Direct Inward Dialing: +1 408 916 9890

Starting on Oct. 15, 2024, Microsoft Entra ID, Microsoft Intune, and other Microsoft Azure applications will require users to sign in with Microsoft Entra MFA. With increasing threats of account takeovers and large-scale phishing attacks targeting Microsoft Entra ID users, this looks to be a step in the right direction.
However, this mandate also brings with it some practical concerns that admins need to know about before preparing their organizations for this mandate. Continue reading to see why Microsoft will mandate MFA for Microsoft Entra ID and Azure sign-ins, how Microsoft plans to implement it, some of the possible concerns this move might bring, and how ManageEngine M365 Manager Plus can help your organization prepare for this in an efficient way.
MFA has always been a major help in securing access to user accounts, applications, resources, and more. However, implementing it across an organization is often a hassle. Setting up and using MFA is often seen as difficult due to admins having to adjust configurations and users having to learn the new flow of authentication.
However, the benefits far outweigh the cost and effort of setting up MFA. A recent study by Microsoft found that 98.56% of MFA-enabled accounts are secured from breaches involving leaked credentials because even when credentials are exposed, they are not useful when authentication is not solely dependent on them. As long as the user can secure their authentication factor, which is easier to secure than a text-based password, their access is mostly secured.
Microsoft already sowed the seeds for this mandate way back in November 2023 with the introduction of three default Conditional Access policies. These policies are in report-only mode, and admins can choose to implement them now or opt out until they are enforced automatically on Oct. 15, 2024.
However, this is not the main action plan of the mandate. Microsoft has sent out advance email notices to all global administrators that they will be required to use MFA to log in to their admin centers and, eventually, other administrative resources, too. This will be carried out in two phases.
While these are the official phases announced as of September 2024, Microsoft has also stated that it plans to "ensure 100% of user accounts are protected with securely managed, phishing-resistant multi-factor authentication." So, it wouldn't be a surprise if MFA is mandated for non-admin users sometime soon.
Now that we have an overview of what the mandate is about, we can dive into the common concerns this raises for admins.
Only users who sign in to the applications mentioned above with a user role that supports create, read, update, or delete operations will be required to configure MFA to access these applications, though it is always a good idea for every user to set up MFA to secure their access.
Users who do not have MFA configured for their accounts before the deadline will be prompted to register for Microsoft Entra MFA and to set up their preferred MFA methods when they sign in after the deadline.
If your organization or even a specific tenant is not ready to set up MFA before the deadline, one of your global administrators will have to apply for a grace period on this page before Oct. 15, 2024. This will postpone the enforcement date for your tenant to March 15, 2025.
To satisfy this mandate, you need to set up MFA using Conditional Access or per-user MFA. Conditional Access policies help you set up multiple verification steps and change the required methods depending on the sign-in conditions, like the location and time. Per-user MFA enables you to set up MFA for individual users if you do not prefer to use Conditional Access.
To configure MFA for your users in tenants with MicrosoftEntra ID Free licenses without any additional costs, you can enable security defaults in your tenant's properties, which will require all users and admins to register for MFA using the Microsoft Authenticator app or any third-party application using OATH TOTPs.
While MFA requirements previously could be bypassed using Conditional Access policies configured with trusted IPs, locations, and other factors, it will not possible to do the same with this mandate's policies in effect. We reached out to Microsoft to ask how this MFA mandate will be implemented, and Microsoft informed us that this will be done using a Conditional Access policy that will not be accessible to any of the tenant members and will only target the listed applications.
Microsoft stated in its reply to our questions that if any user objects are used as service accounts to run scripts or other automations, they will also need to undergo MFA once the mandate is in effect. Workload identities, such as applications, managed identities, and service principals, will not have to authenticate with MFA, and it is recommended that you convert your service accounts into workload identities.
Configuring MFA is an essential security measure for your company, and ensuring that all your users have MFA enabled is even more important. Monitoring the usage of MFA throughout your organization helps reduce the chances of unauthorized access to your users' accounts.
ManageEngine M365 Manager Plus is a comprehensive tool used for reporting, managing, monitoring, auditing, and creating alerts for critical activities in your Microsoft 365 environment. It can help you plan and execute your MFA implementation with detailed reports that can be used to effortlessly set up MFA for your users in bulk.
