Summarize
Introduction
With the advent of AI in ITSM, incident management as a core ITSM practice evolves even today. The primary objective of incident management is to restore regular services as quickly as possible while minimizing the impact on business productivity. But how an incident ticket is logged, and how it progresses through its life cycle from logging to closure, has evolved with technology.
Implementing effective incident management practices has become increasingly critical as organizations depend more heavily on IT infrastructure to support their core business processes. This guide explores incident management exhaustively, keeping the ITIL® recommendations in mind.
Fundamental concepts and definitions
Building a successful incident management process begins with establishing a clear definition of an incident for your organization and understanding the strategic importance of how you evaluate incident management.
What is an IT incident?
ITIL defines an IT incident as "any unplanned disruption or reduction in the quality of an IT service that compromises business continuity."" Incidents can range from isolated user issues, such as individual printer failures, to enterprise-wide system failures that affect critical business operations across multiple departments. The scope and complexity of incidents vary significantly across organizations, making proper classification essential.
How an incident is classified:
| Incident type | Impact scope | Business effect | Response priority |
|---|---|---|---|
| Minor incident | Single user/department | Limited business impact | Standard SLA |
| Major incident | Business-critical services | Organization-wide disruption | High priority |
| Critical incident | Complete service outage | Severe business disruption | Emergency protocols |
Why is incident management important?
A systematic approach to incident management transforms reactive, chaotic incident firefighting into transparent, efficient incident resolutions that maintain customer confidence. This leads to:
- Decreased downtimes
- Improved employee experience
- Enhanced service transparency across the enterprise
- Systematic documentation of resolutions
- Reduced mean time to resolution
- Prevention of major business outages
What are the risks of inadequate incident management?
- Lack of visibility into ticket status and resolution progress, creating frustration among employees
- Failing to document knowledge results in repeated resolution efforts for known errors
- Extended service disruptions, directly affecting business revenue
- Increased likelihood of escalating incidents into major outages
The incident life cycle
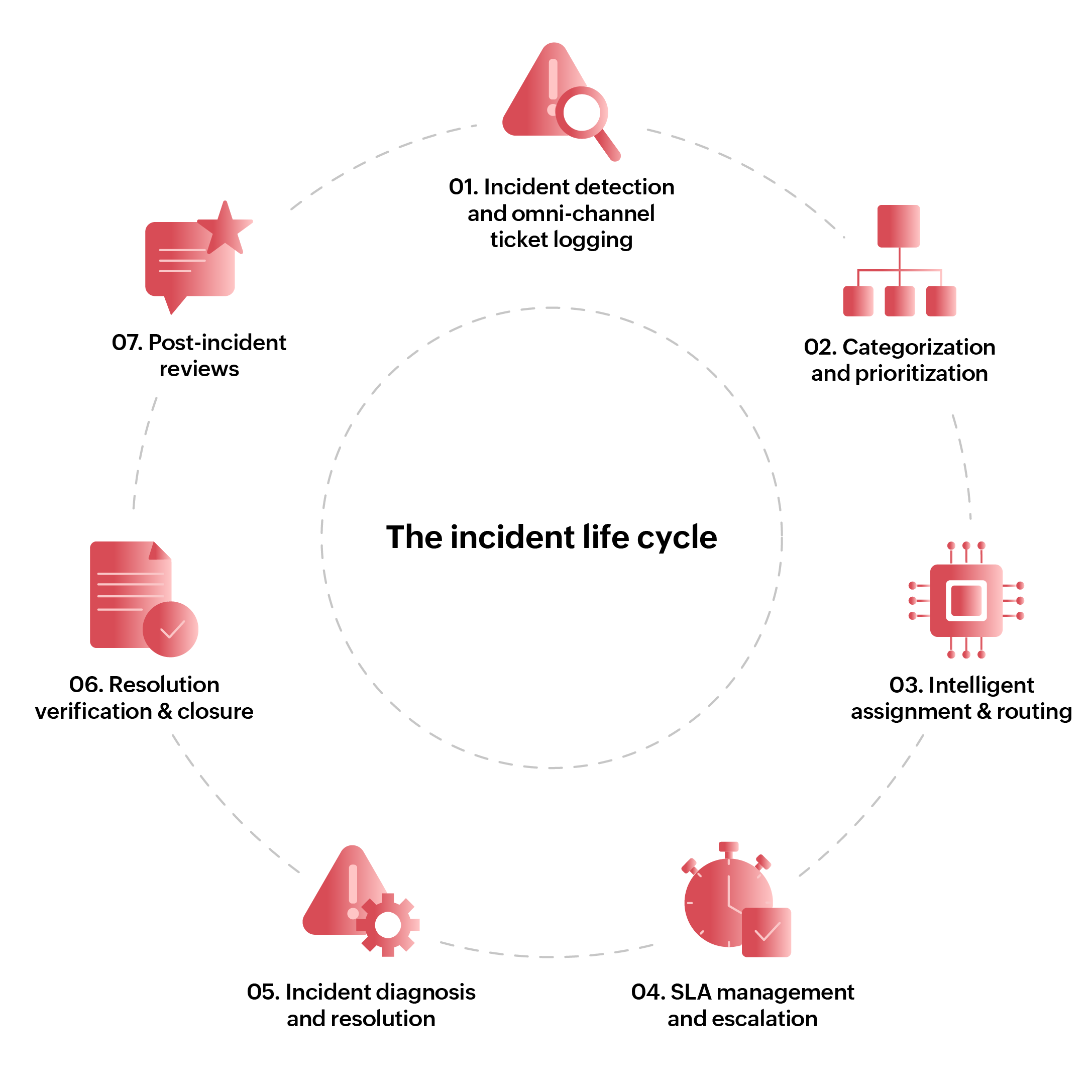
The incident life cycle tracks an incident from its logging to the confirmation of user satisfaction with the resolution. The life cycle encompasses ticket logging, triage, assignment, response, diagnosis, resolution, and closure post user approval.
This approach comprises seven distinct phases. Let's go through them in order.
