Direct Inward Dialing: +1 408 916 9892
ADAudit Plus' identity threat detection and response (ITDR) hardens your Active Directory security with UBA-driven insights, real-time alerts, and deep forensic visibility, enabling you to spot identity-based threats early, perform detailed investigation, and accelerate incident response.
Proactively monitor changes, flag indicators of compromise, and mitigate breaches across your Active Directory environment with ADAudit Plus.
Detect over 25 Active Directory attacks using MITRE-ATT&CK®-aligned detection rules and real-time alerts.
Gain valuable forensic insights with a comprehensive timeline of events before, during, and after breaches.
Initiate rapid response with automated remediation scripts to recover faster and minimize damage.
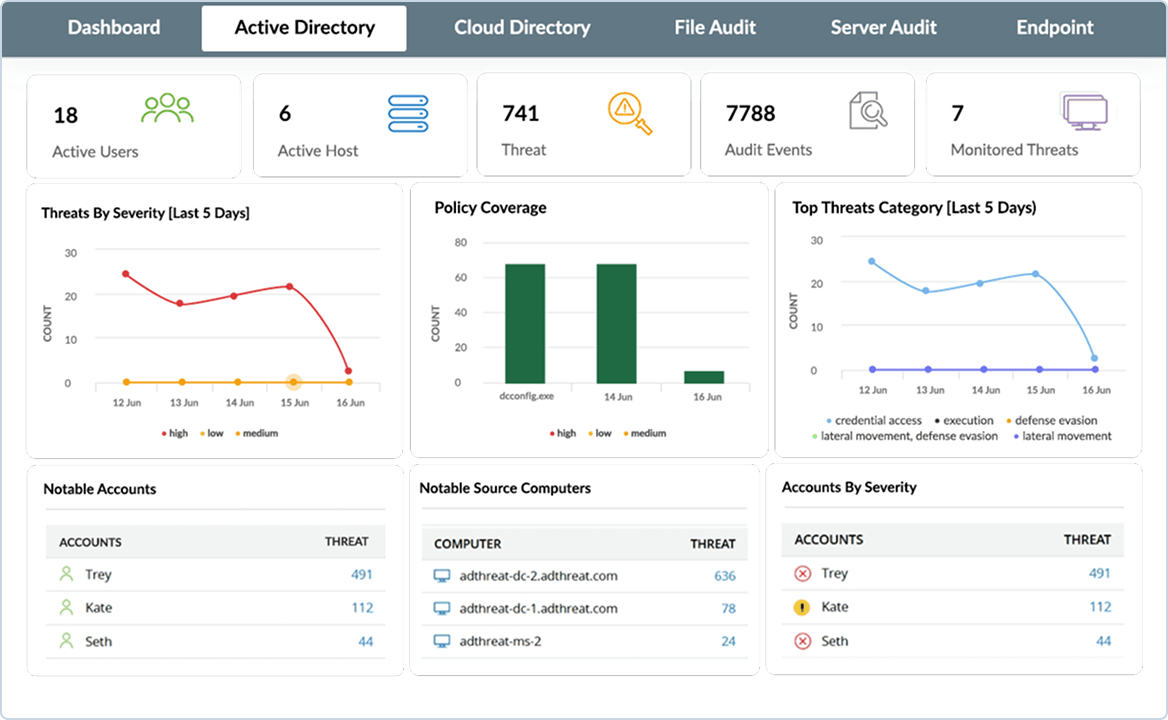
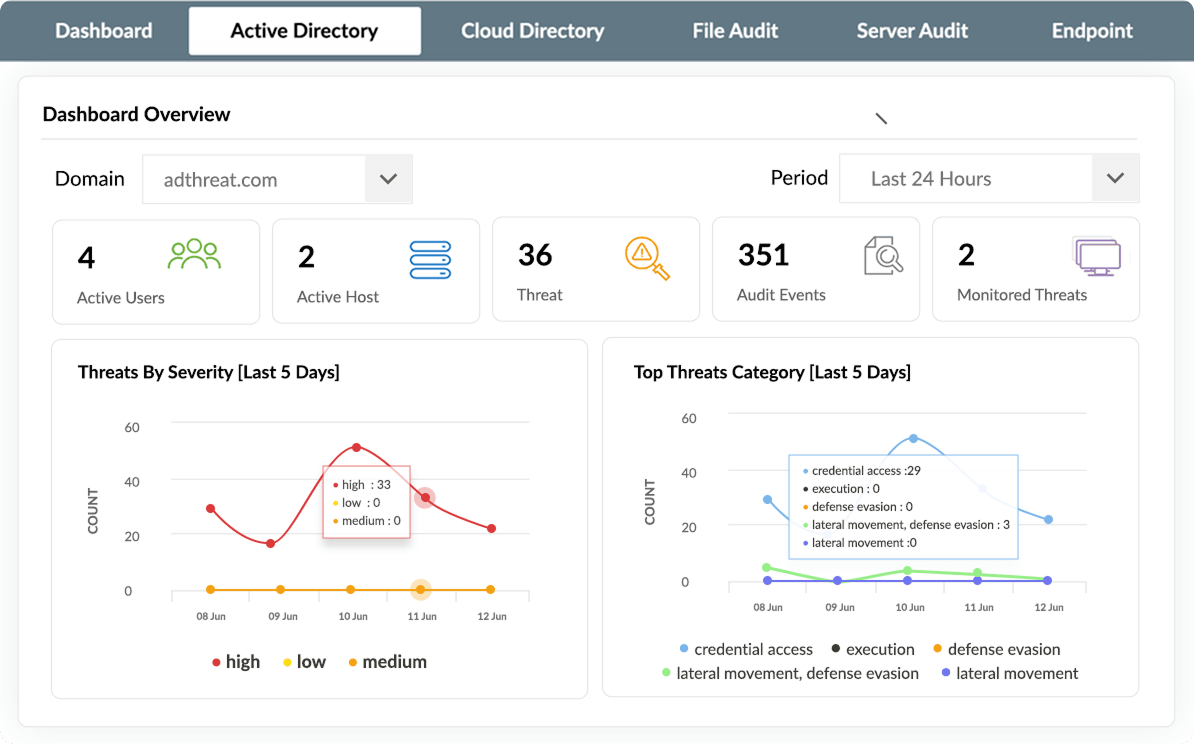
Get a clear picture of your Active Directory security posture with an overview of users, hosts, and threats. Quickly zero-in on threat categories linked to potential indicators of compromise and prioritize remedial actions based on their severity.
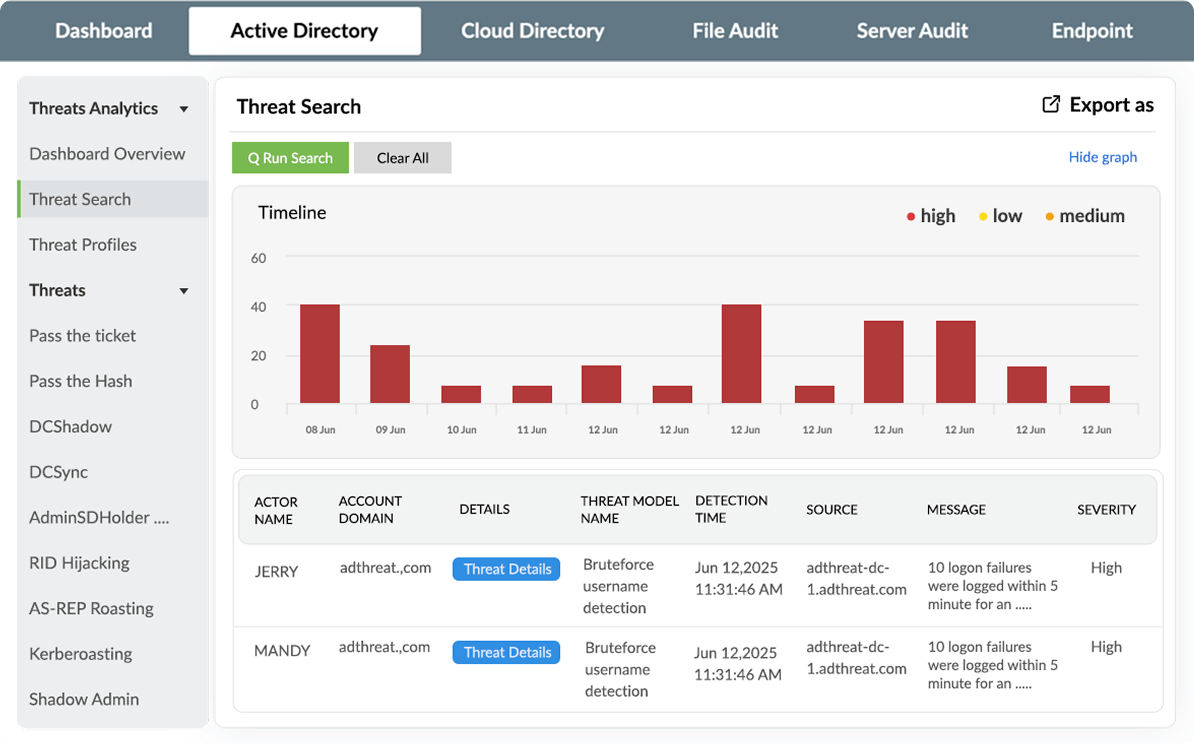
