A brief description of Kerberos
Kerberos is Microsoft's default authentication protocol to authenticate users into a network. All popular operating systems like Apple OS, Microsoft Windows, Linux have Kerberos built in. The authentication system rests on three cornerstones - the client, the server, and the Key Distribution Center. It relies on a shared secret key cryptography which prevent the interception of the packets being transmitted.
How Kerberos authentication works
Displayed below are the components of the Key Distribution Center.
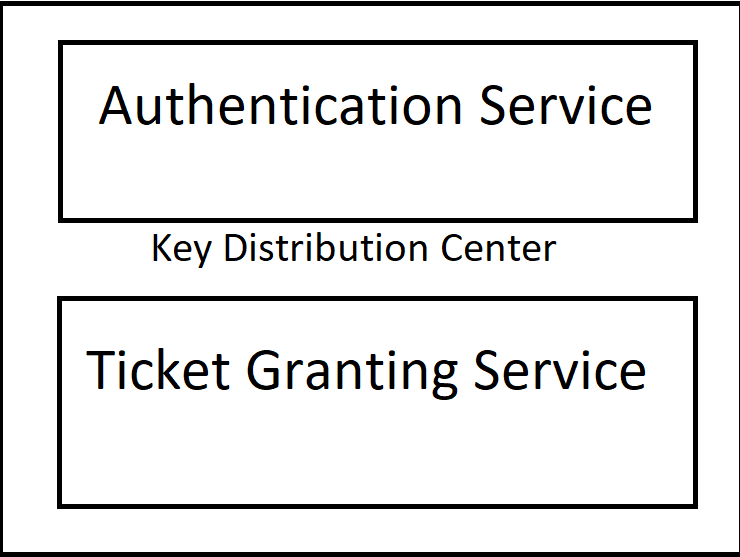
- The first component of Kerberos, the client acts on behalf of the user to request access to the server. The client provides the Authentication server with the user's ID as plaintext and encrypts this message with the password provided by the user.
- The Authentication Servers looks up the user's password from the database using the user's ID. It then uses the user's password to decrypt the the message request. When this verification is performed successfully, the Authentication server grants a Ticket-granting-ticket (TGT) to the client. This TGT is also shared with the Ticket-Granting-Server (TGS) and is encrypted with a secret key.
- The client sends the TGT to the TGS requesting access to the server. TGS then decrypts this TGT with the secret key that was sent over by the Authentication server in the previous step. When this verification is successfully performed, TGS grants a ticket that the client can present to the server it wants access to. TGS also shares this ticket encrypted with a secret key with the server.
- The client can now send over the ticket from TGS to the server. The server decrypts this ticket with the secret key shared by the TGS and gives the client access to the server's resources.
Benefits of Kerberos authentication
- The Kerberos tickets generated are reusable and can be cached on the client's side for later use.
- Kerberos allows authenticated domain entities to use resources across domains
- It also supports smart card Logon which increases security by introducing a two-factor authentication system. This suggests that authentication doesn't just rely on password authentication but also on the users entering a secret smart card pin.
Here's something else you should consider:
As an epilogue to what you've learnt about Kerberos above, if you're monitoring logons and logoffs of users in your network, you'd normally turn to Event Viewer to do this. However we suggest that you give ADAudit Plus a try.
