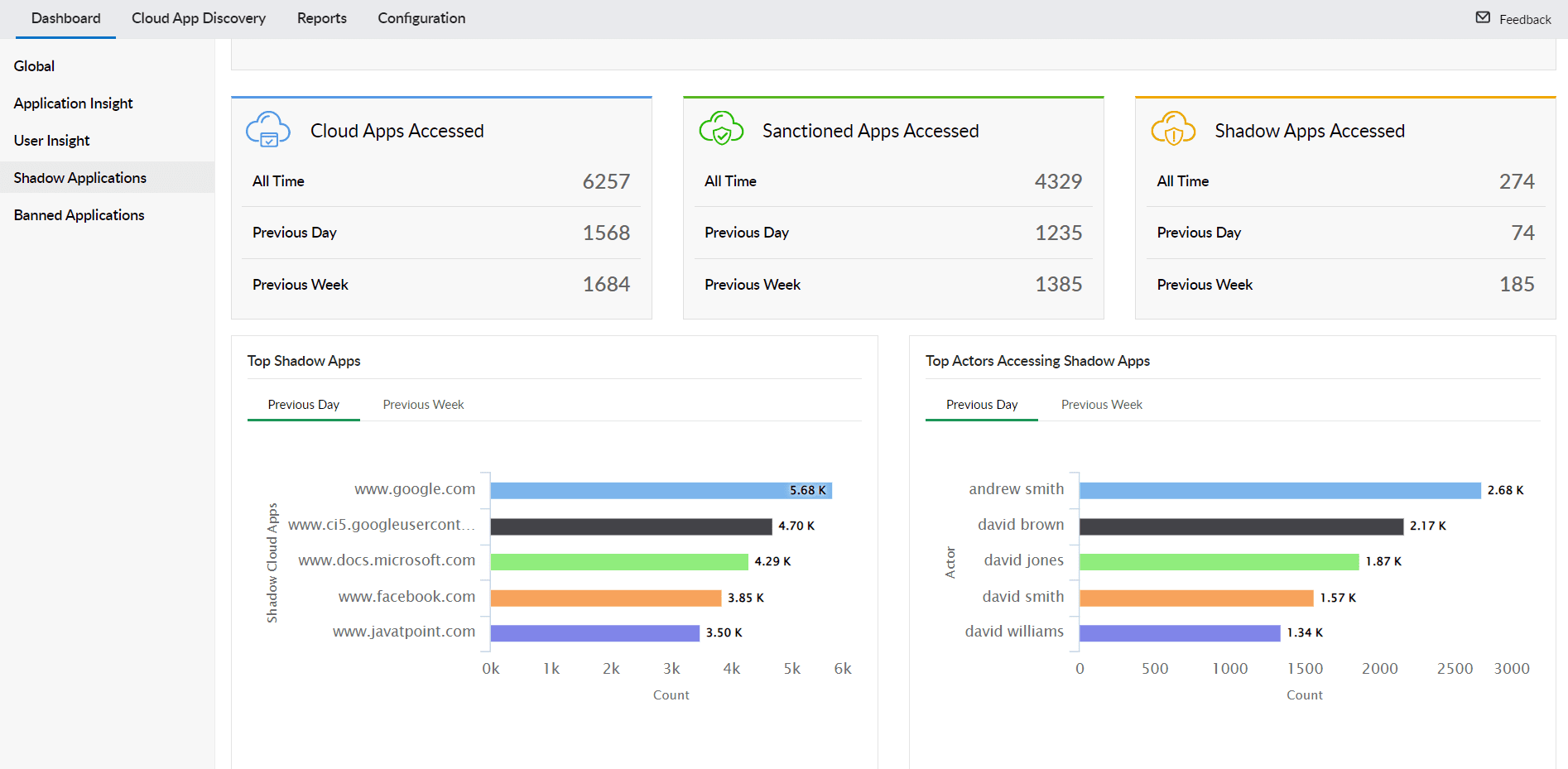
Figure 6: Shadow Application reports in Log360
9. Backup and Disaster Recovery: Implement a robust backup and disaster recovery strategy to ensure data integrity and availability in case of a security incident or data breach. Regularly backup your data and test your recovery procedures to ensure they work effectively.
10. Employee Training and Awareness: Educate employees on security policies so they understand the repercussions of their careless actions, and are more careful while using cloud apps. Also encourage openness, so employees share any incidents or errors committed, and the IT admins become aware of how employees use cloud apps.
No business can completely eliminate employee errors. However, transparency with the right technology is vital. Employees require leeway to use different cloud apps for productivity gains and, at the same time, security analysts need sufficient oversight to monitor the use of these apps to ensure security. It is imperative to achieve a perfect balance between the two.