Access in-depth threat reports to identify over 25 common Active Directory attacks, such as Kerberoasting, Golden Ticket, and DCSync. Drill down into contextual evidence for each attack to uncover who did what, when, and where, leading to the exploit.
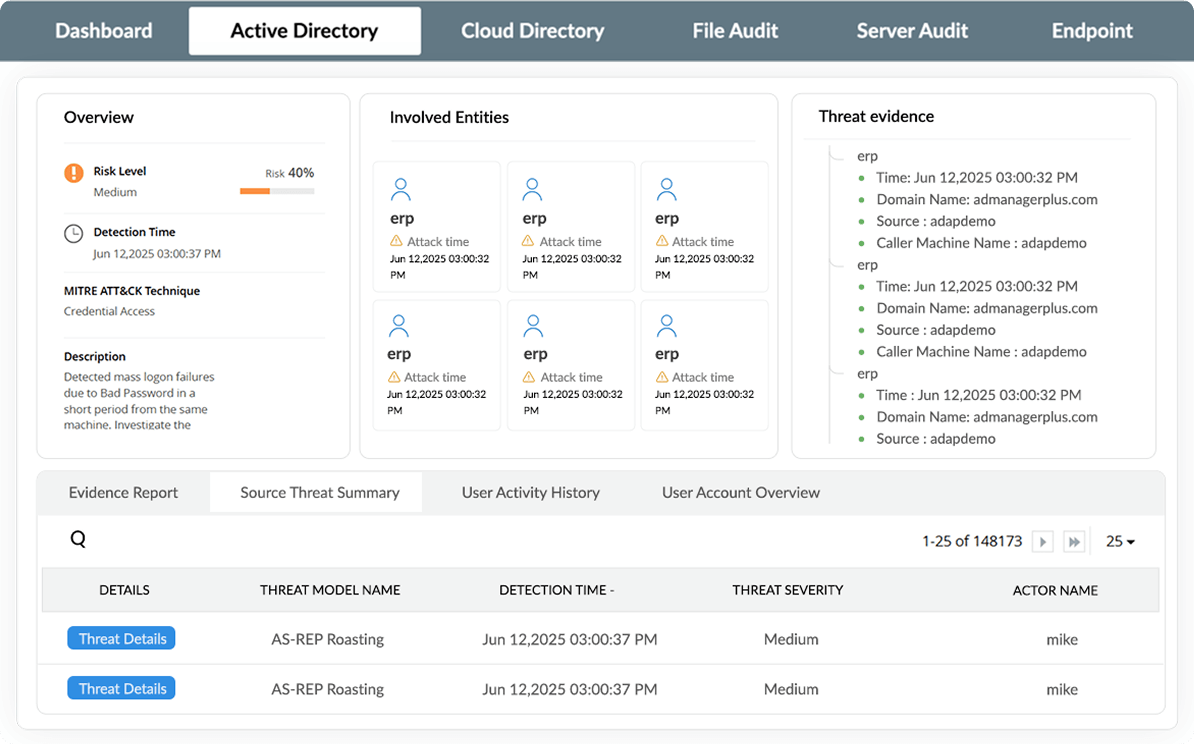
Trace attack paths with a detailed timeline of the attacker's actions to understand how the breach unfolded. Correlate attack evidence with a user's activity history to pinpoint security gaps and vulnerabilities within your Active Directory environment.
