Direct Inward Dialing: +1 408 916 9892
The Lightweight Directory Access Protocol (LDAP) developed in 1993 was a core protocol that eventually paved the way for Microsoft's Active Directory. LDAP was developed to give users access to information stored in databases. This information was organized into directory information trees. To access the information, the user first needed to authenticate themselves. The authentication protocol was based on a client-server model. The client is a system requesting access to information in an LDAP database while the server is an LDAP server.
To authenticate a username, you need the user's 'Distinguished Name' (DN). The DN is rather like a breadcrumb or a web trail you see on some sites.
For example here's how a user named Betty's DN looks. To understand the DN you need to read it from right to left.
uid=betty, ou=users, dc=adap, dc=netObviously judging by the length of the DN, you can't expect a user to remember it when providing the credentials for authentication. So instead of this, the client collects the user's username or email ID and performs a DN resolution which is analogous to a DNS resolution when you're looking up a website's IP address.
The username or email ID is run against a database of all user entries until an exact match turns up. The directory attributes to search for are specified in the searchFilter configuration parameter.
ldapAuth.dnResolution.searchFilter = (|(uid=%u)(mail=%u))%u is replaced with the user identifiers collected in the login form.LDAP authentication uses a bind command to authenticate users and give them the required access. To validate the password, the DN of the user and the password provided by the user are scanned. This password provided by the user is checked against the value stored in the schema attribute name userPassword.
Any LDAP related error is logged in the Service logs, so you can check these logs to troubleshoot. For example, this is how your Service log reports an error in authentication due to a bad username:
2020-01-01 11:32:51,460 INFO – user.auth: username=betty authenticated=false message=Invalid usernameIf spending hours looking through your logs on native tools isn't your thing (and we're pretty sure it's not), you can check out ADAudit Plus.
ADAuditPlus is a comprehensive solution that simplifies your AD auditing and reporting needs. Login to an intuitive dashboard that gives you a holistic view of all the activities recorded on your network. You also have access to over 300 detailed pre-configured reports that make tracking network activity quick and easy.
As a follow up to what you've learned above about LDAP Authentication, here's a sneak peek at our ADAudit Plus dashboard, that provides you with detailed LDAP auditing reports.
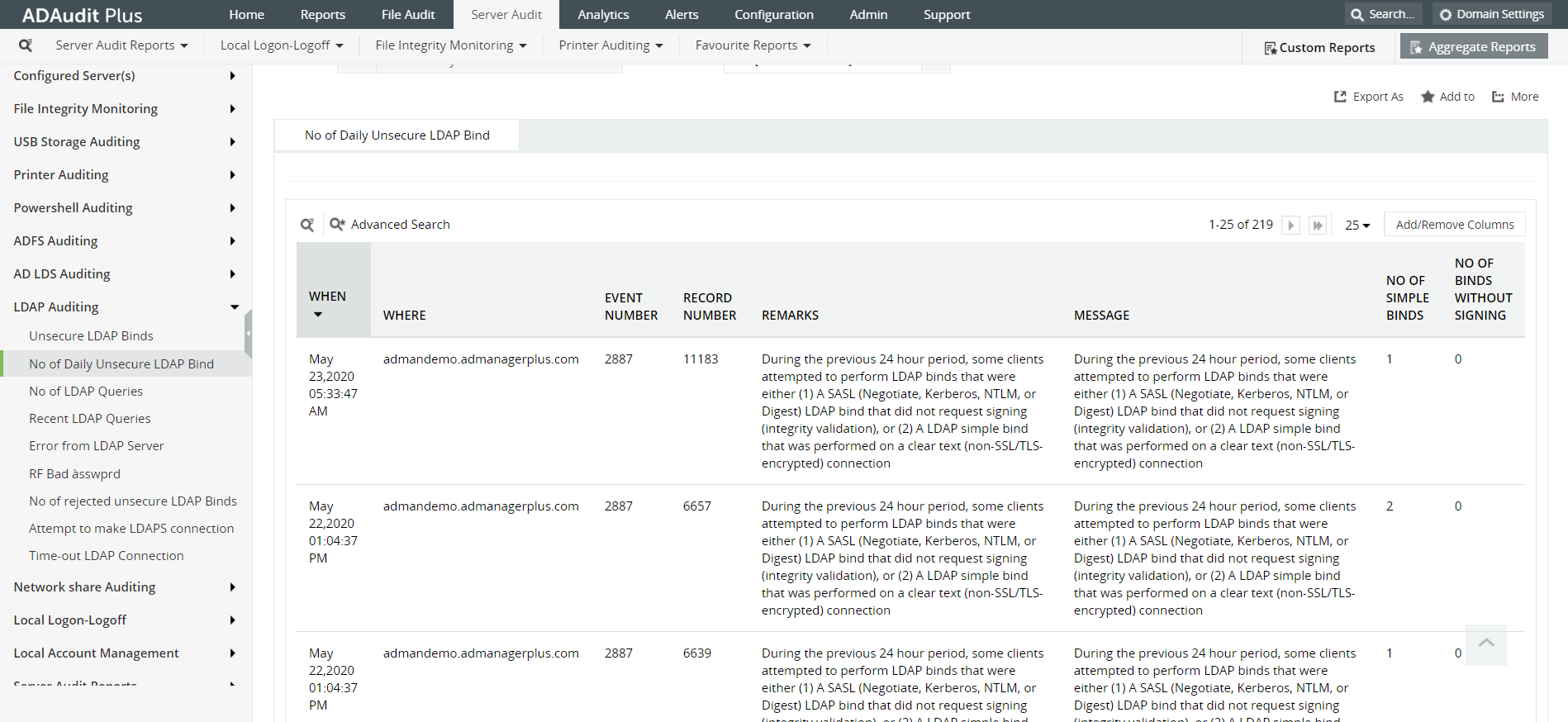
ADAudit Plus is a real-time, web-based Windows Active Directory (AD) change reporting software that audits, reports and alerts on Active Directory, Windows servers and workstations, and NAS storage devices to meet the demands of security, and compliance requirements. You can track AD management changes, processes, folder modifications, permissions changes, and more with 200+ reports and real-time alerts.To learn more, visit https://www.manageengine.com/active-directory-audit/.
Try ADAudit Plus login monitoring tool to audit, track, and respond to malicious login and logoff actions instantaneously.
Try ADAudit Plus for free