What is a golden ticket attack?
Just like in Charlie and the Chocolate Factory, having a golden ticket in Active Directory gives you nearly unlimited access to all resources, sensitive information, and critical systems with a Windows domain. Hackers use a forged Kerberos Ticket Granting Ticket (TGT) to pretend to be a authenticated user within the network.
How is a golden ticket attack possible?
A Kerberos golden ticket attack exploits how the Key Distribution Center (KDC) in Active Directory validates authentication. The KDC is a domain service located on domain controllers. It has two core components, Authentication Server (AS) and Ticket Granting Server (TGS). When a user requests access to a service/resource, the AS authenticates the user credentials and issues a TGT, after encrypting it with the password hash of the KRBTGT account. This password hash is shared with the TGS. So, the TGS validates the TGT, and issues an access token, allowing access to the requested service/resource.
The TGT contains a session key and a validity period, between which the user don't have to re-authenticate. Now, if an attacker obtains the KRBTGT password hash, they can forge a TGT on their own, encrypt it with the password hash, and impersonate any user to gain unrestricted access, all the while being completely undetected—causing a golden ticket attack.
The created golden ticket will remain valid even if the user resets their password since access is given based on the KRBTGT password hash, and not the user password.
Golden ticket attack example
An attacker needs two key pieces of information to execute a golden ticket attack.
- Domain and user information
- KRBTGT account password hash
The first piece of information can be obtained by compromising a user account within the domain. For example, the attacker can use a phishing scam, malware, or brute force attack to gain access to the user account. With that, they can get info such as the FQDN and SID of the domain.
Getting the second piece of information may be a bit tricky, but not at all the difficult. For example, an attacker can use tools like Mimikatz to run a DCSync attack, execute a Pass-the-hash attack or steal the BTDS.DIT file and crack the password offline.
The attacker may use any of these techniques to get the FQDN and SID of the domain, username of the account, and KRBTGT password hash information. They can now mint a brand new TGT and use it legitimately to gain access to critical resources, data, or services, for as long as they want. For example, they can get a TGT to grant access to the CEO’s account, allowing them to view confidential information or manipulate financial data undetected.
How to detect a golden ticket attack
Detecting a Golden Ticket attack is difficult for multiple reasons:
- The forged TGTs appear legitimate
- There is no password guessing required
- The KRBTGT hash has a long lifespan
- Kerberos' trust model inherently validates TGTs, leading to low-to-zero suspicion.
However, there are a few indicators of compromise that we can be on the lookout for:
Unusual account activity: Look for changes to privileged accounts, modifications to security policies, high number of TGT requests from single user, accounts logging in from unfamiliar IPs or systems outside usual hours, accumulation of data at endpoints, first-time access of a critical resource by a user.
Process tracking: Execution of processes like DCSync and installation of software like Mimikatz can be a direct indication of an impending attack.
TGT-related anomalies: Excessive TGT creation and issuance, unexpected usage of TGTs by a single account, and abnormal ticket lifespans can be sign of a golden ticket attack.
KRBTGT account usage: Investigate any change to the KRBTGT account hash or unusual access.
How to protect against a golden ticket attack
You cannot completely prevent golden ticket attacks. What you can do is implement certain principles to reduce the risk of an attack: Here's a few of them:
Regularly rotate KRBTGT account passwords: This invalidates existing golden tickets. However, all issued TGTs will become invalid once the password is changed.
Restrict privileged access: Limit the accounts that can access the KRBTGT account. Enforce the principle of least privilege and minimize users with administrative authority.
Implement strong network segmentation: Segregate domain controllers and sensitive resources to contain potential breaches.
Use Multi-Factor Authentication (MFA): Adding MFA to privileged accounts increases the difficulty for attackers to achieve initial access.
Continuous monitoring: Deploy endpoint detection and response (EDR) solutions, and regularly audit system logs to monitor for unusual activity.