Phase 1: Incident detection and omni-channel ticket logging
The incident life cycle begins with detection, which is facilitated through multiple channels that organizations must monitor and integrate effectively. Having multiple channels improves the user experience when logging tickets, allowing them to use the channel most convenient to them and log tickets in a timely manner.
Channels your ITSM should log tickets from:
- Automated monitoring systems and observability tools that provide proactive alerts
- User-initiated reports that include help desk tickets, emails, and chat interactions
- Internal collaboration tools, such as Slack, Microsoft Teams, and Cliq
Mature ITSM platforms provide comprehensive omni-channel ticketing capabilities that unify incident creation across these channels into single, coherent ticket workflows—rather than having separate people monitor each channel. This unified approach ensures consistent service delivery regardless of the channel that tickets are logged from.
Modern service desk systems also streamline the logging process by providing a customizable self-service portal with a service catalog. This catalog has a set of request and ticket templates as well as a unified view of all pending, on hold, and completed tickets, ensuring a cohesive collection of data.
Effective ticket logging forms the foundation of successful incident resolution by capturing comprehensive information. This practice also reduces resolution delays and provides essential context for your technicians.
ITSM integration with full-stack observability tools
Modern ITSM platforms integrate with full-stack observability tools to provide complete visibility across applications, infrastructure, and network layers. This enables automatic correlation of KPIs, application logs, and system telemetry data with reported incidents, revealing underlying patterns. These tools can automatically detect relationships between seemingly unrelated incidents, identify recurring patterns, and provide context-rich information that accelerates incident diagnoses and resolution.
| Information category | Required details | Business purpose |
|---|---|---|
| Ticket tracking | Unique ticket ID, timestamp, source channel, category, and priority | Tracking and audit compliance |
| Requester information | User details, contact information, department | Communication and escalation |
| Technical details | Affected systems, error messages, symptoms | Root cause analysis (RCA) |
| Business context | Service impact, affected processes, urgency drivers | Prioritization and resource allocation |
Major incident management
While these fields are pertinent to how we handle incidents, we also need to have response plans for major incidents, which would also be logged through the same channels. A major incident is defined as a high-impact, high-urgency incident that significantly affects business operations, multiple users, or critical services. These incidents require immediate attention and escalated response procedures beyond standard incident management protocols.