11. Compliance and Regulations: Ensure that you adhere to applicable regulatory requirements and industry standards. Keep up with new compliance regulations and apply the required processes to ensure compliance.
ManageEngine Log360 provides audit-ready reports which enable organizations to fulfill the requirements of essential regulatory mandates like SOX, HIPAA, FISMA and the PCI DSS.
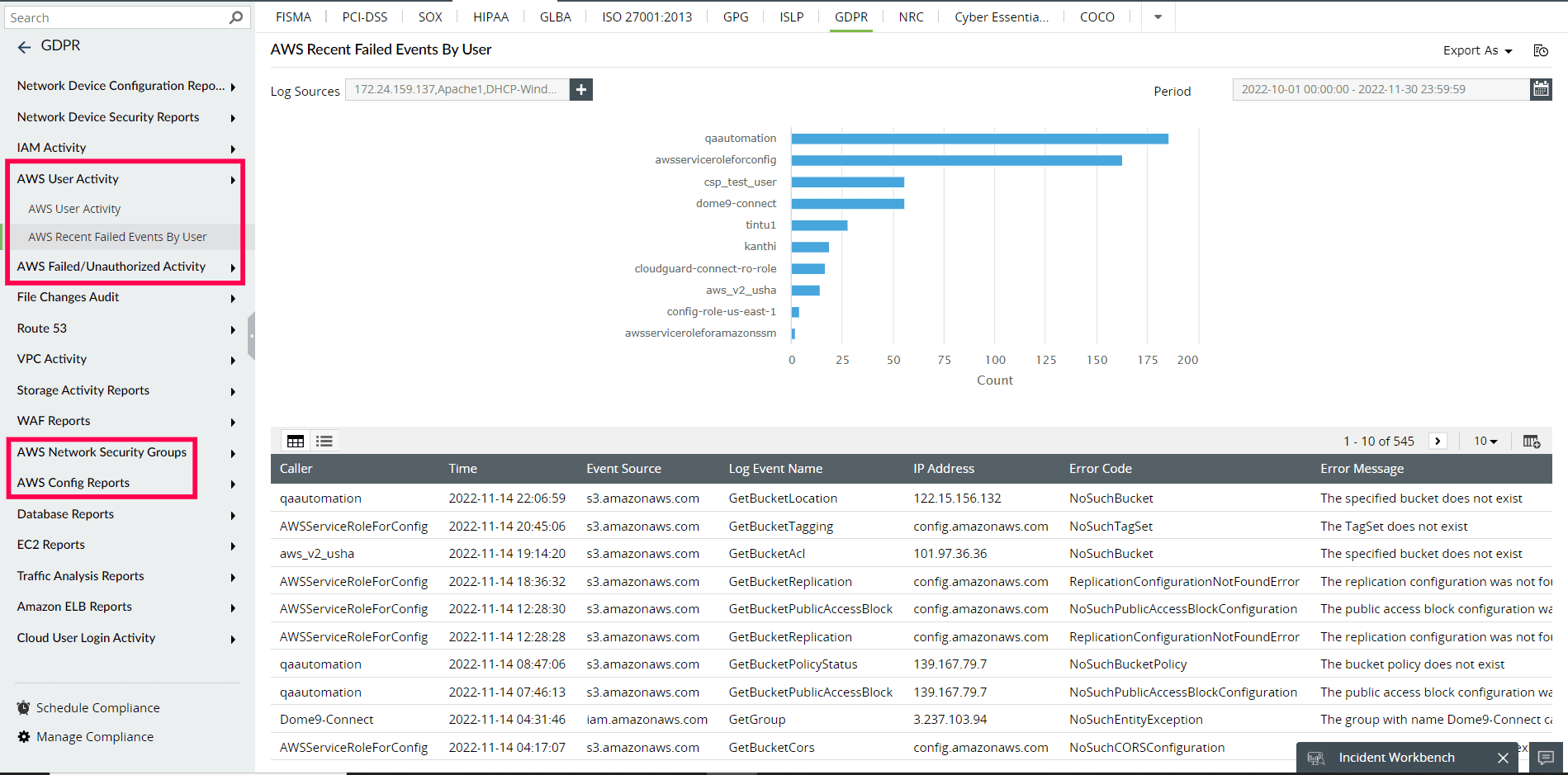
Figure 7: AWS reports in Log360
12. Vendor Risk Management: Evaluate the security posture of the cloud service providers and third-party suppliers you utilize to host or manage your cloud apps. Ensure that they follow industry standard security practicess and have appropriate security measures in place..
Implementing these 11 cloud security strategies will dramatically improve the security posture of your cloud evironment and reduce the danger of cyberthreats. However, it is critical to continuously analyze and change your security procedures to handle emerging threats and vulnerabilities.
