Direct Inward Dialing: +1 408 916 9892
Kerberos delegation was introduced in Windows Server 2000. This is a feature that allows an application or service to access resources on another server. A user, for example, might want to access a web server that in turn needs access to a SQL database. Instead of allowing the web server to access the SQL database directly, the web server's service account can be delegated to the SQL database. This means that when a user wants access to a website's resources, the web server's service account poses as the user, to request access to the SQL database. This means that the user can receive access to the database without providing access to web server itself. The initial Kerberos delegation feature became the epicenter for a number of cyber attacks. So, over the years Kerberos delegation evolved into flavors that were more secure than the first.
In the section after this, we'll describe how Kerberos delegation works in all different flavors. But before that, we'll walk you through a few essential concepts to help you connect the dots when we get to the actual delegation process.
This is a physical entity represented by a user account. The user account allows the user to perform everyday tasks according to the configured roles and permissions.
In Kerberos authentication, a Ticket Granting Ticket (TGT) is a user authentication token issued by the Key Distribution Center (KDC) that is used to request access tokens from the Ticket Granting Service (TGS) for specific resources in the domain.
A service is a process that is executed on a computer. The computer acts as a host of the service. Services are identified with a SPN and is executed in the context of a domain user to acquire a TGT from the TGS. A domain user has a list of services they can use. These services are stored as SPNs in the ServicePrincipleName attribute.
A service account is a special account used by an application, and not a user. It can be given permission to access the resources the application needs.
This is the earliest and least secure delegation mechanism that became available in Windows Server 2000. Here, the service is allowed to act on behalf of the user who was authenticated against the domain by acquiring a valid TGT from the client.
For unconstrained delegation, the userAccountControl attribute of an object is updated to a 'Trusted_For_Delegation' flag. When this object authenticates to the host, the TGT from the Kerberos authentication is cached in memory. The host will then use this TGT as the proof of identity of the user to access other services within the domain.
However, this delegation mechanism is unsafe. A cyber attacker could easily hack into a computer or user account and get access to the TGT that was cached. This gives them access to other services on the domain.
This slightly advanced delegation flavor was introduced in the Windows Server 2003 version. A few tweaks to the original delegation mechanism reduced the exposure of the network to possible attacks. In this delegation mechanism, only some third-party services are granted the delegation privilege.
For Constrained delegation, the object's userAccountControl attribute is updated to the “TRUSTED_TO_AUTHENTICATE_FOR_DELEGATION” flag. Also the msDS-AllowedToDelegateTo attribute is updated to the SPN configured on the delegation tab.
Again, Constrained delegation is not attack-proof since NTLM hashes and plain text passwords can be hacked. Once this happens, the hacker can request the TGS for a TGT to access other domain resources.
Resource-based Constrained delegation mechanism reconfigures the way the other two delegation flavors worked. Instead of specifying which object can delegate to what service, the resource hosting the service specifies which object can access its service.From our previous example, a web server service account impersonates the user to gain access to a SQL database. But this time instead of specifying the constrained delegation privilege in the web server service account, we will specify that the web server has this privilege on the SQL database. This means that the resource (SQL database) maintains a list of services that have delegation privileges to it.
Resource-based Constrained delegation configuration includes updating the value of the resource's msDS-AllowedToActOnBehalfOfOtherIdentity attribute with the SID of the object with constrained delegation privileges. Resource-based Constrained delegation configuration can only be done via PowerShell since there is no graphic interface available in the AD Users and Computers console.
As an epilogue to what you've learnt about Kerberos above, if you want to monitor logons and logoffs of users in your network, you'd normally turn to Event Viewer to do this. However we suggest that you give ADAudit Plus a try.
ADAudit Plus is a comprehensive Active Directory(AD) auditing and reporting solution . Its intuitive user interface, pre-configured reports, and advanced filter options make it easy for you to track logons and logoffs in your network efficiently.
In the Logon activity, report, check out the 'Authentication Package' column to see which authentication protocol was used to authenticate a user.