Once declared, an incident response team should be established comprising the Major Incident Manager, technicians, business representatives, and a communications coordinator. The team must ensure regular status updates to relevant stakeholders, immediate containment, root cause analysis (RCA), and service restoration, following which a Post-Incident Review (PIR) has to be scheduled.
Phase 2: Categorization and prioritization
Once incidents are logged, every ticket must be categorized and prioritized, which is known as triaging. This ensures that the most impactful incidents receive timely attention.
Advanced platforms incorporate AI throughout the incident triaging and assignment processes, automating:
- Analysis of incident tickets to predict appropriate classifications
- Assessment of priority levels
- Identification of configuration items (CIs)
- Determination of the right categories and subcategories
This significantly reduces manual triaging efforts while improving consistency and accuracy in incident processing. These ML-based algorithms enable continuous improvement of prediction accuracy by learning from resolution outcomes and technician feedback. Most organizations arrange incidents into categories and subcategories based on the business impact of the associated service or the asset affected by the incident.
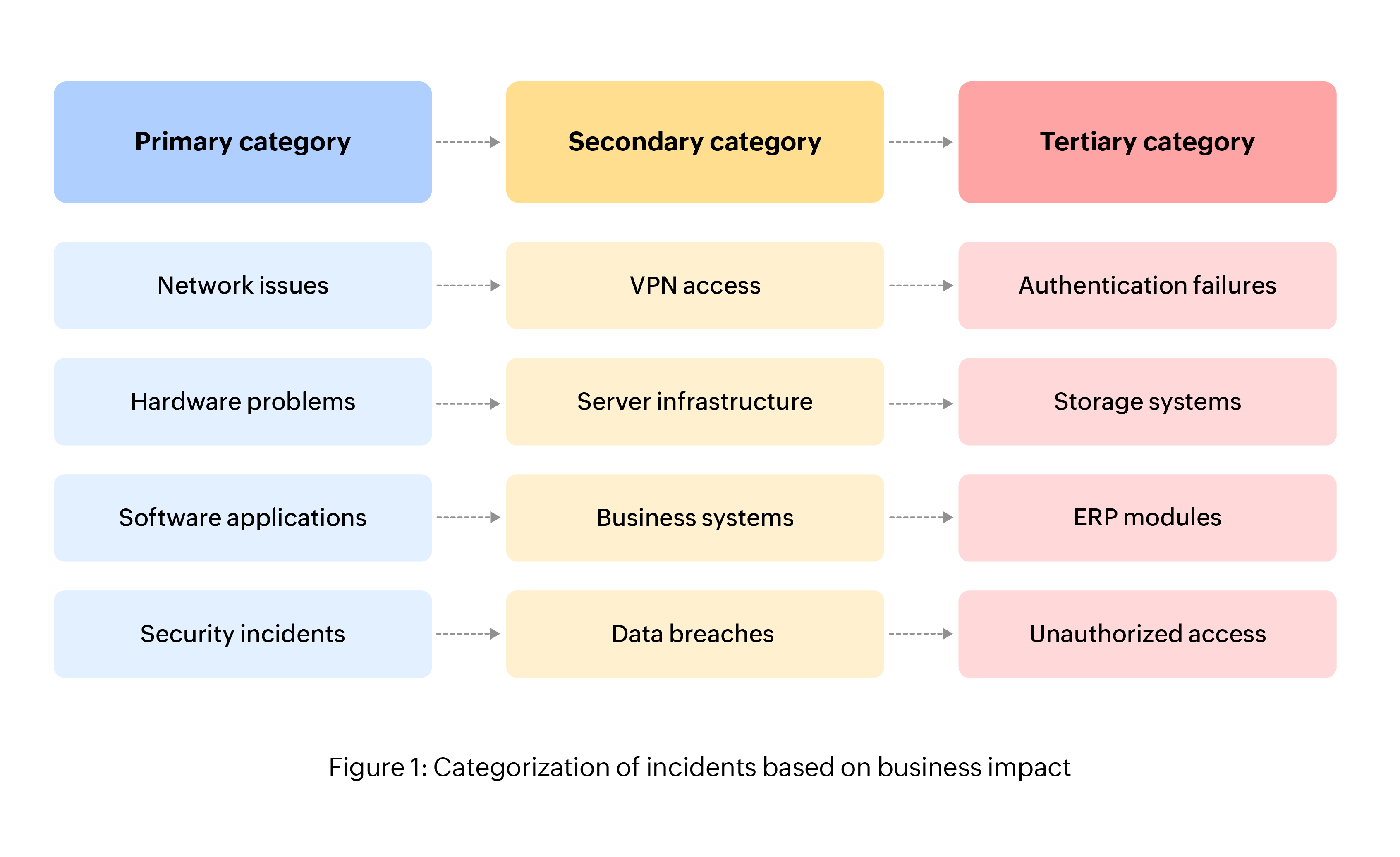
Effective categorization ensures tickets reach technicians with the right expertise. Determining priority requires a clear understanding of both impact and urgency. Impact is the degree of business disruption and users affected, while urgency indicates the time sensitivity and business risk associated with delayed resolution. The table below is called a priority matrix.
