Direct Inward Dialing: +1 408 916 9890

Microsoft Entra ID serves as a core identity management solution for organizations worldwide. It is used not just for authenticating users, but orchestrating access, enforcing security, and ensuring compliance across your organization. Managing Entra ID requires more than setting up accounts or assigning licenses. It is about continuously refining how identities are governed, secured, and optimized at scale.
This guide outlines ten practical ways to strengthen your Entra ID environment, from tightening stale user management to scaling permissions and monitoring risks proactively. Each recommendation is built on core Entra ID features, helping your Entra admins improve identity governance while keeping your environment streamlined. Here are the topics that we'll explore in this blog.
Maintaining an active, accurate user directory is one of the simplest ways to strengthen your Entra ID environment. Inactive accounts not only create hidden security risks, but they can also tie up valuable resources like licenses, driving up costs over time. Making it easy to clean up inactive users and resources ensures a more secure, less burdensome environment over time.
Inactive accounts tend to accumulate quietly when users take extended leaves or exit the organization, or due to the existence of yet-to-be-identified duplicate accounts. Without a clear process for spotting them, these dormant accounts can quietly expose your environment to risks from unauthorized access to credential misuse.
You can use this information to review the real, active state of your organization and promptly block or disable these accounts before they become a liability or worse, a threat.
Start identifying and cleaning up Microsoft 365 inactive users.
Inactive users often retain licenses unless manually revoked. These unused licenses quietly accumulate, wasting resources and blocking reuse.
Automating cleanup typically involves scheduling periodic user activity checks, identifying inactive accounts based on sign-in patterns, and revoking or reallocating licenses through scripted workflows using Microsoft Graph or PowerApps.
Streamline Microsoft 365 license management for inactive accounts.
