What is an unconstrained delegation attack?
Unconstrained delegation is a feature in Active Directory that allows a service or computer account to impersonate a user account. When enabled, it permits the service or computer to retain the user's ticket-granting ticket (TGT) and seamlessly access other services across the domain on the user's behalf, without prompting for re-authentication. While this may be convenient in some cases, if an attacker gains access to the stored TGT, they can use it to access any service or computer in the domain, leading to an unconstrained delegation attack.
Uncontrained delegation attack example
A user accesses a web application to retrieve data from a separate backend server. Typically, they would need to authenticate twice—once for the web app and again for the backend server. However, when unconstrained delegation is enabled on the service, a single authentication is enough. The service stores the user's TGT and can reuse it to fetch data from the backend server, without asking the user to authenticate again. Now, an attacker can use any number of credential attack techniques to steal the TGT and access any service or computer in the domain, or escalate their privileges.
Unconstrained delegation attack flow
- The attacker identifies a computer with unconstrained delegation by using a PowerShell cmdlet that finds computer accounts that are configured with TrustedForDelegation = True.
- They gain SYSTEM or local admin access to the computer by exploiting a vulnerability or stolen credentials.
- The attacker waits for a privileged user like a Domain Admin to authenticate to the system. When they authenticate, their TGT is stored in memory.
- The attacker uses tools like Mimikatz to extract the TGT and inject the TGT into the attacker's own session to make it valid.
- With the injected TGT, the attacker requests service tickets and accesses services across the domain, including Domain Controllers, file servers, databases, etc.
- The attacker can then also escalate privileges by extracting credentials from the Domain Controller and go on to create new Domain Admin accounts or golden tickets for long-term access.
How do I detect an unconstrained delegation attack?
Detecting an unconstrained delegation attack can be difficult, but there are several key indicators and signs you can look for, such as unusual ticket behavior, unexpected access patterns, and abuse of high-privilege accounts.
Key Windows events to monitor:
- Event ID 4769 – A Kerberos service ticket was requested
A large number of service tickets (TGS) being requested from the same machine.
- Event ID 4624 – Successful logon
High-privilege accounts logging onto systems that have unconstrained delegation.
- Event ID 4672 – Special privileges assigned to new logon
Domain Admin or other privileged accounts logging into systems that should not host them.
How can I protect against unconstrained delegation attacks?
Mitigating the risks associated with unconstrained delegation involves a combination of configuration changes, best practices, and ongoing security measures:
- Avoid unconstrained delegation: Ideally, avoid using unconstrained delegation altogether. It is a legacy feature with significant security flaws.
- Monitor delegated accounts: Identify accounts configured for delegation and monitor the above-mentioned events to ensure an unconstrained delegation attack does not occur.
- Secure sensitive accounts: Enable the "Account is sensitive and cannot be delegated" option for highly privileged and other sensitive accounts in Active Directory.
- Use the Protected Users group: Placing privileged users in the Protected Users security group prevents their credentials from being delegated.
- Rotate passwords regularly: Stolen TGTs can be invalidated with regular password rotation, especially for critical service accounts.
- Control machine account creation: Setting the machine account quota to zero can prevent unauthorized users from creating new computer accounts and configuring them for unconstrained delegation.
