ManageEngine Key Manager Plus - Release Notes
Key Manager Plus 6680 (Minor) (August 2024)
New Feature
- GlobalSign Managed SSL
Key Manager Plus now supports GlobalSign's managed SSL services, revolutionizing the SSL certificate procurement process by utilizing pre-vetted domains to bypass traditional domain validation. This enhancement significantly accelerates certificate issuance, drastically reducing the time and effort required to procure SSL certificates for pre-vetted domains. By leveraging MSSL's pre-vetted domains, organizations can streamline their SSL management process, ensuring faster, more efficient, and hassle-free certificate procurement.
Enhancements
- Using the multiple server deployment type, certificates can now be deployed to the Microsoft Certificate Stores of agents using the From File option with a list of installed agents.
- From this build onwards, SSL certificates can be discovered from the Microsoft Certificate Stores of agents using the From File option with a list of installed agents during the regular discovery process or MS Certificate Store Discovery schedule.
- Earlier, the Key Manager Plus agent should have been directly installed in the Microsoft Certificate Authority server to perform the SSL-based operations from Key Manager Plus. From now on, it is sufficient to install the Key Manager Plus agent on any server, provided the server has access to connect to the MSCA server.
- We have introduced the Email field on the CSR creation form.
- Users can now import SSH keys in bulk, provided the keys are passwordless or share the same passphrase.
- SSH keys can now be created with rsa-sha-256 and rsa-sha-512 key types.
- SSH keys can now be exported as either a public key or a private key as required.
- Key Manager Plus can now parse version 3 PuTTY Private Keys.
- We have added a consent checkbox in the SDP and MDM configuration for accessing the LAN to connect to the services/servers running on the LAN.
- As a best practice and preventive security measure, we have disabled the autofill and password settings for the Key Manager Plus application login.
- Henceforth, the certificates' serial number details will be available for the certificates managed in the Certificate Authority - The SSL Store.
Bug Fixes
- Previously, the sync check status for SSL certificates deployed on servers via the Key Manager Plus agent was not functioning correctly in the multiple server window. This issue has now been resolved.
- Deploying certificates to the Microsoft Certificate Store using the Agent deployment type failed when the KeyStore password was blank. This issue has been fixed.
- In some instances, empty reports were generated during AWS discovery schedules or AWS certificate reports generation, even without active AWS credentials. This issue has now been resolved.
- An issue that affected the modification of schedules created with the SSL Discovery schedule type, using the discovery method From File, has been identified and fixed.
- When creating an Entrust certificate order using the Select CSR method, selecting a CSR with the KeyStore type set to KEY caused the certificate order to fail in the Key Manager Plus portal despite being created in the Entrust portal. This issue has now been fixed.
- When a certificate imported through an existing GlobalSign order is deleted from the SSL tab, the certificate order remains linked to the user who imports it to the Key Manager Plus repository. If another user attempts to import the existing orders using the identical GlobalSign credentials, they gain access to the certificate of the certificate order associated with the prior user. This issue has now been fixed.
- Previously, importing the existing orders from DigiCert failed, for instance, having more than 1000 orders. This issue has now been fixed.
- An issue that led to the failure of the Failover Service configuration has been found and fixed.
Security Fix
- We have added a few fixes for the prevention of Server Side Request Forgery and the usage of the static variable.
Key Manager Plus 6675 (Minor) (June 2024)
Enhancements
- Key Manager Plus now records user login and logout events, enabling administrators to export the recorded data as User Access Reports and schedule automated exports for streamlined auditing and monitoring purposes.
- Administrators can now create a certificate group with digital certificates while adding them into Key Manager Plus via a Keystore file, enhancing flexibility in certificate group management.
- Users can now seamlessly export certificates in a certificate group as a Truststore with a secured Truststore password.
- Users can now view the key usage and extended key usage parameters associated with an SSL certificate during its creation on the Certificate Details Page.
- From now onwards, the SSL certificate expiry information received through SSL certificate expiry notifications or SSL expiry schedules will be organized with the nearest expiry date.
Bug Fixes
- Previously, when an administrator disabled the user password field in the Export Settings, it impacted all users and prevented them from exporting data with a custom password. Key Manager Plus now enables administrators to disable the custom export password option for themselves without affecting other users.
- Previously, separating the SSL certificate description by lines caused data misalignment and broken lines in the CSV file during export. This issue has now been resolved.
- An issue that prevented users from importing and associating a private key (created without DES encryption in OpenSSL) with an existing SSL certificate in the repository has been identified and resolved.
- Previously, when editing a schedule for the SSL Certificate Report that included certificate groups, the certificate group details were not displayed on the edit schedule page. This issue has now been resolved.
- An issue that prevented users from updating additional fields for certificate groups created using the criteria 'Issuer' and 'AWS Services' has been identified and resolved
- Previously, SSL power users with multiple certificate groups could only update additional fields for all groups collectively, not individually. This issue has now been resolved.
Key Manager Plus 6671 (HotFix) (May 2024)
Bug Fixes
- The Key Manager Plus agent of build 6670 could be installed on different resources using a single agent installation key. This issue has now been fixed.
- We have identified and resolved the following issues within the 'Multiple Server' window:
- The 'AutoDeploy on Renewal' was disabled for the certificates, even though they were configured with 'Deploy Certificate to All Servers on Auto-Renewal.'
- The 'Valid To' column failed to reflect the updated expiry date for the auto-deployed certificates upon renewal.
- An issue that prevented the Operators from connecting to the IIS server and performing any IIS Binding-related operations has been identified and resolved.
- Previously, importing data into Key Manager Plus using CSV files failed in certain cases. This issue has now been fixed.
- In build 6670, the certificate orders were not listed in the 'Auto-Renewal' tab for all public CAs except Entrust. This issue has now been resolved.
- Previously, when an administrator exported reports and other files by setting a user password, the User Password field in the Settings > Privacy Settings > Export Settings tab displayed the Undefined error when other administrators accessed the same field. This issue has now been resolved.
- During the certificate export process, the SSL certificate report was inadvertently exported instead of the SHA-1 certificate report. This issue has now been resolved.
Security Fixes
- A vulnerability (CVE-2024-21733) that could have led to the inadvertent exposure of sensitive information through error messages has been fixed.
- In this build, the following vulnerabilities, Horizontal Privilege Escalation (ZVE-2024-3697) and Vertical Privilege Escalation (ZVE-2024-3700), which might have allowed unauthorized access, have been identified and fixed.
Key Manager Plus 6670 (Minor) (Apr 2024)
Enhancements
- Key Manager Plus now supports the auto-renewal process for domain-validated certificates from the Entrust certificate authority. Thus, allowing administrators to streamline the Entrust certificate renewal capability in an automated manner from SSL >> Entrust >> Manage >> Auto-Renewal.
- New RESTful API: Introducing a new REST API - Update Additional Fields - to update the additional fields associated with the SSL certificates stored in the Key Manager Plus repository.
Bug Fixes
- From build 6651, selecting a sub-organizational unit directly during the user import process from Active Directory failed. This issue has now been resolved.
- Previously, deploying multiple SSL certificates on Windows servers using a CSV file, failed in some instances. This issue has now been fixed.
- From build 6650 onwards, ordering, renewing, or reissuing an Entrust certificate order using a CSR from Key Manager Plus without an associated keystore resulted in creating an order in Entrust and not being reflected in Key Manager Plus. This issue has been rectified in this update.
- From build 6660, certificate operations in public CAs involving the import of CSR and private key files failed. This issue has now been fixed.
Key Manager Plus 6660 (Major) (April 2024)
Enhancements
- Key Manager Plus now facilitates the discovery and inclusion of certificates deployed within Citrix LoadBalancer, leveraging certificate details as Keyvault data without exposing sensitive certificate information.
- Previously, users had to input the keystore password manually for every JKS/PKCS certificate identified via the load balancer to include them in the SSL certificates tab. With the recent update, users can streamline this process by adding the required keystore passwords in a file formatted with commas and parsing them to the JKS/PKCS certificates.
- Key Manager Plus now supports HTML report format for SSL expiry schedules, providing users with more versatile reporting options.
- We have introduced the Subject Key Identifier (SKI) and Authority Key Identifier (AKI) values in the certificates signed by the root (i.e., Private CA) and SKI values in the certificates that are self-signed.
- ACME Providers in the Settings >> SSL section will now list all available default ACME providers. In addition, from now on, modifying the Directory/Staging URL for any new changes will retrieve all the updated URLs relevant to the ACME operations.
- The expiry date format in the email received for SSL expiry notification has been modified for quicker readability.
REST API
- A new REST API named 'Export CSR' enables the export of all available CSRs in the Key Manager Plus repository
- The private key filter can now be used as the filter in input data for the 'Get all Certificates' API. In addition, the description field of the certificates is added to the API response.
Bug Fixes
- Duplicate entries appearing in the SSL tab when importing or rediscovering server certificates have been resolved.
- The issue causing duplicate MSCA certificate entries in the SSL tab has been fixed.
- Using the additional field as a criterion for grouping the SSL certificates resulted in an issue with sending expiry notification emails to the specified group emails. This issue has been rectified, ensuring seamless notification delivery.
- Previously, when an additional field was created and used as a criterion for grouping the SSL certificates by an administrator, the SSL expiry email was exclusively dispatched for the certificates owned by the administrator and not for the certificates that are owned by other administrators. This issue has now been mitigated.
- All active and expiring domains are now selectable while creating, renewing, or reissuing an order in Entrust.
- An issue that prevented administrators from viewing the Entrust orders created by other administrators has been fixed.
- The incorrect port number issue in the URL sent via email to reset Two-Factor Authentication has been fixed.
- Importing and exporting private keys with the EC algorithm has not worked as intended. This issue has now been fixed.
Security Fix
- Several internally identified vulnerabilities have been addressed in this release to enhance Key Manager Plus security.
Key Manager Plus 6653 (Hotfix) (Mar 2024)
Bug Fix
- An issue that caused the unexpected termination of the connection between Key Manager Plus and Azure, hindering the retrieval of relevant API responses, has been identified and resolved.
Key Manager Plus 6652 (Hotfix) (Feb 2024)
Bug Fix
- Previously, in some instances, the private key exported from the certificate provided by Entrust CA via Key Manager Plus was not the same as that provided by Entrust CA. This issue has now been fixed.
Key Manager Plus 6651 (Hotfix) (Feb 2024)
Bug Fixes
- Previously, in a few instances, an SSL certificate expiry email has been sent to the users without any information on it. This issue has now been fixed.
