Direct Inward Dialing: +1 408 916 9890

Devices are the frontline access points to your organization's resources. Over time, stale or unused devices can accumulate in Microsoft Entra ID, cluttering your tenant, and creating unnecessary risks and entry points that can be exploited if left unsecured or not properly removed. For IT administrators, understanding how device identities are registered, maintained, and secured in Entra ID moves well beyond just creating and removing devices toward managing them for security and compliance.
This blog will focus on how you can set up a secure device cleanup process within Microsoft Entra ID by identifying, reviewing, and cleaning up stale entries efficiently and highlighting best practices to uphold this process.
In Microsoft Entra ID, a device represents any endpoint, such as a Windows PC, Mac, Android smartphones, or iPhones, that has been enrolled or registered for identity verification and access control. These device records serve multiple purposes, from supporting secure and seamless sign-ins into Microsoft 365 services, being used to determine access rights under Conditional Access policies, and tracking user activity not just across services, but also out of them. You can view and manage these device entries directly from the Microsoft Entra admin center by navigating to Identity > Devices>All Devices.
Each record provides important metadata, such as the device's name, ID, Operating system, Version, Owner, Last sign-in, the type of device (corporate or personal), and more. Clicking on any device shows the roles assigned to it, the administrative units it is a part of, and its BitLocker keys.
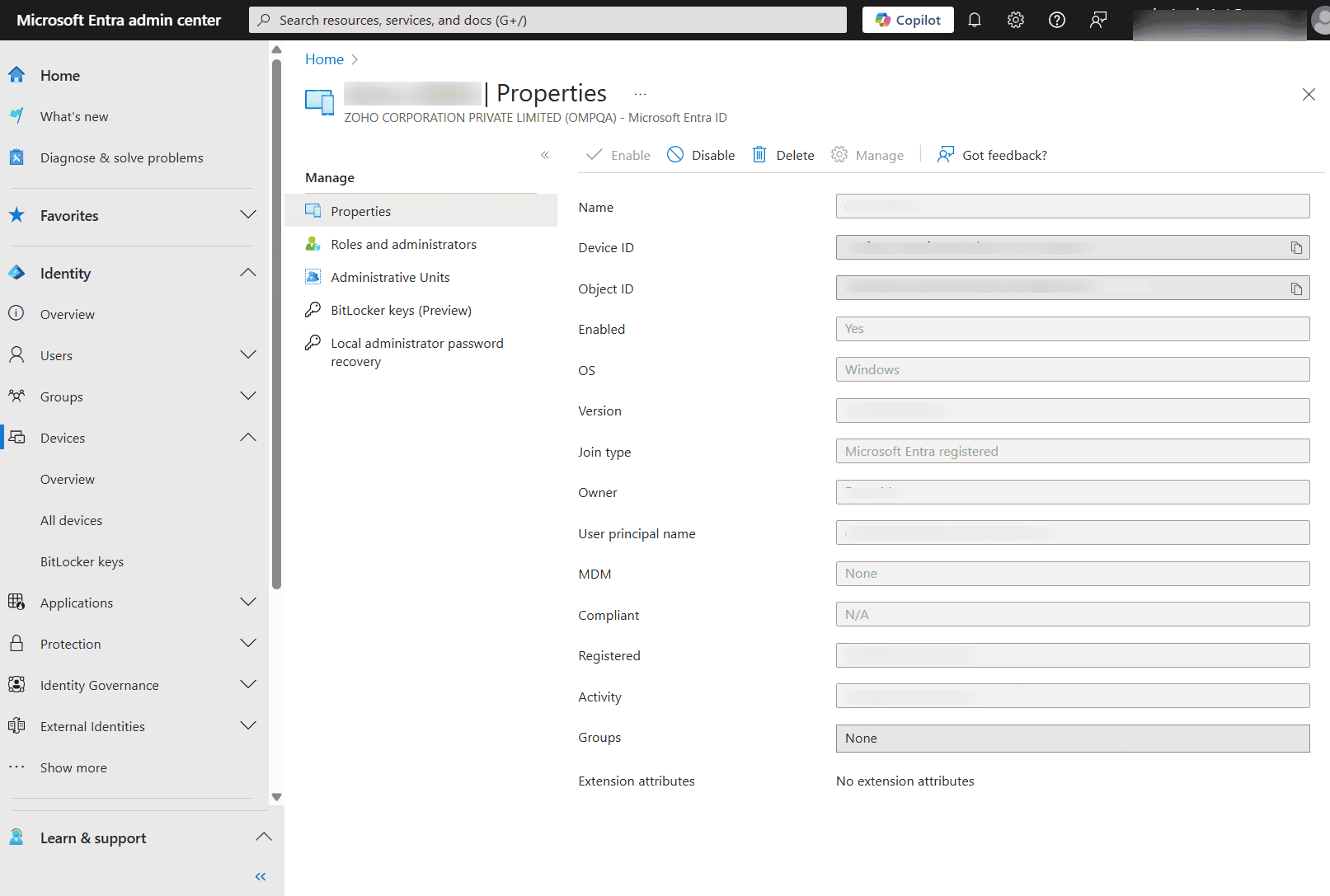
Before diving into cleanup strategies, it is crucial to understand how Microsoft Entra ID categorizes devices and what actions are available for IT administrators to take. This will help IT admins decide the right course of action for the appropriate devices. There are two main concepts:
The state of a device affects how it interacts with your environment, which policies it falls under, and how you should approach its life cycle management. The two device states you need to decide between are Entra Registered vs Entra Joined devices.