13.Adopt a security framework, such as MITRE ATT&CK or NIST CSF: A security framework, such as MITRE ATT&CK or NIST CSF, can bring much-needed structure to building a security strategy. While the ATT&CK framework lets you know about the different kinds of adversary behavior you should be wary of, the NIST CSF provides effective guidelines to monitor, identify, and recover from incidents. Log360 is a MITRE ATT&CK integrated SIEM tool that enables you to monitor cloud activities with reference to the MITRE tactics and techniques and helps you proactively identify potential threats to cloud data. Figure 8 shows a MITRE ATT&CK report in Log360.
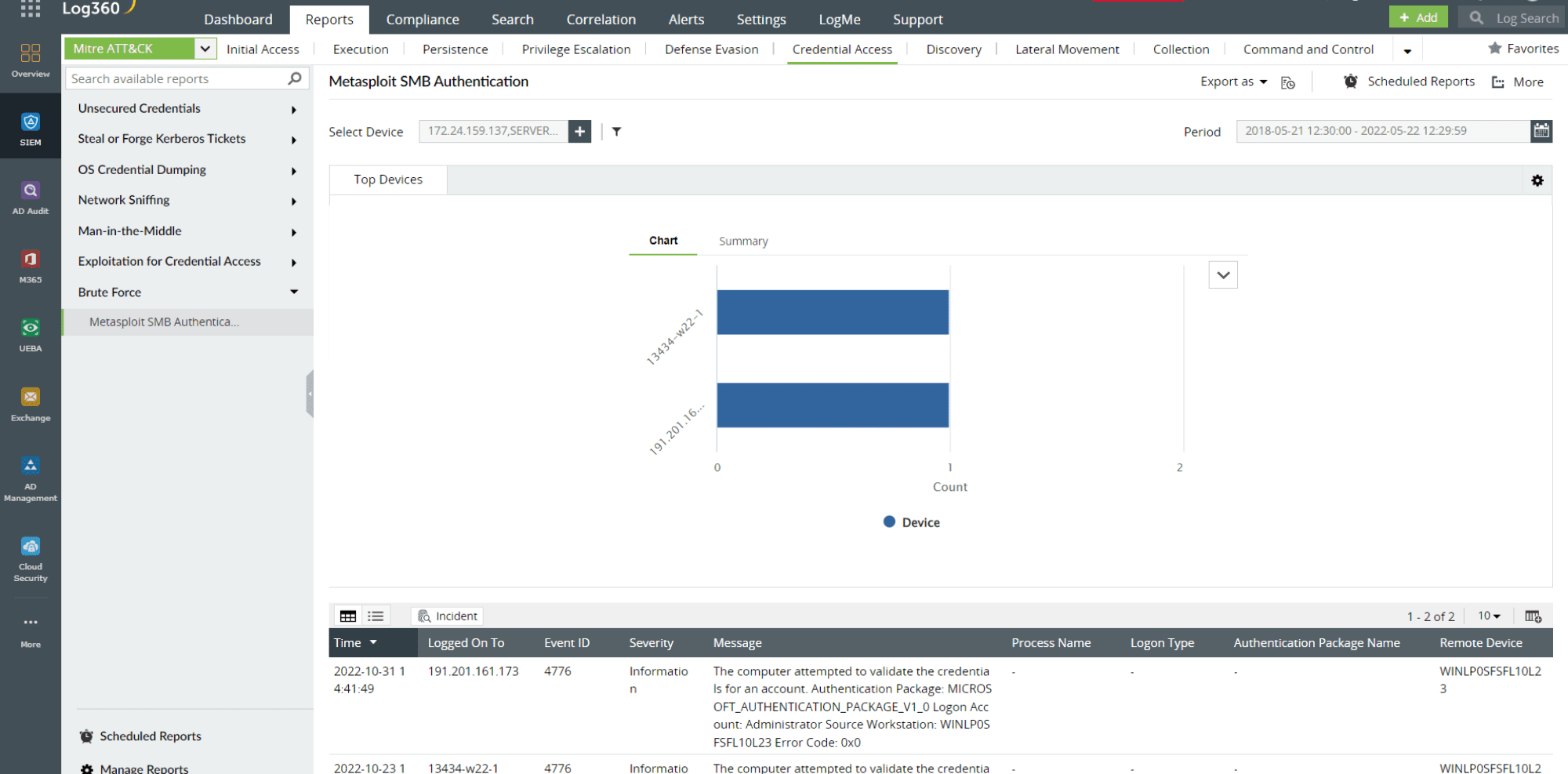
Figure 8:MITRE ATT&CK report in Log360
14. Gain visibility into all cloud activity: Most organizations around the world have adopted a multi-cloud strategy wherein they use cloud services from multiple vendors. This allows them to distribute their assets, data, applications, and storage across multiple hosting environments. While a multi-cloud strategy does have benefits, it also makes it harder for you to monitor what's happening across the cloud at any point in time. An effective security information and event management (SIEM) solution like Log360 that centralizes the information garnered from all cloud platforms and alerts security analysts in the event of a data breachis critical. Figure 9 represents an intuitive dashboard of all cloud activities in Log360.
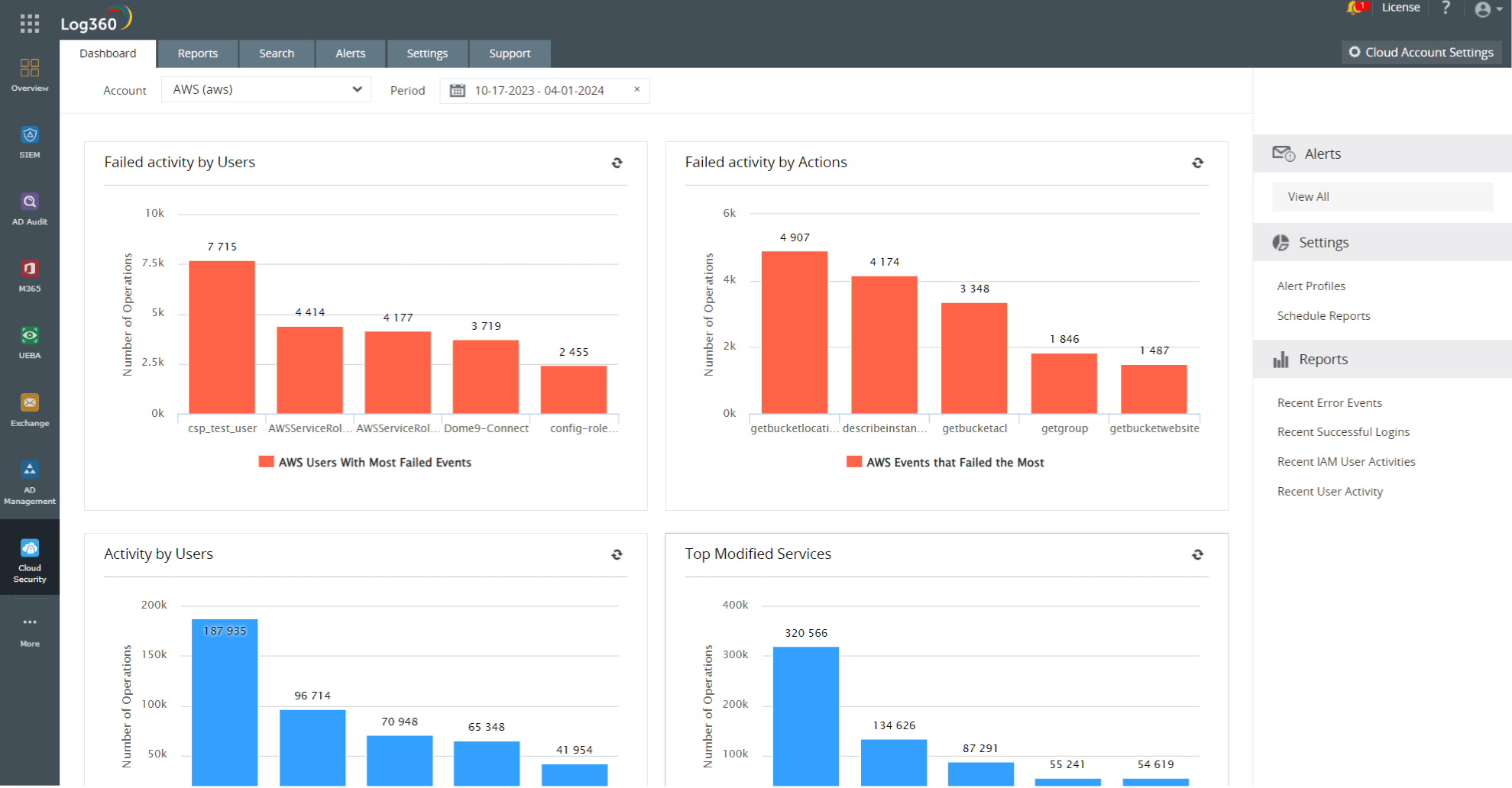
Figure 9:Cloud security dashboard in Log360
Ready for the next step?
Are you looking for ways in which you can protect your organization's sensitive information from being misused? Sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.
You can also explore on your own with a free, fully functional, 30-day trial of Log360.