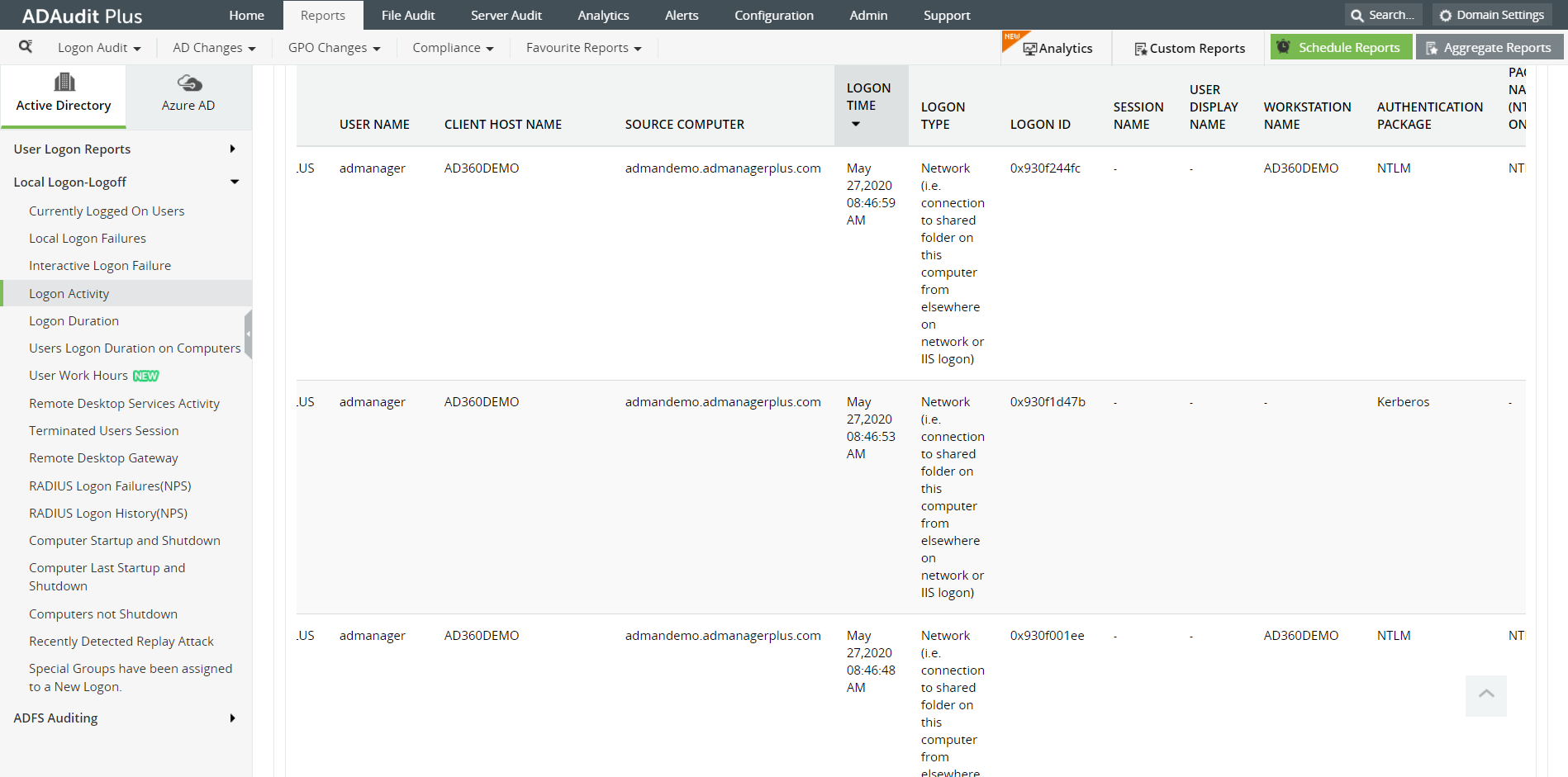
ADAudit Plus is a comprehensive Active Directory(AD) auditing and reporting solution . Its intuitive user interface, pre-configured reports, and advanced filter options make it easy for you to track logons and logoffs in your network efficiently. In the Logon activity, report, check out the 'Authentication Package' column to see which authentication protocol was followed to authenticate a user.
