Direct Inward Dialing: +1 408 916 9892
The audit policies in your Active Directory give you a window to view all the activity taking place on your network. Setting up an audit policy on Windows Server allows you to view various events on Event Viewer. Based on how you configure the audit policy you can view 'success' and 'failure' events. Directory Service Access is an audit policy that allows you to view what AD objects were accessed, who accessed it, and when it was accessed. You can configure this policy either through the 'Local Policy' option or via the 'Advanced Audit Policy' option. We recommend the Advanced Policy option since it gives you more granular control over what events you want logged in Event Viewer.
Event Viewer is the default native AD tool to view all your events. Although Event Viewer is a great tool, it is hard to look through all the messages and events, and find a particular suspicious incident. We suggest opting for an effective solution like ADAudit Plus.
ADAudit Plus is a comprehensive solution that simplifies AD auditing and reporting. It is a one-stop platform that brings together an intuitive user interface, pre-configured reports, and advanced filter options that make it easy for you to track changes to your network, and detect threats immediately. You get a fully equipped dashboard that gives you a holistic view of the various systems in your network. This way you can correlate events across the network and spot suspicious behavior.
Below are a few AD object related reports found in the 'Reports' tab in ADAudit Plus console:
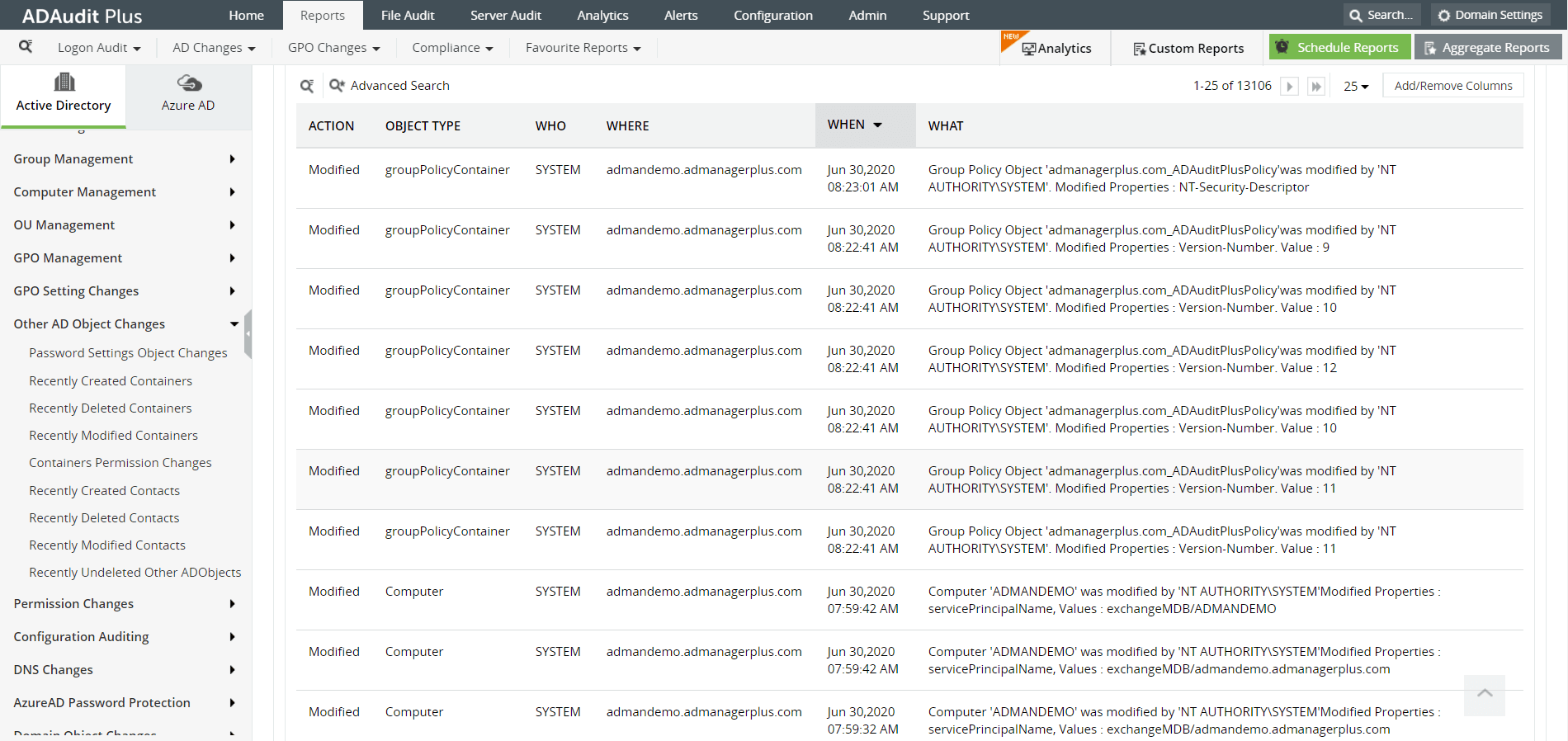
Image: A report on AD Object changes in ADAudit Plus console
