DNS misconfiguration, service failures (DNS, Kerberos, NetLogon), replication delays, old or stale computer objects, and inadequate permissions delegation.
- 5 essential Active Directory health checks
- Automate health reports
- Best practices
- Leveraging ADAudit Plus
- Troubleshooting and FAQ
Prerequisites
Before performing these checks, ensure:
- You have administrator PowerShell access to run commands and access logs.
- There is network connectivity to all domain controllers.
- You have sufficient permissions to read event logs and run diagnostics like DCDiag or Repadmin.
5 essential Active Directory health checks
Keep your Active Directory environment secure, stable, and performing at its best with these five essential checks.
1. Check domain controller replication health
You can check the replication status of all domain controllers in all domains of the forest, including when a domain controller (DC) last replicated and any reasons replication may have stopped, by running the following command in PowerShell:
Repadmin /replsummary
Here's a sample output:
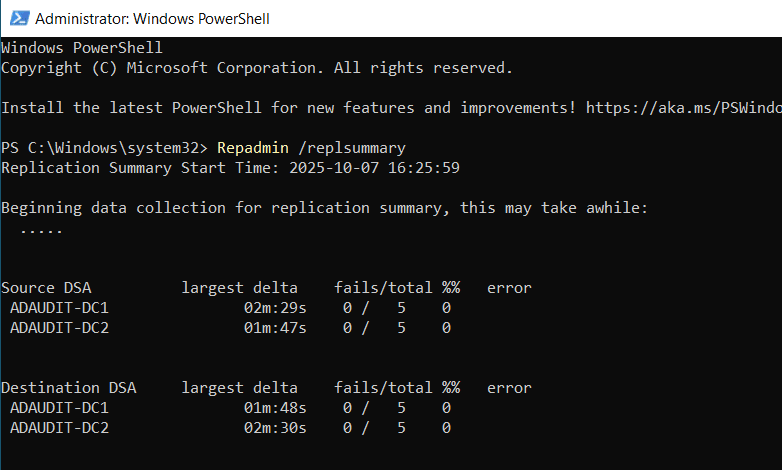
How to interpret the output:
- Look at the fails column to identify replication failures.
- The largest delta column shows the longest replication delay across all DCs.