| Impact/Urgency | Low urgency | Medium urgency | High urgency |
|---|---|---|---|
| Low impact | P4: Minor | P3: Standard | P2: High |
| Medium impact | P3: Standard | P2: High | P1: Critical |
| High impact | P2: High | P1: Critical | P1: Emergency |
To learn more about the ITIL priority matrix, click here.
Phase 3: Intelligent assignment and routing
Next, incidents require assignment to the right technician. To optimize routing, modern ITSM platforms leverage AI and ML algorithms, such as:
- Natural language processing: Automated analysis of incident descriptions and keywords
- Sentiment analysis: Automated detection of user frustration levels to escalate it to the right technician
- Skill-based routing: Matching incidents to technicians with relevant expertise and availability
- Load balancing: Ensures equitable distribution of workloads
Commonly used routing algorithms:
| Method | Use case | Advantages | Considerations |
|---|---|---|---|
| Round-Robin | Standard incidents | Equal workload distribution | May not account for incident complexity |
| Skill-Based | Specialized issues | Optimal expertise matching | Requires comprehensive skill mapping |
| Load Balancing | High-volume environments | Prevents technician overload | Complex configuration requirements |
Phase 4: SLA management and escalation
Service level agreements (SLAs) define acceptable timeframes for incident response and resolution, establishing clear expectations for all stakeholders. The lack of SLA management can damage customer relationships and business operations. SLAs need to be tiered and are not a one-size-fits-all approach. This is to ensure that you have different timeframes of service delivery offered for different priorities, such as the one shown below:
| SLA metric | P1: Critical | P2: High | P3: Standard | P4: Minor |
|---|---|---|---|---|
| Response time | 15 minutes | 2 hours | 8 hours | 24 hours |
| Resolution time | 4 hours | 24 hours | 72 hours | 120 hours |
| Update frequency | Every 30 minutes | Every 4 hours | Daily | As needed |
Escalation mechanisms ensure incidents receive appropriate attention when SLAs are breached or standard resolution processes prove insufficient.
Types of escalations and their intent:
- Functional escalation transfers incidents to specialist teams
- Temporal escalation automatically escalates to prevent SLA breach
- Impact escalation elevates incidents when business impact expands beyond initial assessment
Modern platforms provide automated alarm correlation, automation, and predictive analytics to prevent SLA breaches through proactive escalation. Learn more about SLAs here.
Phase 5: Incident diagnosis and resolution
The assigned technician begins diagnosis to identify a work-around or a solution to the incident. This phase requires both technical expertise and structured problem-solving approaches, ensuring a thorough investigation while restoring services.
ITIL incident management practices emphasize proper communication and documentation throughout the incident life cycle. This gives all the necessary stakeholders the right updates on the ticket, and technicians the knowledge they need to resolve similar occurrences if they arise.
A typical incident diagnosis involves:
- Initial assessment: Gathering additional context and verifying symptoms
- Environmental analysis: Reviewing system logs, configurations, and recent changes
- Identification of the cause behind the incident: Applying structured troubleshooting approaches
- Solution development: Selecting work-arounds or permanent fixes
- Testing and validation: Verifying resolution effectiveness before implementation
Phase 6: Resolution verification and closure
Proper incident closure requires verifying whether solutions address underlying issues, ensure user satisfaction, and restore normal service operations. Modern ITSM platforms like ServiceDesk Plus allow you to also setup no-code automations to mandate ticket data while closing an incident ticket, ensuring that data is documented for audits and compliance.