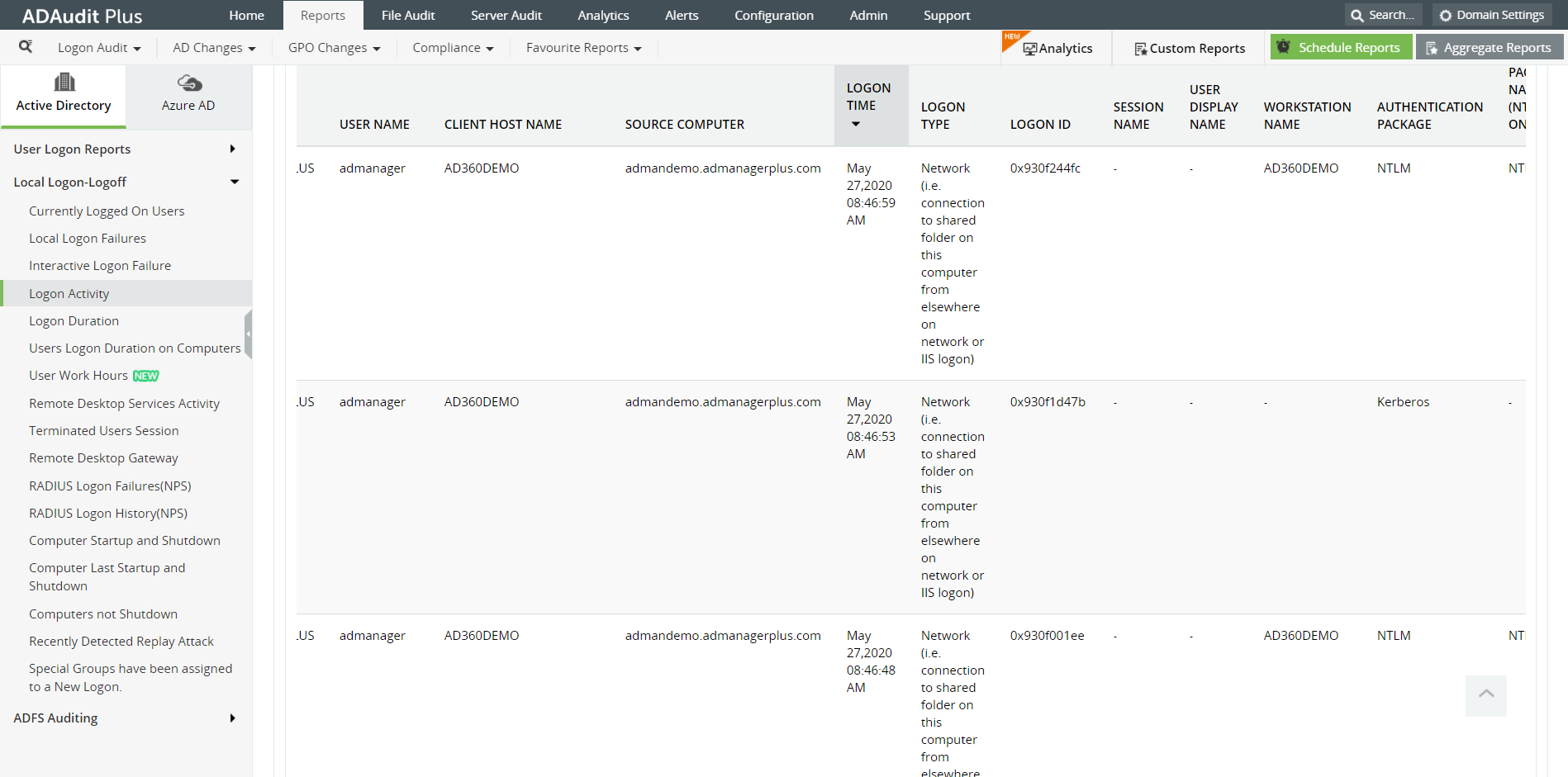 Image: User logon activity report displays essential details related to user logons including which authentication protocol was used to authenticate the user.
Image: User logon activity report displays essential details related to user logons including which authentication protocol was used to authenticate the user.
ADAudit Plus is a real-time, web-based Windows Active Directory (AD) change reporting software that audits, reports and alerts on Active Directory, Windows servers and workstations, and NAS storage devices to meet the demands of security, and compliance requirements. You can track AD management changes, processes, folder modifications, permissions changes, and more with 200+ reports and real-time alerts. To learn more, visit https://www.manageengine.com/active-directory-audit/
Try ADAudit Plus login monitoring tool to audit, track, and respond to malicious login and logoff actions instantaneously.
Try ADAudit Plus for free