- Any errors listed under a specific DC indicate where troubleshooting is needed.
To learn more about DC replication, click here.
2. Verify Active-Directory-related services are running
There are four system components that are critical for the efficient running of Active Directory Domain Services:
- DFS Replication: Ensures files and folders are consistently replicated across multiple servers in the network.
- DNS Server: Resolves domain names to IP addresses, critical for domain controller communication.
- Intersite Messaging: Facilitates replication and messaging between domain controllers in different sites.
- Kerberos Key Distribution Center: Authenticates users and issues Kerberos tickets for secure access.
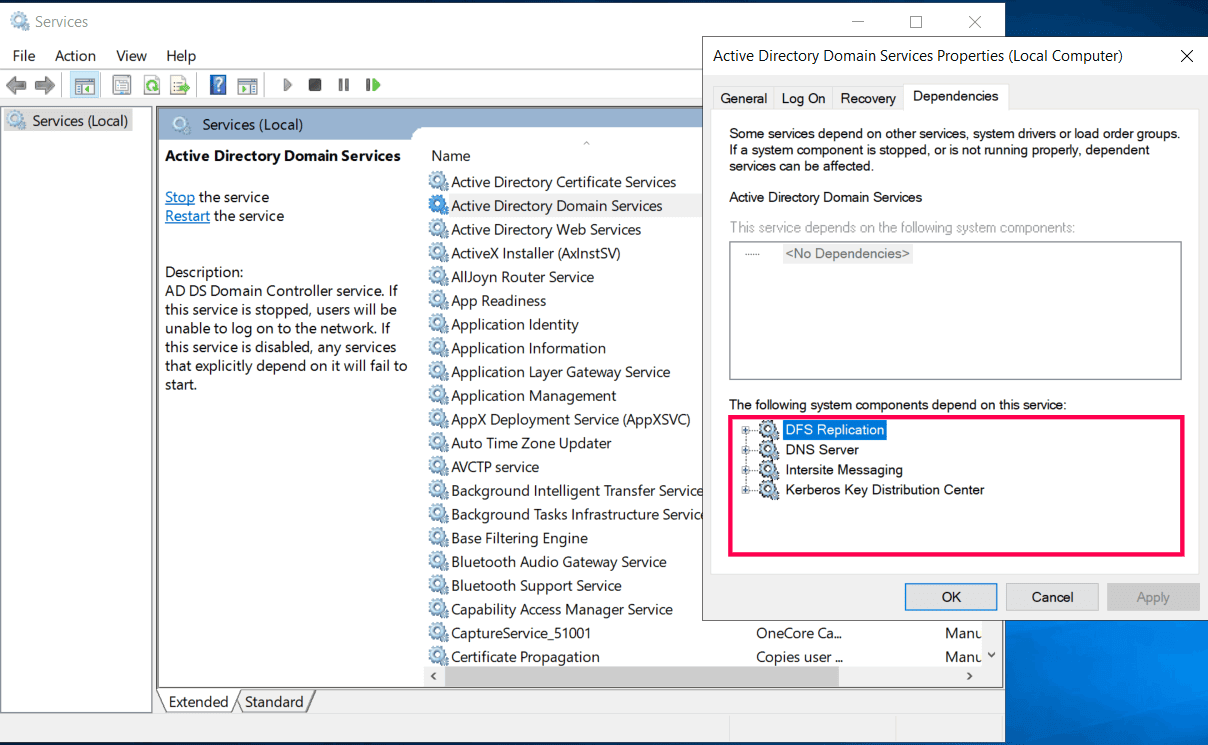
Make sure that these components are running properly by executing the following command in PowerShell:
$Services='DNS','DFS Replication','Intersite Messaging','Kerberos Key Distribution Center','NetLogon','Active Directory Domain Services'
ForEach ($Service in $Services) {Get-Service $Service | Select-Object Name, Status}
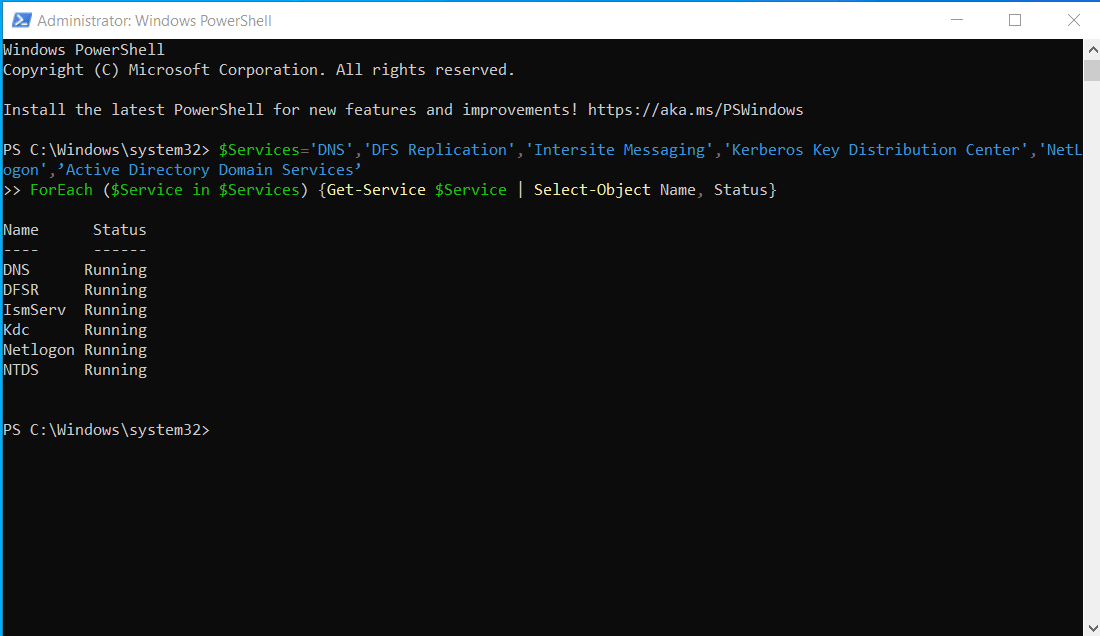
Note:
This above command also checks:
- NetLogon service: Handles authentication requests and locates domain controllers in Active Directory.