Strong authentication controls are the first line of defense for any environment.Optimizing how users authenticate and their access to resources helps prevent breaches long before they reach critical levels.
By strengthening authentication methods and enforcing smarter access policies, you build a more resilient and adaptive security perimeter.
Allowing users to authenticate through trusted external identity providers can enhance flexibility, retain a workflow that suits you, and simplify access management for external users such as partners, contractors, and multi-organization teams.
At a high level, this involves configuring federation settings for your trusted external identity providers, selecting supported authentication protocols (such as SAML or OpenID Connect), and configuring an Entra application for the same uses.

Check out how to configure external authentication methods securely.
Entra ID Conditional Access is one of the most powerful and adaptable tools for balancing security with user experience. Instead of applying one-size-fits-all access restrictions, it lets you enforce access decisions dynamically based on multiple factors such as user location, device compliance, sign-in risk, and the application you are accessing.
A properly configured policy ensures that legitimate users can work smoothly while risky activities are automatically challenged, blocked, or monitored. You can also test its effects before enforcement.
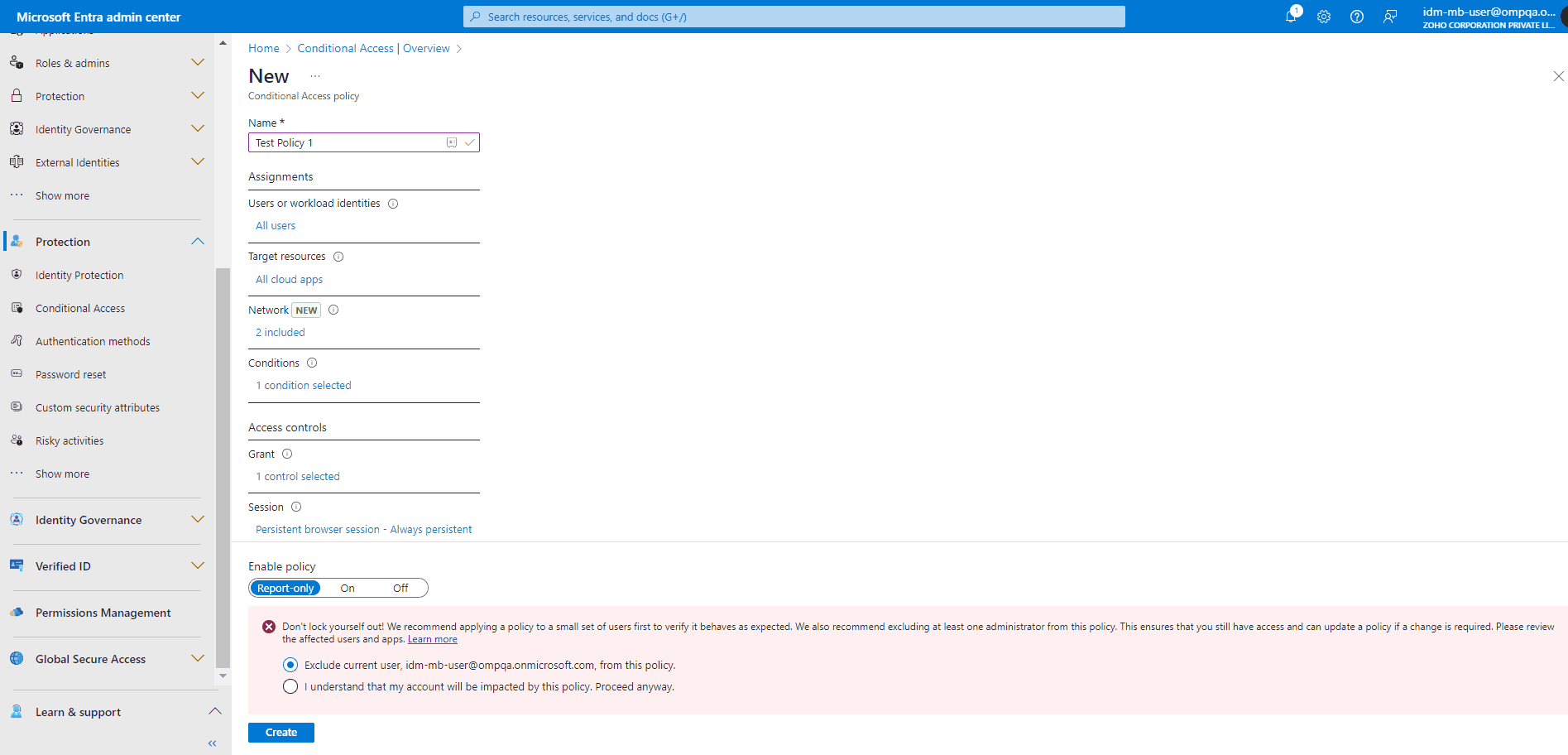
Build smarter Conditional Access policies.
Disabling a user account does not immediately end their active sessions. Until the user logs out or their tokens expire, they may still access resources, even critical ones. To prevent this, you must revoke their session tokens explicitly. Forcing a logout ensures that no lingering access persists after the user’s permissions should have ended.
Note: As of May 31, 2025, you can only bulk edit 60 users in a single operation using the Microsoft Entra admin center. To revoke access for more users in a single go, you will have to use Microsoft Graph PowerShell.
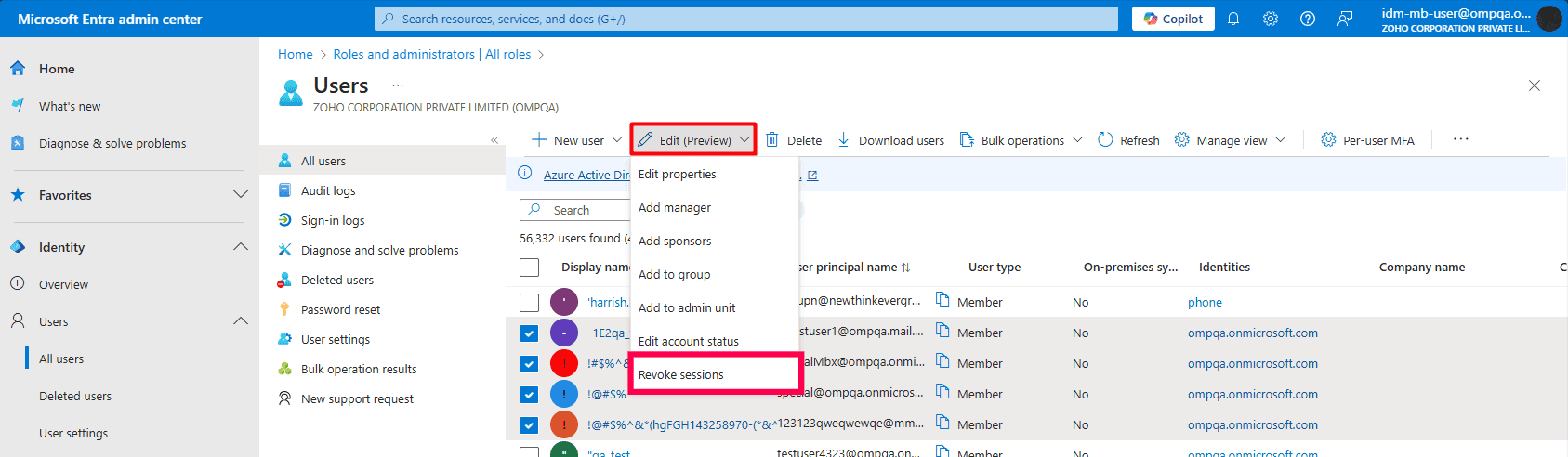
Revoke sessions in Entra ID efficiently in bulk using Microsoft Graph PowerShell.
