Direct Inward Dialing: +1 408 916 9892
The Sarbanes-Oxley Act (SOX), passed in 2002 by the United States Congress, aims to regulate the financial reporting activities of public companies. The objective of this compliance mandate is to minimize financial fraud and thereby make companies more accountable to their shareholders and the general public. This is achieved partly by making corporate disclosures more transparent.
Though SOX helps protecting consumers from financial fraud, it also has requirements that would require the company to secure sensitive financial data such as financial account numbers, banking records and so on. Here's where the IT department can pitch in to ensure data security and integrity.
1. Sec. 302. Corporate Responsibility For Financial Reports
This section stipulates that the CEO, CFO or any other employees who perform similar functions, of a company should closely review the quarterly and yearly financial reports of the company. If any part of these documents is factually incorrect, they would be held personally responsible.
Therefore, the IT department has to ensure the integrity of such financial data by monitoring the access permissions to it. Any unauthorized attempt to access, modify, or delete such data should be prevented.
2. Section 404: Management assessment of internal controls
This section demands that companies have an efficient internal controls system to ensure that all financial data is accurate and that adequate controls are in place to safeguard this data. Therefore, the company has to implement a set of rules or policies to harden the data security.
The IT department will have to establish, manage, and constantly review internal controls that will streamline the sensitive data access. For instance, the IT teams are responsible for implementing a strong password policies which protect the systems with sensitive data from credential-based attacks, thereby preventing the data from falling into the wrong hands. Added to that, establishing principle of least privilege (POLP), granting permissions only to the right persons, will help in establishing effective internal controls.
The responsibility of the IT team doesn't stop with establishing these controls, but also extends beyond that. They need to constantly monitor these controls, and user activities within the network to ensure that the data is secure.
Furthermore, they are also expected to deploy tools that handle the situation in case of a data leak or security incident. These tools should help them respond to an attack or incident quickly and thereby prevent further damage.
3. Section 802: Criminal penalties for altering documents
The Act imposes up to 20 years of imprisonment for modifying, altering or falsifying the documents in any way.
This section also requires that the auditing records have to be maintained for a minimum of 5 years from the fiscal year the audit was conducted, and any person who willfully violates this can also face criminal charges.
This means that the IT department should employ tools that can audit and report on the network activities at all times. If there is an attempt to falsify or modify any data, it should be prevented and the person responsible must be identified. The security tools implemented should also be able to archive the audit records. The persons involved in any unauthorized changes to the data can be found through forensic analysis of these archive records.
4. Section 902: Attempts and conspiracies to commit criminal fraud offenses
This section of SOXsays that the punishment for attempting or conspiring to commit fraud would the same as the punishment for committing the crime itself.
This means that the IT department should employ tools that can monitor and report on the network. For example, the tools should be able to detect and alert admins in real-time of file modifications by unauthorized users or attempts to delete files. The admin can then identify the agents who tried to tamper with the network data.