- NTDS (Active Directory Domain Services): The core service that stores and manages Active Directory objects and replication.
3. Run DCDiag for Active Directory diagnostics
The Domain Controller Diagnostic (DCDiag) tool allows IT administrators to test various aspects of a domain controller, including DNS. One of the most common causes of Active Directory performance issues is DNS failure, which can also lead to replication problems. Running DCDiag for DNS helps administrators verify:
- The health of DNS forwarders
- DNS delegation
- DNS record registration
Here's the PowerShell command to run the DCDiag tool:
DCDiag /Test:DNS /e /v
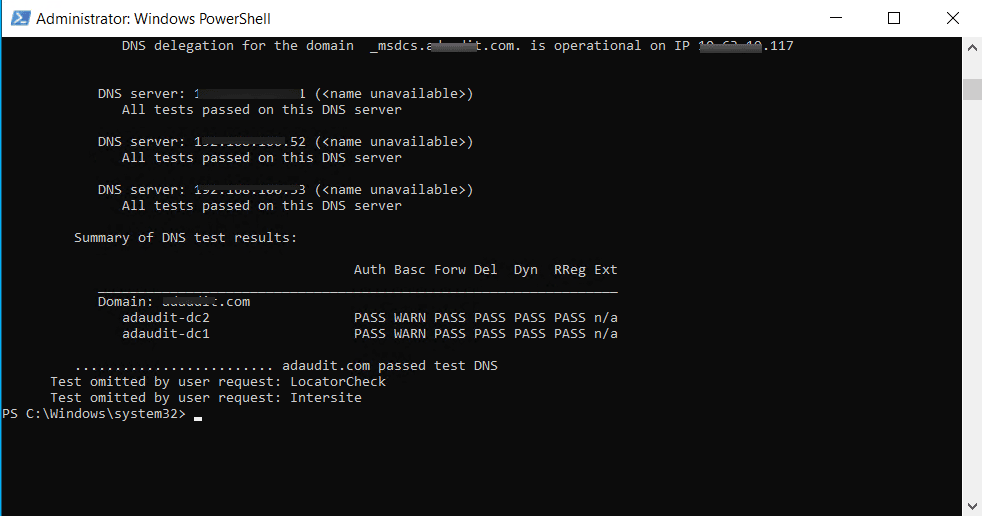
How to interpret the output:
| Column | Meaning |
|---|---|
| Auth | Checks if the DNS server is authoritative for the domain. |
| Basc | Basic connectivity and configuration test: Ensures DC can contact other DNS servers and resolve queries correctly. |
| Forw | Forwarder test: Checks if DNS forwarding is configured and functional. |
| Del | Delegation: Verifies DNS delegations are configured properly. |