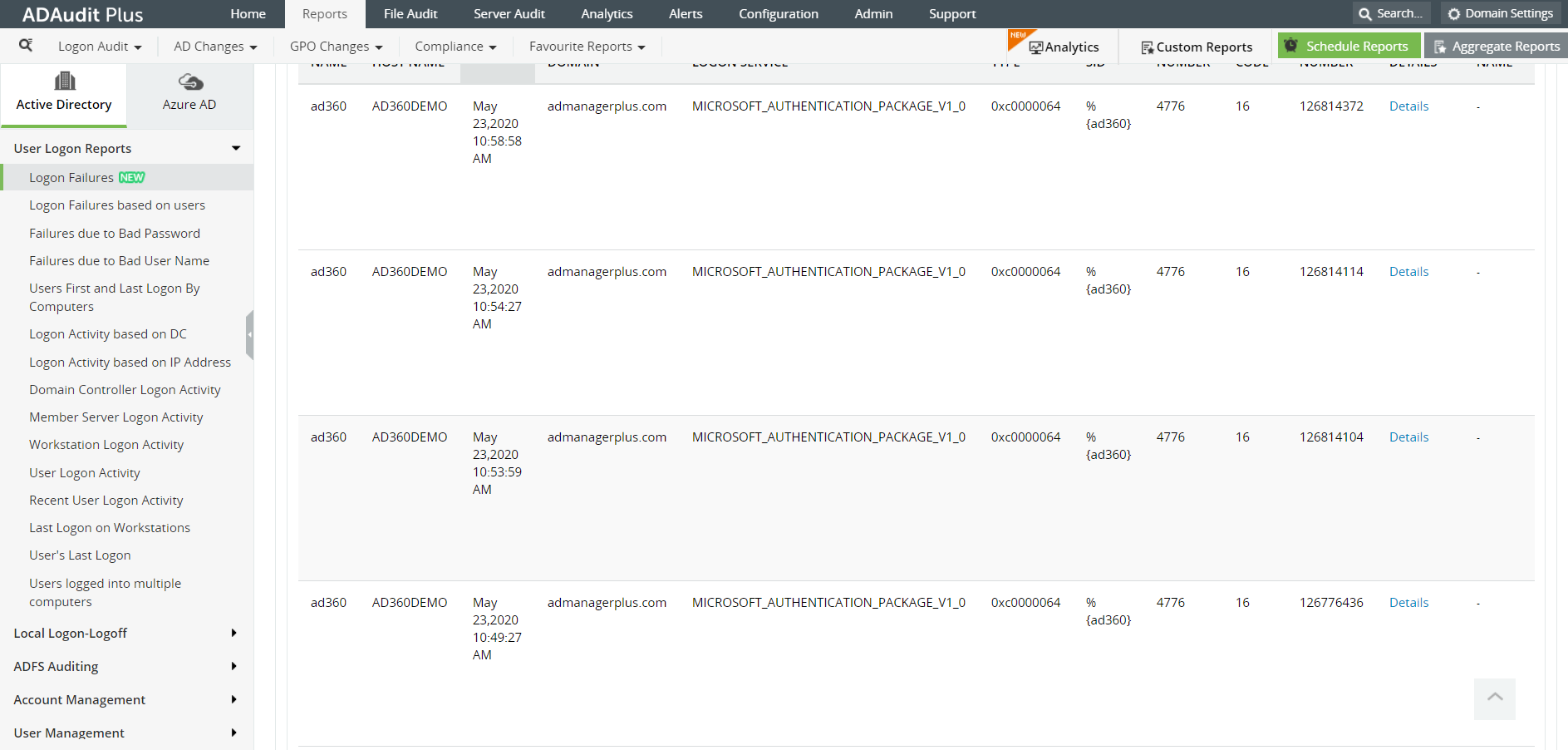
ADAudit Plus is a real-time, web-based Windows Active Directory (AD) change reporting software that audits, reports and alerts on Active Directory, Windows servers and workstations, and NAS storage devices to meet the demands of security, and compliance requirements. You can track AD management changes, processes, folder modifications, permissions changes, and more with 200+ reports and real-time alerts.To learn more, visit https://www.manageengine.com/active-directory-audit/.
✕
Native auditing becoming a little too much?
Try ADAudit Plus login monitoring tool to audit, track, and respond to malicious login and logoff actions instantaneously.
Try ADAudit Plus for free