ADAudit Plus is a real-time, Active Directory auditing and reporting tool that monitors your network constantly and provides over 200 audit reports on the various entities and events such as users, servers, logons, file modifications and so on. This tool has a section for compliance which has separate reports for different compliance mandates, including SOX. The section for SOX has reports on the different activities that need to be monitored for a company to stay SOX-compliant such as file modifications, logon activity and so on. Here is a list of reports that are available in the SOX section of ADAudit Plus:
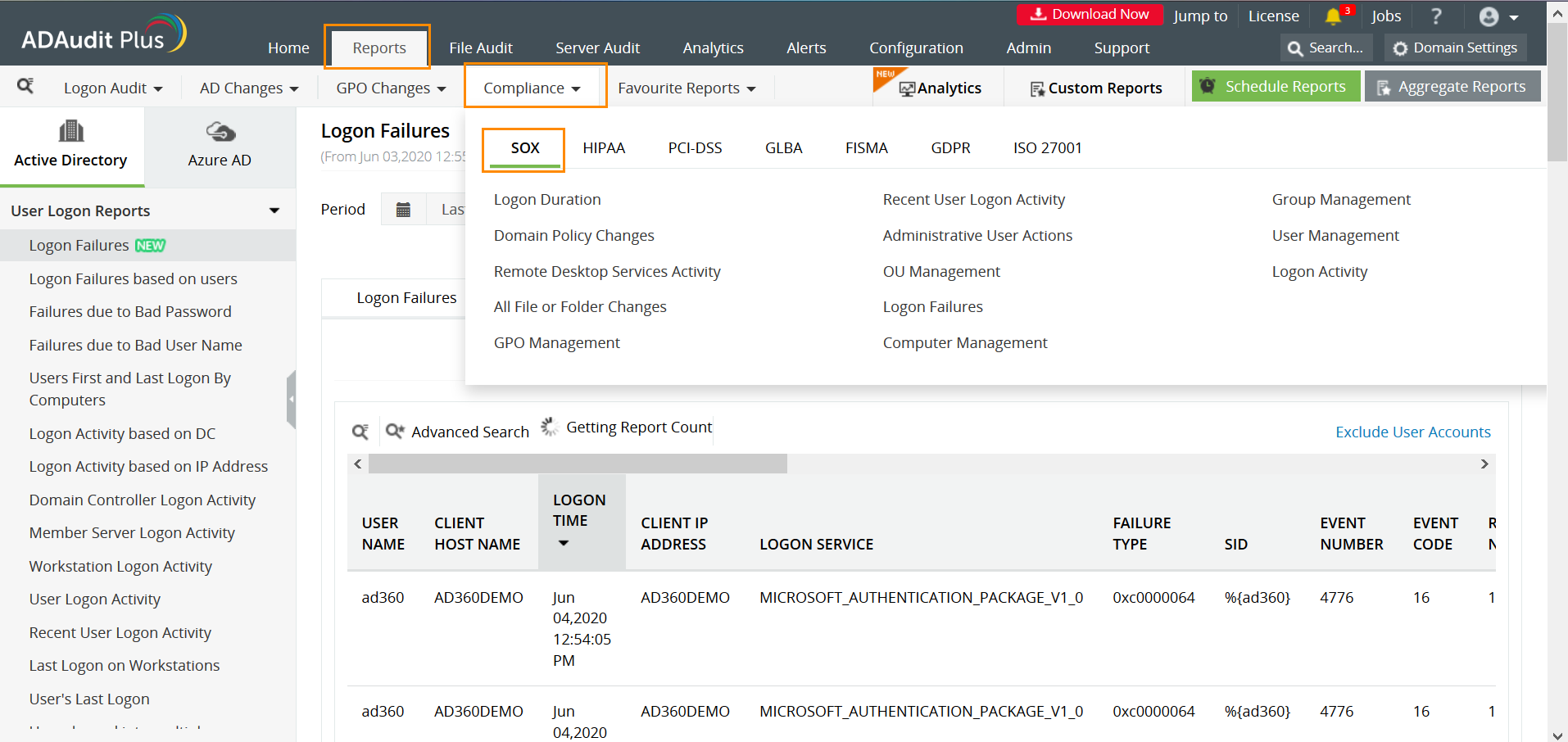
The SOX section has reports on Logon activity, File or folder modifications, OU management among others. These reports effectively monitor all the user and entity activities and events on the network.
ADAudit Plus is a real-time, web-based Windows Active Directory change reporting software that audits, tracks, reports and alerts on Windows (Active Directory, workstations logon/logoff, file servers and servers), NetApp filers and EMC servers to help meet the demands of the much-needed security, audit and compliance. With ADAudit Plus, track authorized/unauthorized AD management changes, access of users, GPO, groups, computer, OU. Track every file, folder modifications, access and permissions changes with 200+ detailed event-specific reports and get instant emails alerts. You can also export the results to XLS, HTML, PDF and CSV formats to assist in interpretation and computer forensics. For more information on ADAudit Plus, visit https://www.manageengine.com/active-directory-audit/.
Try ADAudit Plus login monitoring tool to audit, track, and respond to malicious login and logoff actions instantaneously.
Try ADAudit Plus for free