| Dyn | Dynamic updates: Confirms the DNS zones accept secure dynamic updates. |
| RReg | Record Registration: Ensures DCs can register their SRV and host records. |
| Ext | External name resolution: Tests external DNS resolution (e.g., internet names). |
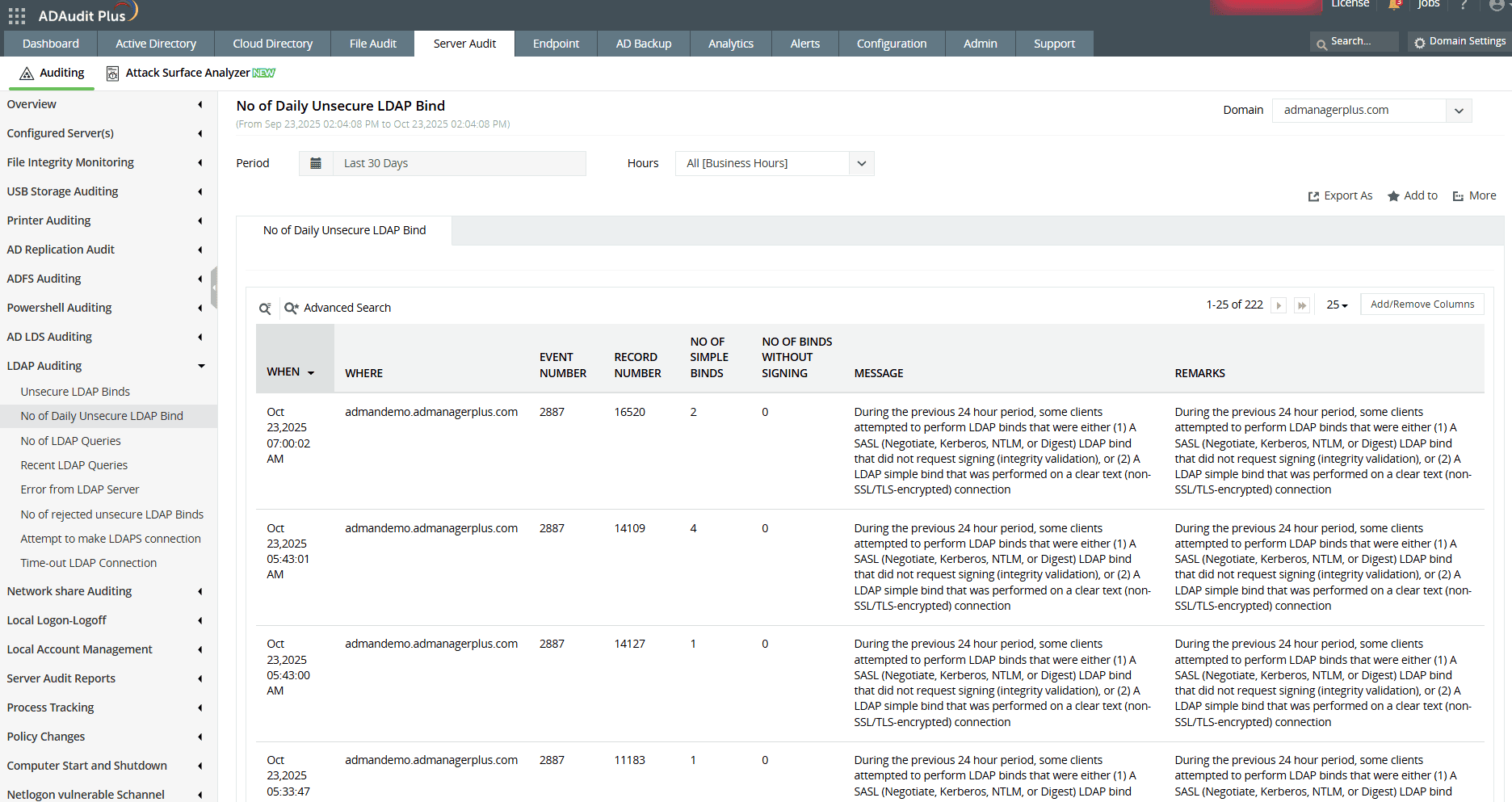
4. Detect unsecure LDAP binds
Unsecure LDAP binds are dangerous because they transmit credentials in cleartext, making it possible for attackers to intercept and misuse them. Identifying and addressing these binds is critical to securing your Active Directory environment.
The first step in mitigating the vulnerability of unsecure LDAP binds is to determine whether your environment is affected. Here's how:
Audit for event ID 2887
Event 2887 is logged by default on the DC once every 24 hours and shows the number of unsigned and cleartext binds to the DC. Any number greater than zero indicates that your DC is allowing unsecure LDAP binds.
The PowerShell command to retrieve this information is as follows:
Get-WinEvent -FilterHashtable @{
LogName = 'Security'
ID = 2887
}
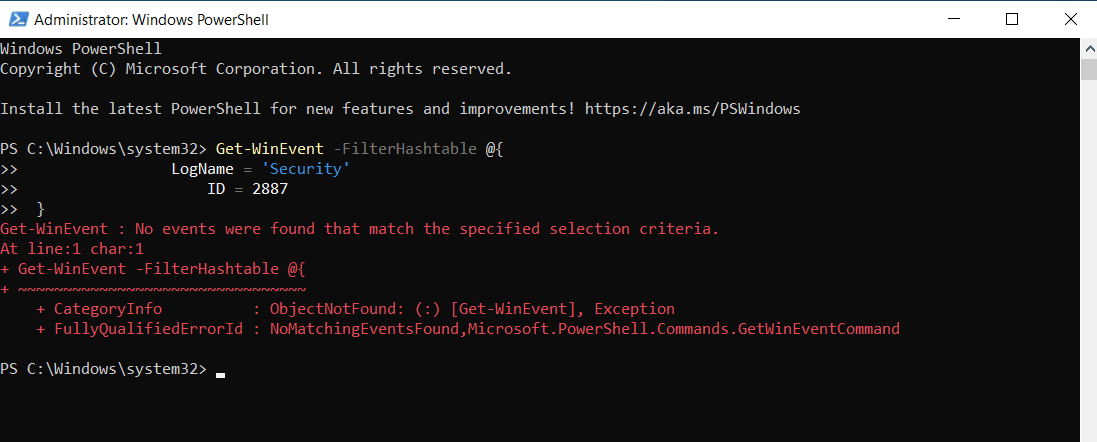
In this sample output, we don't see any unsecure binds.