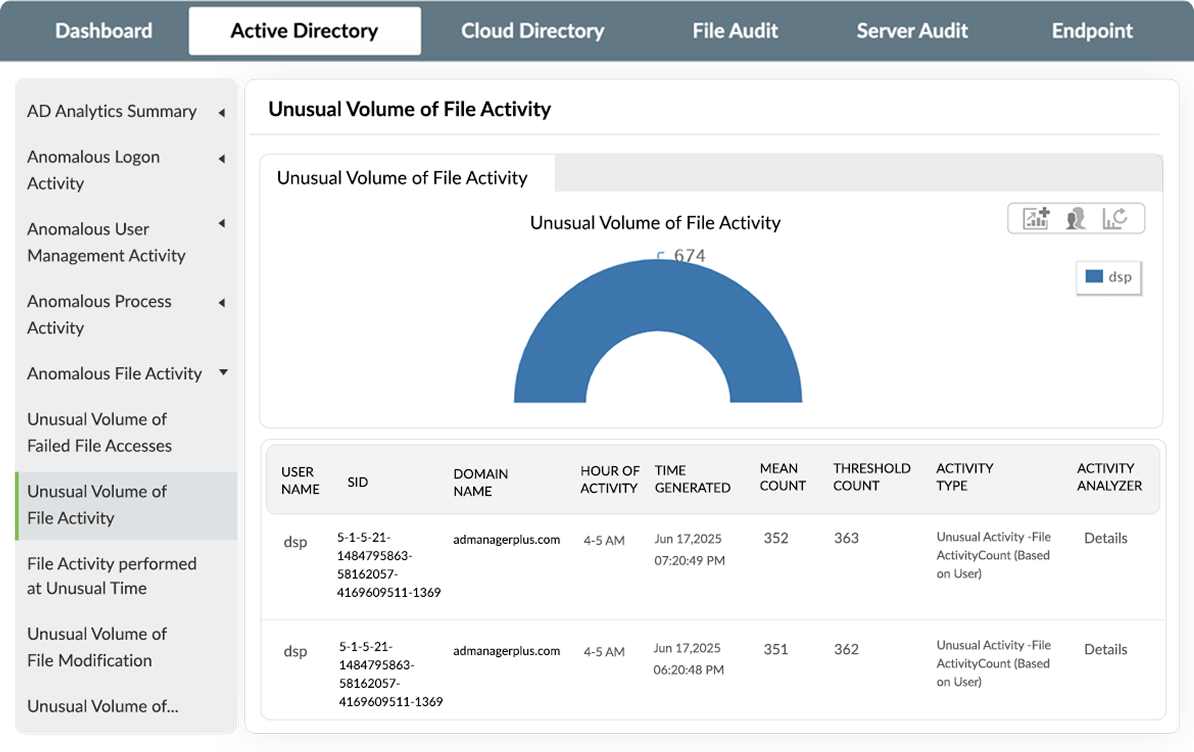
Leverage advanced machine learning and statistical analytics to analyze user behavior and detect potential malicious activity. Focus on users whose actions deviate from the established baseline to spot threats before they escalate.
