IT Asset Inventory Management
The first and the most important part of IT Asset Management (ITAM) is to be able to scan/discover all the assets in your network. Only when you have discovered all the assets can you efficiently monitor and manage them. AssetExplorer gives you a wide range of asset scanning methods to make sure that you get them all.
Asset Management
All the assets in the network are broadly categorized in AssetExplorer as IT Assets, non-IT assets, asset components, software and groups.
Product and vendor details
Group assets and manage them easily
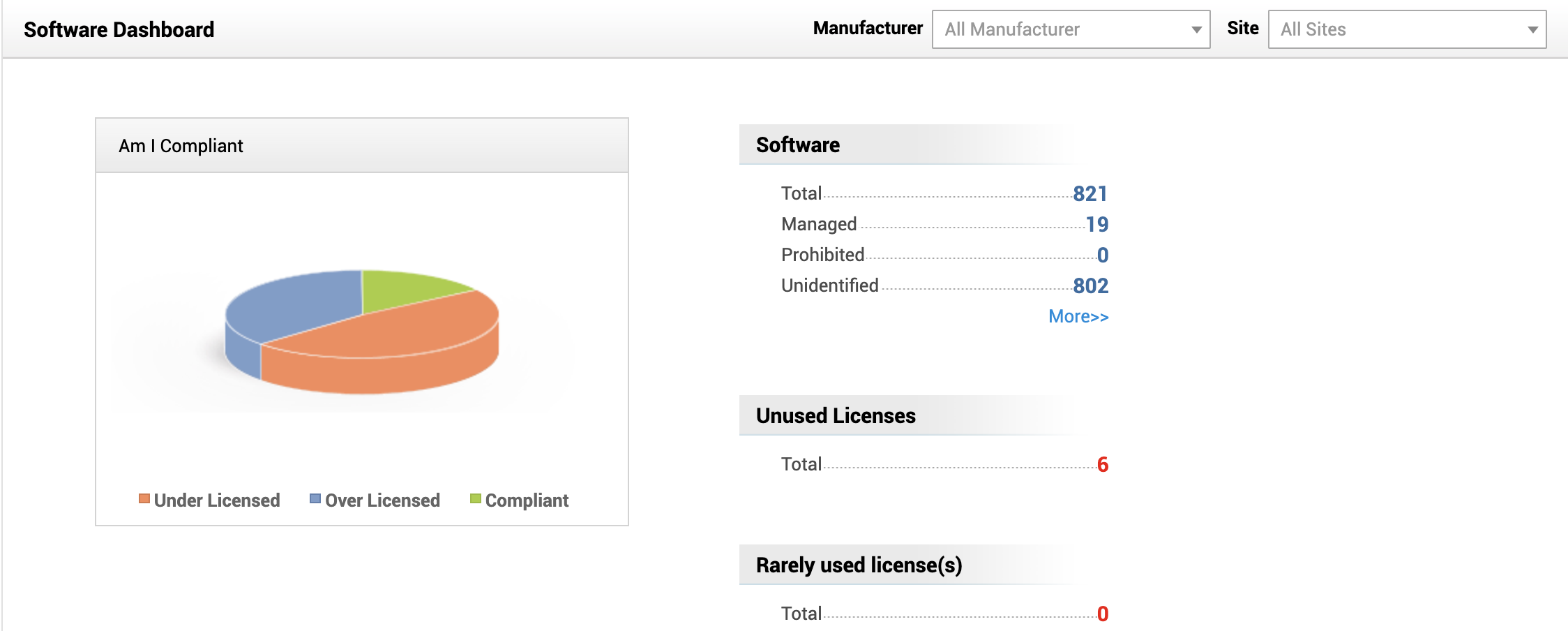
View software compliance with Flash charts
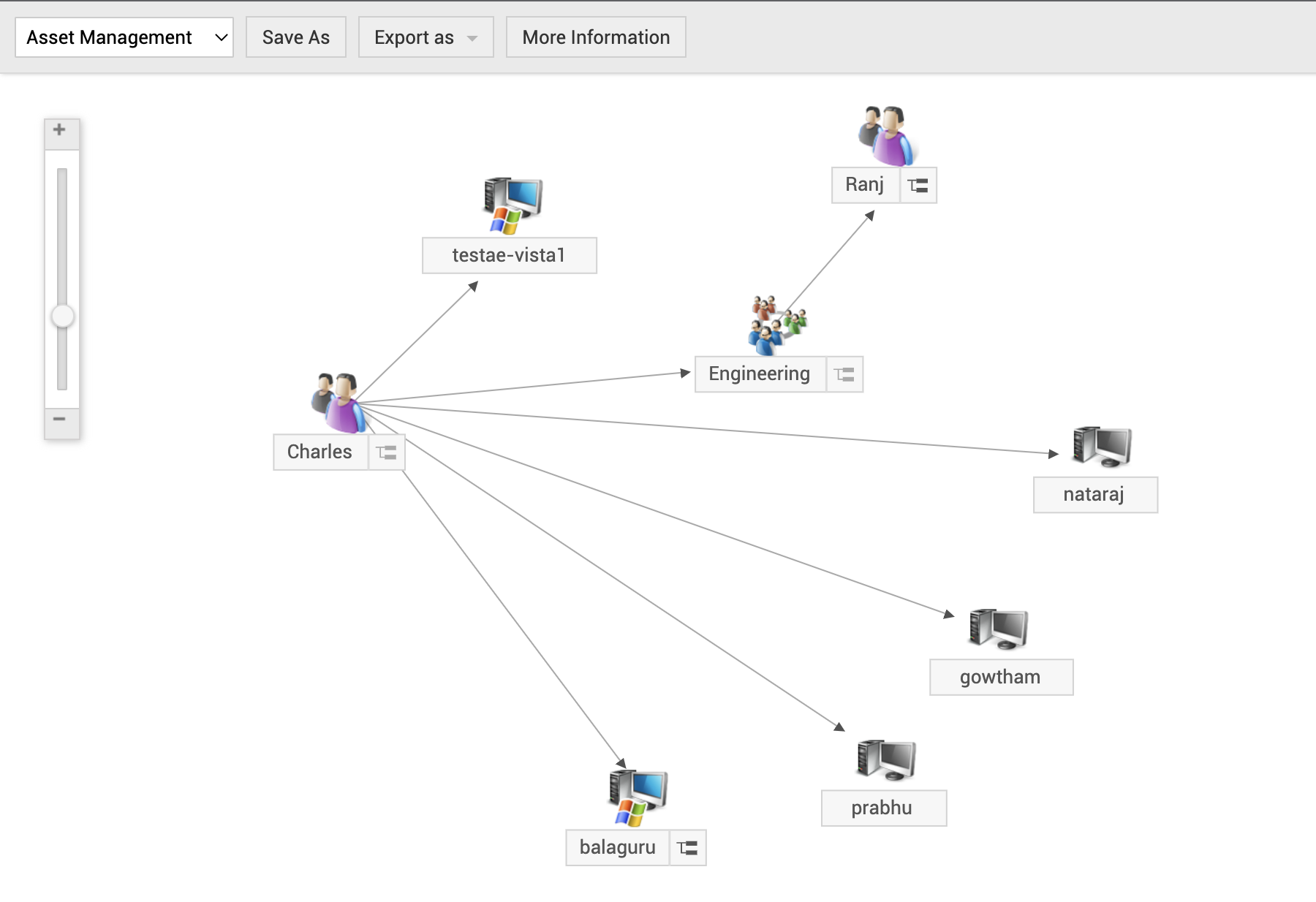
Relationship between your business critical resources
Experience powerful asset discovery capabilities with AssetExplorer
Facing bottlenecks in discovering and mapping your IT asset landscape? The unified agent for asset discovery helps IT administrators discover, track, and manage IT assets spread across their organization without a hitch.
The unified agent scans Windows, Linux, and macOS devices and ensures uniformity of data fetched across these devices. The unified agent installed on the workstation (in the same network or remote location) delivers information into the ManageEngine AssetExplorer database during the first scan. During subsequent scans, the agent updates the changes in the asset data in the AssetExplorer database.
Other scanning techniques:
Network and network range scans
This method of asset scanning is used to discover and track IP devices, such as routers, switches, and printers. Enter the Network name or the network range, and AssetExplorer takes care of rounding up the assets to your dashboard.
Individual asset scan
You can also scan IT assets individually by providing the IP address of the specific asset.
Manual import
When all else fails, or if you have a CSV file of all your assets, you can simply import the file and add all the assets to AssetExplorer.