Even the best access controls need to rely on strong monitoring to stay effective. Without visibility into how users are signing in and where risks are emerging, you cannot get the right data to take timely actions, block suspicious sessions, or strengthen conditional access.
By surfacing user-level risk early, you reduce the likelihood of silent breaches or delayed responses.
Entra ID includes built-in risk detection that continuously evaluates sign-ins for potential threats. It assesses factors such as sign-ins from unfamiliar locations, leaked credentials, or behavioral anomalies, and flags them using machine learning and Microsoft threat intelligence.
This automated system helps you catch high-risk activity early without relying solely on static rules or manual oversight.
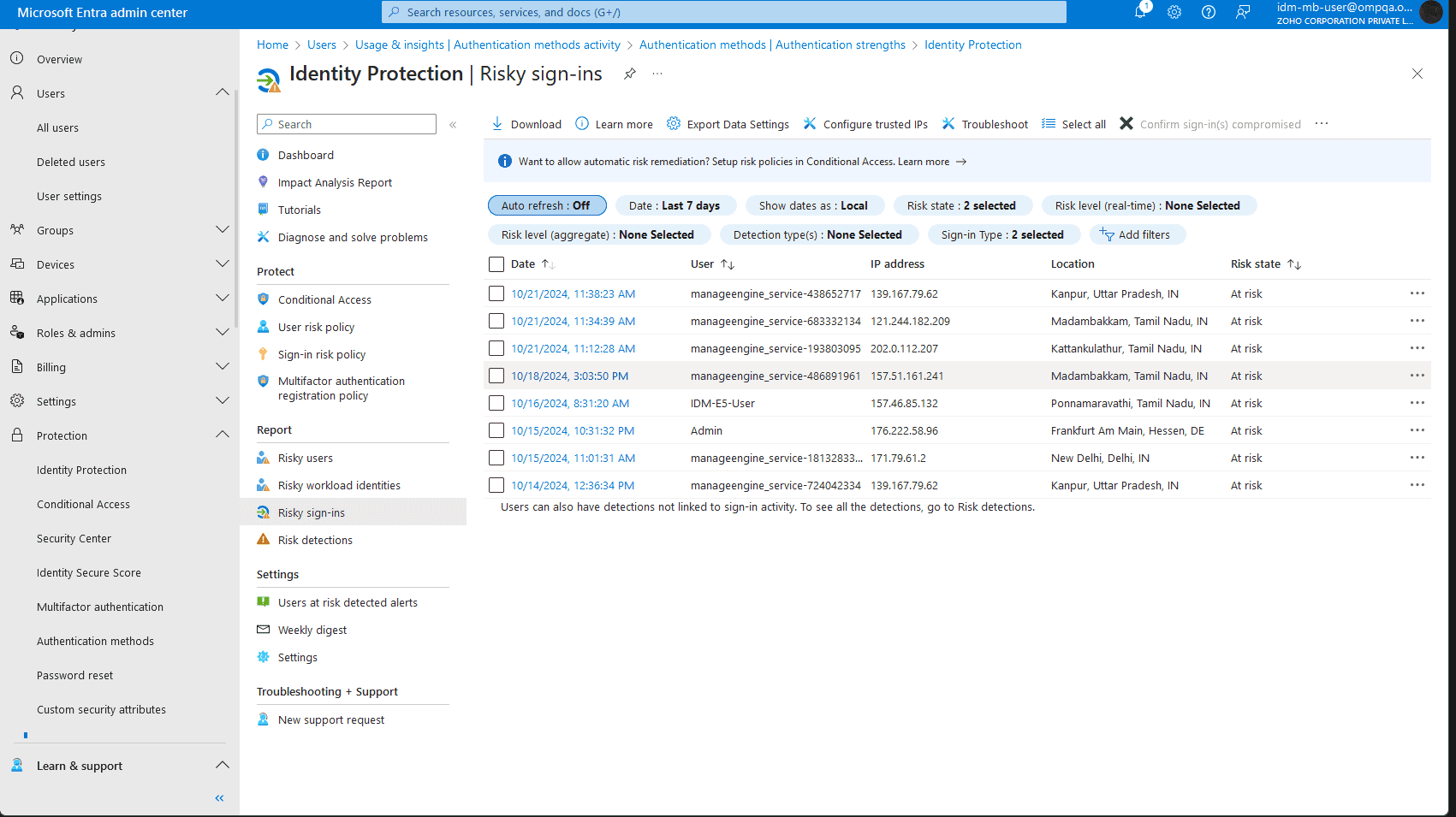
Stay ahead of threats by monitoring risky users in Entra ID.