Audit for event ID 2889
Event 2889 is logged on the DC each time a client computer attempts an unsigned LDAP bind. It provides the IP address and account name of the computer that attempted authentication over an unsigned LDAP bind.
The PowerShell command to retrieve this information is as follows:
Get-WinEvent -FilterHashtable @{
LogName = 'Security'
ID = 2889
}
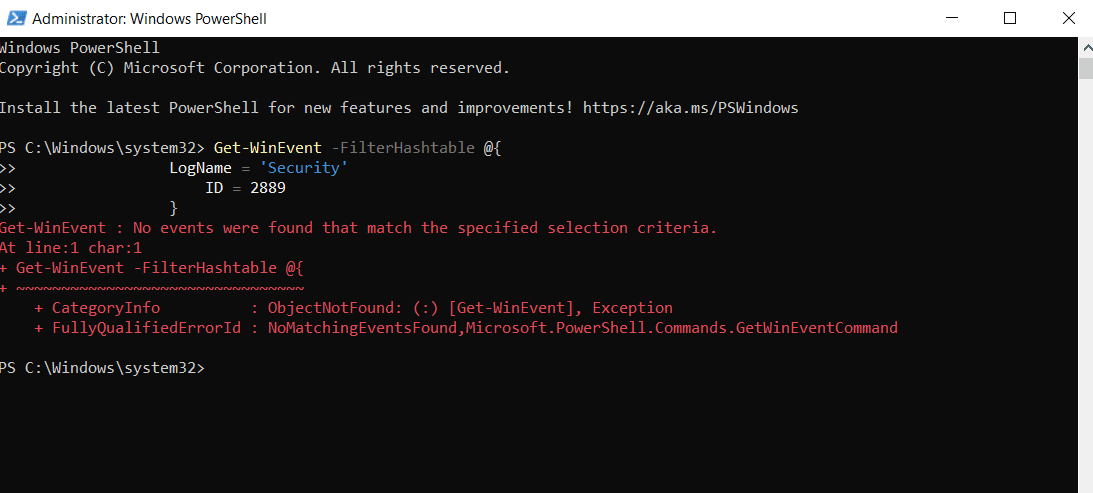
In this sample output, we don't see any unsecure binds.
5. Check SYSVOL and NETLOGON share availability
These shared folders are essential for Group Policy and logon scripts to work correctly. If they're missing or inaccessible, users may face login issues or failed policy updates.
The PowerShell command to retrieve this information is as follows:
Test-Path \\$env:USERDNSDOMAIN\SYSVOL
Test-Path \\$env:USERDNSDOMAIN\NETLOGON
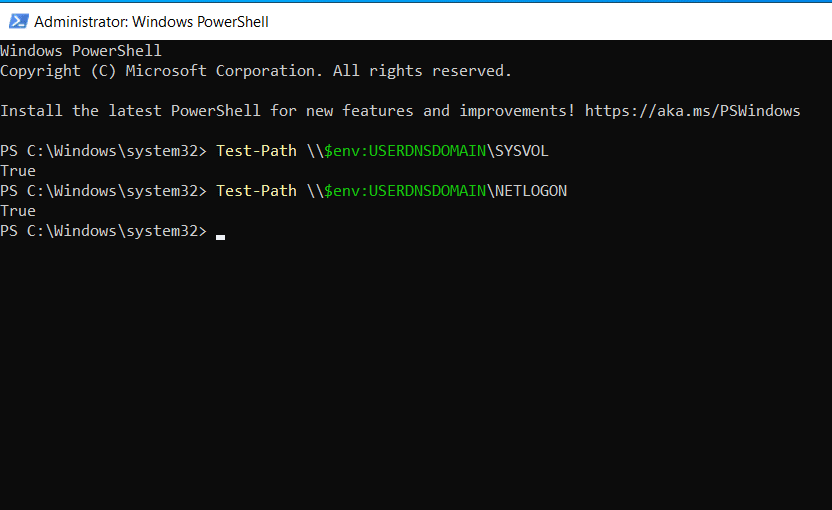
How to interpret the output:
- True: If both commands return True, the shares are accessible.
