Direct Inward Dialing: +1 408 916 9892
Principle of least privilege (POLP) is a highly recommended IT security best practice. According to this principle, employees of a company should have access only to the tools and data that they need to perform their jobs and nothing more. This principle is also known by other names such as Principle of Minimum Privilege (POMP) and Principle of Least Authority (POLA).
Following this principle at your company will ensure that not too many people have access to your firm's sensitive data. This will reduce the number of people that can access the data, thereby giving it more protection from insider and outsider threats.
According to POLP, the employees will be given access to only those resources that they need to perform their role. For example, a software developer who works with codes does not need access to the company's financial data. Or an employee who works in Marketing does not need access to the highly sensitive, proprietary code that developers use. As this will reduce the number of people who have access to sensitive data, it becomes easier to spot any malicious actor who attempts to steal or tamper with it.
In a company which uses POLP, it will be easy to detect any unusual activity surrounding the sensitive data. This process is made easier with ADAudit Plus, an Active Directory auditing tool, which tracks user, group and server activities on the network. The tool uses User Behavior Analytics (UBA) to identify unusual activities on the network. For example, if a user suddenly downloads a lot of information from the file servers, that they generally should not have access to, ADAudit Plus raises an alert in real time. The admin can also use the audit reports on ADAudit Plus to check the users who have accessed the sensitive files or the users who have been added to privileged AD security groups recently. Here is a sample report from ADAudit Plus on administrative user actions:
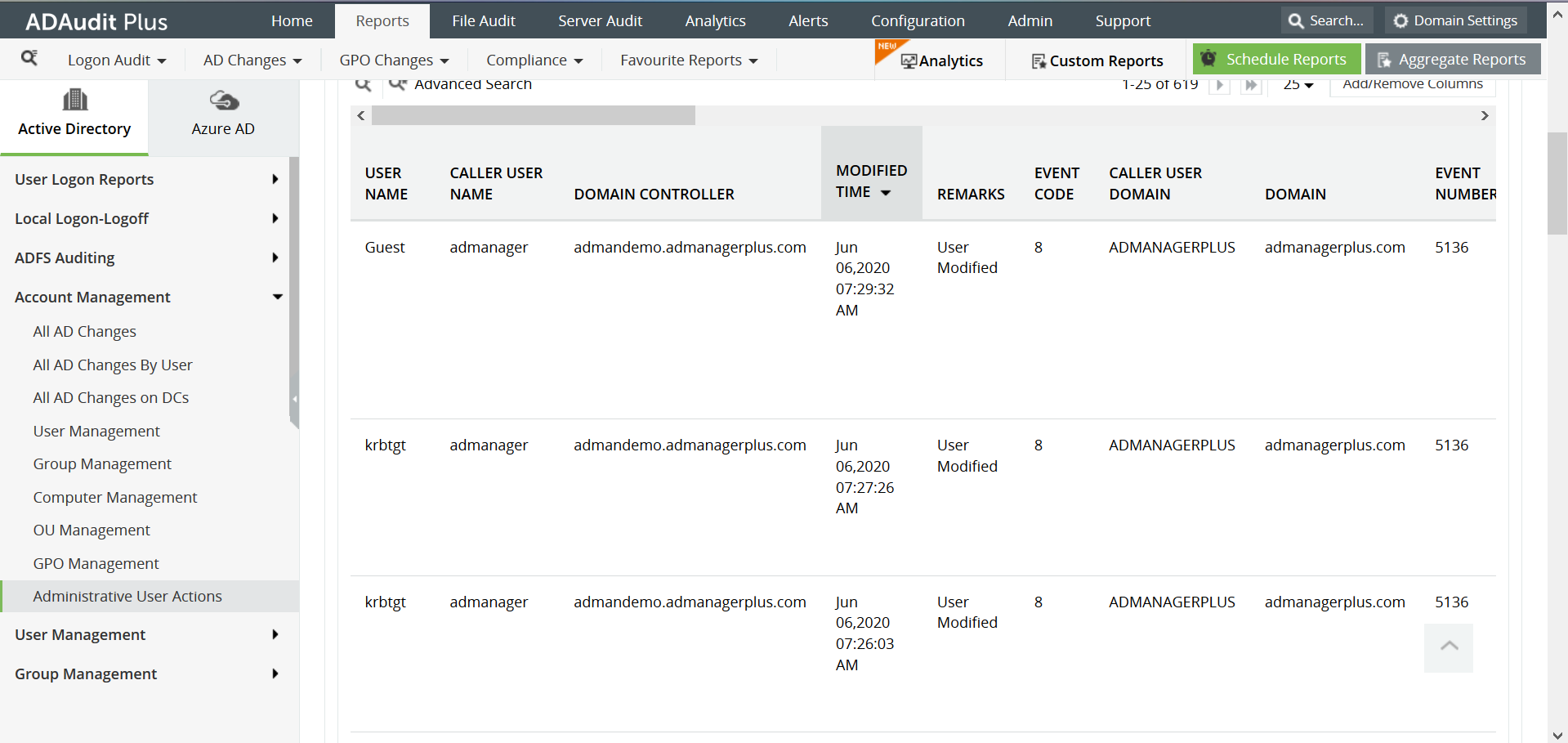
In a company which uses POLP, it will be easy to detect any unusual activity surrounding the sensitive data. This process is made easier with ADAudit Plus, an Active Directory auditing tool, which tracks user, group and server activities on the network. The tool uses User Behavior Analytics (UBA) to identify unusual activities on the network. For example, if a user suddenly downloads a lot of information from the file servers, that they generally should not have access to, ADAudit Plus raises an alert in real time. The admin can also use the audit reports on ADAudit Plus to check the users who have accessed the sensitive files or the users who have been added to privileged AD security groups recently. Here is a sample report from ADAudit Plus on administrative user actions:
ADAudit Plus is a real-time, web-based Windows Active Directory change reporting software that audits, tracks, reports and alerts on Windows (Active Directory, workstations logon/logoff, file servers and servers), NetApp filers and EMC servers to help meet the demands of the much-needed security, audit and compliance. With ADAudit Plus, track authorized/unauthorized AD management changes, access of users, GPO, groups, computer, OU. Track every file, folder modifications, access and permissions changes with 200+ detailed event-specific reports and get instant emails alerts. You can also export the results to XLS, HTML, PDF and CSV formats to assist in interpretation and computer forensics. For more information on ADAudit Plus, visit https://www.manageengine.com/active-directory-audit/ .
Try ADAudit Plus login monitoring tool to audit, track, and respond to malicious login and logoff actions instantaneously.
Try ADAudit Plus for free