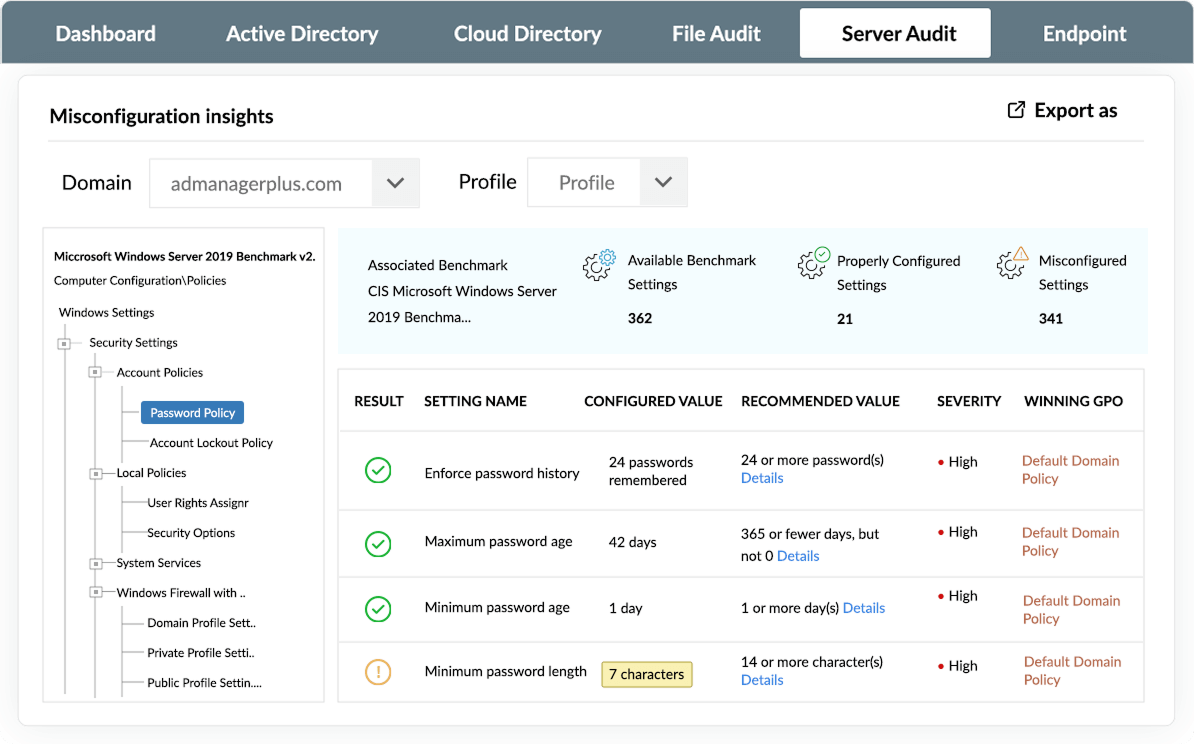
Visualize the exposure status of your AD-joined domain controllers, member servers, and workstations by evaluating them against CIS-based misconfiguration rules. Follow recommended steps to remediate exposures and align with CIS benchmarks.