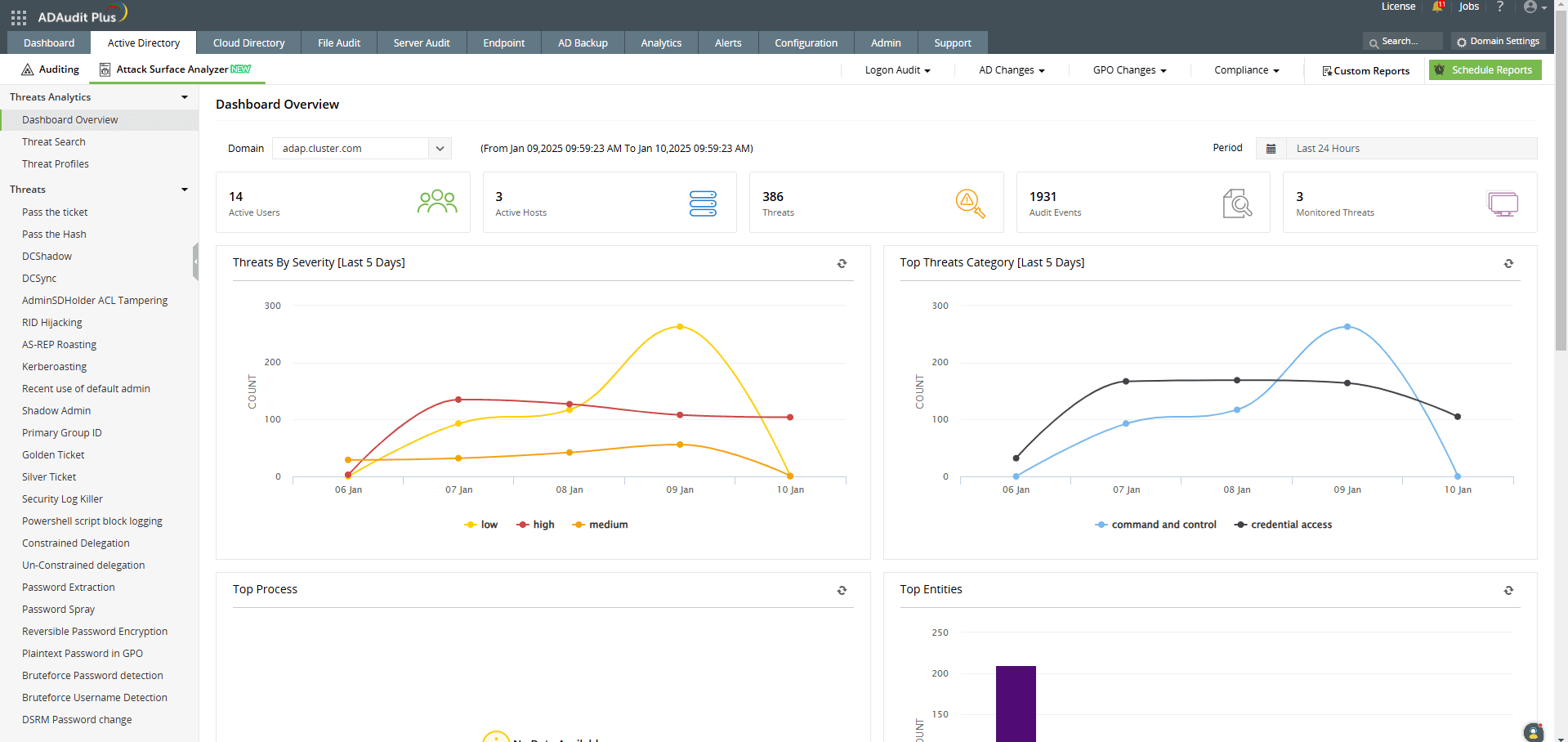
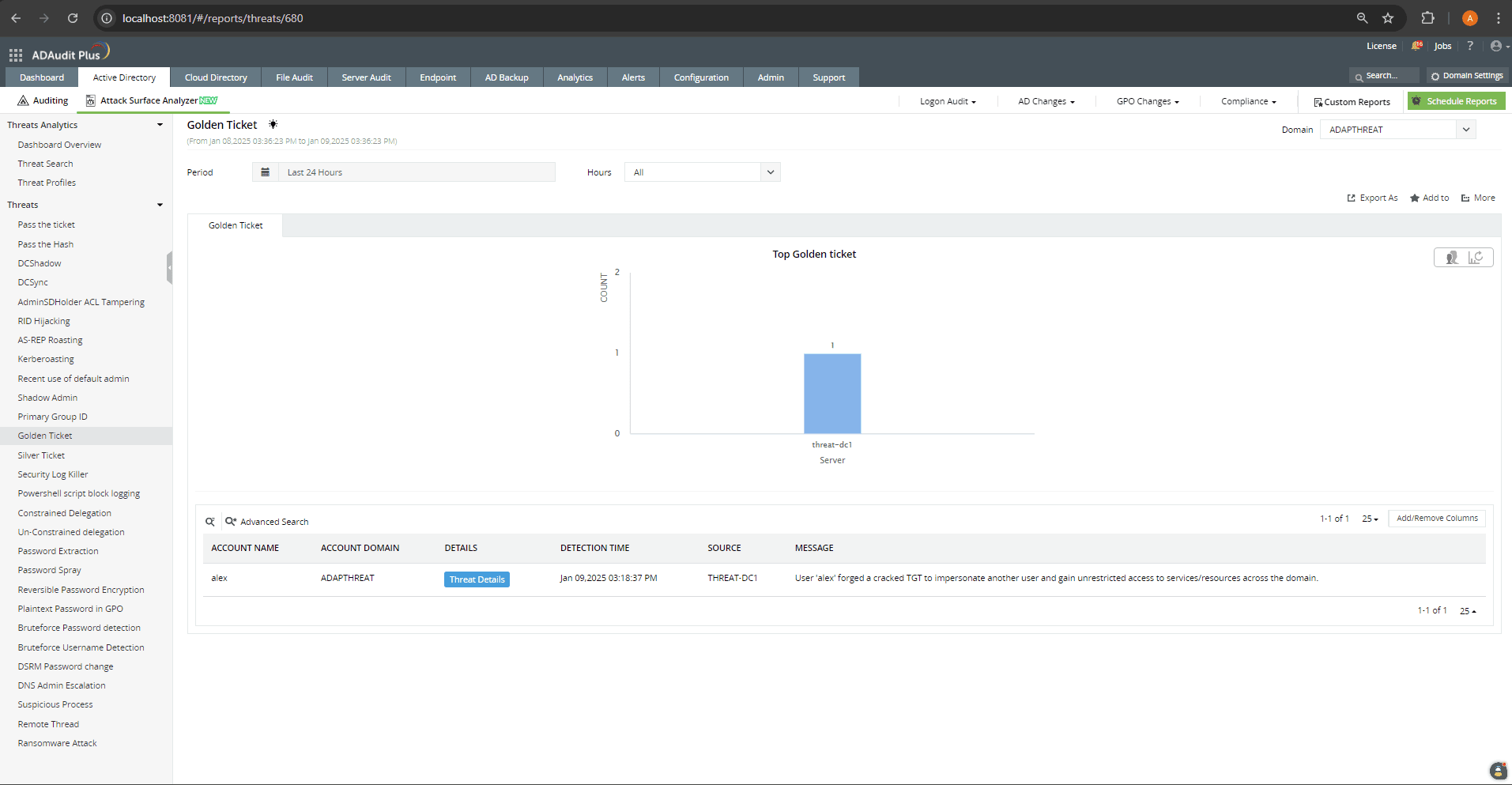
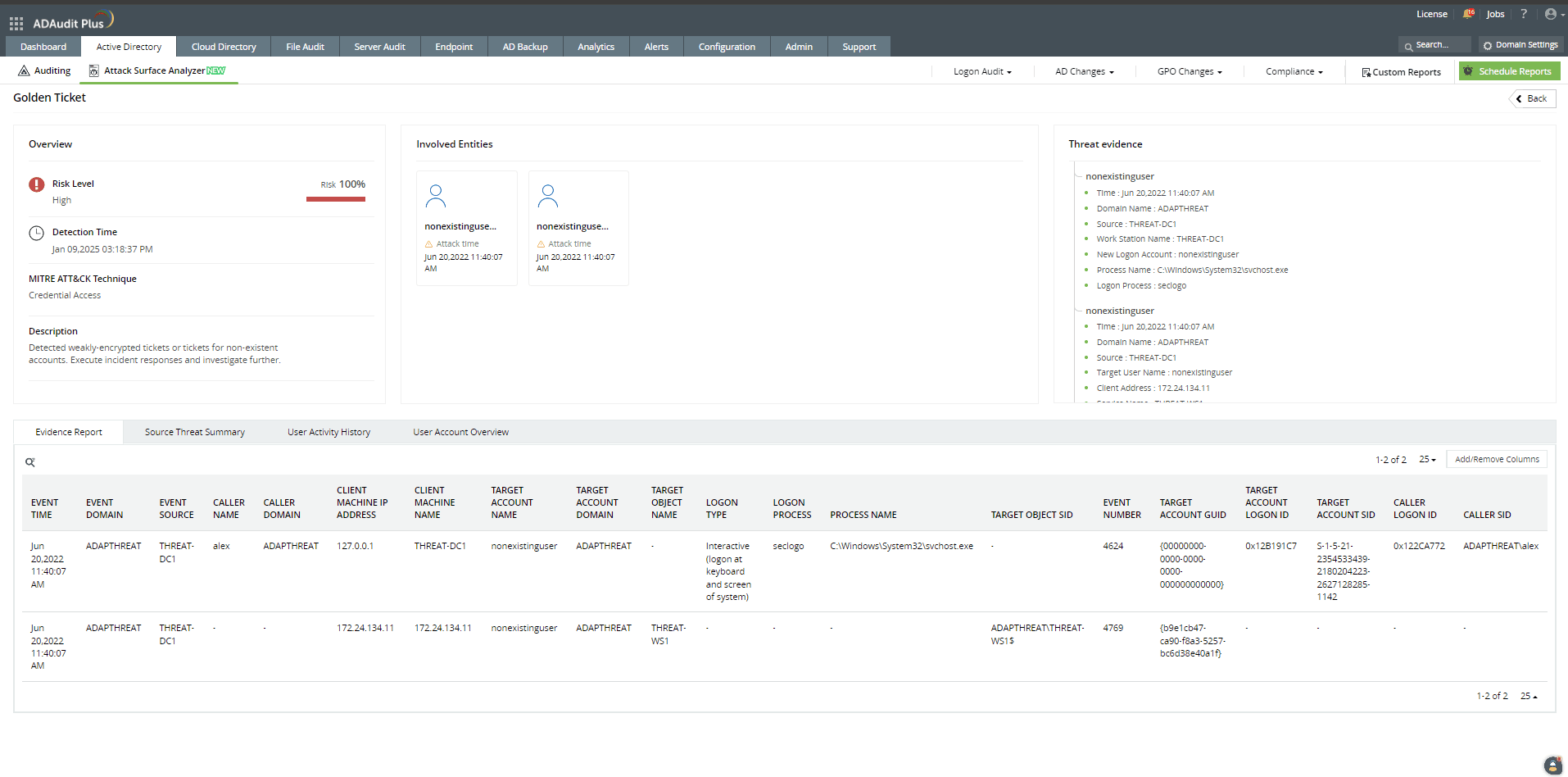
How ADAudit Plus can help you detect and mitigate golden ticket attacks
ADAudit Plus' Attack Surface Analyzer features curated dashboards and specialized reports that help you detect and respond to golden ticket attacks in real time. Powered by exclusive rules derived from the MITRE ATT&CK framework, the Attack Surface Analyzer delivers invaluable threat insights, enabling you to investigate potential golden ticket attacks in just a few clicks.
Start protecting your on-premises and cloud AD resources with ADAudit Plus
Detect over 25 different AD attacks and identify potential misconfigurations within your Azure, GCP, and AWS cloud environments with the Attack Surface Analyzer.
See the Attack Surface Analyzer in actionWe're thrilled to be recognized as a Gartner Peer Insights Customers' Choice for Security Incident & Event Management (SIEM) for the fourth year in a row.