Help Center
Quick Start
- Overview
- System requirements
- Minimum privileges required
- Default port configuration
- Installing DataSecurity Plus
- Uninstalling DataSecurity Plus
- Starting DataSecurity Plus
- Launching DataSecurity Plus
- Configuring your solution
- Licensing details
- Applying a license
File Auditing
- About File Auditing
- Domain configuration
- File server configuration
- Failover cluster configuration
- NetApp server configuration
- Nutanix server configuration
- Workgroup configuration
Setting up File Audit
Dashboard
Reports
Alerts
Configuration
Storage Configuration
File Analysis
- About File Analysis
- Domain configuration
- File server configuration
- Workgroup configuration
- SMB File Server Configuration
- On-Demand Reports
Setting up File Analysis
Dashboard
Reports
Alerts
Configuration
Data Risk Assessment
- About Data risk assessment
Setting up Data risk assessment
Dashboard
Reports
Ownership analysis
Configuration
Endpoint DLP
- About Endpoint DLP
Setting up Endpoint DLP
Reports
Alerts
Prevention policies
Configuration
Cloud Protection
- About Cloud Protection
- Gateway Server Installation Steps
- Gateway Configuration in Endpoint
- Gateway Cluster Configuration
- Gateway Server Management
- Certificate Authority Configuration
- Two-way SSL configuration
- Manage Certificate Trust Store
- Threat Analytics Database
- Manage Banned Applications
- Manage Authorized Applications
- Regenerating gateway server access key
- Updating gateway server
- Gateway Server Failover
- Load Balancer Configuration
- Global Insight
- Application Insight
- User Insight
- Shadow Application Insight
- Banned Application Insight
- Cloud App Discovery
- File Upload & Download Reports
- Control Policy reports
- General Reports
- Application Insights
- Shadow Domain Insights
- Banned Domain Insights
Setting up Cloud Protection
Dashboard
Reports
Control Policies
Storage Configuration
Administrative settings
- Technician configuration
- Notification filters
- Manage agent
- Agent settings
- SIEM integration
- Business hours configuration
- Two-factor authentication
- Workgroup configuration
- Security policy
Email configuration
General settings
- Connection
- Personalize
- DataSecurity Plus Server
- Privacy Settings
- Disk utilization
- Schedule Retention Policy
Release notes
2026
2025
2024
2023
2022
2021
2020
2019
2018
2017
2016
2015
Troubleshooting
- HTTP communication failure
- Dormant DataEngine
- Secure Gateway server failure
- RPC communication failure
- Cloud Protection Gateway server failure
- Known issues and limitations
- Known errors and solutions
- Report discrepancy in File Analysis
Guides
- Agent document
- How to Migrate/Move DataSecurity Plus
- How to apply SSL certificate
- How to automate DataSecurity Plus database backup
- How to set alerts in DataSecurity Plus
- How to secure your DataSecurity Plus installation
Gateway cluster configuration
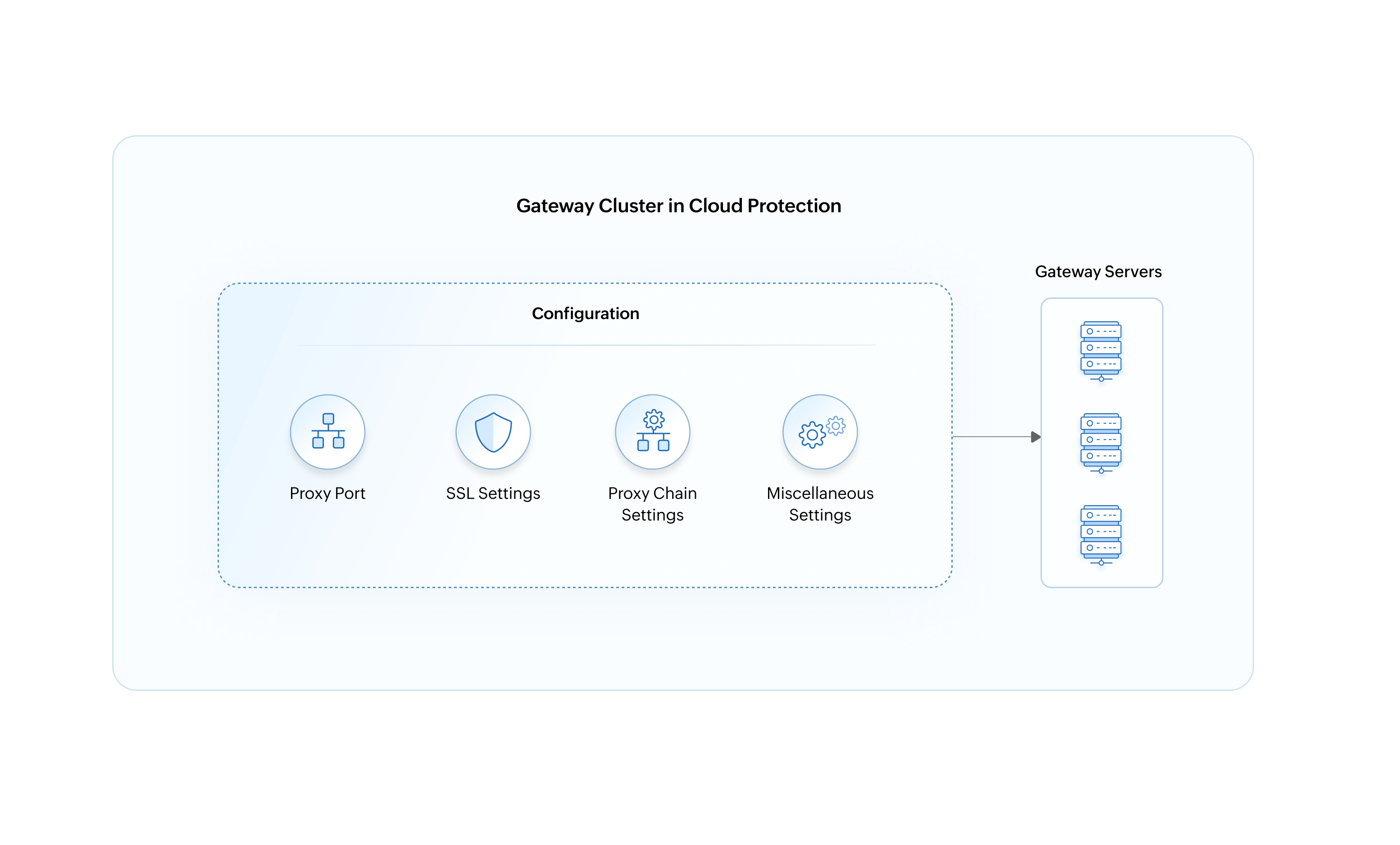
Gateway cluster: Cloud protection enables the clustering of gateway servers that share similar configurations using the gateway cluster. It simplifies the management of multiple gateway servers, as users only need to define the configurations once.
