Knowing who is logged in to a system helps with security, troubleshooting, and resource management. For example, it prevents unauthorized access, ensures no one is using a server outside maintenance windows, and helps identify sessions consuming high resources.
System administrators often need to check which users are currently logged in to a Windows machine, whether for monitoring, troubleshooting, or security.
This guide explains multiple ways to view logged-on users using CMD, PowerShell, and Task Manager across Windows Server editions (2008-2022) and Windows desktop operating systems (10 and 11). You will also learn how to export the results to CSV for reporting.
- Native Windows tools
- ADAudit Plus
View logged-on users using CMD
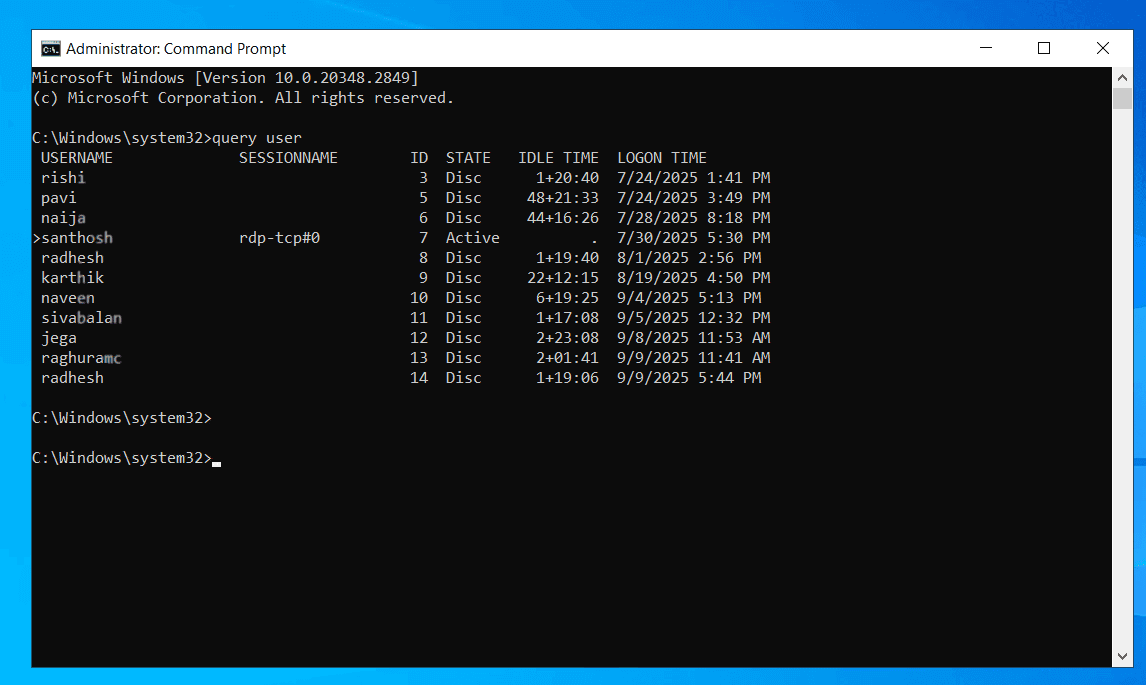
The simplest way to view logged in users is by using the query user command.
- Open Command Prompt as administrator.
- Run the following command:
Sample Windows PowerShell script
query user
This will display the usernames, session IDs, and session states of Logged-in users. It's a straightforward way to see logged-in users without extra tools.