While Entra ID’s risk detection handles most common threats, it may not catch every edge case, especially if users behave unusually without triggering risk thresholds.Manual log reviews using Microsoft Graph PowerShell give admins deeper visibility, not just for uncovering missed risks, but also for auditing user activity, troubleshooting access issues, and validating login behavior across different contexts.
This helps refine your overall monitoring posture and supports audit, investigation, or compliance needs.
Track login activity across Microsoft 365.
As your Entra ID environment grows, so does the need for precise, scalable access control. Without clear boundaries and regular oversight, it becomes easy for permissions to accumulate unchecked, increasing the risk of privilege abuse, data exposure, and significant lateral movement if one of the admin accounts is ever hacked.
The following measures help keep your administrators' influence in check without compromising oversight.
Predefined roles in Entra ID cover most standard use cases, but they often grant broader permissions than necessary. Creating custom roles allows you to define exactly what privileges an administrator or operator should have—no more, no less.
By scoping access to only the actions required for a given responsibility, you reduce the risk of accidental misconfiguration, insider threats, and unnecessary exposure of critical systems.
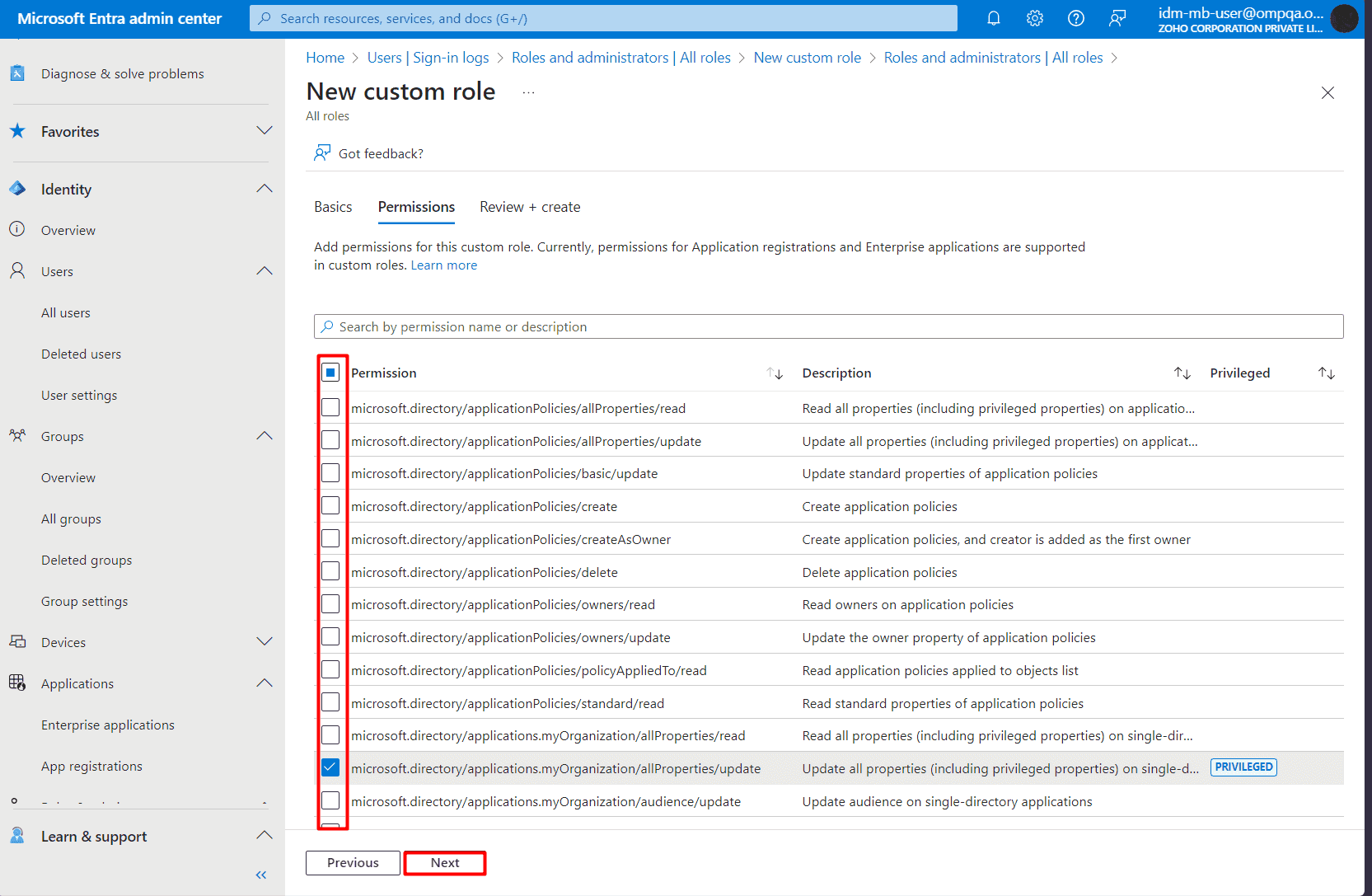
Build tailored access controls with custom Entra ID roles.
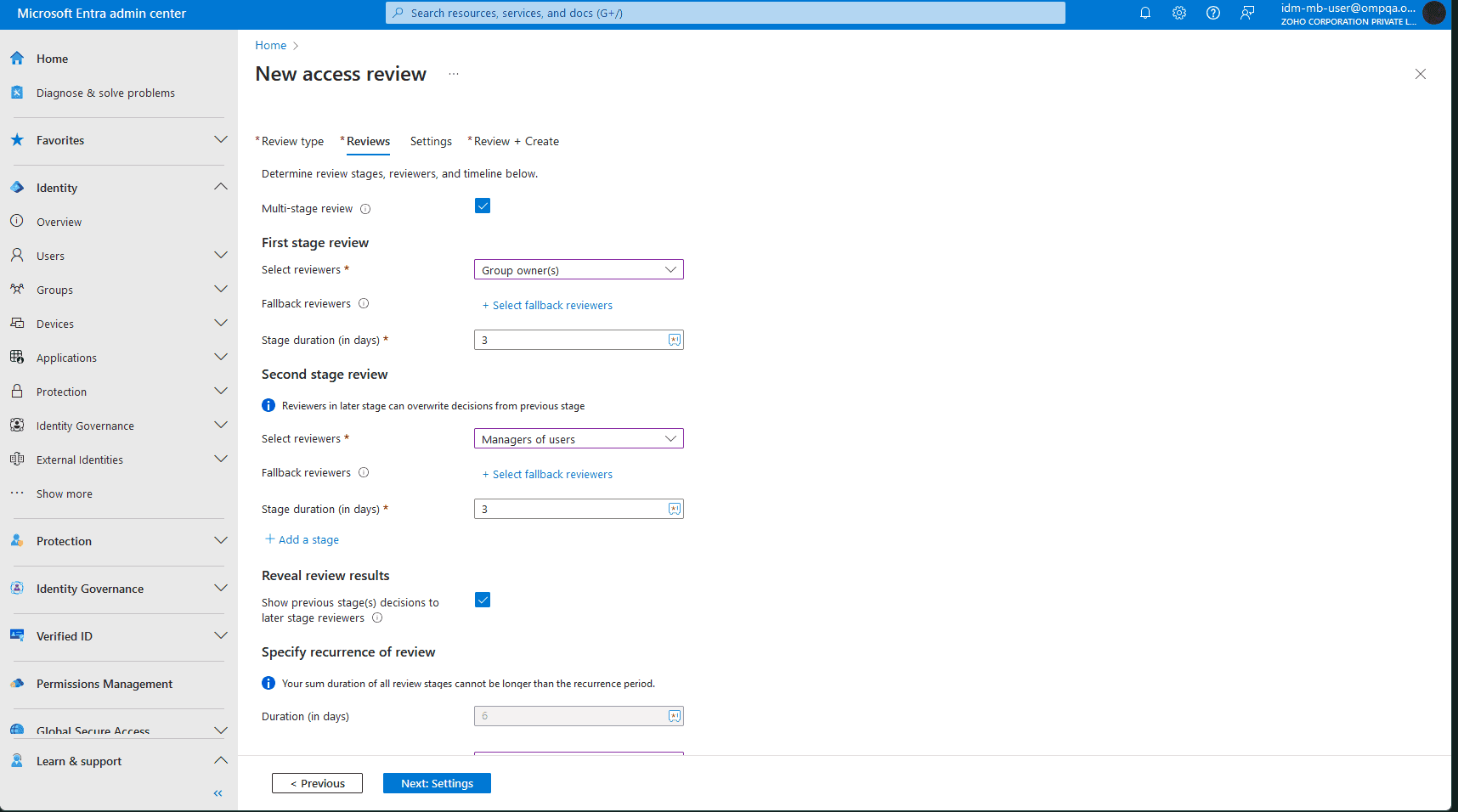
Assigning access is only half the battle; keeping permissions aligned with actual needs over time is even more critical. Access Reviews in Entra ID help automate the process of revalidating user access to groups, applications, and roles, based on your organization's ever-changing requirements.
By prompting users or managers to confirm whether access is still needed, you can catch unnecessary permissions early and reduce the risk of privilege creep.
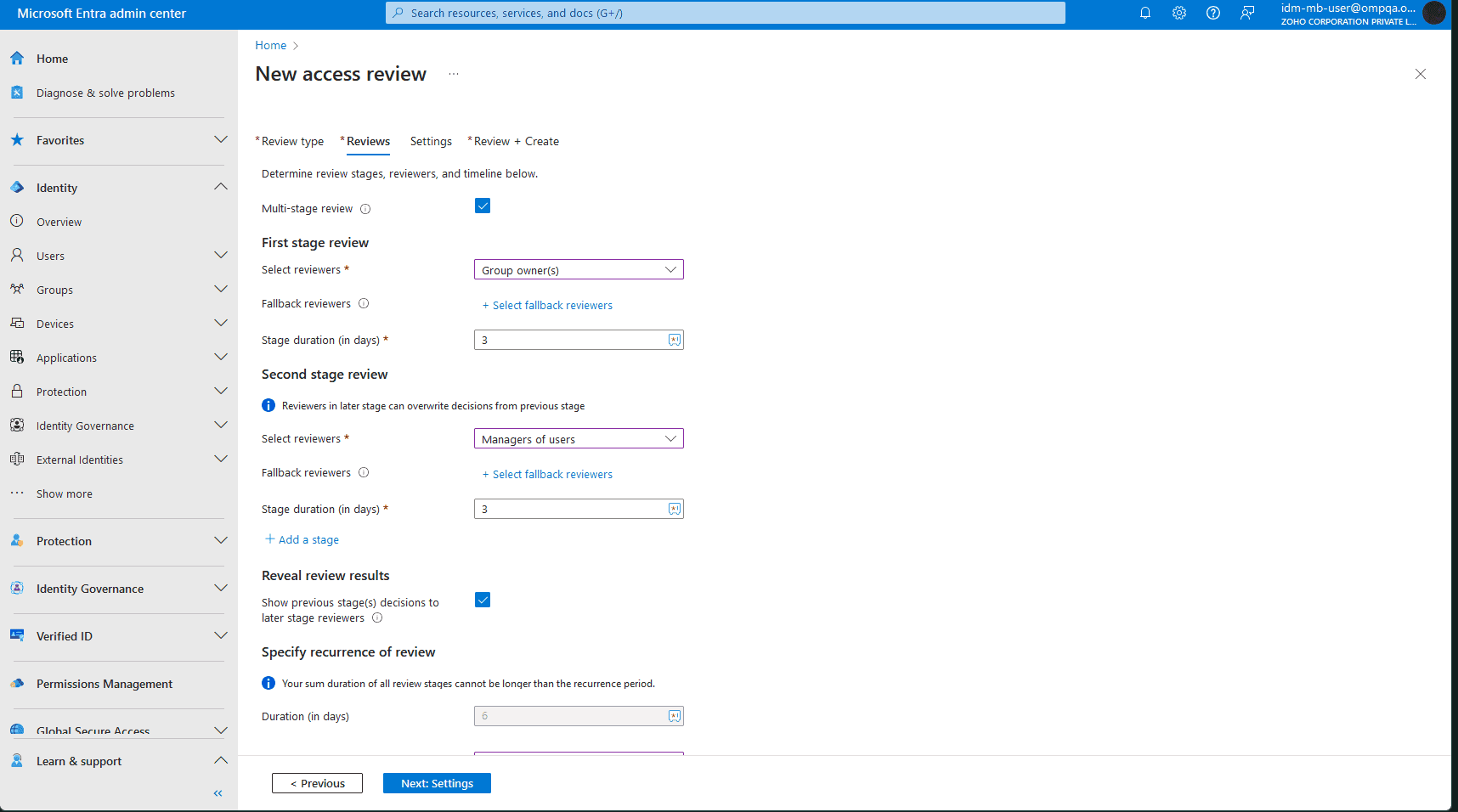
Enforce least privilege with Microsoft Entra Access Reviews.
