How to check non-owner mailbox access in Microsoft 365
Last updated on:In this page
- How to get a non-owner mailbox access report using the Microsoft Purview compliance portal
- How to check non-owner mailbox access using Exchange Online PowerShell
- How to run a non-owner mailbox access report in M365 Manager Plus
- Monitor your Exchange Online environment and more
- Important tips
- Frequently asked questions
Regularly auditing non-owner mailbox access is a critical security and compliance task. Unmonitored access can lead to data breaches or compliance failures, especially when sensitive information is involved.
For administrators, manually checking audit logs to track this activity is complex and time-consuming. Without a clear, efficient way to report on non-owner access, it is difficult to detect suspicious behavior, verify appropriate permissions, and respond to security incidents promptly.
- Microsoft Purview
- Graph PowerShell
- M365 Manager Plus
Method 1: How to get a non-owner mailbox access report using the Microsoft Purview compliance portal
Prerequisites
You must be assigned at least the Audit Reader role to access and run audit log searches in the Microsoft Purview compliance portal.
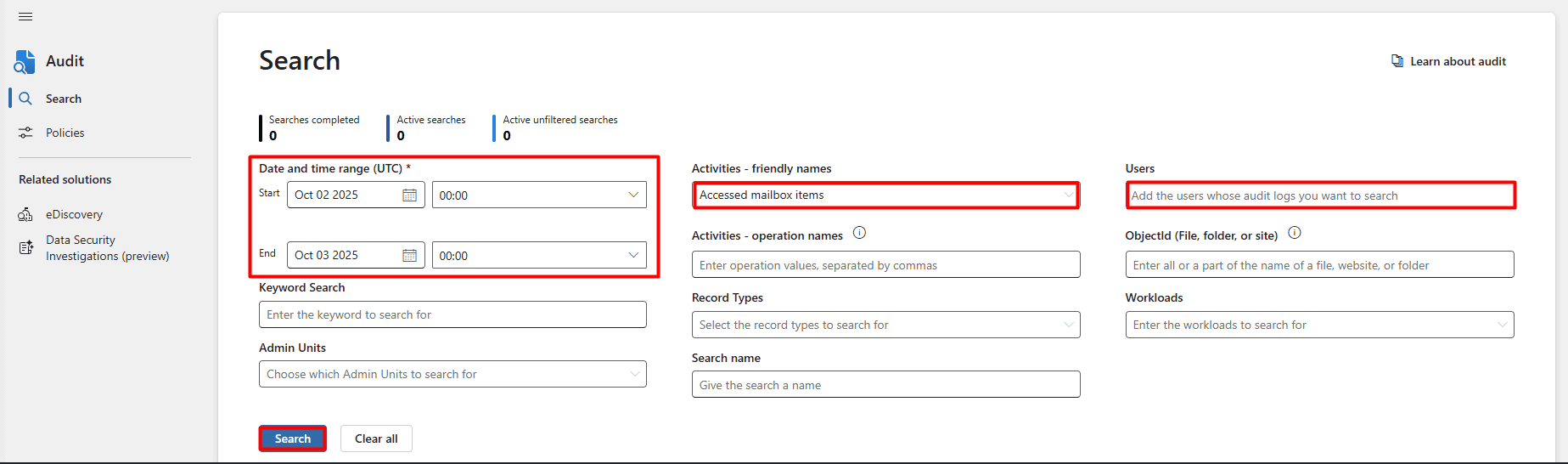
- Log in to the Microsoft Purview compliance portal and select Audit from the sidebar or the main menu.
- Configure the Start and End fields with the required dates.
- In the Activities - friendly names drop-down, search for and select Accessed mailbox items. This logs access by non-owners.
- In the Users field, type the mailboxes you want to investigate. You can leave this blank to search all mailboxes.
- Click Search to generate the non-owner mailbox access report. This will show which non-owners accessed the specified mailboxes.
Method 2: How to check non-owner mailbox access using Exchange Online PowerShell (Search-UnifiedAuditLog)
Prerequisites
Before using Exchange Online PowerShell, please verify that:
Steps
- The Audit Reader role is applied to the account you use to sign in to Exchange Online PowerShell.
- You are connected to the Exchange Online module.
- To check if the ExchangeOnlineManagement PowerShell module is installed, use this script:
Install-Module ExchangeOnlineManagement -Scope CurrentUser
Update-Module ExchangeOnlineManagement - Connect to Exchange Online PowerShell with this script:
Connect-ExchangeOnline
- To check if the ExchangeOnlineManagement PowerShell module is installed, use this script:
Using the Search-UnifiedAuditLog cmdlet to run a non-owner mailbox access report
The Search-MailboxAuditLog cmdlet was used previously to parse through mailbox audit logs and retrieve a report of actions taken by administrators and delegates. However, the Search-MailboxAuditLog cmdlet is deprecated.
You will have to use its replacement, the Search-UnifiedAuditLog cmdlet. It queries the Microsoft 365 unified audit log, which contains audit records from various services, including Exchange Online.