Some of the data that can be mandated through ticket closure automation:
- User confirmation of service restoration and satisfaction with resolution
- Solution updated in knowledge base for future reference
- RCA completed where applicable
- Satisfaction survey
Phase 7: Post-incident reviews
Post-incident reviews (PIRs) transform incidents into organizational learning that improve future incident response. ITIL recommends effective stakeholder communication and comprehensive documentation throughout the incident life cycle. PIRs contribute heavily to this documentation.
How should a PIR be developed?
- Timeline: Conduct reviews within 48 hours of incident closure while details remain fresh.
- Participants: Include all relevant stakeholders and decision-makers who contributed to the resolution.
- Culture: Maintain a blameless approach focused on system improvement rather than individual accountability.
- Documentation: Produce a comprehensive analysis with specific, actionable recommendations.
The structure of a typical PIR:
| Section | Content requirements | Deliverables |
|---|---|---|
| Executive summary | High-level overview and business impact assessment | Management briefing document |
| Detailed timeline | Chronological event sequence with specific timestamps | Process improvement insights |
| Incident analysis | Systematic investigation using proven methodologies | Preventive action plans |
| Recommendations | Specific, measurable improvement actions | Implementation roadmap |
When more than one incident with similar characteristics are flagged, then this is looked into as a potential problem with one root cause behind all of these incidents. If verified to be a problem, then a problem is then created on behalf of the incident, and a RCA occurs. This analysis usually takes time due to further investigation, finding a permanent solution for the incident, and recording it as a known error.
Organizational roles and responsibilities
Successful incident management requires clearly defined roles that ensure coordinated and efficient response across all phases of the incident life cycle. Each role cumulatively contributes towards service restoration.
Incident management hierarchy
End user
The end user serves as both the initial reporter of incidents and the final validator of resolutions. Their active participation throughout the incident life cycle directly impacts resolution speed and accuracy.
Primary responsibilities include accurate incident reporting with comprehensive details, timely response to technician requests for additional information, resolution acknowledgment and feedback, and adherence to established communication channels. Effective user engagement reduces the time needed to diagnose an issue and ensures solutions meet actual business needs.
Tier 1 service desk (First-line support)
Tier 1 support represents the first point of contact for service requesters and serves as the foundation of effective incident management operations. They handle initial incident processing and resolution of common issues while maintaining communication with users throughout the process.
Core functions include initial incident logging, categorization, and priority using established criteria, resolution of common issues using documented procedures and solution articles, serving as a communication hub that facilitates escalation management for complex incidents.
Tier 2 and 3 service desk (Advanced support)
Advanced support tiers provide specialized technical capabilities for complex incidents that exceed first-line resolution capabilities. These team members possess deeper technical knowledge and broader system access required for comprehensive diagnosis and resolution.
Specialized capabilities include:
- In-depth technical diagnosis and complex problem resolution
- Knowledge base maintenance and documentation
- Identification of recurring patterns requiring problem management
- Mentoring and knowledge transfer to Tier 1 staff
Incident manager
The incident manager provides strategic oversight for the entire incident management process while serving as the primary coordinator for major incident response. An incident manager's responsibilities include monitoring incident response, major incident coordination, stakeholder communication, and decision-making during escalations.
Read our e-book on 5 ways ServiceDesk Plus
makes an incident manager's life easier.
Here's your free copy
If your download doesn't start automatically, please click here.
Modern best practices and innovation
Modern incident management practices leverage advanced technologies, such as AI, automations, and predictive analytics, to build upon established ITIL foundations. This leads to significant improvements in service quality, user satisfaction, and efficiency while reducing downtime costs.
Implementing powerful automations
Automation represents the foundation of efficient service desk operations, enabling organizations to handle increasing incident volumes while maintaining and improving service quality.
| Automation level | Capabilities | Implementation focus | Business value |
|---|---|---|---|
| Basic rules | Data validation, auto-assignment | Immediate deployment wins | Reduced manual effort |
| Workflow automation | Process standardization, routing | Consistency and compliance | Improved service quality |
| Advanced scripting | Custom integrations, external systems | Complex scenario orchestration | Enhanced productivity |
Organizations should first develop condition-based business rules through automated ticket assignment, then implement visual workflows that standardize service delivery processes. Finally, they should develop custom triggers for external system connectivity and complex scenario orchestration that extends platform capabilities beyond standard functionality.