Entra Registered devices are used with a device local account, and not the organization's account. When they are added to Microsoft Entra ID, they can be granted access to resources. However, this does not mean the device is compliant or enrolled into MDM services such as Microsoft Intune, so they cannot be managed as granularly or securely as an enrolled device. Personal devices of employees, or BYOD devices that are added by users, and not owned by the organizations, will be marked Registered.
Entra Joined devices are tied to the organization. You need to sign in to your designated Microsoft 365 account to access the device. These devices are set up to be enrolled into your configured MDM services out-of-the-box. These devices can be controlled to a greater extent compared to Registered devices, such as requiring them to be secured with a specific lock method, encrypting their storage, tracking their location, and more.
There are two actions you can take when you determine if a device is not required for your organization. Disable the device to prevent access but retain it in your organization, or delete it if you wish to remove it from your Microsoft 365 environment.
Disabling a device prevents it from authenticating to Microsoft Entra ID. This means even if the device is acquired by a third party, the device cannot be accessed using any organization accounts, and thereby the organization's resources. However, this is not an be-all-end-all case. The device can be enabled later, and all of its access permissions and policies will stay intact. In many cases, this action is suggested when you find a device suspicious and want to assess it.
When you delete a device from Microsoft Entra ID, the device is erased from the directory, all policies applied on it will no longer affect the device, and the device can no longer communicate with the organization's tenant. This action must be carried out when the device is off-boarded out of the organization. If you wish to bring back this device, you will have to treat it as a new device and create the device registration again from scratch.
Now you know what you need to do to off-board your devices. However, you now need to know how to find the stale or inactive devices you need to focus on.
Cleaning up stale devices in Microsoft Entra ID starts with one fundamental task: identifying which devices are no longer active. A stale device refers to any endpoint that hasn't connected to Microsoft Entra ID for a long time. There can be several reasons why these devices are inactive:
Whatever the reason is, you can access the device's details from the All Devices menu. You can find the Activity timestamp of its last sign in, find out its Owner, and more information to assess their compliance yourself, and take a call on how to proceed.
Here is a Microsoft Graph PowerShell script to help you get the list of devices that have been inactive for the last 30 days.
Connect-MgGraph -Scopes "Device.ReadWrite.All"
$devices = Get-MgDevice | Where-Object {
$_.ApproximateLastSignInDateTime -lt (Get-Date).AddDays(-30)
}
Now that you have discovered the devices you want to remove from Entra ID, you will have to decide if they actually need to be removed right away. Disabling a device before you decide to delete it can help you in more ways than one.
Once you pass these checks, you can delete the device if you wish to off-board it completely.
The go-to method is to select the devices in the All Devices menu and click Disable or Delete. However, it becomes less practical to execute when there are hundreds of devices to clean up every month, and you cannot just click all of them and be done with it. Instead, automating the process is more efficient.
Here are two Microsoft Graph PowerShell scripts that you can use to automate your stale device cleanup in Entra ID.
This script disables devices that have been inactive for over 30 days:
Connect-MgGraph -Scopes "Device.ReadWrite.All"
$devices = Get-MgDevice | Where-Object {
$_.ApproximateLastSignInDateTime -lt (Get-Date).AddDays(-30)
}
$devices | ForEach-Object {
Write-Host "Disabling device:" $_.DisplayName
Update-MgDevice -DeviceId $_.Id -AccountEnabled:$false
}
Use this script to delete Entra ID devices that have been disabled for more than 30 days:
Connect-MgGraph -Scopes "Device.ReadWrite.All"
$thresholdDate = (Get-Date).AddDays(-60) # 30 days inactive + 30 days disabled
$staleDevices = Get-MgDevice | Where-Object {
$_.ApproximateLastSignInDateTime -lt $thresholdDate -and
$_.AccountEnabled -eq $false
}
$staleDevices | ForEach-Object {
Write-Host "Deleting device:" $_.DisplayName
Remove-MgDevice -DeviceId $_.Id
}
You can also use these scripts in your Power Automate flows and run them automatically every month to automatically disable Entra ID devices and delete them if they go inactive for a long period of time.
Note: Some Microsoft Entra devices are identified as Hybrid Join where the device is registered in both your on-premises Active Directory and Microsoft Entra ID. You will have to make sure the device is removed from your AD environment before you delete it in Microsoft Entra ID. Not doing so can cause directory sync failures, and removing the device only from Microsoft Entra ID does not prevent it from accessing your on-premises environment. Failing to do so might allow the device to retain access to your on-premises resources despite removal from Entra ID.
Managing multiple devices and identities across Microsoft 365 can quickly become overwhelming. Entra often requires IT admins to juggle multiple tools, scripts, and portals to perform routine tasks such as cleaning up stale devices, assigning licenses, or managing user access. Without a centralized system, this fragmented approach increases security risks, wastes time, and leaves room for human error.
ManageEngine M365 Manager Plus simplifies this chaos. It brings Microsoft 365 identity management across multiple services into a single, centralized console, reducing the complexity of routine administration while strengthening control over your Microsoft 365 environment.
This also includes Microsoft 365 device management. Easily identify and remove stale or orphaned devices using custom filters. Sensitive data on enrolled mobile devices can be wiped remotely, reducing security risks. Every cleanup action is documented through audit-ready reports, eliminating the need to rely on Graph API scripts for basic hygiene tasks.
Beyond device cleanup, M365 Manager Plus delivers other benefits, including:
Download the free, 30-day trial of M365 Manager Plus to see these features in action for yourself and explore the other features this tool has to offer. Contact us for a free, personalized demo on setting these features up to secure your Microsoft 365 environment.