As your directory scales, controlling who can access which users and resources becomes critical for maintaining security and access boundaries. Administrative Units in Entra ID allow you to partition your directory so that delegated Entra admins can only manage the users, groups, and devices assigned to them without visibility or control over the rest of the tenant.
This ensures that administrative authority is properly scoped while reducing the risk of data overexposure.
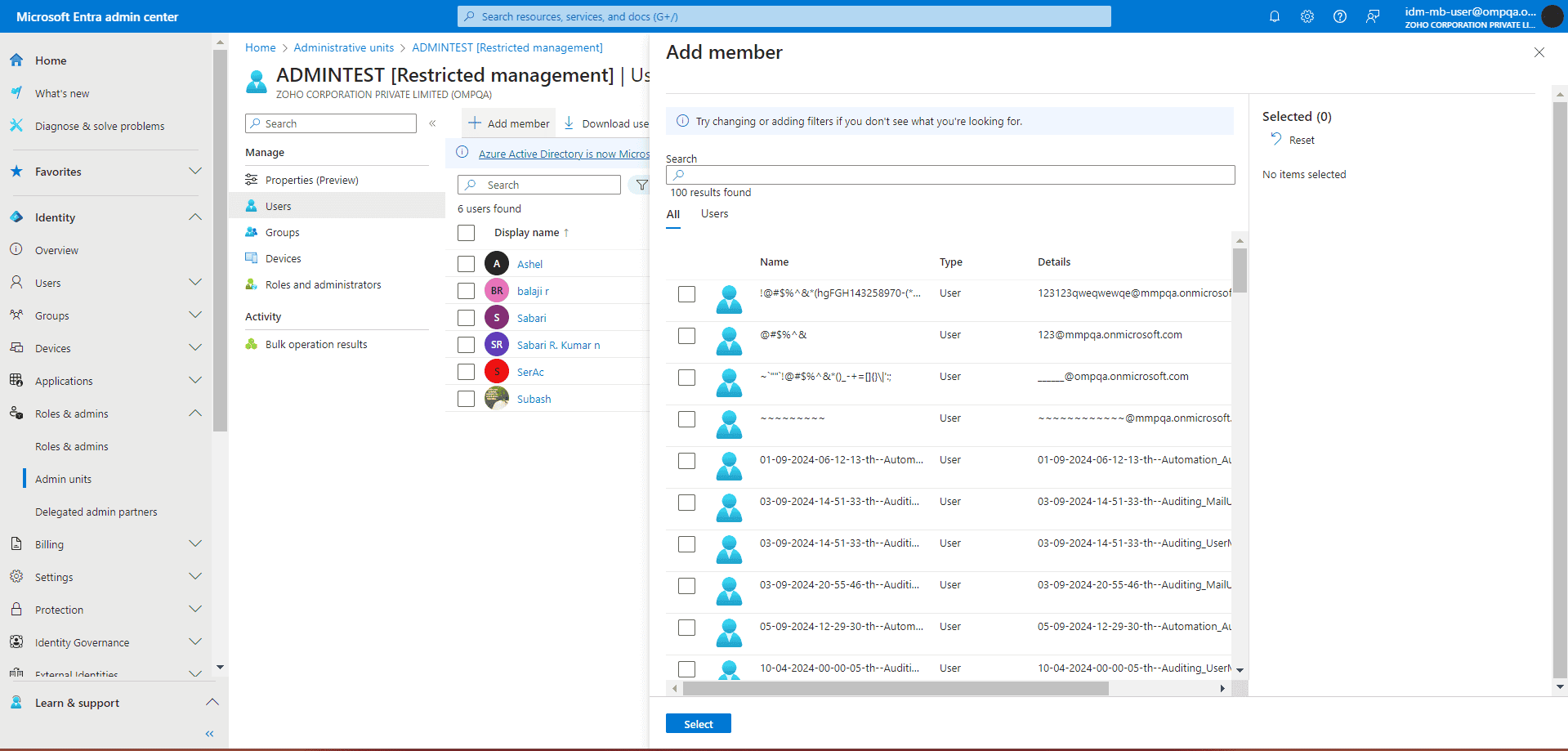
Delegate control safely with Administrative Units.