- We have found an issue where duplicate entries were added to the certificate group when an existing certificate was rediscovered with the 'Group Certificates By CommonName' option enabled. This issue has now been resolved, and duplicate entries will no longer be added.
Security Fixes
- An OpenSSH vulnerability (CVE-2023-48795), which might have allowed unauthorized access and data manipulation, has been prevented by updating third-party jars.
- We have identified and resolved a vulnerability that resulted in stored Cross-Site Scripting (XSS) while fetching groups and organization units from the Active Directory.
Key Manager Plus Release 6650 (Major) (Jan 2024)
New Feature
Entrust CA Integration
- Enhancing its capabilities, Key Manager Plus has integrated with Entrust Certificate Authority, a leading player in certificate solutions for SSL/TLS certificates and digital identities. With this integration, users can efficiently request, acquire, import, deploy, reissue, and renew certificates issued by Entrust directly from the Key Manager Plus web interface. Simplify the end-to-end lifecycle management of SSL/TLS certificates by exploring the SSL >> Entrust section.
Public CA Auto-Renewal
- Introducing an enhanced feature in Key Manager Plus - auto-renewal capabilities for domain-validated certificates obtained from third-party certificate authorities like GoDaddy, GlobalSign, AWS, Sectigo, and more. Now, automating the certificate renewal process is seamless. Enable the auto-renewal capability from the respective CA tab to initiate automated renewal tasks based on the provided certificate requirements. To experience this efficiency, navigate to SSL >> CA Tab >> Manage >> Auto Renewal and streamline your certificate renewal process effortlessly
Enhancements
- As a part of this release, the PostgreSQL server has been upgraded from version 10.18 to 14.7 for the Key Manager Plus 64-bit architecture.
- The CSR parser field in the Tools section has been introduced now with the email attribute field.
- We have introduced a new report named Private CA Report in the Reports >> SSL section. The report benefits the user by providing insights into the number of end-user certificates or intermediate certificates signed by the Private CA.
New RESTful APIs
- Revoke MSCA Certificate - To revoke an MSCA certificate when shown a sign of a compromised private key.
- Fetch Unmanaged Certificates from a Load Balancer or Shared Path - To fetch the discovered and unmanaged certificates of format JKS/PKCS from a load balancer or shared path.
- Import the Fetched Unmanaged Certificates from a Load Balancer or Shared Path - To import the fetched unmanaged certificates of format JKS/PKCS from a load balancer or shared path into the Key Manager Plus.
Bug Fixes
- We have resolved an issue in the scheduled SSL Expiry reports in PDF. Previously, when enabled with the 'Include multiple servers list for certificates' option, handling extensive rows of multiple servers led to the failure of generating reports.
- Fixed an issue where uploading an IIS binding file across multiple servers with an empty bind hostname was not allowed. This restriction has now been resolved.
- We have fixed the bug preventing email notifications for Schedule Names containing the character '\'.
- Previously, when utilising the RESTful API to sign a CSR in Key Manager Plus, failures occurred when the template name had case-sensitive or space-sensitive differences. This issue has now been resolved.
Security Fixes
- We have enhanced the security of the Key Manager Plus library by upgrading the jar components to their latest version identified internally, mitigating the risk of vulnerabilities.
- We have successfully addressed an issue that resulted in the exposure of the PostgreSQL database password within the database_params.conf file between the Key Manager Plus installation and server initialization process.
- The security issue (CVE-2023-6105) that could have led to the inadvertent exposure of sensitive information to low-privileged OS users with access to the host through improperly configured installation directory permissions has been discovered and resolved.
Key Manager Plus Release 6620 (Nov 2023)
New Feature
Configurable ACME
- Key Manager Plus now supports adding ACME providers for the effective automation of certificate lifecycle management. Just like its integration with renowned certificate authorities such as Let's Encrypt, Buypass Go SSL, and ZeroSSL, which offer automated SSL/TLS certificate management, Key Manager Plus now have the flexibility to incorporate other ACME service providers. To do this, navigate to Settings >> SSL >> ACME Providers This empowers efficient certificate management with automated precision.
Enhancements
- In this release, we have expanded the available drop-down menu options for Additional Fields to five, providing users with four additional drop-down menus for increased versatility.
- RESTful API Changes - We have introduced a new RESTful API - Get SSH Key Passphrase, which allows the retrieval of the passphrase of SSH keys.
- From now onwards, the SSL Expiry Report data will be sorted based on the expiry date.
- We have introduced two additional certificate conversion formats in the Tools section, now supporting the conversion from Java KeyStore (.jks) to Privacy Enhanced Mail (.pem) and vice versa.
Behavioral Change
- The response format of the Get Certificate Private Key Passphrase RESTful API has been modified for quicker interpretation of results.
Bug Fix
- Earlier, certificates could not be created with multiple organizations and organization units. This issue has been fixed.
- Previously, IIS binding failed with SHA256 SSL fingerprint enabled. This issue has now been fixed.
- Previously, saving IIS binding updated other rows with incorrect values under 'Settings' >> 'SSL' >> 'IIS Binding'. This issue has now been fixed.
- Earlier, the self-signed certificates that are auto-renewed accumulated over the new discovery list. This issue has been fixed.
- In prior versions, when the SAN field in the CSR request page included an IP address, it was not appearing in the SSL parser or the SSL certificate details page. This issue has been rectified in this update.
- In previous versions, after certificate renewal, auto-deployment to MS Store failed in a few cases. This issue has been fixed now.
Security Fixes
- In this release, we have addressed a few vulnerabilities identified internally.
Key Manager Plus 6610 (September 2023)
Bug Fixes
- A problem that prevented creating Private CAs with the Key Algorithm types EC and DSA has been resolved.
Security Fixes
- A stored XSS vulnerability caused by the Key Name parameter after associating a key via Public Key Association has been fixed.
- We have fixed a Remote Code Execution (RCE) vulnerability that allowed the adversary to execute the arbitrary command on the Windows machine via the Key Manager Plus agent.
Key Manager Plus 6600 (Major) (August 2023)
New Features
- Private Certificate Authority (CA) / Intermediate CA
Key Manager Plus now offers a new feature - Private CA (Intermediate CA) that allows organizations to create and manage their certificates internally. Selected users can sign end-user certificates for internal servers, applications, and services using the intermediate certificate, signed using the root certificate.
With this feature, organizations can:
- Achieve enhanced security and gain more control over their certificate management process without relying on external CAs.
- Minimize the risk of external threats and improve their overall certificate management process.
- Streamline the process of issuing and revoking certificates while maintaining complete control over their certificate authority, thus ensuring the certificates issued by the organization are trusted and secure, making it easier to manage and monitor all the internal certificates in one central location.
- Jenkins Integration with Key Manager Plus
Jenkins is an open-source automation server that facilitates Continuous Integration (CI) and Continuous Delivery (CD) of software projects. Key Manager Plus now supports integration with Jenkins which provides SSL certificates support that includes creating CSR, downloading CSR, creating a certificate, and downloading certificates for organizations' freestyle projects during the build generation and post-build process. With this plugin in DevOps, one can attain certificate-related capabilities in the automated schedules run through Jenkins.
- Azure Key Vault - TLS Secrets Management
Key Manager Plus now allows you to manage the TLS secrets stored in the Secrets of Microsoft Azure Key Vault - a management service offered by Microsoft. Through this integration, users can create (PFX format), renew, and manage the entire lifecycle of SSL/TLS certificates stored in the Secrets of Azure Key Vault via Key Manager Plus by importing them into the Key Manager Plus repository.
Enhancements
- From now on, Key Manager Plus supports DNS Made Easy to complete domain control validation while acquiring certificates from public Certificate Authorities, alongside the available DNS support types.
- New RESTful APIs: The following three new REST APIs have been introduced in Key Manager Plus:
- Fetch all SSH Resources - To fetch all SSH resources
- Fetch all Audit Details -To get all the audit details
- Bulk SSL Discovery from a File - Performs resource discovery based on DNS names stored in the files
- Get SSL Vulnerability Count - To get the total number of SSL vulnerabilities
- Previously, the CSRs were signed in REST API using MSCA. From now on, either MSCA or root CA can be used to sign the CSRs, and in addition, the API response will display the certificate serial number for further API-related use.
- From this build onwards, additional field data can be added as a dropdown option by giving the values to be displayed in DropDown Field type in Settings >> Additional Fields.
- From now on, the 'Certificate Details' will show the additional field(s) information related to the SSL certificates in the SSL tab.
- From now on, you can create CSR by importing the KeyStore file from the Key Manager Plus SSL repository instead of exporting them locally and importing them back for CSR creation.
- In addition to the JTDS JDBC driver, Key Manager Plus now supports Microsoft Java Database Connectivity (JDBC) driver to connect to the SQL server, thus enhancing the user's connectivity to the SQL data.
- We have introduced a new global search filter that allows users to search for resources based on their DNS/IP addresses.
- From now on, Key Manager Plus will record all the SSL discoveries performed via public Certificate Authority (CA) integrations from the Audit window.
- We have introduced a new PKCS 8 export type in this release that permits additional exportation capabilities.
Upgrade
- We have migrated to the OpenJDK version 1.8.0_372 for the 64-bit supported builds. For the 32-bit build users to use this upgrade seamlessly, please migrate to the 64-bit architecture.
Note: TLS protocol version 1.2 or higher is required for SQL server connections, as this OpenJDK upgrade disables TLS1.0 and TLS1.1 by default.
UI Change
- From this build onwards, the personal key storage of Key Manager Plus will be referred to as 'Key Vault' instead of 'Key Store' to avoid misinterpretation between the internal KeyStores.
Bug Fixes
- The revoked status of the certificates was still showing even after the renewal of revoked certificates in MSCA. This issue has been fixed now.
- In builds 6450 and 6500, the mail-server configuration did not get saved properly because of the presence of the '&' character in the mail server fields, which triggered an EXTRA_PARAM_FOUND error in the user interface. This issue has now been fixed.
- An issue that denied the remote connections for machines with OpenSSH version 7 & above using SSH key authentication has been found and fixed.
- Previously, the load balancer discovery schedule failed when specified with a port number during the schedule configuration. This issue has now been fixed.
- From build 6450, for users with the Microsoft 365 GCC High subscription, the mail server settings failed to work using OAUTH, as the OAUTH mail server setting failed to support US-specific subscriptions. The issue is now fixed.
- From build 6210, while signing a CSR with a certificate, SHA256 was being used as the default signature algorithm instead of the signer certificate's signature algorithm. This issue has now been fixed.
- Previously, the Subject Alternate Name that contains a Principal Name faced a parsing issue during the certificate operations. This issue has now been fixed.
Key Manager Plus Release 6500 (Major) (April 2023)
New Features
- Kubernetes Integration
We have introduced Kubernetes (K8s) integration, an open-source platform that automates containerized application deployment, scaling, and management. Kubernetes secrets, a feature provided by the Kubernetes platform, facilitates a secure way of storing Kubernetes TLS secrets (certificates) within Kubernetes clusters.
The integration aids the administrator in securely fetching the Kubernetes TLS secrets (certificates) into Key Manager Plus, managing them within the single centralized repository, and rotating/updating the secrets obtained from multiple Kubernetes clusters.
Navigate to 'SSL >> Kubernetes' to configure and manage all your Kubernetes TLS secrets (certificates) via Key Manager Plus.
- New User Role - SSL Power User
We have introduced a new static custom role - SSL Power User. Users designated with this role will have elevated privileges to perform complete SSL certificate management capabilities.
Enhancements
- As a part of this release, Digicert is added as a vendor to the SSL Store list. The previously available SSL Store vendors, which include Thawte, Geo Trust, and Rapid SSL, will now be a part of Digicert.
- It is now possible to add an email address while configuring 'Certificate Sync Status Check' from 'Settings >> SSL >> Certificate Sync Status'. Once added with the configured recurrence time interval, the list of all the SSL certificates with their deployed servers will be sent to the given email address, with the following details: days to expire, date of expiry, serial number, and fingerprint.
- Henceforth, while creating a Certificate Signing Request (CSR), only the Common Name, Validity, and Store Password will be the mandatory fields.
- We have added the following additional key sizes to the key algorithms for increased security strength:
- 3072 and 4096 key sizes for RSA
- 2048 and 3072 key sizes for DSA
- Key Manager Plus now supports SHA256 SSL fingerprint to encrypt the SSL certificates. Administrator can navigate to 'Settings >> SSL >> SSL Fingerprint' to change their SHA values. All the existing certificates can also be changed to SHA256 fingerprint by enabling the checkbox provided.
- From now on, the dashboard on the Key Manager Plus homepage will not consider the EC certificate key size into account for the 1024-bit and lesser keys calculation.
Bug Fix
- Previously, when an administrator tried to rediscover the certificates in an organization, it failed with an empty error message. This issue has now been fixed.
Security Fixes
- A Remote Code Execution (RCE) vulnerability reported on the SSH server by passing malicious links has been fixed.
- An issue that allowed the users with the Operator role to access the server with the pre-opened terminal even after revoking the permission has been found and fixed.
- A stored XSS vulnerability caused by an image uploaded during the rebranding of Key Manager Plus has been found and fixed.
Key Manager Plus Release 6450 (Feb 2023)
New Features
- SMTP OAuth Authentication
Key Manager Plus now supports OAuth authentication for SMTP-based email communications to provide a secure channel for outbound emails from Key Manager Plus. With this, users can configure OAuth from Google or Microsoft Exchange Service as their mail server to send email notifications from Key Manager Plus. This process eliminates the need for the users to provide account credentials to authenticate the notification emails.
- Server Certificates in Centralized Repository
Users can now maintain server certificates in the Key Manager Plus' centralized SSL repository without affecting the available number of keys in the license.
- FortiGate Firewall Discovery and Deployment
Using Key Manager Plus, users will now be able to discover certificates from the FortiGate Firewalls. Users can also add and manage multiple FortiGate Firewall accounts and deploy certificates to them individually.
Enhancements
- A new option provided under 'SSL >> Certificates >> Multiple Servers' allows users to add additional fields, such as character, date, and email, in the Multiple Servers page.
- New REST API: In this release, we have added a new REST API - Import CSR, to import the Certificate Signing Request (CSR) by providing valid information.
- It is now possible to include the multiple server lists of the SSL certificates in the notification email of the SSL expiry schedule.
Bug Fixes
- Previously, the SSH and SSL discovery (including scheduled discovery) results included the IP address(es) provided in the 'Exclude IPAddress' field. This issue has now been fixed.
- Earlier, the certificate requests raised by a user was accessible to all other users with the operator role. From now on, the certificate requests will be accessible only to the administrators, apart from the users who created them.
- In the notification policy, email notifications pre-configured by administrators for the certification expiry, were sent at configured intervals without the subject or details. This issue has been fixed now.
- Previously, the IP and the DNS fields had similar entries when an IP was not resolved into DNS, thus creating duplicate entries on the multiple server page. We have fixed this issue now.
- In the notification policy, email notifications pre-configured by administrators for the expiry of PGP keys, were sent at configured intervals without the subject or details, even when no PGP keys were present. This issue has now been fixed.
- Earlier, in addition to the latest version, .Net Framework version 3.5 was required for IIS binding. From now on, any .Net Framework version above 4 will be sufficient to bind a certificate to a website in IIS.
- Previously, adding or updating the schedules used the client machine's date instead of the server's. We have fixed it now in this release.
- An issue that led the SSL discovery to fail with an exception message - 'certificates do not conform to algorithm constraint' has been fixed.
- There was an issue fetching some columns from the ServiceNow help desk that appear under 'Settings >> Ticketing system'. This issue has been fixed now.
Key Manager Plus Release 6420 (Nov 2022)
Enhancement
- Certificate Discovery using 'File' option for Microsoft Certificate Store
Key Manager Plus now supports file-based certificate discovery for the Microsoft Certificate Store. This feature allows you to import a text file with a select list of hostnames/IP addresses that are accessible to Key Manager Plus, using which the remote machines are scanned and certificates are discovered. After a successful discovery, Key Manager Plus will consolidate the newly-discovered SSL certificates in its certificate repository. In addition, scheduled discovery of Microsoft Certificate Store certificates now comes with two new options: discovery using IP range and via a text file.
Bug Fixes
- From build 6400 onwards, when users tried to add a new SSL certificate with the same common name as another certificate that was already available in Key Manager Plus, the new certificate was not added to the repository. This issue has been fixed.
Key Manager Plus Release 6401 (Hotfix) (Oct 2022)
Bug Fixes and Enhancements
- Some bugfix and enhancements have been done.
Key Manager Plus Release 6400 (Oct 2022)
New Feature
- Importing Certificate Details
In addition to adding certificate objects in different formats, Key Manager Plus now allows users to manually add certificate details into the Key Manager Plus repository and manage them along with other certificate objects. This feature is beneficial when a user has the details of an SSL certificate that resides in a demilitarized zone and therefore cannot be added to Key Manager Plus as an object through discovery. In this case, users can create a CSV file with the specified certificate details and upload them to Key Manager Plus. Furthermore, users can also set up expiry notifications for certificate details.
- Certificate Deployment to Citrix ADC Load Balancer
Users will now be able to deploy SSL certificates to the Citrix ADC load balancer directly from the Key Manager Plus interface. Users can add and manage multiple Citrix accounts and deploy certificates to them individually.
Enhancement
- From now on, users can set a time-out value while configuring Radius Server Authentication. During authentication, if no response is received from the Radius Server within the timeout interval, the authentication will fail.
- Henceforth, users will be able to associate columns from ServiceNow with the columns from 'SSL >> Certificates' tab to add additional information to the tickets.
- Earlier, Digicert users were able to add only one API key to Key Manager Plus. Henceforth, they can add multiple API keys to Key Manager Plus.
- Two new RestAPIs to 'To get Certificate in different file formats' and 'To Export an SSH Key in a specific Key Type' have been added.
Bug Fixes
- Load Balancer discovery and Shared Path discovery did not work for some users. This issue has been fixed.
- Earlier, the users were unable to edit the wildcard certificate details after navigating to the Certificate Details page. This issue has been fixed.
- Earlier, when a certificate that was a part of a certificate group expired, the expiry notification email was sent to all groups in Key Manager Plus instead of to only the groups to which the certificate belonged. This issue has been fixed.
- Bulk certificate sync with ServiceDesk Plus failed for some certificates. This issue has been fixed.
- From build 6300, the expiry notification email address specified in the CSR form failed to be encoded. Due to this, the email address appeared as garbled text on the SSL page. This issue has been fixed.
Key Manager Plus Release 6350 (Aug 2022)
New Feature
- Integration with Sectigo Certificate Manager: Key Manager Plus now integrates with Sectigo Certificate Manager—a PKI management platform built to manage SSL/TLS certificates, SSH keys, and other digital identities. The integration facilitates users to request, acquire, import, deploy, and renew certificates issued by Sectigo and automate their end-to-end lifecycle management of SSL/TLS certificates directly from the Key Manager Plus web interface.
Enhancement
- From now on, while configuring ServiceDesk Plus as the ticketing system in Key Manager Plus, users can retrieve pre-existing templates from ServiceDesk Plus and utilize them to create tickets that will be displayed in ServiceDesk Plus.
Key Manager Plus Release 6300 (June 2022)
New Feature
- Key Manager Plus - Azure Key Vault Integration
Key Manager Plus now supports integration with Microsoft Azure Key Vault—an SSL certificate management service offered by Microsoft. Through this integration, users can request, renew, and manage the entire lifecycle of SSL/TLS certificates stored in the Azure Key Vault by importing them into the Key Manager Plus repository.
- Rebranding
Key Manager Plus allows administrators to rebrand the product instance and tailor it according to their organizational needs. Administrators can customize the brand name, logo, and product disclaimer based on the organization's legal requirements.
Enhancements
- The PostgreSQL server has been upgraded from version 9.5.21 to 10.18.
- The Apache Tomcat server has been upgraded from version 8.5.32 to 9.0.54.
- Key Manager Plus has now migrated to the OpenJDK platform, version 1.8.0_252.
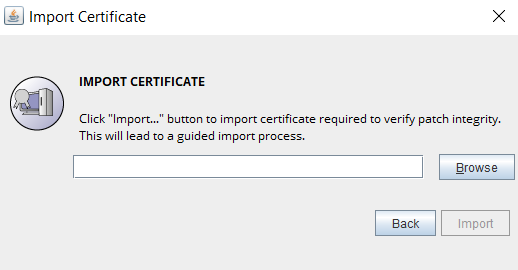
- We have implemented a patch integrity verification, which will henceforth require importing an SSL certificate (available as a downloadable file) whenever the product is upgraded using the PPM file. It is only a one-time operation. For the upgrade instructions and PPM download links, click here.
- Key Manager Plus will allow users to import the keys created using OpenSSL version 3.0 onwards.
- Users can now import WebSphere certificates into the Key Manager Plus repository.
- Key Manager Plus now allows users to group their certificates based on the 'Expiry Notifications Email' while creating a certificate group.