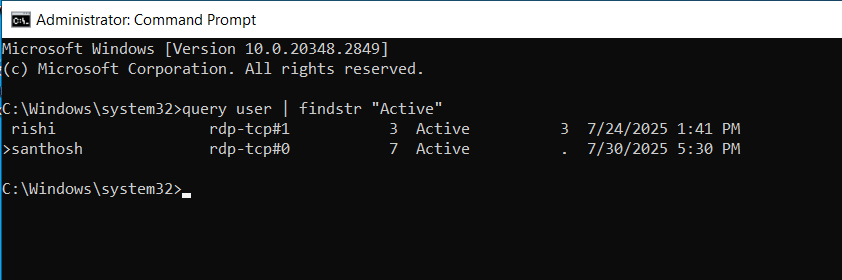
- To filter only the users who are currently logged in and active, run:
Sample Windows PowerShell script
query user | findstr "Active"
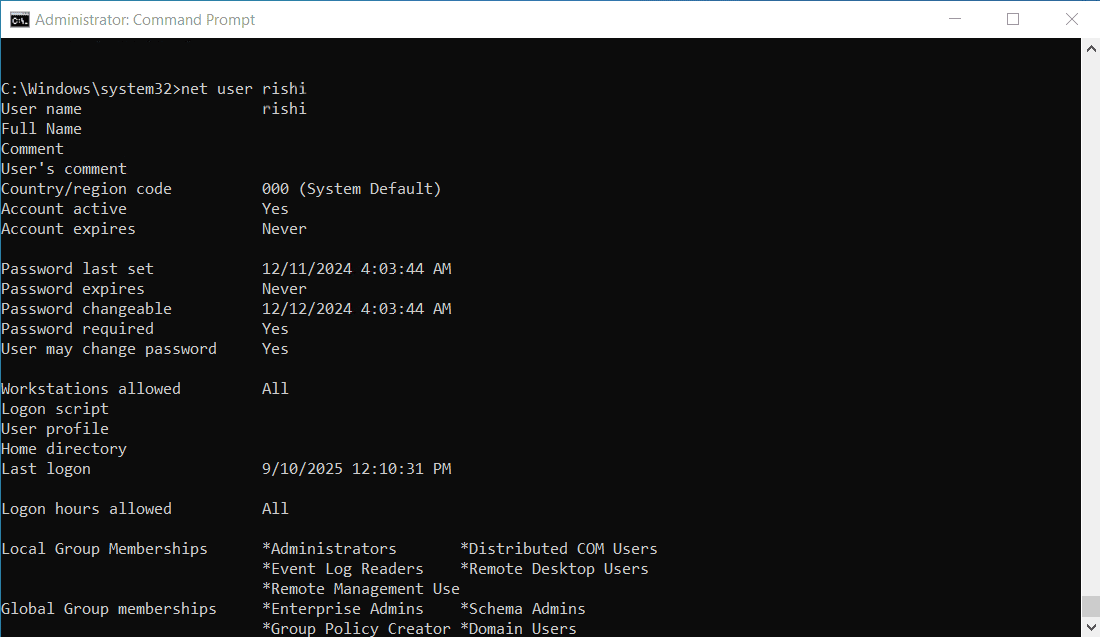
The columns in the output represent the following:
- SESSIONNAME
- Shows the type of session. For RDP, you'll see something like rdp-tcp#0.
- If it's blank, the session is a disconnected session not actively tied to a console or RDP.
- ID
- The session ID assigned by Windows.
- Each login session gets a unique numeric ID.
- Used when running commands like logoff <ID> or reset session <ID>.
- STATE
- Active: The user is currently logged in and using the session.
- Disc (disconnected): The user was logged in but has disconnected the RDP or console session (still consuming resources but not actively connected).
- Listen: A system listener waiting for new RDP connections.
- Down: The session is not functioning correctly.
- Idle: The session has had no input activity for a long time (usually shown through IDLE TIME rather than this column).
- IDLE TIME
- The duration the session has been inactive (no keyboard or mouse input).
- Format: Days+HH:MM
- Example: 1+20:40 = 1 day, 20 hours, 40 minutes of inactivity
- A . (dot) means there's no idle time (the user is currently active).
Note:
If you also want to see all user accounts available on the system using CMD (not just those currently logged in), run the following command:
Sample Windows PowerShell script
net user
To view the details of a specific account, run:
Sample Windows PowerShell script
net user < username>
View logged-on users using PowerShell
PowerShell offers multiple ways to check logged-in users. Depending on your needs, you can view the current console user, all active sessions, or export results for reporting.
- Check the current logged-In console user by running:
Sample Windows PowerShell script
Get-CimInstance Win32_ComputerSystem | Select-Object UserName
On older versions like Windows Server 2008 R2, replace Get-CimInstance with:
Sample Windows PowerShell script
Get-WmiObject Win32_ComputerSystem | Select-Object UserName
- This displays the currently active console user.
- Limitation: It only shows the user physically logged in at the machine, not remote RDP sessions.
- List all active sessions by running:
Sample Windows PowerShell script
quser
- This works similarly to query user in CMD.
- It lists all users logged in locally and via RDP, including their session ID, state, and idle time.