Once your identity environment is stable and well-governed, the next step is gaining deeper insights into how your changes impact it. Workbooks in Entra ID let you visualize trends—such as sign-in patterns, risky behaviors, and authentication methods—through customizable dashboards. These insights can reveal shifts that raw logs alone might miss, helping you refine your policies by understanding your environment more clearly.
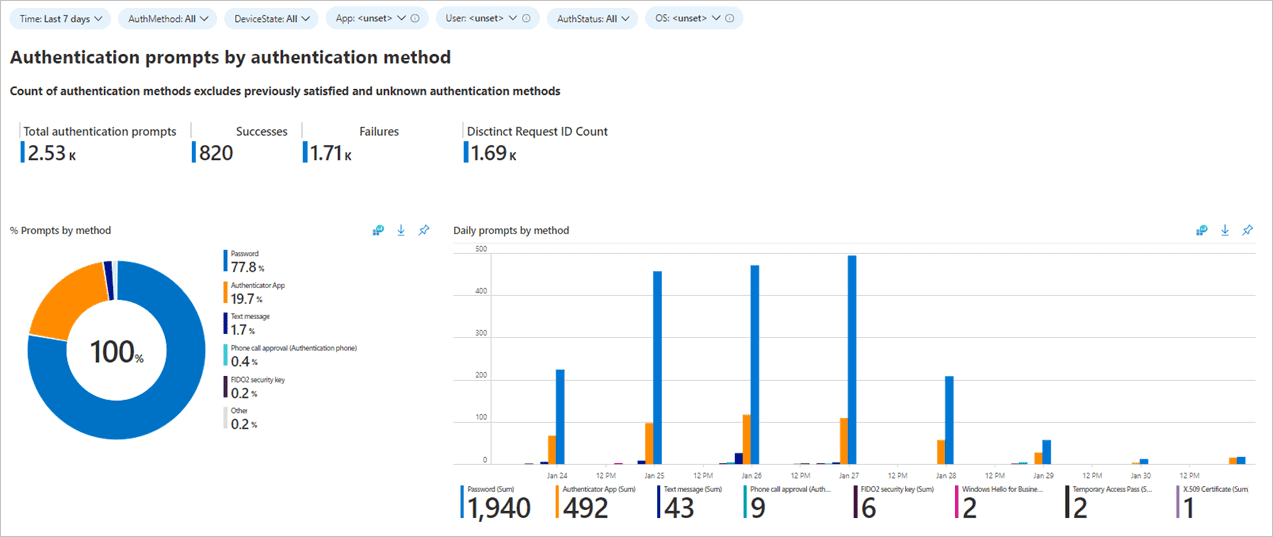
Bring your Entra ID data to life with Entra Workbooks.
Improving your Entra ID environment doesn’t always require sweeping changes. Often, small, focused improvements—such as cleaning up inactive users, tightening access controls, or monitoring sign-in risks more closely—create the biggest long-term impact. If you're looking for a way to accelerate and simplify these improvements, ManageEngine M365 Manager Plus is the perfect administrative assistant for you.
M365 Manager Plus is a comprehensive administration and security solution for Microsoft 365 used for reporting, managing, monitoring, auditing, and creating alerts for critical activities in your Microsoft 365 environments.
Here's how M365 Manager Plus helps you move faster, stay secure, and manage your Microsoft 365 environment with less effort: