About the vulnerability
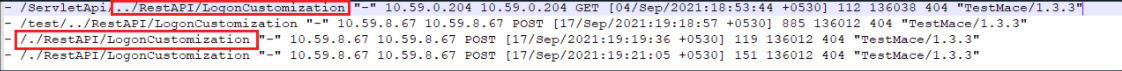
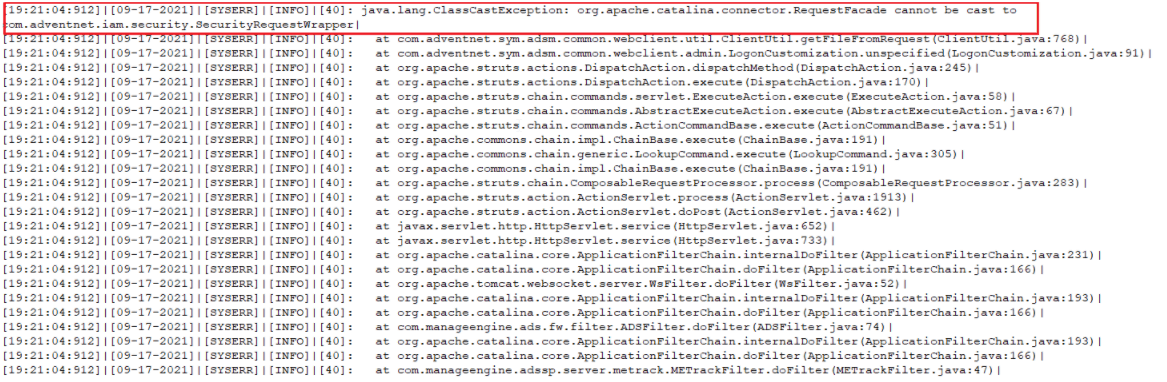
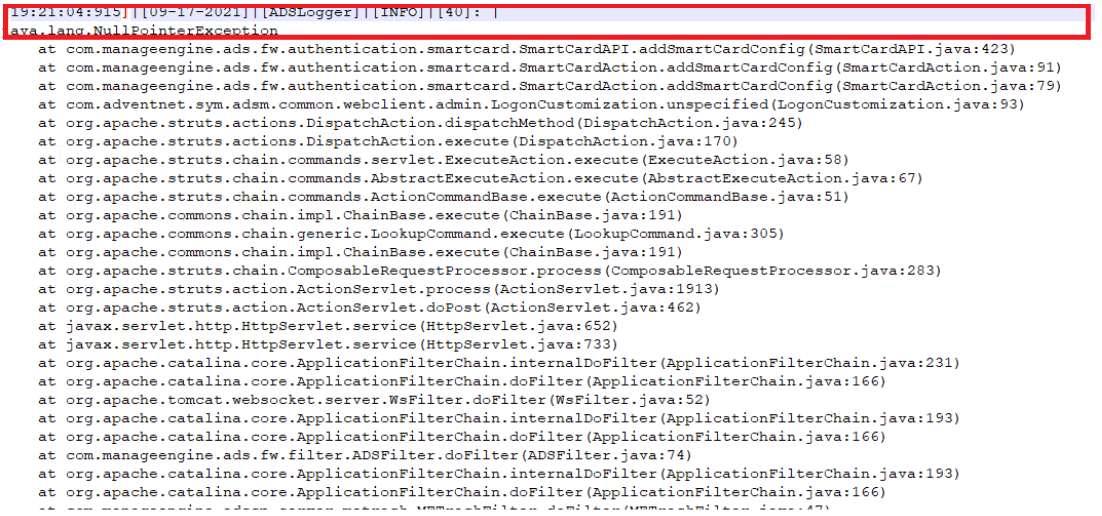
An authentication bypass vulnerability (CVE-2021-40539) that affects the REST API URLs that could result in remote code execution (RCE) was identified in ADSelfService Plus, ManageEngine's self-service password management, and single sign-on solution. ManageEngine rates this vulnerability affecting ADSelfService Plus builds 6113 and below as critical, and has noticed indications of exploitation by cyber actors. Instances of this vulnerability were first detected in August 2021, when malicious actors tried gaining access to ADSelfService Plus by exploiting CVE-2021-40539. This vulnerability allows malicious cyber actors to place webshells and conduct post-exploitation activities such as compromising administrator credentials, conducting lateral movement, and exfiltrating registry hives and Active Directory files. This was addressed by releasing the fix in build 6114.
In a security advisory ManageEngine released consecutively, it strongly urges users and administrators to update to ADSelfService Plus build 6114 or above. Referencing ManageEngine's advisory, the Federal Bureau of Investigation (FBI), United States Coast Guard Cyber Command (CGCYBER), and the Cybersecurity Infrastructure and Security Agency (CISA) in their join advisory have also recommended users to update to ADSelfService Plus build 6114 or above.
We have partnered with Veracode, an independent application security company, to conduct manual pen tests on ADSelfService Plus so that we get a third-person perspective on the security footing of the solution.