- To filter only active users, run:
Sample Windows PowerShell script
quser | Select-String "Active"
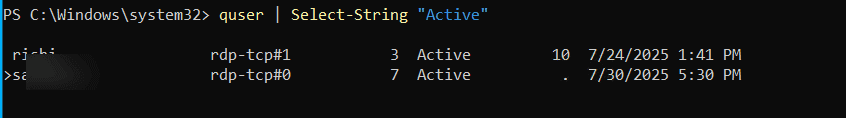
Export logged-on users to CSV
You can export results for reporting or auditing by running:
Sample Windows PowerShell script
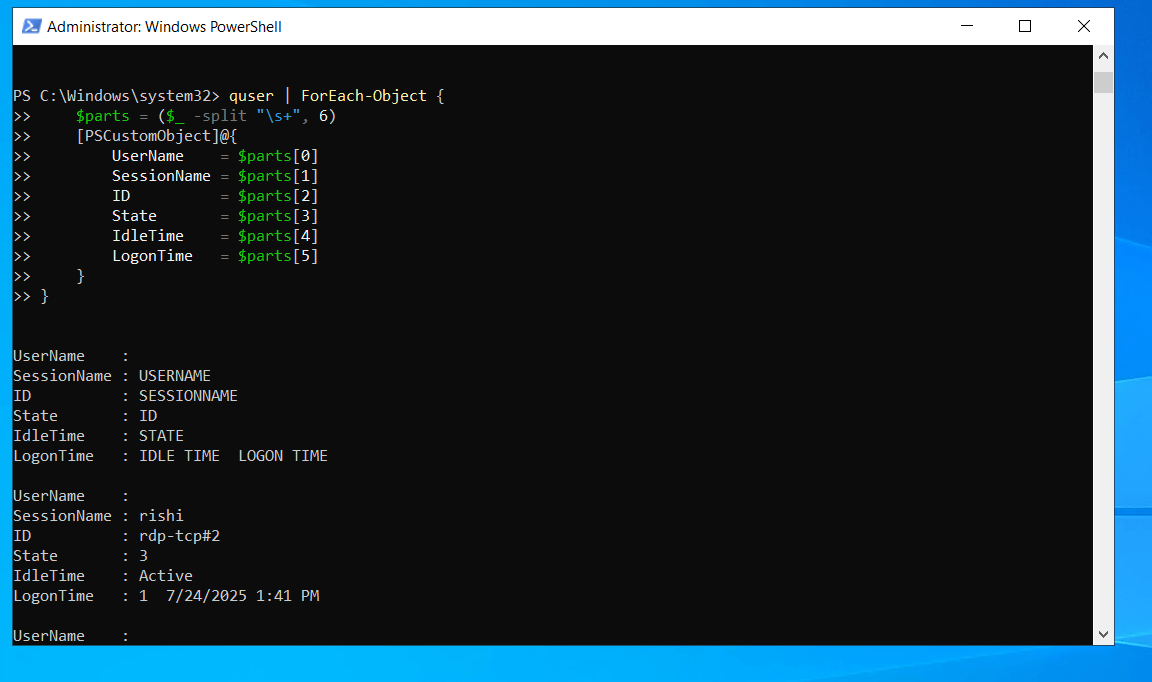
quser | ForEach-Object {
$parts = ($_ -split "\s+", 6)
[PSCustomObject]@{
UserName = $parts[0]
SessionName = $parts[1]
ID = $parts[2]
State = $parts[3]
IdleTime = $parts[4]
LogonTime = $parts[5]
}
} | Export-Csv -Path "C:\LoggedInUsers.csv" -NoTypeInformation
- This creates a CSV file in the given path location with user details.