- False: A False result may indicate replication or permissions issues with SYSVOL.
Automate your Active Directory health check
Here's a PowerShell script that automates Active Directory health checks and generates a summary report. It runs diagnostics for replication, service status, DNS health, LDAP binds, and logs results to a timestamped file.
$date=Get-Date -Format "yyyyMMdd-HHmmss"
$log="C:\ADHealthReport_$date.txt"
"AD Health Check - $date" | Out-File $log
Write-Host "Checking Replication..."
repadmin /replsummary | Out-File $log -Append
Write-Host "Checking AD Services..."
$services='DNS','DFS Replication','NetLogon','NTDS'
Get-Service $services | Select-Object Name,Status | Out-String | Out-File $log -Append
Write-Host "Running DCDiag DNS Test..."
dcdiag /test:DNS /e /v | Out-File $log -Append
Write-Host "Checking LDAP Binds (Events 2887 & 2889)..."
Get-WinEvent -FilterHashtable @{LogName='Security';ID=2887} -MaxEvents 1 | Out-File $log -Append
Get-WinEvent -FilterHashtable @{LogName='Security';ID=2889} -MaxEvents 10 | Out-File $log -Append
Write-Host "Checking SYSVOL Share..."
(net share) | Out-File $log -Append
Write-Host "Health Check Report saved to $log"
Note:
This script needs be scheduled to run periodically using Task Scheduler with appropriate administrative privileges. It creates a detailed text report that consolidates Active Directory health information in one place, ready for review or automated email forwarding.
Best practices to keep Active Directory healthy
After performing these checks and diagnostics, following these best practices will help maintain Active Directory health over time:
- Perform regular domain health checks: Schedule weekly replication and DNS diagnostics to identify issues early.
- Monitor event logs proactively: Keep an eye on Event IDs such as 1311, 1864, and 2889 to detect replication errors or unsecured LDAP binds.
- Automate monitoring with PowerShell or tools: Use scheduled scripts or AD auditing solutions to track health continuously without manual intervention.
- Verify DNS health on all domain controllers: Ensure proper DNS registration and resolution to prevent replication failures.
- Maintain regular backups: Keep both system state and Active Directory database backups to recover quickly from corruption or failures.
Monitoring Active Directory with ADAudit Plus
ADAudit Plus automates Active Directory monitoring, providing continuous visibility and real-time alerts to help IT teams maintain a healthy environment. Key areas include:
- DNS zones modified: Detect deleted or modified DNS zones to prevent replication or name resolution issues.
- Replica sync history: Track replication between DCs to identify failures, delays, or inconsistencies.
- Unsecure LDAP binds: Monitor LDAP activity across your domain controllers with event-based reports, long-term log retention, and real-time alerts.
- Registry edits: Audit changes to sensitive registry keys affecting Active Directory or system configuration.
A one-stop solution for all your IT auditing, compliance, and security needs
ADAudit Plus provides capabilities like change auditing, logon monitoring, file tracking, compliance reporting, attack surface analysis, response automation, and backup and recovery for diverse IT systems.
Troubleshooting and FAQ
Ideally, run replication and DNS diagnostics weekly. Continuous monitoring via scripts or auditing tools is recommended for critical environments.
Replication can fail due to network issues, DNS misconfigurations, or stopped critical services. Run repadmin /replsummary, check connectivity between DCs, and verify that services like NTDS and DFS Replication are running.
Your account might lack the required permissions. Ensure it is part of the Event Log Readers group or has delegated access to the needed logs.
Experience
ADAudit Plus for free
With ADAudit Plus, you can:
- Check replication sync history
- Track unsecure LDAP binds
- Get alerts on critical AD changes
- Detect 25+ types of AD attacks
- And much more