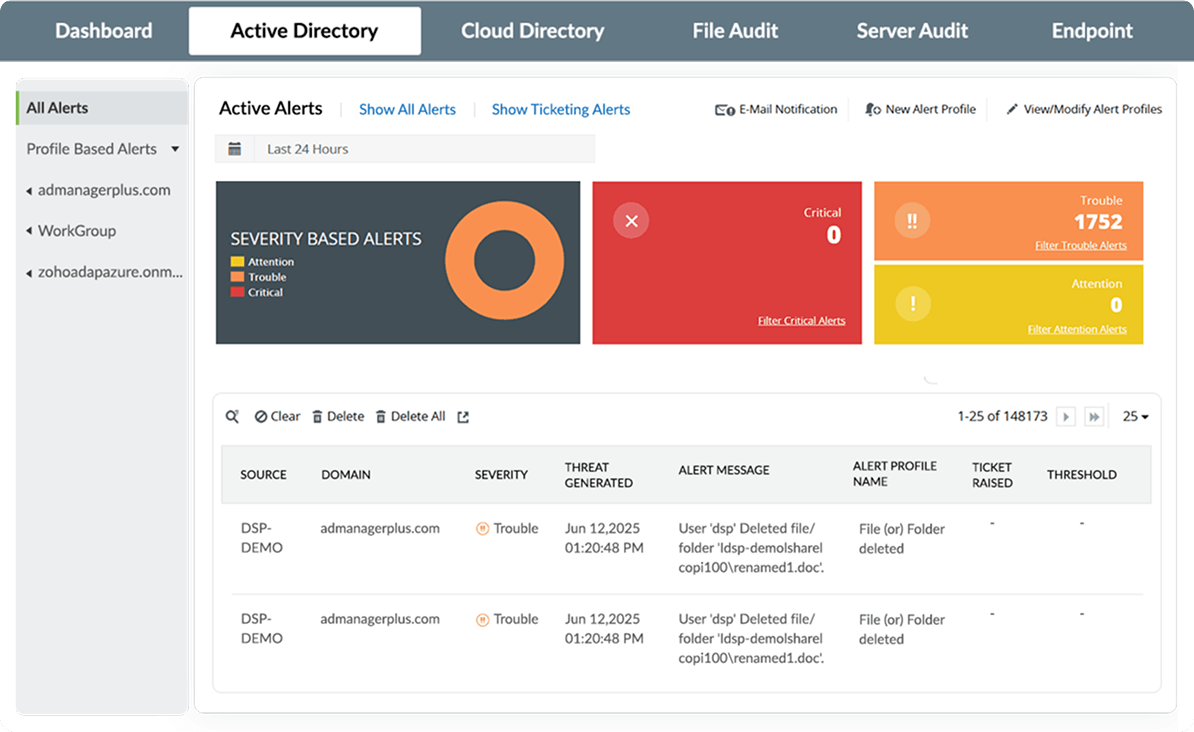
Receive instant notifications via SMS or email about suspicious activities or potential attacks within your Active Directory environment. Ensure rapid response by executing automated scripts to neutralize threats and prevent further damage.
To assist your evaluation, we offer:
Active Directory is a prime target for attackers because it is a vital part of most organizations' IT infrastructure, responsible for holding and managing identities and their permissions. Once compromised, attackers can gain access to valuable information and resources, enabling them to wreak widespread damage, including tampering with sensitive files, data theft, and even ransomware. For this reason, securing Active Directory should be the top priority for organizations keen on protecting identities and their access rights, and, ultimately, safeguarding their critical data and resources.
Identity threat detection and response (ITDR) is a security strategy focused on detecting, mitigating, and responding to identity-based threats within identity-managing environments like Active Directory. ITDR involves continuous monitoring of user behavior, analyzing suspicious activity patterns, and providing real-time response to contain potential attacks. By integrating ITDR capabilities into their security framework, organizations can protect identities, safeguard their sensitive resources and tighten their security posture.
ITDR solutions equipped with UBA continuously monitor user activity and changes across the Active Directory environment to detect subtle deviations in behavior. They also use MITRE ATT&CK-aligned detection rules to identify common attack patterns such as privilege escalation and lateral movement. Together, these capabilities provide a comprehensive view of your Active Directory security posture, enabling security teams to quickly spot anomalies, respond to early indicators of compromise, and stay ahead of identity-based threats.
Some of the most common Active Directory attacks include:
To mitigate these attacks, it’s crucial to implement a strong Active Directory auditing and monitoring strategy. ITDR solutions with UBA capabilities like ADAudit Plus provide full visibility into Active Directory environments, enabling early detection of attack patterns, real-time response to anomalies, and detailed forensic analysis to support remediation efforts.