How ADAudit Plus can help you detect and mitigate unconstrained delegation attacks
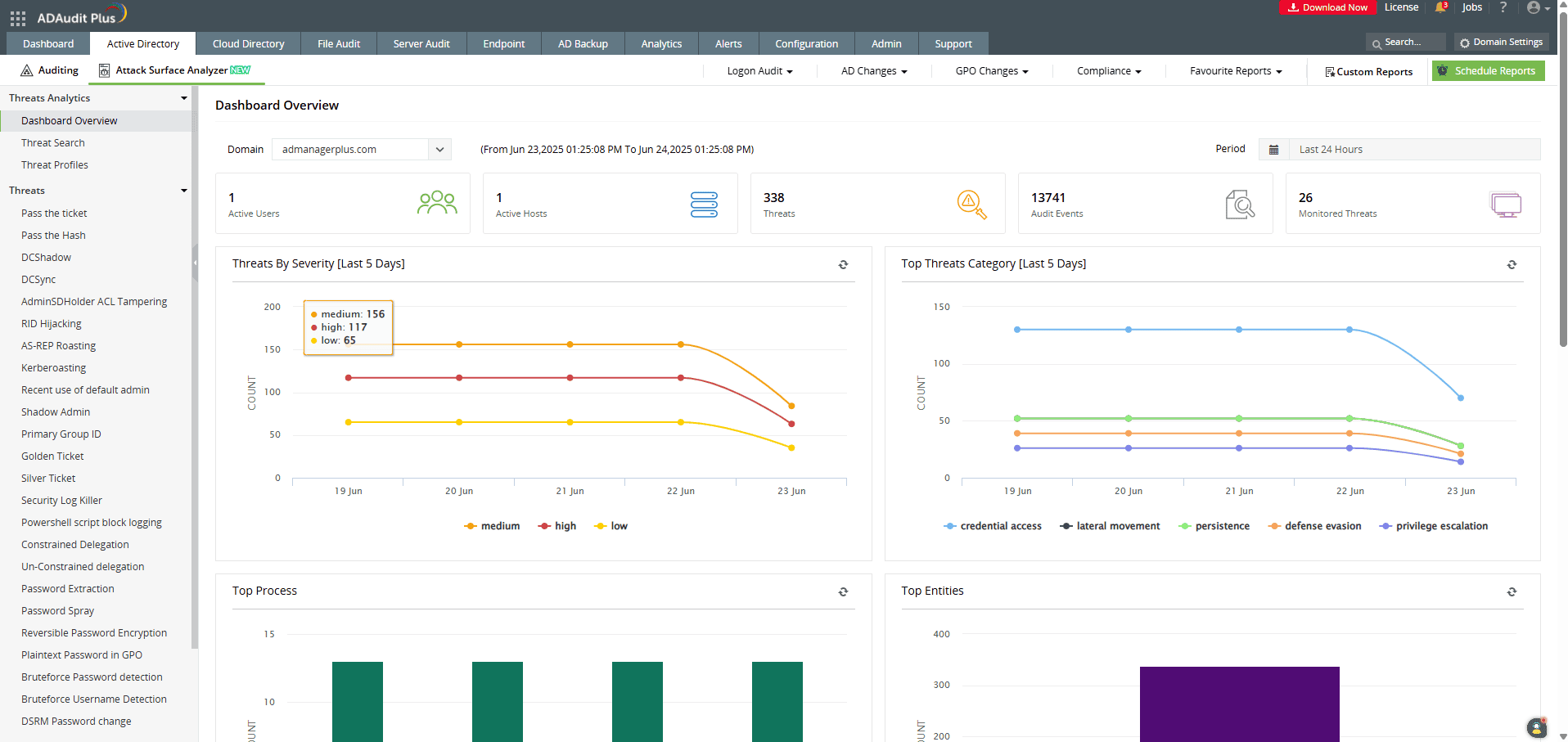
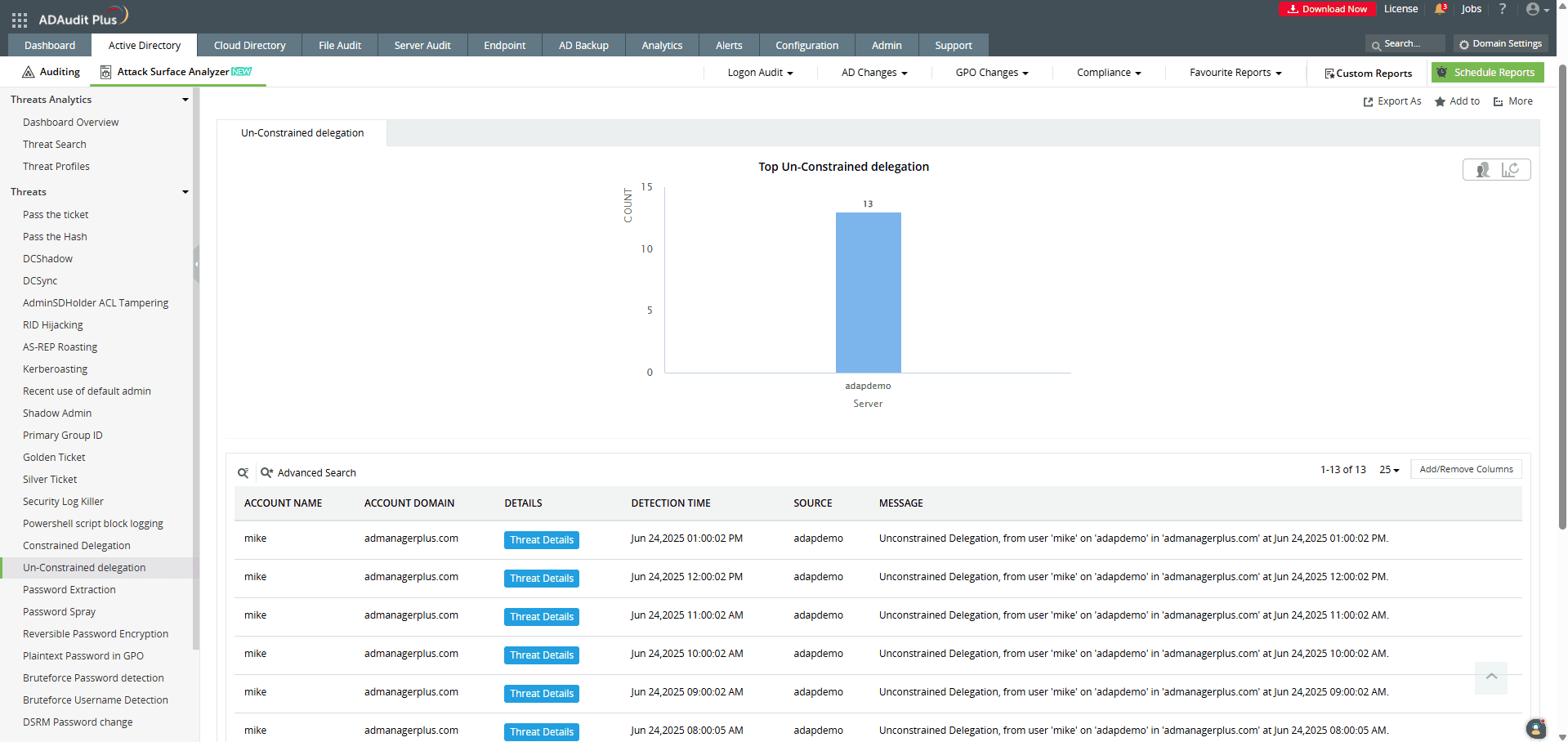
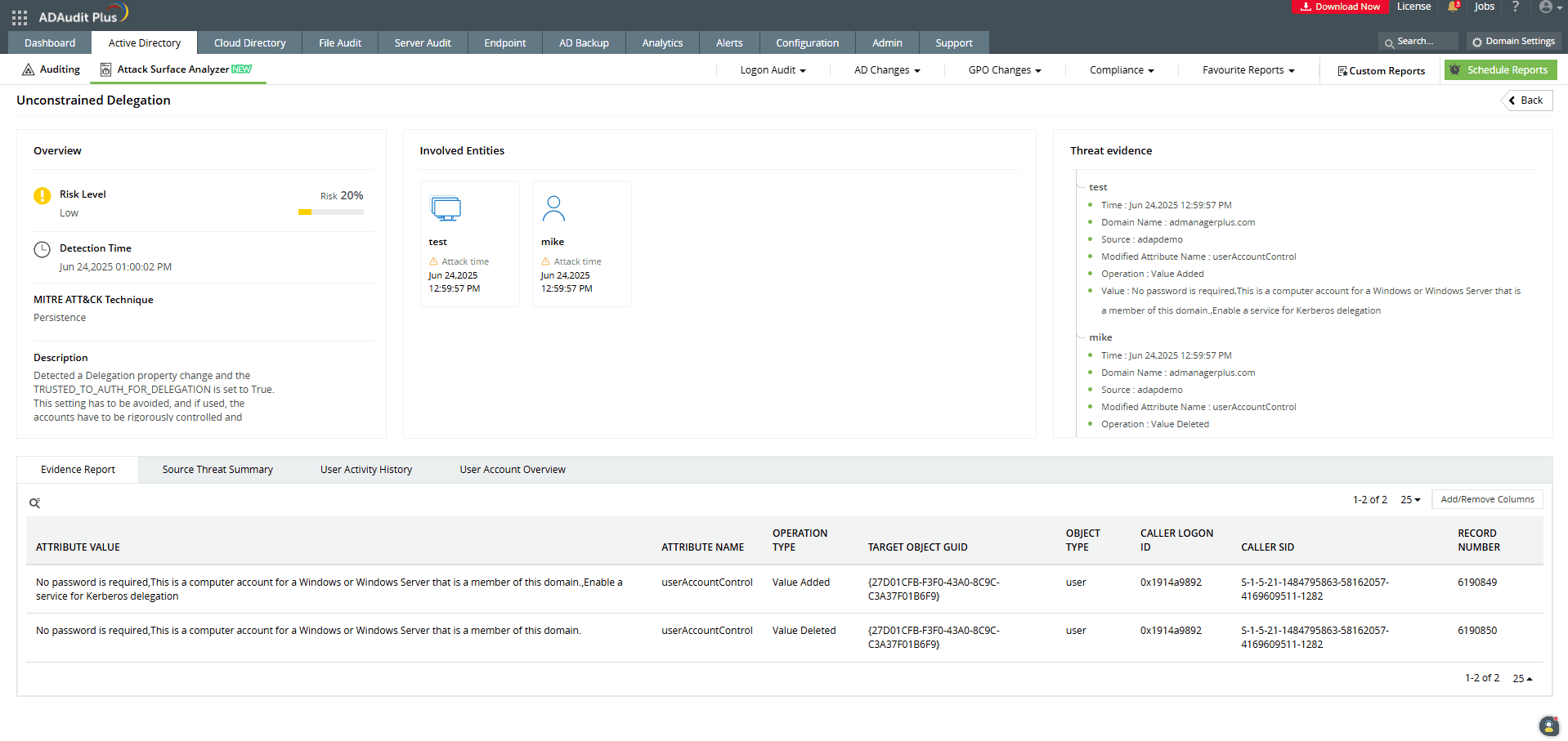
ADAudit Plus' Attack Surface Analyzer provides you with curated dashboards and specialized reports that help you identify accounts configured for unconstrained delegation and respond to unconstrained delegation attacks in real time. Powered by exclusive rules derived from the MITRE ATT&CK framework, the Attack Surface Analyzer delivers invaluable threat insights, enabling you to investigate potential unconstrained delegation attacks in just a few clicks.
Start protecting your on-premises and cloud AD resources with ADAudit Plus
Detect over 25 different AD attacks and identify potential misconfigurations within your Azure, GCP, and AWS cloud environments with the Attack Surface Analyzer.
See the Attack Surface Analyzer in actionWe're thrilled to be recognized as a Gartner Peer Insights Customers' Choice for Security Incident & Event Management (SIEM) for the fourth year in a row.