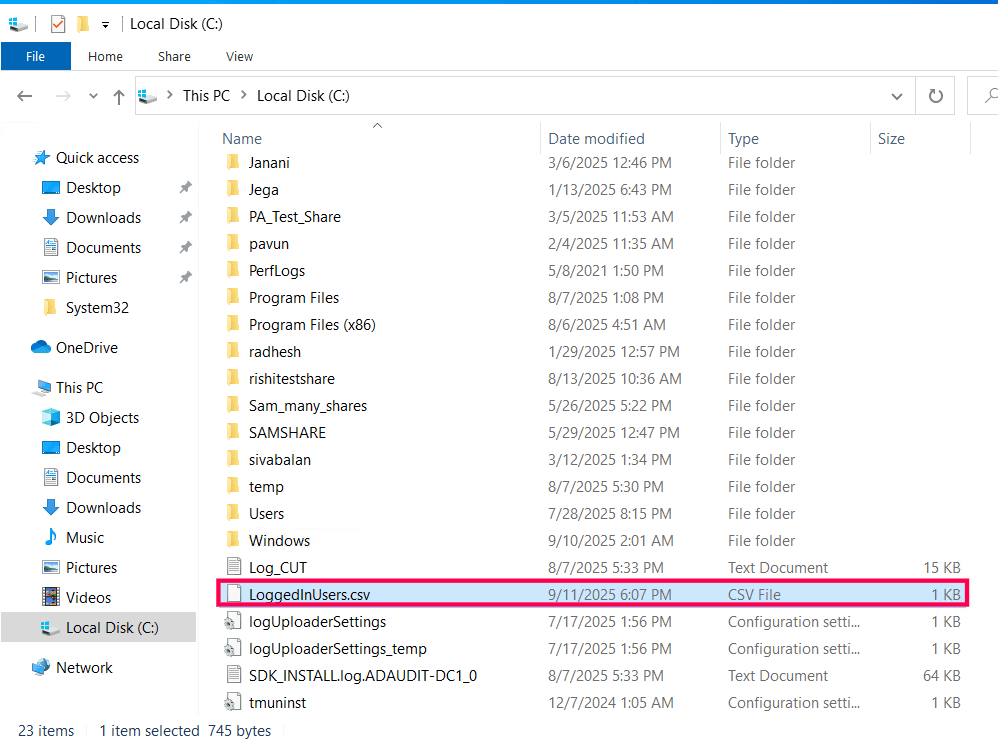
Once exported, the CSV file can be opened in Excel or any reporting tool for deeper analysis.
This allows administrators to sort, filter, and archive login records, making it easier to track trends, investigate suspicious activity, or share reports with management and auditors.
Note:
- If you don't need an export, simply remove the | Export-Csv -Path "C:\LoggedInUsers.csv" -NoTypeInformation part to display results directly in the console.
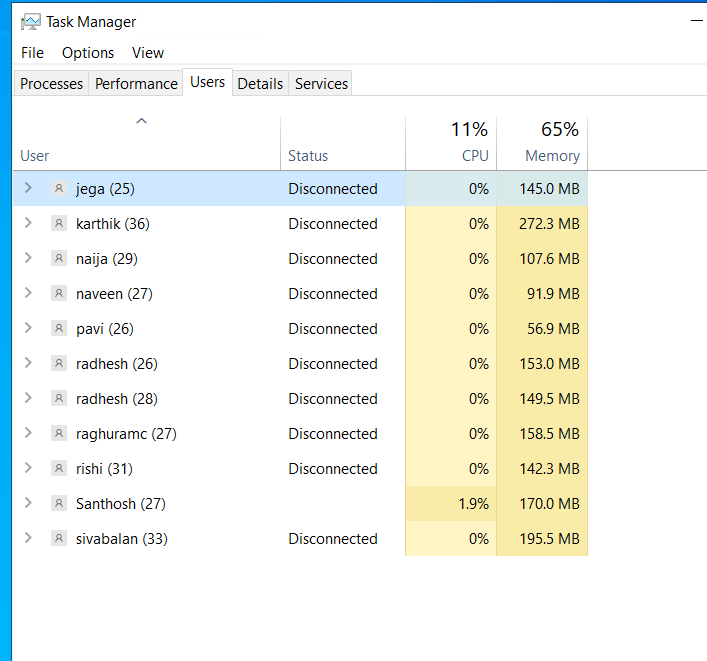
View logged-on users with Task Manager
Note:
Task Manager is available on Windows desktop editions and Windows Server with a GUI. It is not available on Server Core installations.
If you prefer a graphical method to view logged-in users, Task Manager provides a quick way to check who's logged in.
- Right-click the taskbar and select Task Manager.
- If you're using Windows 10 or 8, you might need to click the More details button located at the bottom to see active processes.
- Click the Users tab at the top of Task Manager; here, you can see the list of currently logged-on users and their status.
Simplify the way you see logged-on users
- Download and install ADAudit Plus.
- Find the steps to configure auditing on your domain controller here.