Here is how you can use M365 Manager Plus to optimize your MFA implementation campaign:
The Multi Factor Authentication Status report in M365 Manager Plus gives you the details of the MFA methods configured for your users in Microsoft Entra ID (Fig. 1). If any of your users have not configured MFA for their accounts, their status will be shown as Disabled. You can filter for such entries in the report and select them for your MFA implementation.
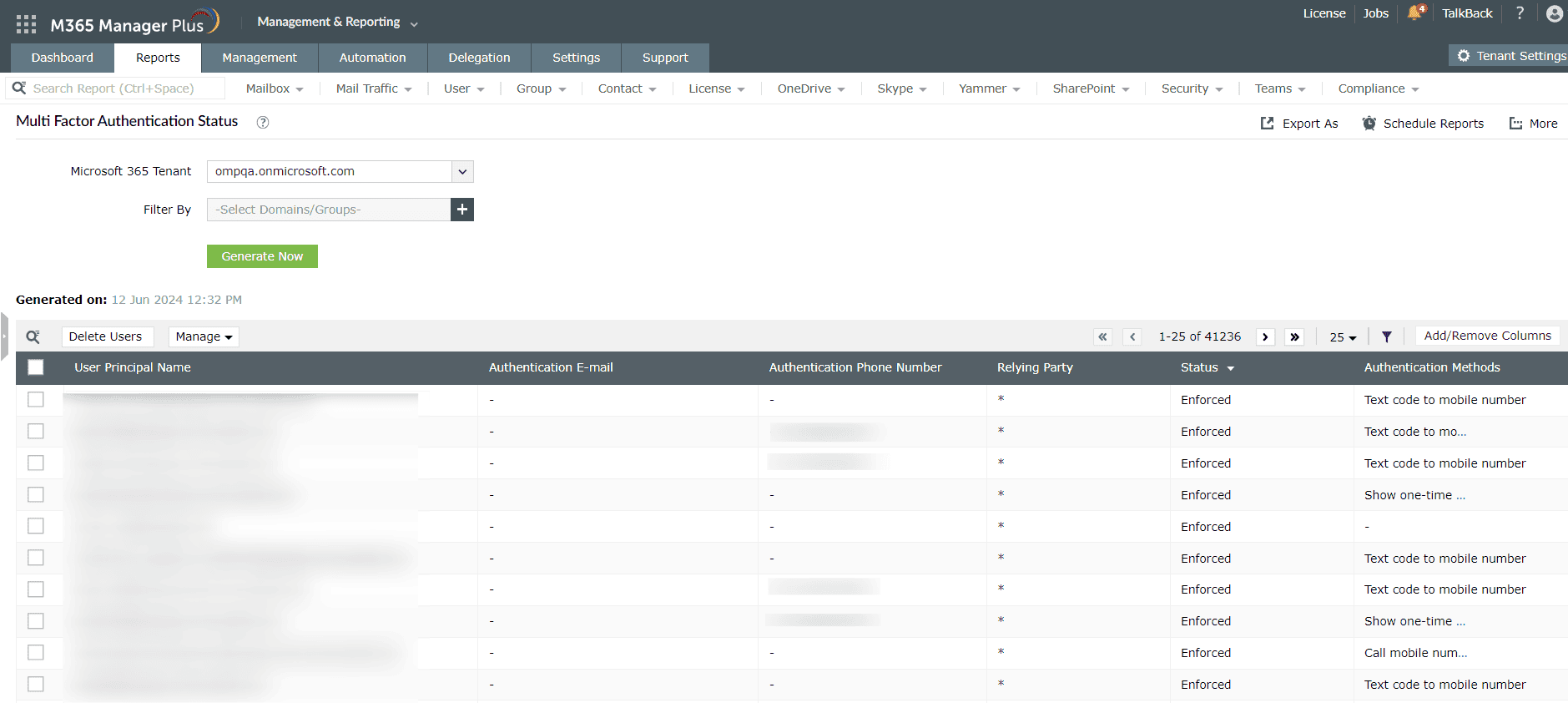
Figure 1. The Multi Factor Authentication Status report in M365 Manager Plus.
Once you select the users for whom you want to configure MFA, you can select the MFA Settings management task from the same report. You can set the allowed MFA methods and the default method to use. You can also choose to just enable MFA for users and let them select their own authentication methods, or you can enforce MFA with the available authenticators.
Download the free, 30-day trial of M365 Manager Plus to see these features in action for yourself and explore the other features this tool has to offer. Contact us for a free, personalized demo on setting these features up to secure your environment.