- From now on, under Multiple Servers, the users will be able to reassign the Primary server from the list of available servers while attempting to delete the existing Primary server.
- A new RestAPI to 'fetch PGP keys' has been added.
Bug Fixes
- Earlier, for some customers, the Key Manager Plus logo appeared bigger in email expiry notifications. This issue has been fixed.
- In Linux installations, the certificate discovery failed while discovering certificates from Shared Path using certificate list. This issue has been fixed.
- The certificates that were added to a certificate group created using additional fields as the grouping criteria, were not visible during certificate signing for Operator users with sign CSR permission. This issue has been fixed.
- Operator users were unable to view the details of the certificates that were part of a certificate group created using additional fields as the grouping criteria. This issue has been fixed.
- Administrator users were unable to edit the value of additional fields for certificates that are a part of a certificate group created using any criteria. This issue has been fixed.
Key Manager Plus Release 6210 (March 2022)
New Feature
- Key Manager Plus now comes with an exclusive tab for MSCA certificates under 'SSL >> MSCA'. Through this, users can manage the entire lifecycle of MSCA certificates and perform operations such as discovery and renewal from one place. In addition, two new options, 'Revoke' and 'Delete' have been added to the MSCA tab
Enhancements
- Key Manager Plus now comes with an option that mandates users to include 'Server Name Indication' while configuring and updating IIS Binding.
- Users can now rediscover the expired and about-to-expire certificates from the 'Certificate Expiry' widget in the Dashboard
Bug Fixes
- Earlier, the root certificate-based signing failed if the 'SAN' field contained a wildcard. This issue has been fixed.
- While discovering certificates using MSCA, certificate discovery failed if the language of the templates was not English. This issue has been fixed.
- Earlier, while importing users from AD and enabling SAML SSO, there was an issue with the SAML SSO login. This issue has been fixed.
- Earlier, Load Balancer discovery failed when the certificates were discovered using the 'Discover certificate list' page. This issue has been fixed.
Key Manager Plus Release 6200 (January 2022)
New Feature
- Two-Factor Authentication Support
Key Manager Plus now allows you to integrate with the following services to provide Two-Factor Authentication support for application login.
- Google Authenticator
- Microsoft Authenticator
- One-time password
- AWS Certificate Manager Integration
Key Manager Plus now supports integration with AWS Certificate Manager (ACM)—a trusted certificate authority and certificate manager. This integration enables users to request, acquire, deploy certificates from Key Manager Plus to AWS ACM , renew and automate the end-to-end lifecycle management of SSL/TLS certificates issued and managed by ACM, directly from the Key Manager Plus web interface.
Enhancements
- Key Manager Plus now allows operators to select administrators directly to send an email while adding a request for a certificate on the certificate request page.
- In addition to server certificates, Key Manager Plus now allows users to import client certificates from DigiCert and manage them in the Key Manager Plus repository.
- Users can now create a scheduled task for AWS certificate discovery.
Bug Fixes
- Assigning the certificate group created using any criteria other than common name failed to load operator user's SSL repository page.
Security Fixes
- Path Traversal Vulnerability, Remote Code Execution (RCE) and SSL validation vulnerabilities
- Privilege escalation vulnerabilities in the SSH Users view(CVE-2022-24446) and while exporting SSL certificates(CVE-2022-24447), reported by CERTXLM, have been fixed.
Key Manager Plus Release 6161 (November 2021)
Security Fixes
- A stored XSS vulnerability (reported by Ranjit Pahan), caused by HTML tags in certificate attributes, during SSL certificate import, CSR import, and SSL and CSR parse operations has been fixed.
Key Manager Plus Release 6160 (November 2021)
Enhancements
- Earlier, during certificates deployment using IIS Binding, users could deploy to a single server or agent only. From now on, users will be able to deploy certificates to multiple servers as well.
- Henceforth, users will be able to export the private key from the Microsoft Certificate store after certificate deployment.
- From now on, besides deploying to the computer account, Key Manager Plus allows you to deploy certificates to the Microsoft certificate store user account using the agent. The latest version of Key Manager Pus agent should run in the user account to which the certificates are to be deployed.
- 'Organization' and 'Organization Unit' have been added to the 'Column Chooser' on the 'SSL Certificates Report' page.
- Henceforward, users can choose to exclude automatically renewed certificate(s) from email notifications.
- Users can now bypass proxy server settings while performing Citrix Load Balancer certificate discovery using the 'Use REST API (By default KMP uses CLI commands for discovery and fetching certificates)' option available in the UI. Using this option, Key Manager Plus can bypass the proxy server and directly perform online certificate discovery. This option is also available during scheduled certificate discovery.
- Key Manager Plus now provides an option to import issuer certificates into the repository and form a complete certificate chain. Users can store and export the complete certificate package in JKS, PKCS, and PEM formats.
Bug Fixes
- Earlier, ServiceDesk Plus (SDP) ticket creation failed due to the API rate limit set by SDP. This issue is fixed now.
Key Manager Plus Release 6151 (Hotfix) (October 2021)
Bug Fixes
- Earlier, on some occasions, the 'Edit User' form under 'Settings >> User Management >>Users' displayed UI glitches for users with the 'Operator' user role. This issue has been fixed.
- Earlier, operations such as account creation and placing certificate requests performed through 'Let's Encrypt CA' failed. This issue has been fixed.
Key Manager Plus Release 6150 (September 2021)
New Feature
- Support for SAML-based Single-Sign-On (SSO)
Key Manager Plus integrates with federated identity management solutions to act as the SAML service provider and works with SAML identity providers to offer single sign-on. Through this feature, you can leverage a third-party SAML identity provider's authentication mechanism to access the Key Manager Plus interface without supplying your existing local authentication credentials for Key Manager Plus. Key Manager Plus supports several SAML SSO identity providers including, Okta, Azure SAML SSO, and AD FS.
- New Tools Category Added:
Key Manager Plus now comes with a 'Tools' category that will allow users to independently perform certificate conversion, SSL/CSR parsing, and vulnerability scanning without adding certificates into the Key Manager Plus repository.
i. Certificate Signing Requests (CSR) and SSL Parser - The parser tool allows users to upload certificates or their contents directly to the interface and sort the attributes into a readable format.
ii. Certificate Format Converter - The converter tool supports one-click conversion for a wide range of certificate formats.
iii. Scan Vulnerabilities - The scanner tool allows users to scan any domain for vulnerabilities by entering the domain name and port directly. Unlike the SSL Vulnerability scan, this tool checks for vulnerabilities in any domain, without adding the certificate to the repository.
- Certificates Synchronization Status Check
From Key Manager Plus build 6150 onwards, Key Manager Plus allows you to perform regular checks on the synchronization status of SSL certificates deployed to multiple servers directly. Additionally, you can schedule the synchronization check and generate a 'Certificate Sync Status' report based on the results.
Enhancements
- From build 6150, after certificate renewal, the expired certificate's details can be sent via email. Configure the required setting under 'Settings >> SSL >> Certificate Renewal'.
- From build 6150, Key Manager Plus will display the hosted SSL certificate's CommonName, Serial number, and SyncStatus with the managed servers and include them in the 'Deployed Servers' report.
- Earlier, scheduled tasks were performed only during the scheduled time. Now, from build 6150 onwards, scheduled tasks can be performed anytime by using the 'Execute' button available under the 'Schedules' tab.
- From build 6150, KMP allows you to check the SyncStatus using Agent. For this to work, the agent should also be updated to version 6150.
- From build 6000, certificates were managed based on their Serial Number. From build 6150, certificates having the same common name and different serial numbers can be grouped by enabling 'Managing Certificate History Settings' under 'SSL >> Certificate History'.
- From build 6150, after certificate renewal, the old certificate will be listed under 'Certificate History'.
- From build 6150, Key Manager Plus allows you to add additional properties to CSR while signing with root by using the 'Advanced Options' menu. It allows users to choose from a list of Key Usage and Advanced Key Usage properties, and add them to the new certificate. Examples for the Key Usage properties include; Digital Signature, Decipher Only, Encipher Only, and Certificate Sign.
- From build 6150, Key Manager Plus allows you to import PGP keys created using third party tools.
Bug Fixes
- Earlier, certificate order creation for GoDaddy's 100 UCC SAN SSL certificates was failing. This issue is fixed now.
- Earlier, while importing SSL certificates from the GoDaddy portal, Key Manager Plus failed to import some of the certificates. This issue is fixed now.
- Earlier, when an MSCA certificate was discovered from a different domain, the 'MSCA' type certificate was changed to the type 'Domain', which caused the auto-renewal process to fail. This issue has been fixed now.
Security Fixes
- A path traversal vulnerability has been fixed.
Key Manager Plus Release 6100 (May 2021)
New Feature
- Active Directory Synchronization
Key Manager Plus now comes with the Active Directory (AD) synchronization feature that allows users to set up recurring synchronization schedules for single or multiple domains during AD user import. AD synchronization schedules can be created to import users from user groups or organizational units that are part of multiple AD domains.
Enhancements
- Earlier, when certificates were renewed, the deployed servers and the credentials had to be mentioned manually. From now on, the renewed certificates will automatically inherit the deployed servers and their credentials.
- Henceforth, the SSL certificates can be manually mapped with deployed servers list to any server directly from 'Inventory >> More >> Add Deployed Server'.
- Earlier, only the administrators were able to perform CSR signing. Hereafter, the administrators can allow the operators as well to sign the certificates.
- From now on, certificates/CSRs/certificate groups will have an email field to which the SSL expiry email notifications can be sent, where the expiry notification email address can be provided while creating the Certificate and CSR.
- A new option - Deploy to Microsoft certificate store user account, has been added, which facilitates the deployment of the Microsoft Store deployed certificates to the respective user accounts, in addition to deploying to the computer accounts.
- The SSL Certificate Expiry Notification set up under "Settings >> Notifications >> Expiry" will now include Issuer, FingerPrint, and Serial Number fields in the Certificate Expiry email.
Bug Fixes
- The auto-renewal duplication issue has been fixed.
- There was an issue in exporting the certificates as password-protected zips when password protection for exports was enabled under Privacy Settings. This issue has been fixed now.
- There was a failure in Linux deployment from the ServiceDesk Plus request. This issue has been fixed now.
Key Manager Plus Release 6002 (April 2021)
Security Fixes
- Privilege escalation vulnerabilities (ZVE-2021-0959 and ZVE-2021-0958 ) in the Report view and during data export, reported by Ranjit Pahan, have been fixed.
- An XSS vulnerability (ZVE-2021-0956) that occurred during Linux shared file discovery, reported by Ranjit Pahan, has been fixed.
Key Manager Plus Release 6001 (March 2021)
Security Fix
- An XSS issue with the AD imported user details in the user management page, reported by Matt (CVE-2021-28382), has been fixed.
Bug Fixes
- MSCA discovery, when carried out using an agent without any filter, failed. This issue is fixed now.
- An issue that caused incomplete Scheduled LoadBalancer discovery and failed audit has been fixed.
Key Manager Plus Release 6000 (February 2021)
New Features
- SSL Certificate Rediscovery
Key Manager Plus allows you to rediscover SSL certificates from the same source using the server details entered during the previous discovery operation.
- Integration with Buypass Go SSL and ZeroSSL
Key Manager Plus now integrates with Buypass Go SSL and ZeroSSL—two certificate authorities that use the Automatic Certificate Management Environment (ACME) protocol to provide free, secure SSL certificates. Users can now request, acquire, create, deploy, renew, and automate the end-to-end management of SSL/TLS certificates issued by Buypass Go SSL and ZeroSSL, all directly from the Key Manager Plus web interface.
- Integration with ManageEngine Mobile Device Manager (MDM) Plus
Key Manager Plus now integrates with ManageEngine Mobile Device Manager (MDM) Plus. This integration uses ManageEngine MDM APIs to discover and deploy SSL certificates to and from the mobile devices managed by your MDM server. Key Manager Plus then lets you filter the discovered SSL certificates based on the OS type such as iOS, Android, Windows, Chrome OS, Mac OS, and Apple tvOS. It is also possible to export reports of the MDM certificates managed in the Key Manager Plus repository within a selected period. Additionally, you can schedule periodic generation of MDM certificate reports.
Enhancements
- Certificate Discovery from UNC Shared Path for Linux/Mac OS
Key Manager Plus now supports SSL certificate discovery from UNC (Universal Naming Convention) shared paths for Linux and Mac OS machines. Use this feature to discover SSL certificates stored in a folder path within a server that is accessible by Key Manager Plus. After the discovery, Key Manager Plus will consolidate the newly-discovered SSL certificates in its certificate repository. This option is also available during scheduled certificate discovery.
- MSCA Discovery with Agent using Multiple Templates
Users can now select up to five certificate templates while performing agent-based certificate discovery of local CA certificates. Before using this enhancement, please ensure if the Agent is upgraded to version 6000.
- Support for .CRT Extension
Henceforth, certificates can be exported/deployed with the .CRT extension too.
- Search-Enabled Custom Columns
Key Manager Plus allows you to search within custom columns for SSL Certificates and SSH keys.
- Multiple Servers List
Now you can include multiple servers for certificates in SSL certificate expiry notifications.
- GoDaddy Certificates Import
From now on, users can directly import the existing certificates from their GoDaddy account into the Key Manager Plus repository.
- Local Disassociation of Keys
It is now possible to dissociate keys locally if remote dissociation fails for users whose access has been discontinued.
- New Fields in the deployCertificate Rest API
In the deployCertificate Rest API, serial number and server name have been added in input data, where the server name is an optional field used to select a specific server to deploy a certificate.
- APIs - Serial Number as the Mandatory Field
Earlier, the Serial Number field, which was optional in the below APIs, has now been made mandatory; To get a certificate, To get certificate keystore, and To delete a certificate.
- Serial Number in the getCertificateDetails Rest API
In the getCertificateDetails Rest API, Serial Number has been added as an optional field, filling which fetches the details of that particular certificate alone.
Bug Fixes
- During SSL discovery, discovery from servers with mutual authentication failed. This issue has been fixed now.
- In build 5970, the Agent authentication failed for AD Users. This issue has been fixed now.
Behavior Change
From now on, all certificates with unique serial numbers will be listed under the 'Certificates' tab. However, the existing users can manage their already added certificates from the History section, which has now been moved under the Column Chooser.
Key Manager Plus Release 5970 (December 2020)
Enhancements
- From now on, Key Manager Plus supports ClouDNS to complete domain control validation while acquiring certificates from public Certificate Authorities.
- Support for 'Load Balancer' SSL Certificates discovery for Citrix devices.
- Support for AES256-encrypted PKCS12 Keys tores while adding certificate Keystores.
Security Fix
- For security reasons, henceforth, HTTP security headers will be added to all response URLs.
Key Manager Plus Release 5960 (November 2020)
New Features
- Certificate Discovery from UNC Shared Path
Key Manager Plus now supports SSL certificate discovery from UNC (Universal Naming Convention) shared paths. Use this feature to discover SSL certificates stored in a folder path within a server that is accessible by Key Manager Plus. After the discovery, Key Manager Plus will consolidate the newly-discovered SSL certificates in its certificate repository. This option is available during scheduled certificate discovery also.
- Certificate Discovery in DMZ Machines using Agent
It is now possible to discover the SSL certificates from directories in remote machines that are not directly accessible by Key Manager Plus—all through the Key Manager Plus Agent. This option is available during scheduled certificate discovery also.
- Browser Deployment of Certificates
Users will now be able to deploy SSL certificates in browsers from Key Manager Plus for the following server types: Windows, Linux, and MacOS.
- SSH Key Association using "Elevate to root user" Option
This release comes with the new "Elevate to root user" option. Now, as a security measure, it is possible to restrict users from directly accessing root users by disabling the root user login. Enabling this option elevates a user login from a non-root user to a root user and associate keys to all other users in the server.
- New RestApi
The new REST API, 'Deploy Certificate', has been added.
Enhancements
- We have upgraded the PostgreSQL server to version 9.5.21.
- Users can now select up to five certificate templates while performing template-based SSL certificate discovery.
- Users can now bypass proxy server settings while performing SSL certificate discovery. If this option is selected, Key Manager Plus will bypass the proxy server and directly perform online certificate discovery. This option is available during scheduled certificate discovery also.
- Earlier, after certificate renewal, users will have to deploy MSCA/-self-signed certificates manually. Now, it is possible to deploy these certificates automatically if the user credentials are available.
- Users will now be able to choose the Certificate type [CER/DER/P7B] and Keystore type [JKS/PKCS/PEM/KEY] while deploying Certificates to Windows and Linux machines and while exporting certificates.
- Now, it is possible to renew MSCA type Certificates with a new private key if a private key not available already.
Bug Fixes
- Earlier, it was possible to add or modify IISBinding only by giving the 'hostname'. This issue has been fixed, and now 'hostname' is not mandatory to create or update IISBinding.
- Certificates renewal happened without SAN names when the renewal was carried out using the 'Renew'' button in inventory.
- Earlier, MSCA templates showed the OID instead of the template name. This issue is fixed.
Key Manager Plus Release 5950 (August 2020)
New Features
- On-demand Renewal of Certificates
This release comes with a 'Renew' option under 'SSL >> Certificates' that allows users to initiate the renewal of Self Signed, Root Signed, Microsoft CA Signed, and Agent-signed certificates, and also the certificates issued by the third-party CAs.
- LDAP Authentication and Scheduled Users Sync
In addition to Active Directory and RADIUS authentication, Key Manager Plus now supports user import and user authentication using LDAP servers as well. Use LDAP integration to import Active Directory (AD) users from Microsoft AD and OpenLDAP into Key Manager Plus Linux installations, and also regularly update the user database through the sync operation provided by Key Manager Plus. Besides, users can use LDAP authentication for access, bypassing the local authentication provided by Key Manager Plus. Supported LDAP server types are Microsoft Active Directory and OpenLDAP.
Enhancements
- Key Manager Plus now supports scheduled SSL discovery and MS Certificate Store Discovery tasks with agent.
- Previously, the certificates due for expiry in 10 days or less got automatically renewed. Now, users will be able to customize the number of days to auto-renew the certificates before they expire.
- From now on, during CSR signing of SSL certificates using the agent, it is possible to specify the Agent timeout value, in seconds.
- Henceforth, users will be able to select specific Certificates or Certificate Groups while generating the 'SSL Certificates Report' Schedule type (under 'Schedule >> Add Schedule').
- Users will now be able to add and edit the deployed servers list under 'SSL >> Certificates >> Multiple Servers (icon)'. Newly added servers will be mapped with the latest certificate version in the certificate repository.
- Key Manager Plus now supports IP range discovery for MS Certificate store discovery ('Discovery >> MS Certificate Store') using the KMP service with the domain Admin account. This allows administrators to discover certificates across networks.
- Key Manager Plus now supports 'Load Balancer' Certificates discovery for 'SSL Discovery' schedule type. Use this schedule type to discover certificates from load balancers, such as BIG-IP F5, Nginx, etc., which support SSH access on a scheduled basis.
- Certificates and CSR generation pages have been enhanced with the Random Password generation feature.
Bug Fixes
- Under 'Settings >> SSL >> IIS Binding', binding list retrieval failed for bindings with a protocol other than HTTP/HTTPs. This issue has been fixed.
- Earlier during Digicert import, Key Manager Plus failed to import client/personal certificates into KMP. This issue is now fixed.
- Earlier, the date format had the month as a part of the value, due to which sorting did not work. Now, this issue has been resolved by modifying the date format in the CSV file to be the standard date format.
- Earlier while discovering certificates using a load balancer, there were problems with commands other than the standard Linux commands. This issue has been fixed.
- Get templates issue fixed for CA name-based fetch.
- Previously, the proxy configuration was not supported in GlobalSign integration, due to which users with proxy were unable to use the integration. This issue has been fixed now.
Key Manager Plus Release 5920 (June 2020)
Enhancements
- The 'Certificate Renewal Report' page under the 'Reports' tab now comes with a column chooser.
- Users can now view all the certificates associated with a particular agent by clicking the 'Host Name' of the agent listed under 'SSL >> Windows Agents'.
- Now, users can tailor schedules by adding custom email content and a unique signature.
- Now, users can discover certificates issued by a particular 'Microsoft Certificate Authority' just by entering the MSCA name in the text box provided, during discovery. Remember, this additional option will be available for Key Manager Plus installations in Windows server machines only.
- Now, it is possible to add the Wildcard name in the SAN field while creating a CSR or a self-signed certificate. With the Wildcard certificates, one can secure an unlimited number of subdomains for a registered base-domain.
- Earlier, Certificate Expiry Notification emails sent to the email addresses specified in additional fields followed a fixed format. Now, the customization settings configured for notification emails in 'Notification' and 'Schedule' tabs will be applied to the emails sent via email addresses in the additional fields as well.
Bug Fixes
- Agent got duplicated when re-installed from a different IP address. This has been fixed.
- The 'Common name' column sorting issue in the 'Certificate Sign Report' wizard has been fixed.
- The issue in MSCA auto-renewal with the EC key has been fixed.
- Get Templates issues that existed with the non - English languages have been fixed.
Key Manager Plus Release 5910 (May 2020)
New Features
- New Certificate Format - PEM
A new certificate format, Privacy Enhanced Mail (PEM), has been added, in addition to the already available certificate export formats, Keystore and PFX, where the PEM format is used for digital certificates and keys, deployed in web server platforms (e.g., Apache).
- Support for GoDaddy DNS
From now on, Key Manager Plus supports GoDaddy DNS to complete the domain control validation procedure while acquiring certificates from public Certificate Authorities, along with the already available DNS support types, Azure DNS, Cloudflare DNS, Amazon route 53, and RFC2136 Update. Using GoDaddy DNS, users can update the DNS record for GoDaddy domain validation from the Key Manager Plus portal itself.
Enhancements
- This release comes with an exclusive page for 'Windows Agents', accessible from the SSL tab, from where users will be able to perform all agent-specific operations such as SSL Discovery using agent, deployment of SSL certificates in certificate groups using agent and CSR Signing with MSCA agent.
- Certificate deployment in multiple servers has now been made simpler by using an agent, provided the agent is running in the server to be deployed, and both the agent name and the server DNS name are the same.
- Now, auto-renewal of certificates is possible for the 'MSCA using agent' sign type as well, from 'Settings >> SSL >> Certificate Renewal'.
- The 'Certificate Sign Report' comes with the following MSCA/Third party CA signing details; Certificate Authority, Certificate Template, Sign Type column.
- The 'Certificate Renewal report' comes with the 'Renewed By' column relevant to MSCA and 3rdPartyCA renewal details.
- A new option 'Reissue Certificate' has been added under 'SSL >> GlobalSign' that allows users to request GlobalSign to reissue an SSL certificate.
- The new 'GlobalSign Orders Report' allows the GlobalSign orders to be added as individual reports, which provide a detailed view of certificate orders requested from the GlobalSign CA.
- From now on, users can add a "Key Comment' while importing a new SSH key and editing an existing key from the repository. Also, users can avail the checkbox "Update comment in associated users" to update the Key comment to the associated end servers automatically.
- Now, it is possible to add additional properties to a certificate while creating it, by using the 'Advanced Options' menu. It allows users to choose from a list of Key Usage and Advanced Key Usage properties, and add them to the new certificate. Examples for the Key Usage properties include; Digital Signature, Decipher Only, Encipher Only, and Certificate Sign.
- The DigiCert CA page has been enhanced with a new menu 'Show' that has four options, Expired, Revoked, Rejected, and Others, used to filter the DigiCert CA list view.
- Now, while adding or modifying the Certificate Groups, it is possible to set 'additional fields' also as one of the 'By Criteria' filters for certificates.
- While creating an additional field, users are allowed to choose if it is applicable for SSH/SSL/both. The 'Additional fields' option is now available under 'Settings'.
- New REST APIs 'GET CSR list' and 'Sign CSR' have been added.
- The 'Expiry Notification' has been enhanced with the custom mail content, 'Title' and 'Signature'.
Change
In the below set of REST APIs, the fetch details format is modified is such a way that the "details" attribute holds all the data; GetCertificateDetails, getallsslcertificates, getAllSSLCertsExpiryDate, sslCertSingleDiscovery, sslCertRangeDiscovery, getallsshkeys, GetSSHKey, getAllSSHUsers,getAllKeyStoreKeys,GetSSHKeysForUser and GetAllAssociatedUsers.
Security Fixes
- The Key Manager Plus server's SSL TLS has been upgraded to version 1.2.
- The Key Manager Plus agent's TLS has been upgraded to version 1.2. This is configurable in 'Agent.conf'.
- Earlier, during API calls, the Authentication token was passed as a request parameter. Hereafter, each API call made to the application requires the Authentication token to be passed in the request header.
- Earlier, the Keystore password of the certificate uploaded into the server was appended in the URL, which posed a security risk. From now on, the Keystore password will be sent as the 'RequestBody' to maintain optimal security.
- A local File Intrusion issue during MS store discovery has been fixed.
- The operator user was able to view the admin terminal audit. This has been fixed.
Bug Fixes
- Server certificate update failed in case of Key Store with multiple alias names. This has been fixed.
- In the build of 5900, the certificate repository column order and also the column values got altered after adding the 'Port' column. This has been fixed.
- The root and intermediate certificates of PEM format got added as separate entries in the certificates repository. This has been fixed now.
Key Manager Plus Release 5900 (March 2020)
New Feature
- GlobalSign
Key Manager Plus now supports integration with GlobalSign SSL—atrusted certificate authority and a leading cloud-based PKI solutions provider. This integration enables users to request, acquire, import, deploy, renew and automate the end-to-end lifecycle management of SSL/TLS certificates issued by GlobalSign, directly from the Key Manager Plus web interface.
- Certificate Deployment using Agent
Key Manager Plus can already deploy and bind certificates to IIS servers belonging to the domain, where Key Manager Plus also resides. Now, Key Manager Plus can also deploy certificates to IIS servers in demilitarized zones and also bind them to websites in IIS, all using an agent. This makes Key Manager Plus more scalable, as it can deploy and bind certificates in IIS servers, irrespective of whether they are in the same or different domain.
- CSR Signing using Agent
In addition to the already available two sign types namely, 'MS Certificate Authority' and 'Sign with Root', used to sign certificates from Key Manager Plus, a third sign type 'MS Certificate Authority with Agent' has been introduced. This new sign type is mainly used to sign certificates originating from a distinct domain, i.e., other than the domain to which Key Manager Plus belongs.
- System Integration - ServiceDesk Plus and Service Now
From release 5900, Key Manager Plus integrates with enterprise ticketing systems namely ServiceDesk Plus (on-premise) and ServiceNow. This integration ensures that automatic service requests are created in the ticketing environment to notify administrators of SSL certificates that are at the risk of expiring and certificates that are deemed vulnerable after a vulnerability scan in Key Manager Plus. Users can set notification policies to govern the frequency of service request creation for expiring and vulnerable tickets.
Enhancements
- It is now possible to customize notifications and their intervals. Users can now choose not to receive notifications regarding the expired certificates, and send a separate email and customized subject per certificate, from 'Settings >> Notification'. The same actions can be done while creating new schedules under 'Schedule >> Add Schedule', where you have to select the Schedule Type as 'SSL Expiry'.
- It is now possible to bulk edit the additional fields for multiple SSH keys and certificates.
- The column chooser was introduced in the version 5850 in the SSL window. Now, the IP address and Port are added in the column chooser which allows the users to display the selected columns in the list view.
- It is now possible to provide ephemeral access (validity in hours and minutes) to certificates created using the 'Create Certificate' Rest API.
- Earlier, Key Manager Plus allowed signing and deployment of certificates only from Windows systems. Now, it is possible to perform certificate signing and deployment to Windows systems from Linux installations through agents.
- It is now possible to provide customized subjects in schedules.
Security Enhancement
Earlier, PostgreSQL data directories in Windows installations were entirely accessible to all locally authenticated users. Now, as a security practice, we have exerted the following measures, applicable for installations under the 'Program Files' directory:
- No inherited permissions are allowed for data and configurations directories
- "Authenticated Users" permission has been excluded entirely
Only the CREATOR OWNER, SYSTEM, Installation User, NT AUTHORITY\Network Service and Administrators groups will have the Full Control over the directories and also can start PostgreSQL.
Key Manager Plus Release 5860 (January 2020)
New Feature
- Pretty Good Privacy (PGP) Keys
PGP encryption is used to enhance cryptographic privacy and authentication for online communication by encrypting and decrypting texts, emails, files, etc. It uses a combination of data compression, hashing, and public-key cryptography to boost confidentiality. Now, Key Manager Plus brings you this PGP functionality in the form of PGP key generation, where the keys are used to encrypt the data like emails, texts, etc. Create, store and manage PGP keys under 'KMP >> Key Store >> PGP Keys'. Modify the key description anytime, export private/public keys, export keys to multiple email ids, and generate, view, and schedule reports. You can also send expiry notification emails to admins. This feature allows you to share and collaborate information securely among your trusted groups of users and businesses.
Key Manager Plus Release 5850 (December 2019)
New Features
- SSL Certificate Deployment and Binding - IIS Server
From release 5850, you can both deploy a certificate to the IIS server and also bind it to the desired website in the IIS, all from the Key Manager Plus interface itself, without the need to access the IIS server separately. Also, an option has been provided to automatically restart the IIS server for the deployment and binding to take effect, thereby eliminating the need for the manual restart from the IIS end.
- Additional Fields
Key Manager Plus now brings you the 'Additional Fields' feature, configured from 'Settings >> General Settings' that is used to include any additional information about SSH keys and SSL certificates, stored in the repository. There are four different categories to add the additional fields: character, numeric, date and email. Users can choose to add or remove the additional fields from SSH and SSL views.
- Column Chooser
The 5850 version of Key Manager Plus comes with the Column Chooser feature that allows users to show or hide columns at runtime, and also rearrange the columns from the current view via drag-and-drop.
Enhancements
- Now, it is possible to use the Key Manager Plus service account credentials for authentication while deploying certificates in Windows servers.
- Henceforth, while creating a certificate, users can provide ephemeral access (validity in hours and minutes) to the certificate, after which the certificate auto-expires. This eliminates the need for compulsory permanent access credentials to access target systems and also explicit access repeal.
- It is now possible to perform SNI-based SSL discovery using the Common Name and IP Address combination.
- The option to filter certificates based on the key length and signature algorithm within specific expiry days has been added to the 'getAllSSLCertificates' Rest API.
Bug Fixes
- During all AD-related operations performed from the Key Manager Plus interface, the 'Connection Mode' got saved as 'No SSL' only, even if the 'SSL' mode was chosen. This issue has been fixed now.
- Earlier, MSCA signing supported 'java keytool' CSR only. Now, from this release, all CSRs will be supported by MSCA signing.
- During certificate creation, all values entered in the SAN field were all together categorized as 'DNS' only. Now, the values are segregated as 'DNS' and 'IP Address' categories.
Key Manager Plus Release 5810 (October 2019)
New Features
- Key Manager Plus now enables users to discover, import, and configure expiry notifications for SSL certificates hosted in the following Amazon Web Services: AWS Certificate Manager (ACM) and AWS Identity and Access Management (IAM).
- Key Manager Plus now supports automated renewal of self-signed certificates in addition to Microsoft CA certificate renewal.
Enhancements
- Key Manager Plus now provides additional insights on agent activity such as heartbeat interval, latest response time and operation performed.
- Key Manager Plus now provides an option to edit the email ID associated with the Let's Encrypt user account.
- Key Manager Plus now supports the discovery of SSH keys with ECDSA and ED25519 signature algorithms.
- A new REST API—to view the private key passphrase of SSL certificates—has now been added.
- For scheduled SSL expiry task, users now have the option to choose whether or not, to receive email notifications when no certificates in that particular schedule are nearing expiration.
- Key Manager Plus offers automatic bundling of individual private key (.key) files and certificate files (.cer/.pem) into 'JKS' and 'PKCS' keystore file formats and provides export option for the same.
- Two extra categories have been added for criteria-based certificate group creation: AWS service and certificate template.
Bug Fixes
- Previously, certificate deployment failed if the field "Store Password" contained a space character when creating certificates from SSL → Certificates tab. This has now been fixed.
- Previously, when performing bulk operations, the "Create and Deploy" action failed when executed on SSH user groups, for RSA and DSA signature algorithms. This has now been fixed.
- Previously, when there was a "space" character present in a certificate group name, attempting to fetch the SSL certificates report pertaining to that group from the Reports tab threw the following error: "Invalid field format". This has now been fixed.
- Previously, even after the certificate private key was imported and attached to a certificate in Key Manager Plus' certificate repository, the "Export Keystore/PFX" was still disabled. This has now been fixed.
Key Manager Plus Release 5800 (August 2019)
New features
- Integration with DigiCert SSL: Key Manager Plus brings forth integration with DigiCert—leading provider of TLS/SSL, IoT and various other PKI solutions—enabling users to request, acquire, create, deploy, renew and automate the end-to-end management of SSL/TLS certificates issued by DigiCert, all directly from Key Manager Plus' web interface.
- CSR templates: Key Manager Plus now allows users to create and use predefined templates for CSR (Certificate Signing Request) generation.
- Users can now choose to exclude specific certificates from being added to Key Manager Plus repository when performing SSL discovery or during manual addition.
- Key Manager Plus now supports creation and management of SSH keys using ECDSA and ED25519 key algorithms.
- Key Manager Plus now supports RFC2136 DNS updates to complete domain control validation when acquiring certificates from public certificate authorities.
Enhancements
- Key Manager Plus now includes provisions that allow users to sign CSRs (either using your internal Microsoft CA or a root certificate) as and when they are generated.
- Key Manager Plus now supports file-based discovery for scheduled SSH and SSL discovery tasks.
- A new dashboard widget that provides data about SSL configuration vulnerabilities has now been added.
- Two new REST APIs have been added: REST API for SSL certificate addition and REST API for SSH key deletion
Key Manager Plus Release 5750 (May 2019)
Enhancements
SSL discovery
- Agent based discovery:Key Manager Plus now supports agent based SSL discovery that allows administrators to discover and import certificates present across a network by installing one or more instances of agent software on target systems. The agent, which is available as a compressed package with all the necessary configurations in Key Manager Plus interface, once installed in the required end servers, performs certificate discovery and updates the certificate database in a timely manner.
- Load balancer certificate discovery:Key Manager Plus now allows administrator users to discover and consolidate SSL certificates deployed to Linux based load balancers such as Nginx and F5 through a process tunneled via SSH.
- When performing Certificate Store and MS CA discovery, administrators can now make use of Key Manager Plus service account credentials to login to target systems, using the dedicated option provided, without having to manually enter them.
SSL / TLS encryption for mail server configuration:Key Manager Plus now allows users to encrypt communication for email notifications sent from the application using the SSL / TLS option available in SMTP configuration settings.
Bug Fixes
- Multiple server icon issue:Previously, when a certificate was deployed to two servers and then if one of the deployed servers was deleted, the "Multiple Servers" icon still continued to be enabled. This has now been fixed.
- Previously, when discovering multiple certificates from a single resource, changing the DNS name of one of those certificates caused it to be reflected across all the discovered certificates. This has now been fixed.
- Previously, when scheduled discovery operations failed (both SSH and SSL), the audit records were not updated correctly for a few cases. This has now been fixed.
Key Manager Plus Release 5710 (May 2019)
Enhancements
- SSH and SSL Discovery:
- Key Manager Plus now provides a subnet discovery option for both SSH and SSL discovery, allowing administrators to discover keys and certificates from specific subnetworks within an IP range.
- Users can now choose to exclude specific IP addresses when performing bulk discovery from an IP address range.
- Certificate Deployment:Key Manager Plus now provides an additional key based authentication functionality (apart from the conventional password authentication) which users can leverage to deploy certificates to password-less Linux end servers.
- Besides Azure and Cloudflare DNS, Key Manager Plus now supports Amazon Route 53 DNS to complete the domain control validation procedure when acquiring certificates from public certificate authorities.
Bug Fixes
- Previously, in the following scenarios—Microsoft Certificate Store discovery, server certificate upload and Radius server configuration (server secret field)—if the password entered contained special characters, a "harmful content" error was being thrown. This has now been fixed.
- Previously, certificates that did not have a common name (the SAN name is taken as the common name by default in these cases) failed to update after running a scheduled discovery. This issue has now been fixed.
- Previously, the 'Days' filter in the SSL Expiry Report failed to render correct results. This has now been fixed.
Key Manager Plus Release 5700 (April 2019)
New features / Enhancements
- Integration with public certificate authorities: Key Manager Plus facilitates end-to-end life cycle management of certificates obtained from trusted certificate authorities (CAs) enabling users to request, consolidate, deploy, renew and track certificates issued by multiple commercial CAs from a single interface. This functionality powered through a seamless API integration with The SSL Store™—one of the largest platinum partners of world's leading CAs—provides users the option to acquire and manage certificates from the following third-party CAs directly from Key Manager Plus' web interface: Sectigo (formerly Comodo), Symantec, Thawte, Geotrust, and RapidSSL.
- Audit notifications: Users can now choose to receive audit log notifications for various operations performed in Key Manager Plus. The alerts can be configured in the form of email notifications, or SNMP traps / Syslog messages to management systems within your network.
- Key Manager Plus now provides users the option to update credentials for SSH resources in bulk, which is useful in cases where multiple resources operate with the same credentials.
Bug Fixes
- Previously, the DNS based domain control validation procedure was unsuccessful for Let's Encrypt sub domain certificate requests. This has now been fixed.
- Previously, those certificates that contained string parameter "WITH" (in this format, eg., SHA256WITHRSA) in the signature algorithm could not be classified as root certificates. This issue has now been fixed.
- Previously, when pushing key files to users after key association, dissociation or editing authorized_keys file via SCP, there were issues with accessing the file post transfer due to file name issue. This has now been resolved by generating a random file name before transferring to the appropriate user accounts.
- In Key Manager Plus build 5650, the global search for certificates based on common name and SAN failed to retrieve proper results. This has now been fixed.
- Previously, the file-based discovery of SSL certificates failed for large file sizes (more than 50 thousand IP addresses). This has now been resolved.
- Previously, there were issues with resetting the password for Key Manager Plus account (local authentication) using the "Forgot Password" option. This issue has now been fixed.
Key Manager Plus Release 5650 (Jan 2019)
New features
- Failover service (FOS) with common MS SQL clusters: Key Manager Plus now provides administrator users the option to map redundant Key Manager Plus server instances to a common MS SQL cluster. Therefore, if one Key Manager Plus instance fails, the other instance(s) that are configured to the same database take over ensuring uninterrupted access to the application.
- Let's Encrypt wildcard certificate management support: Users can now request, acquire and manage wildcard certificates issued by Let's Encrypt certificate authority from Key Manager Plus.
- Administrators can now create scheduled tasks for discovering and importing certificates from Microsoft Certificate Store and certificates issued by Microsoft Certificate Authority.
- Users can now import certificate signing requests (CSRs) generated outside Key Manager Plus, forward to trusted certificate authorities and track their statuses from Key Manager Plus.
Enhancements
- Key Manager Plus now offers a more simplified workflow to establish connection with SSH resources that utilize password-less, key based authentication.
- During resource deletion, users are now provided with the option to either dissociate or retain the SSH keys associated to the resource using Key Manager Plus. This option was not available in the earlier versions and the associated key was automatically dissociated.
- Users now have the option to import certificate signing requests (CSRs) generated outside Key Manager Plus when placing GoDaddy certificate orders.
- Key Manager Plus now provides users an additional option to export only the private key during CSR export.
Bug Fixes
- Harmful content fix on non-English, Windows operating system: Previously, Key Manager Plus installed on non-English Windows operating system had traces of harmful content in schedule creation and audit records. This has now been fixed.
- Previously, during SSH resource deletion, the SSH keys manually imported into Key Manager Plus and associated to specific user accounts from the application were supposed to be dissociated after the resource had been deleted. However, the keys remained associated to the user accounts even after resource deletion. This has been fixed and also, users can now choose to either dissociate or retain the associated keys (Refer enhancement 2).
- Previously, when enumerating user accounts for resources that utilized password-less, key based connection establishment, the SSH keys in the user accounts were not discovered. This has now been fixed.
- Previously, SSH key import was unsuccessful if the key passphrase contained special characters like '~', '?', '<' and '>'. This has now been fixed.
Key Manager Plus Release 5630 (Dec 2018)
New features / Enhancements
- Key Manager Plus now supports SMTP server certificate discovery that allows administrators to exclusively discover and manage SSL certificates used by mail servers.
Bug Fix
- Previously, when deploying SSL certificates to Microsoft Internet Information Services (IIS) server, the private key exported with the certificate was being corrupted on deployment. This has now been fixed.
- Previously, administrators were unable to sign certificates with custom root CA if Subject Alternative Name (SAN) wasn't provided during CSR generation. This has now been fixed.
Security Fix
- Previously, when performing template-based discovery of certificates issued by the Microsoft Certificate Authority (MS CA), the CA server's account credentials were being stored in clear text in the Key Manager Plus server's log files. This has now been fixed.
Note: The potential for exposure was limited only to customers matching specific conditions. A detailed advisory was sent to customers to check for such conditions and in the unlikely case of exposure happening, the advisory included instructions to sanitize the exposure and fix the conditions.
Key Manager Plus Release 5620 (Oct 2018)
New features / Enhancements
Integration with GoDaddy SSL: Key Manager Plus now supports lifecycle management of SSL certificates issued by GoDaddy certificate authority. This enhancement, powered through a seamless integration with GoDaddy's API, allows administrators request, consolidate, deploy, renew, revoke and manage life cycles of certificates issued by GoDaddy certificate authority from a single interface.
Key benefits
- Fully automated, end-to-end management of certificate lifecycles.