Deploy GenAI features to reduce bureaucratic overheads
Modern AI systems analyze incident characteristics and provide real-time assistance through contextual recommendations to knowledge articles and resolutions. Content generation capabilities include automated ticket summaries that capture essential information efficiently, knowledge base article creation that documents solutions systematically, and communication enhancement through contextual email response drafting that improves user interactions.
Deploy conversational AI as your first line of incident response
Advanced chatbots provide 24/7 availability without staffing constraints, enabling service coverage across time zones and business hours. These systems handle routine task automation, such as password resets, software installations, and system status checks. Intelligent escalation capabilities ensure seamless handoffs to human agents when automated resolution proves insufficient.
Take advantage of predictive intelligence where human intelligence fails
Advanced ITSM platforms like ServiceDesk Plus deploy predictive models like Zia, trained on historical data which are capable of identifying incident patterns and trends to identify potential problems. These models can predict change risks while scheduling changes, assign categories and subcategories while triaging tickets, route tickets to the right technician, and identify incident patterns to predict potential problems.
Measurable benefits
The top three use cases for organizations implementing AI augmentation were process optimization, risk advisory, and knowledge discovery according to a recent survey conducted by ManageEngine. Other use cases included increased first-contact resolution rates through better resource recommendations, enhanced technician productivity, and job satisfaction through elimination of routine tasks.
Implement data-driven decision-making
Comprehensive analytics enable informed decision-making based on empirical evidence rather than anecdotal information. Real-time dashboards provide live visibility into service desk metrics, while custom reporting delivers tailored analytics for specific business requirements.
Performance measurement and KPIs
Effective performance measurement requires systematic tracking of metrics while providing actionable insights for continuous improvement. KPIs must balance operational efficiency measures with user satisfaction and business impact assessments. Here are some commonly used KPIs to measure and analyze to get a picture of your service desk's performance.
Important KPIs:
| KPI | Definition | Strategic importance |
|---|---|---|
| First Contact Resolution (FCR) | Percentage resolved during the first interaction without subsequent follow ups | Cost reduction, user satisfaction |
| Average Resolution Time (ART) | Mean time from logging to closure | Service efficiency, business continuity |
| Average First Response Time (AFRT) | Time to initial technician response | User experience, expectation management |
| Mean Time to Detect (MTTD) | Time from incident occurrence to detection | Risk mitigation, proactive management |
| SLA compliance rate | Percentage meeting agreed service levels | Service reliability and customer trust |
| Customer Satisfaction (CSAT) | User satisfaction with service quality | Relationship quality and service value |
Glossary and definitions
- Agentic AI: An emerging AI technology category that enables autonomous task completion without continuous human supervision.
- Configuration Management Database (CMDB): Centralized repositories of IT infrastructure information and relationships.
- Conversational AI systems: Systems that enable natural language interactions to reduce ITSM support workload by offloading first response to AI.
- IT Asset Management (ITAM): Comprehensive life cycle management of IT assets from initial procurement to final disposal, supporting cost optimization and regulatory compliance requirements.
- Key Performance Indicators (KPIs): Measured service desk objectives that enable data-driven decision-making and continuous improvement initiatives.
- Post-Incident Reviews (PIRs): Structured analysis meetings following major incident resolution to document lessons learned in the knowledge base.
- Predictive analytics: Statistical algorithms and ML leveraged to forecast future outcomes based on historical and real-time data patterns.
- Service Level Agreements (SLAs): Written contracts between a service provider and a customer that describe the services to be provided, the standards of performance for those services, and how the service provider will be held accountable for meeting those standards.
Conclusion
Modern incident management combine proven ITIL methodologies with innovative technologies and data-driven insights. This drives significant improvements in service quality, user satisfaction, and business continuity while reducing downtime costs. The integration of AI, predictive analytics, and advanced automation capabilities, alongside the frameworks, and best practices outlined in this guide can be valuable for organizations at any maturity level seeking to improve their incident management capabilities.