Gateway server: A gateway server monitors web traffic to provide actionable insights into web applications used and helps enforce data protection policies like blocking banned applications.
The following is a rundown of how a gateway cluster is configured, managed, and mapped to gateway servers.
Configuring a gateway cluster
To configure a gateway cluster, follow the below steps:
- Log in to the DataSecurity Plus web console.
- Select Cloud Protection from the application drop-down.
- Go to Configuration > Server > Gateway Configuration.
- In the Gateway Configuration page, click Add Cluster in the top-right corner.
- In the Cluster Configuration page, enter the cluster name and port number.
- Click Advanced Settings, and do the following:
- Click the SSL settings drop-down and configure SSL settings to execute deep packet inspection.
- DPI Mode: Depending upon your business requirement, you can select a mode from the drop-down. For further details refer to the below list.
- CA Certificate: Select a CA certificate once deep packet inspection is enabled. It can either be from the drop-down or you can customize a CA certificate by clicking the Create new CA Certificate link next to the CA Certificate drop-down.
Note: The selected CA certificate must be installed in the trusted root certification authorities of the client machines.
- TLS Versions: You can select either one or more of the TLS versions as needed for your environment. SSL versions preceding TLS V1.0 are not supported.
- Configure proxy settings in the Proxy Chain drop-down if the existing Cloud Protection Gateway Server needs to connect to another proxy server for connecting to the internet. To configure proxy settings, select one of the options from the Proxy Chain drop-down as follows:
- Click the Miscellaneous drop-down to specify the minimum disk space allotted for auditing.
- Click Save.
| Mode | Purpose |
| Enable | Enabling the DPI mode helps you monitor and have granular control over your organization's HTTP/HTTPS web traffic. |
| Mixed | Inspect only specific cloud applications. i.e., all cloud applications that are a part of the File Upload Reports are configured in Mixed Mode by default. |
| Disable | Since deep packet inspection is not performed, only HTTP traffic can be audited, i.e., only domain-based control is possible, and granular control cannot be done. |
| Proxy settings | Required details | Purpose |
| No proxy | -- | Select No proxy if you want to connect to the internet directly via the gateway server. |
| Auto proxy | -- | Select Auto proxy if you want to configure the proxy server automatically by detecting the predefined proxy settings in your environment. |
| PAC proxy | PAC script location | Select PAC proxy if you want to route the web traffic based on a certain predefined condition given within the script file. Specify the PAC script location while selecting PAC proxy to successfully execute it. For more information on PAC proxy, click here. |
| IP proxy | IP address with port | Select IP proxy if you want to configure a proxy server manually in your environment by specifying its IP address with its port number. |
PAC script location: The URL of the Proxy-Auto-Configuration (PAC) file that contains scripts on how to handle web traffic requests.
Editing a gateway cluster
To edit a gateway cluster, follow the below steps:
- Log in to the DataSecurity Plus web console.
- Select Cloud Protection from the application drop-down.
- Go to Configuration > Server > Gateway Configuration.
- In the Gateway Configuration page, under the Gateway Clusters panel, click Edit in the target cluster.
- Modify the setting as per your requirement and click Update.
Deleting a gateway cluster
To delete a gateway cluster, follow the steps below:
- Log in to the DataSecurity Plus web console.
- Select Cloud Protection from the application drop-down.
- Go to Configuration > Server > Gateway Configuration.
- In the Gateway Configuration page, under the Gateway Clusters panel, click Delete within the target cluster, and click OK.
Note: A gateway cluster cannot be deleted if it has gateway servers mapped to it. To delete them, either move the mapped gateway servers to a different gateway cluster or remove them from the target gateway cluster.
Gateway cluster insights
The gateway cluster insights includes details on:
- Gateway cluster properties: It comprises the properties configured for the gateway cluster, such as deep packet inspection, port number, proxy configuration status, etc.
- Gateway cluster health: It lists the sync status of the sanctioned and banned applications, disk space, and more.
- Gateway servers: It displays all the gateway servers configured within the gateway cluster and their statuses.
Regenerating an access key in the gateway cluster
An access key is used to establish a connection between the endpoints and the gateway server. The access key is common for all the gateway servers irrespective of which gateway cluster it belongs to. When the access key is regenerated, all the configured gateway servers should be updated with their respective new access key. Refer to the steps listed here for generating a new access key.