Use the following Exchange Online PowerShell cmdlet to run a non-owner mailbox access report:
Search-UnifiedAuditLog -StartDate (Get-Date).AddDays(-7) -EndDate (Get-Date) -RecordType ExchangeItem -Operations MailItemsAccessed -UserIds "mailbox@yourdomain.com" |
Where-Object {($_.AuditData | ConvertFrom-Json).MailboxLoginType -ne "Owner"} |
Select-Object -ExpandProperty AuditData |
Select-Object CreationTime, UserId, Operation, MailboxGuid, LogonType, ClientIPAddress, ClientInfoString, MailboxLoginType Supported parameters
The following table contains some key parameters and properties that can be used with the Search-UnifiedAuditLog cmdlet to provide details on non-owner mailbox access.
| Parameter | Description |
|---|---|
| -StartDate, -EndDate | The date range for the audit log search. |
| -RecordType | Filters the search to a specific type of operation; for this use case, use ExchangeItem to find mailbox-related activities. |
| -Operations | Specifies the exact user or admin activities to search for; MailItemsAccessed is the key operation for tracking who has accessed mailbox items. |
| -UserIds | Specifies the mailbox you want to investigate; provide the email address of the mailbox here. |
| AuditData | A property in the results that contains detailed information about the event in JSON format, including the login type. |
| MailboxLoginType | A field within the AuditData property that identifies the type of user who logged in; for this use case, filter out the owner to find all non-owner access. |
| LogonUserDisplayName | The friendly name of the user who performed the action (the non-owner). |
An example use case to run a non-owner mailbox access report
Scenario: A manager needs to verify which delegates have accessed a specific project-related shared mailbox in the last 30 days to ensure that only current team members are viewing the contents.
This is the cmdlet you will have to run to generate a report of all non-owner access to that mailbox within the last 30 days:
$date = (Get-Date).AddDays(-30)
Search-UnifiedAuditLog -StartDate $date -EndDate (Get-Date) -RecordType ExchangeItem -Operations MailItemsAccessed -UserIds "project.alpha@yourdomain.com" |
Where-Object {($_.AuditData | ConvertFrom-Json).MailboxLoginType -eq "Delegate"} |
Select-Object CreationTime, UserId, Operation, MailboxGuid, LogonType, ClientIPAddress, MailboxLoginType |
Export-Csv -Path "C:\Reports\ProjectAlpha_DelegateAccess_Last30Days.csv" -NoTypeInformation -Encoding UTF8 Method 3: How to run a non-owner mailbox access report in M365 Manager Plus
- Log in to M365 Manager Plus and click the Reports tab.
- Under Other Services, click Security Reports and select the Non-Owner Mailbox Access report.
- Select the Microsoft 365 Tenant, configure the Period, and click Generate Now to view a comprehensive list of all non-owner mailbox access events in your Exchange Online environment.

Monitor your Exchange Online environment and more
M365 Manager Plus empowers you to strengthen security and maintain complete visibility across Exchange Online and your entire Microsoft 365 environment. Its advanced reporting and auditing features simplify mailbox auditing, deliver granular activity logs, and trigger real-time alerts for suspicious or critical events. With its insights, you can detect risks faster, ensure compliance, and monitor your organization’s cloud activity with confidence.
Audit mailbox activity to the letter
Generate detailed, preconfigured audit reports on mailbox access and other Exchange Online activities with just a few clicks. Easily see who accessed which mailbox, what actions they performed, and when they did it—all from an intuitive GUI.
Get notified in real time about suspicious mailbox access
Set up proactive alerts for unusual or unauthorized mailbox access. Get notified instantly when a non-owner accesses a sensitive mailbox, enabling you to take immediate action to mitigate potential threats without complex configurations or separate subscriptions like Microsoft Power Automate and Microsoft Sentinel.
Eliminate PowerShell complexity
Run detailed mailbox audit reports in a single click instead of using complex cmdlets like Search-UnifiedAuditLog. This reduces dependency on scripting, saves valuable time, and minimizes the risk of errors.
Important tips
Regularly audit mailbox permissions: Periodically review who has delegate access to mailboxes, especially sensitive ones, and remove any permissions that are no longer needed.
Check for inactive mailboxes: Many access risks come from permissions left behind after role changes. Reviewing delegate activity against current staff lists helps keep mailbox access clean.
Filter out owner logins: When reviewing access through Exchange Online PowerShell, make sure you check the MailboxLoginType property and exclude “Owner”, as demonstrated in our script.
Frequently asked questions
Non-owner mailbox access refers to any instance where a user other than the primary mailbox owner accesses a mailbox. This is typically done by users with delegated permissions (delegates) or by administrators for management purposes.
Yes. In both the Microsoft Purview portal and PowerShell, you can leave the mailbox field blank to search across your entire tenant. In M365 Manager Plus, you simply choose the tenant and period before generating the report.
Delegate access refers to actions performed by a user who has been granted specific permissions (like Full Access or Send on Behalf) for another user's mailbox.
Administrator access refers to actions performed by a user with an elevated administrative role, often using tools like eDiscovery.
At minimum, you need the Audit Reader role to access non-owner mailbox access events. Without it, you won’t be able to run searches in the Microsoft Purview compliance portal or through PowerShell.
The Search-MailboxAuditLog cmdlet was widely used to search Exchange mailbox audit logs, including for non-owner access. Since it is deprecated now, Microsoft recommends using Search-UnifiedAuditLog, which pulls data from the unified audit log across Microsoft 365. For mailbox access reporting, it provides the same details while offering broader coverage and long-term support.