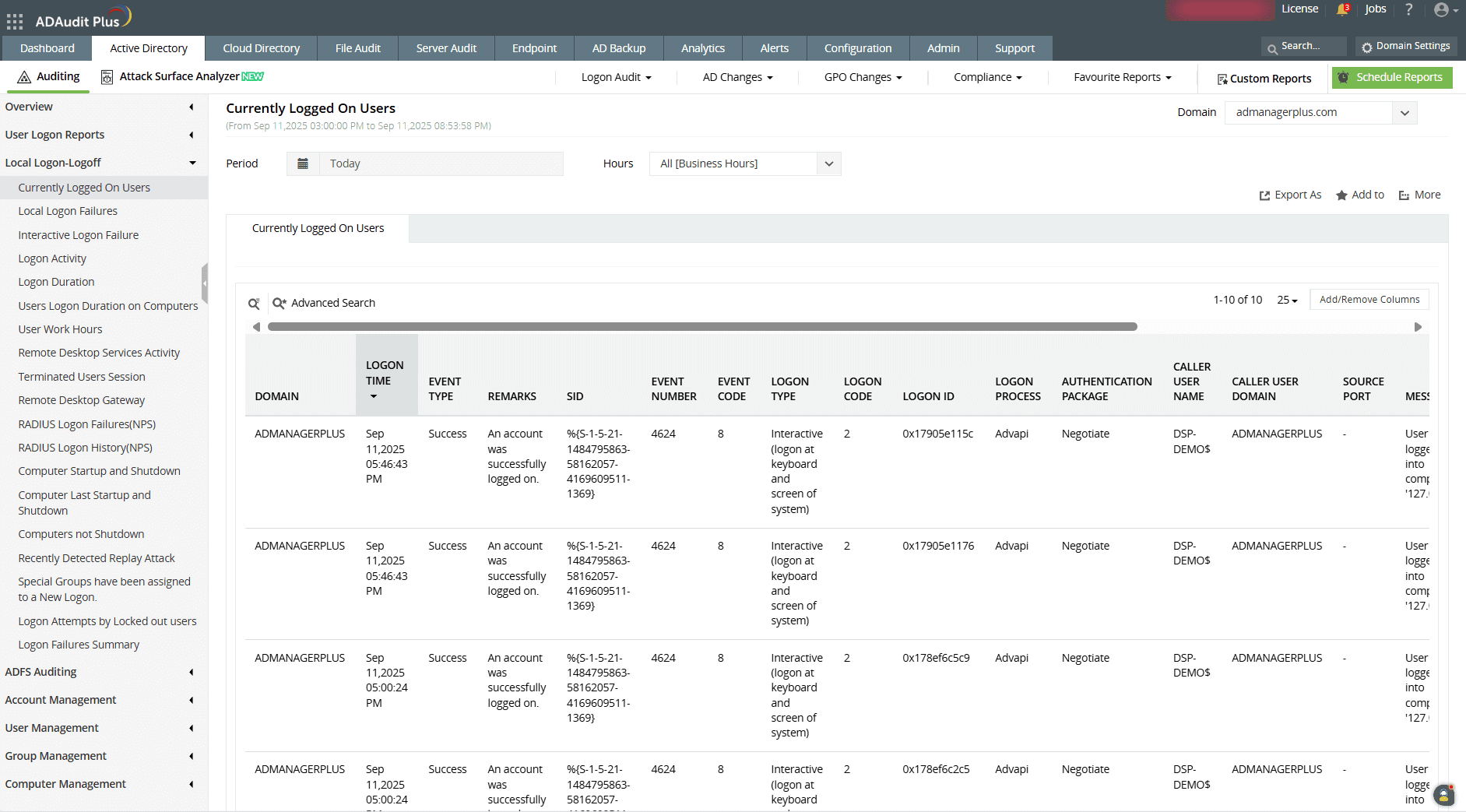
- Open the console and navigate to Active Directory → Local Logon-Logoff → Currently Logged on Users
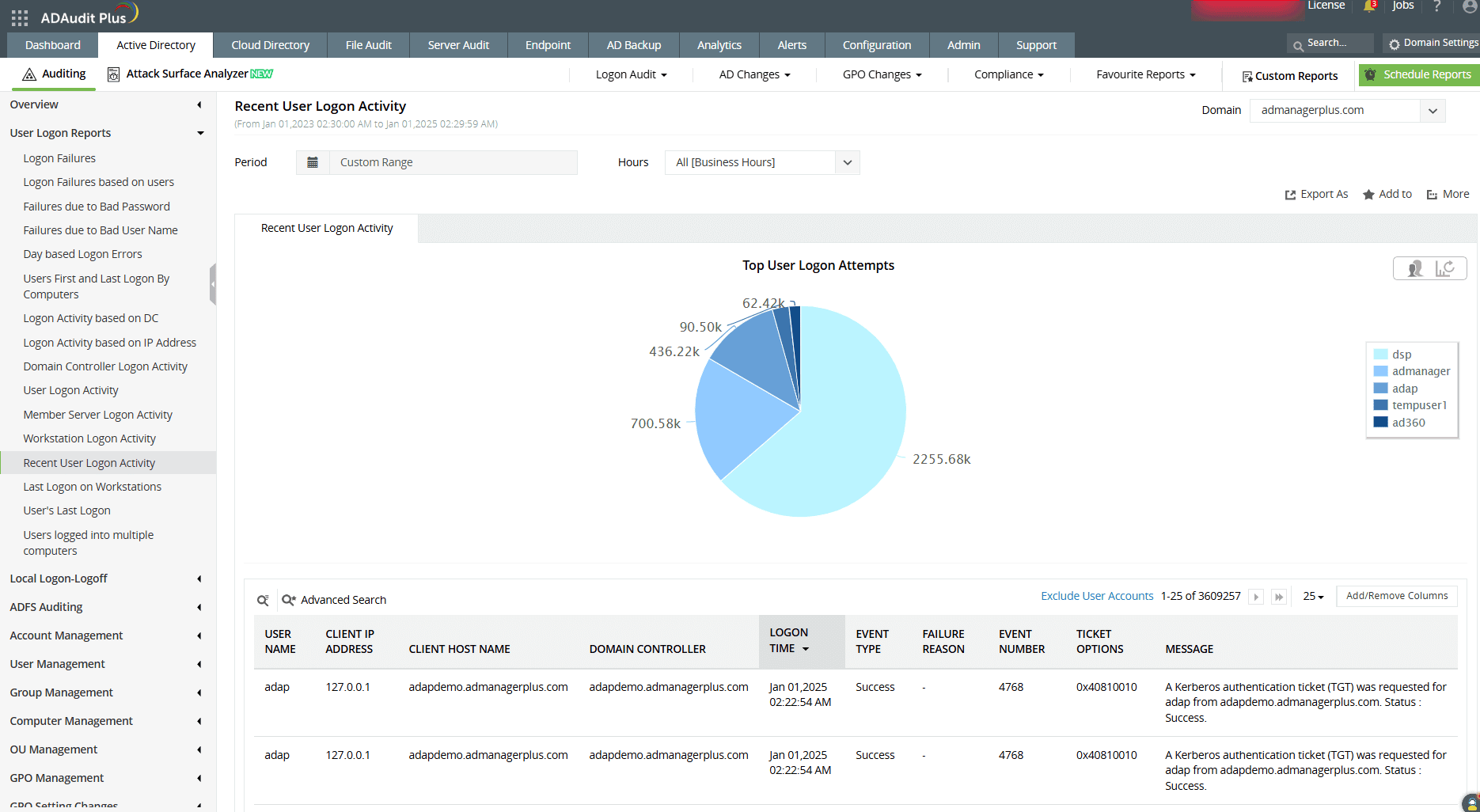
- Audit recent user logon activity by navigating to Active Directory → Local Logon-Logoff → Recent User Logon Activity.
Note:
This solution works on Windows Server 2008 R2 and later (2012, 2016, 2019, 2022, and 2025) for both local and remote user sessions.
The problem with native logon checks
While CMD, PowerShell, and Task Manager can show who is logged in, they only scratch the surface. These methods provide limited visibility and leave gaps in security and compliance monitoring. They:
- Only display current logins without historical tracking.
- Have no centralized reporting across multiple systems.
- Cannot send real-time alerts on suspicious logons.
- Require manual log collection and analysis.
- Become time-consuming and error-prone in larger environments.
To overcome these limitations, organizations often look for an advanced auditing solution that provides deeper visibility, automation, and continuous monitoring.
A one-stop solution for all your IT auditing, compliance, and security needs
ADAudit Plus provides capabilities like change auditing, logon monitoring, file tracking, compliance reporting, attack surface analysis, response automation, and backup and recovery for diverse IT systems.
FAQ and troubleshooting
Some editions (like Home) don’t support certain session commands. Use PowerShell instead.
net user lists all accounts on the machine, while query user shows only active sessions.
Some commands, like net user, may work without admin rights, but most methods to see who is logged in (like query user) require administrator privileges.
Experience
ADAudit Plus for free
With ADAudit Plus, you can:
- Track logon failures by users
- Monitor day-based logon errors
- Detect attacks like Kerberoasting
- Monitor employee attendance
- And much more