- Complete visibility and control over demand, CSR generation, certificate deployment and revocation.
- Centralized tracking of certificate requests with an at a glance view of their status parameters.
- Custom expiration alerts through periodic email notifications.
Key Manager Plus Release 5610 (Aug 2018)
New Features / Enhancements
- Root based certificate signing: Key Manager Plus now enables administrators to sign and issue certificates to end-servers within the network environment, based on a root certificate that is trusted within the network.
- Domain expiry notification: Administrators can now keep a track of expiring domains from Key Manager Plus facilitated through 'Whois Lookup', and also receive periodic email notifications regarding the same.
- Key Manager Plus now expedites domain validation for Let's Encrypt certificate renewal through automated verification of DNS-01 challenges (for Azure and Cloudflare DNS).
- Key Manager Plus now includes provisions to import certificate files to keystore by automatically pinning its corresponding private key with the acquired certificate.
Bugfixes
- Previously, there were a few format issues during SSH keys import. This has now been fixed.
Key Manager Plus Release 5600 (May 2018)
New Features / Enhancements
- Provision to control the exposure of personal data in reports
Key Manager Plus now has provisions to control the exposure of personal data in reports, allowing administrators to mask or hide personal data in reports exported from Key Manager Plus as well as in e-mail notifications for scheduled report generation.
- Password protection for exports
Administrators can now enable password protection for exports, thus enforce an additional layer of security for files (certificates, certificate private key, certificate signing request, PDF and CSV reports, SSH public key, SSH private key, keys secured in keystore) exported from Key Manager Plus.
- Administrator acknowledgement of data transfer for third-party integrationsKey Manager Plus has now made it mandatory for administrators to acknowledge the transfer of personal data when setting up integration with third parties—such as certificate requests from Let's Encrypt and other trusted third-party CAs, integration with ServiceDesk Plus' CMDB—where there is flow of personal data from Key Manager Plus.
- Provision to purge audit trails
Key Manager Plus now includes the provision to purge audit trails, giving administrators the privilege of erasure of personal data that are no longer required in relation to the purposes for which they were originally recorded.
- Database-level encryption of sensitive personal information
Key Manager Plus now offers encryption of sensitive personal data at the database-level providing a greater level of data integrity and privacy.
- Provision to manage non-user email addresses
Key Manager Plus now separately lists and tracks unmapped email addresses—those that are not associated with any Key Manager Plus users but are being used for sending notifications regarding scheduled tasks, license expiration—and also grants administrators the privilege to delete them if needed.
- Key Manager Plus now provides administrators the option to enable or disable API access.
- Users can now export keystore files attached to certificates in various formats (PKCS12 / JKS).
- Key Manager Plus now provides additional options to configure email notifications for certificate expiry and private key rotation.
Bug fixes
- Previously, Key Manager Plus imported certificates that had no common name or SAN during SSL certificate discovery. This has now been fixed and import will be successful only if either of the two parameters are present.
Key Manager Plus Release 5510 (Apr 2018)
New Features / Enhancements
- Key Manager Plus now supports DNS based domain verification for certificates requested from Let's Encrypt CA.
- Template-based SSL certificate discovery option, for certificates stored by Microsoft Certificate Authority.
- Option to transfer files using Secure Copy Protocol (SCP) to user accounts with SSH key based authentication.
Bug Fixes
- Previously, there were issues when parsing SSH key passphrases that contained special characters. This has now been fixed.
Key Manager Plus Release 5.5 (Jan 2018)
New Features / Enhancements
- Microsoft CA certificate signing :
Key Manager Plus now allows users to get certificate requests signed from Microsoft Certificate Authority, thereby facilitating complete life cycle management for certificates issued by Microsoft Certificate Authority.
- Integration with CMDB :
Key Manager Plus now provides the option to sync SSL certificates in its repository with ManageEngine Service Desk Plus CMDB, allowing administrators to map certificates to specific servers / applications in the CMDB and monitor their usage and expiration from Service Desk Plus' CMDB.
- SSL Certificate group :
This enhancement allows users to organize SSL certificates into logical groups based on various criteria and execute actions in bulk on the groups.
- Option to enforce access restrictions by assigning users to specific certificate groups during user additions.
- Date based discovery filter for Microsoft Certificate Authority certificate discovery.
- Option to separately track and manage various versions of the same SSL certificate (with the same common name).
- Option to change Key Manager Plus' web server port directly from the user interface.
- Option to import and map a private key to certificate has been supported.
Bug Fixes
- Earlier, when generating certificate signing requests with SAN names, the SAN names were not updated. This has now been fixed.
- Earlier, there were issues with fetching the system locale on Microsoft CA discovery. This has now been fixed.
Key Manager Plus Release 5.2 (Aug 2017)
New features / Enhancements
- SSL certificate vulnerability scan:
Users can now scan for vulnerabilities in SSL certificates managed using Key Manager Plus. Vulnerability scan is performed on SSL certificates as well as the end-point servers. Key Manager Plus will check for certificate revocation status, certificate-server mismatch, usage of weak encryption algorithms (such as the SHA-1) pertaining to the selected certificate. Also, the end-point servers are scanned for configuration vulnerabilities such as HEARTBLEED, POODLE and usage of weak protocols and cipher suites.
- Users can also schedule periodic vulnerability scan on selected or all certificates in Key Manager Plus repository, obtain e-mail notifications and comprehensive reports post the scan.
- Graphical representation of private-key availability for a given certificate in the SSL → Certificates view.
- Option to download keystore, pfx and private-key files for a given SSL Certificate.
- Option to install SSL certificate for Key Manager Plus server from the product interface.
Bug fixes
- Earlier, Edit resource group action was being redirected to Add Resource Group window. This has now been fixed.
Key Manager Plus Release 5.1 (May 2017)
New features / Enhancements
- Landing server support for SSH key management:
Option to connect to remote networks through landing servers, thereby overcoming the barriers created by network segmentation. Also supports ssh key management for these remote servers.
- Option to deploy certificates onto Windows server (Internet Information Services) and Microsoft Certificate Store directly from product interface.
- Option to identify the different versions of certificates deployed and also the list of servers in which a certificate is deployed.
- Option to add user generated private keys when requesting for certificates from Let's Encrypt CA.
- Key Manager Plus now supports MSSQL as database back end.
- Option to fetch latest authorized_key file,edit and push the file to respective user accounts.
Bug fixes
- Earlier, there were display issues with SSH home directory settings. This has now been fixed.
- Earlier, there were issues while adding .der encoded certificates using Add certificate option. This has now been fixed.
Key Manager Plus Release 5.0 (Feb 2017)
New Features / Enhancements
- End-to-end certificate life-cycle management through integration with Let's Encrypt CA:Key Manager Plus now allows you to request, procure, deploy and automatically renew SSL certificates for your domains from Let's Encrypt, the renowned Certificate Authority.
- Discovery:
- Option to discover and manage certificates from Windows Certificate store.
- Option to exclusively discover and manage certificates issued by Windows Certificate Authority.
- Deployment: Option to deploy SSL certificates as well as JKS/PCKS12 keys to end-point servers directly from the product interface.
- Reports: Additional reports on certificate deployment, certificates deployed on multiple servers, SHA-1 certificates, Let's Encrypt certificates, Let's Encrypt certificate requests.
- Option to export audit records on key and certificate discovery.
- Enhancements to identify SSH user home directory.
- Certificate request workflow enhancements:
- Options to specify device name/ IP address while raising a certificate request.
- Options to automatically import the obtained certificate into .pfx/.keystore file.
- Option to e-mail certificate and JKS/PKCS keys while closing a certificate request.
Bug Fixes
- Earlier, there were connection issues with ubuntu16.04 server. This has now been fixed.
- Earlier, operator users can view all the users in various user groups. This has now been fixed. The operator users can now view only those users present in their own user groups.
Key Manager Plus Release 4.5 (Oct 2016)
New Features / Enhancements
- RESTful APIs for SSL, SSH and Key store: Key Manager Plus now provides RESTful APIs, which help you to connect, interact and integrate any application with Key Manager Plus directly. The APIs also allow applications to create, fetch, associate digital keys and add, retrieve or manage users programmatically.
- Option to discover and manage certificates mapped to user accounts in Active Directory. Both on-demand and scheduled discovery options are supported.
- Support to leverage RADIUS server authentication.
- New report on wildcard certificates deployment scenario.
- Report on the user certificates imported from Active Directory.
Bug Fixes
- Earlier, there were issues with date based sorting in the certificates and scheduled views. This has been fixed.
- Earlier, SSL discovery schedule took too long to complete on failure cases. This has been fixed.
- Earlier, email address was mandatory while saving schedules. This has been made optional.
Key Manager Plus Release 4.1 (Aug 2016)
New Features / Enhancements
- Option to push the private key, public key or both to remote user accounts. This feature is also available as part of key rotation schedule.
- Administrator users can now add commands, restrict hosts and carry out other actions on a public key and push the authorized_key file to the remote user account. They can also view the current authorized_key file content.
- Administrator users can now be able to view the passphrase of the SSH keys, SSL certificates and other keys.
- Option to import multiple SSL certificates is supported now.
- Option to effectively track SSL certificate expiry through a new scheduled task.
- Dashboard settings will be persisted in the database.
Bug Fixes
- Earlier, when root credentials were incorrect and key based authentication is enabled, there was an issue in associating private keys to users. This has been fixed.
- Earlier, there was an issue in importing .pfx (personnel certificates) through import keystore option. This has been fixed.
- Active Directory authentication issue in Key Manager Plus Windows 32 bit build has been fixed.
Key Manager Plus - Release 4.0 (June, 2016)
New Features
Enhancements
- Earlier, for SSH key management, user accounts could be added only if their associated credentials were provided. Now, a feature has been added to manage users using only SSH key pairs (without providing their passwords).
- SSH Private Key Group : This enhancement helps to organize SSH private keys as a logical group and execute key rotation, report creation, key group deployment and other operations in bulk.
- SSH User Group : This enhancement helps to organize SSH users into a group and execute actions in bulk on the group.
- Earlier, the private keys were deployed in the default location. Now, option has been provided to change the remote server user account authorized_key file location (i.e /home/test/.ssh to var/home/test/.ssh) both in bulk and for individual user accounts.
- Support is now provided for JUNOS based Juniper devices.
Changes
- Earlier, licensing was based on the number of SSH users. Henceforth, licensing would be based on the number of keys, which includes SSH private keys, SSL certificates, and the number of keys in the Key Store, which are managed using Key Manager Plus.
ManageEngine® Key Manager Plus Upgrade Pack Download