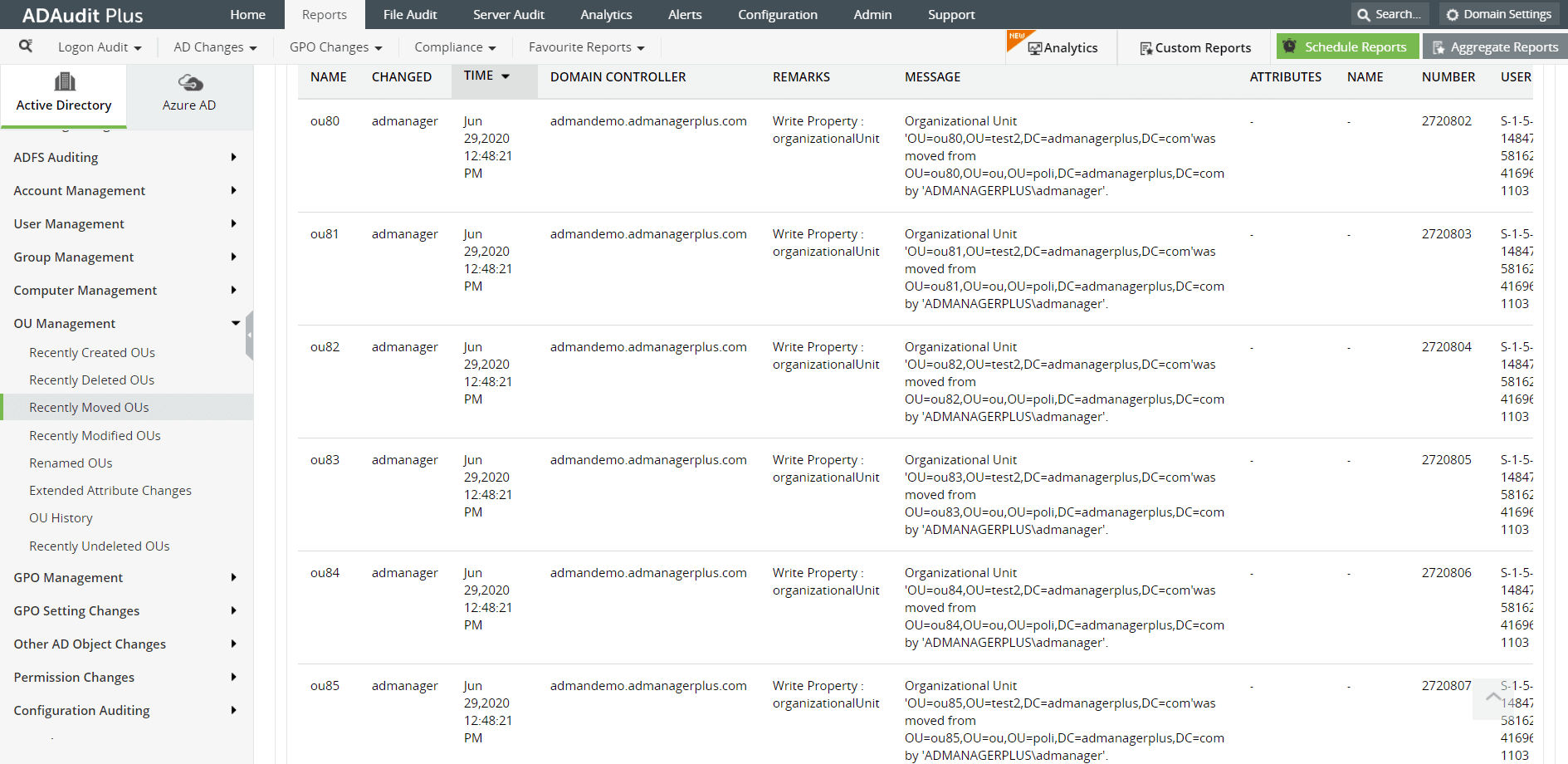
Image: An ADAudit Plus report on recently moved OUs
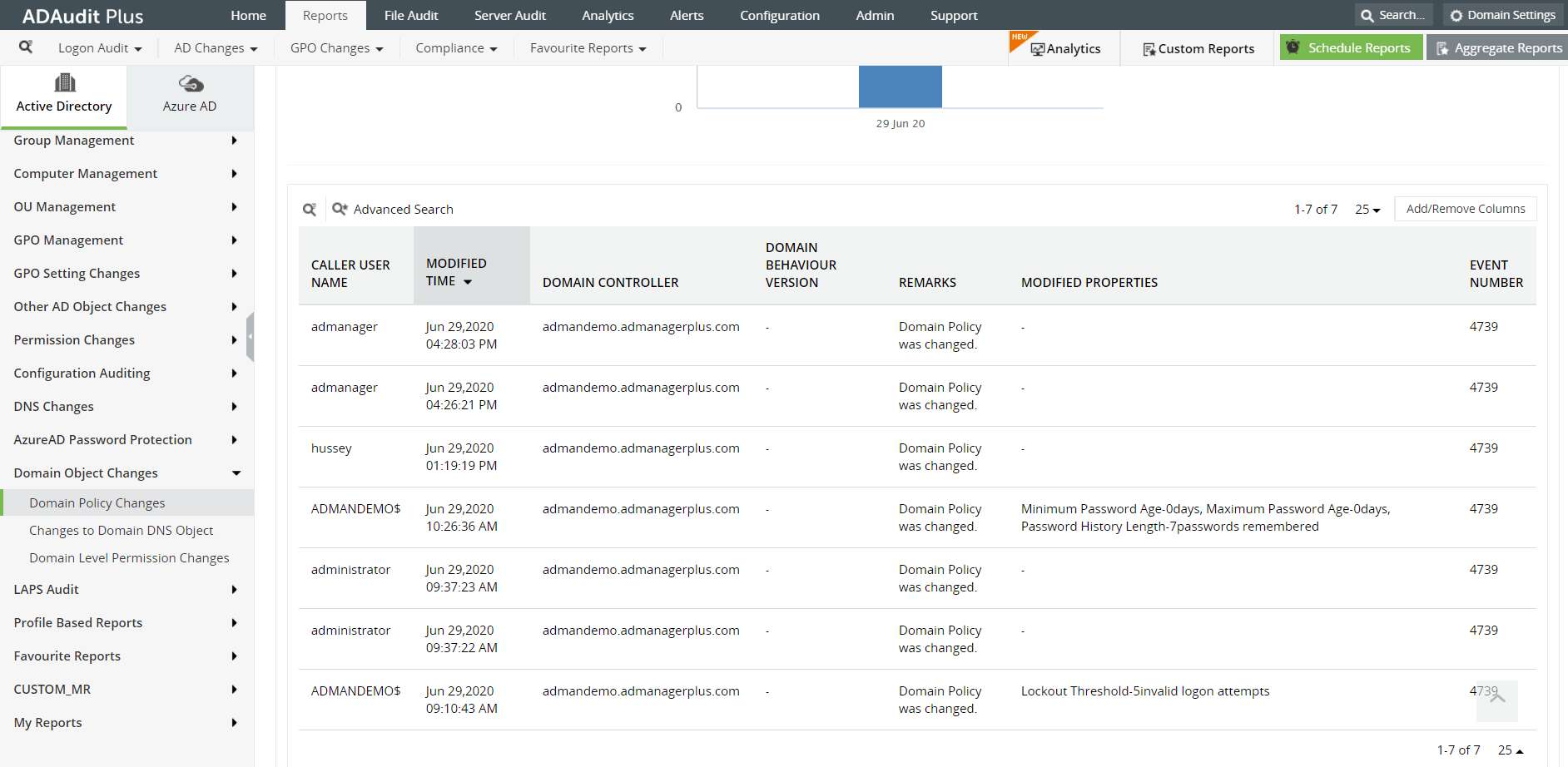
Image: Domain object changes report in ADAudit Plus console
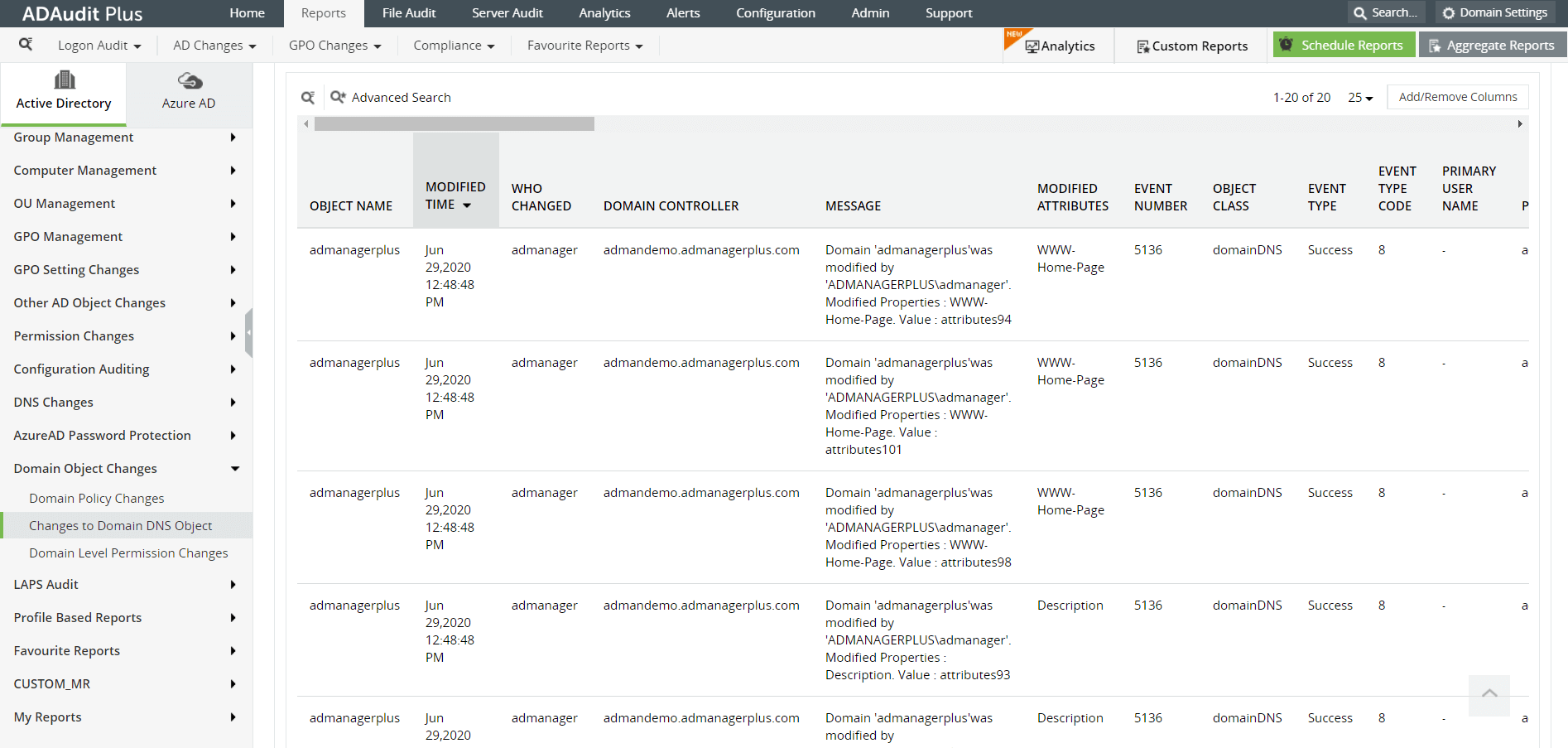
Image: Changes to Domain Object report in ADAudit Plus console
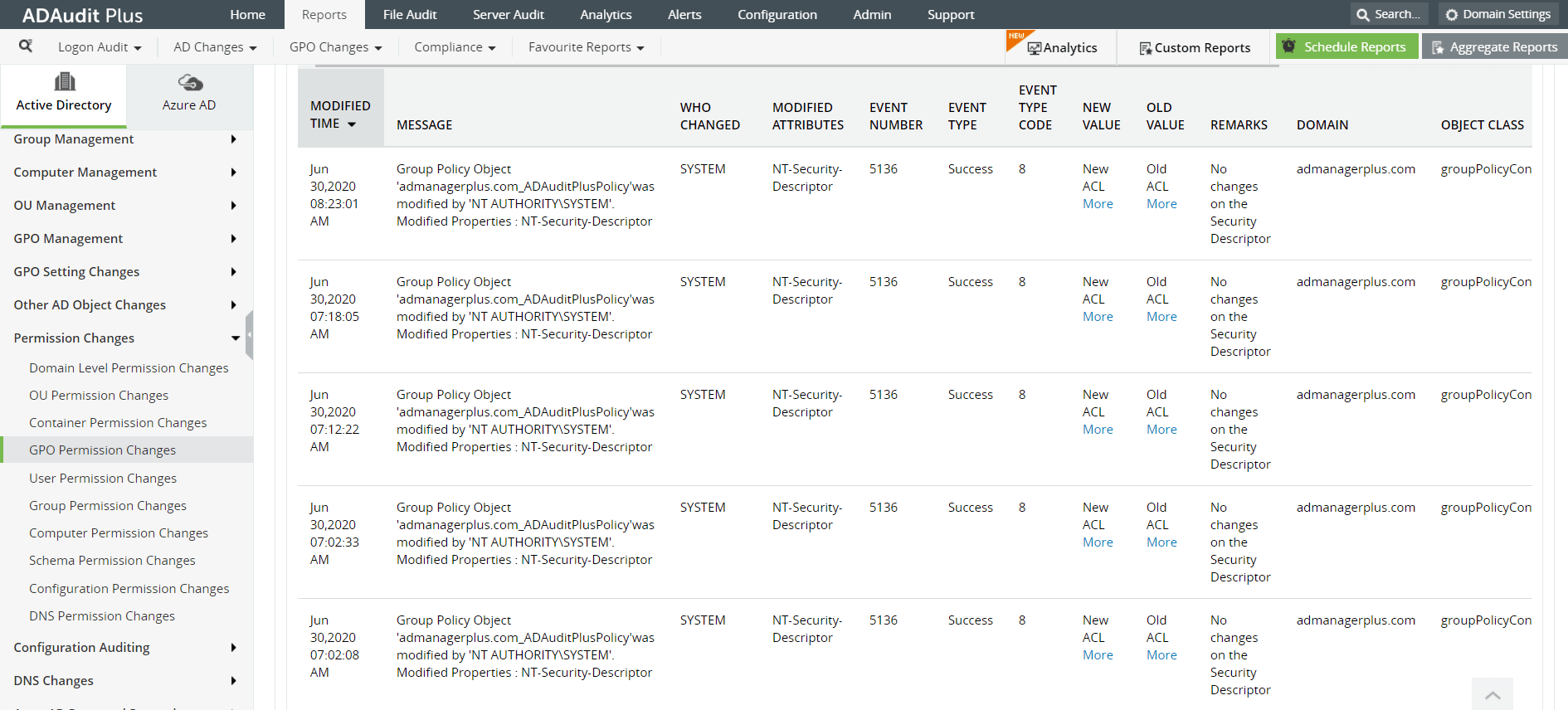
Image: GPO permission changes report in ADAudit Plus console
ADAudit Plus is a real-time, web-based Windows Active Directory (AD) change reporting software that audits, reports and alerts on Active Directory, Windows servers and workstations, and NAS storage devices to meet the demands of security, and compliance requirements. You can track AD management changes, processes, folder modifications, permissions changes, and more with 200+ reports and real-time alerts. You can also get out-of-the-box reports for compliance mandates such as the HIPAA. To learn more, visit https://www.manageengine.com/active-directory-audit/.
Try ADAudit Plus login monitoring tool to audit, track, and respond to malicious login and logoff actions instantaneously.
Try ADAudit Plus for free