Forensics are an integral part of discovering how a cybercrime took place. As a SOC manager, you and your team have to rely on digital forensic clues (IP addresses, file hashes, etc.) to figure out if a cybercrime has taken place, and how an attacker went about it. In cybersecurity, these forensic clues or artifacts are called IoCs. These clues serve as red flags that signal a data breach or intrusive activity on the network.
While threat actors use unusual attack patterns as they become savvier, and attempt to bypass IoCs, you can still refer to the well-established list of IoCs in this blog to make threat detection easier. You'll also learn of the relevant reports within ManageEngine's SIEM solution Log360 (available both on-prem and in the cloud) that help you identify these common IoCs. This blog also helps you identify and manage the new IoCs that you might encounter.
A genuine authentication failure like a bad password or OTP entry is going to be wrong only a limited number of times. However, when there's a threat actor on your network, they're often using tools that tryout different passwords to see if an account can be compromised. If your logs show numerous authentication attempts happening in succession, you need to take a look, as it could be an attacker using a dictionary attack. Other anomalous authentication events like logins from a strange geographical location or multiple login failures to privileged accounts are all indicators of compromise your SOC team should take seriously. Figure 1 and Figure 2 show authentication related reports in Log360.
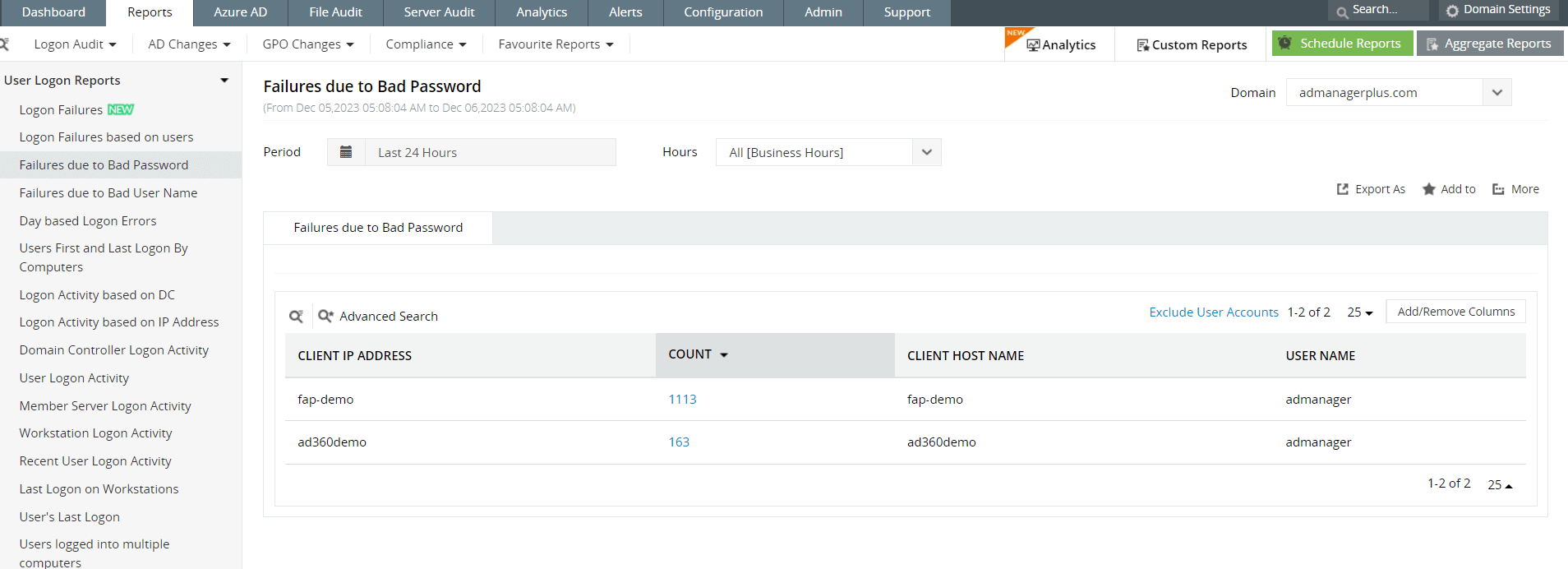 Figure 1: Log360 offers several built-in reports that show logon events, including specific reports on failed logons due to a bad username or password.
Figure 1: Log360 offers several built-in reports that show logon events, including specific reports on failed logons due to a bad username or password.
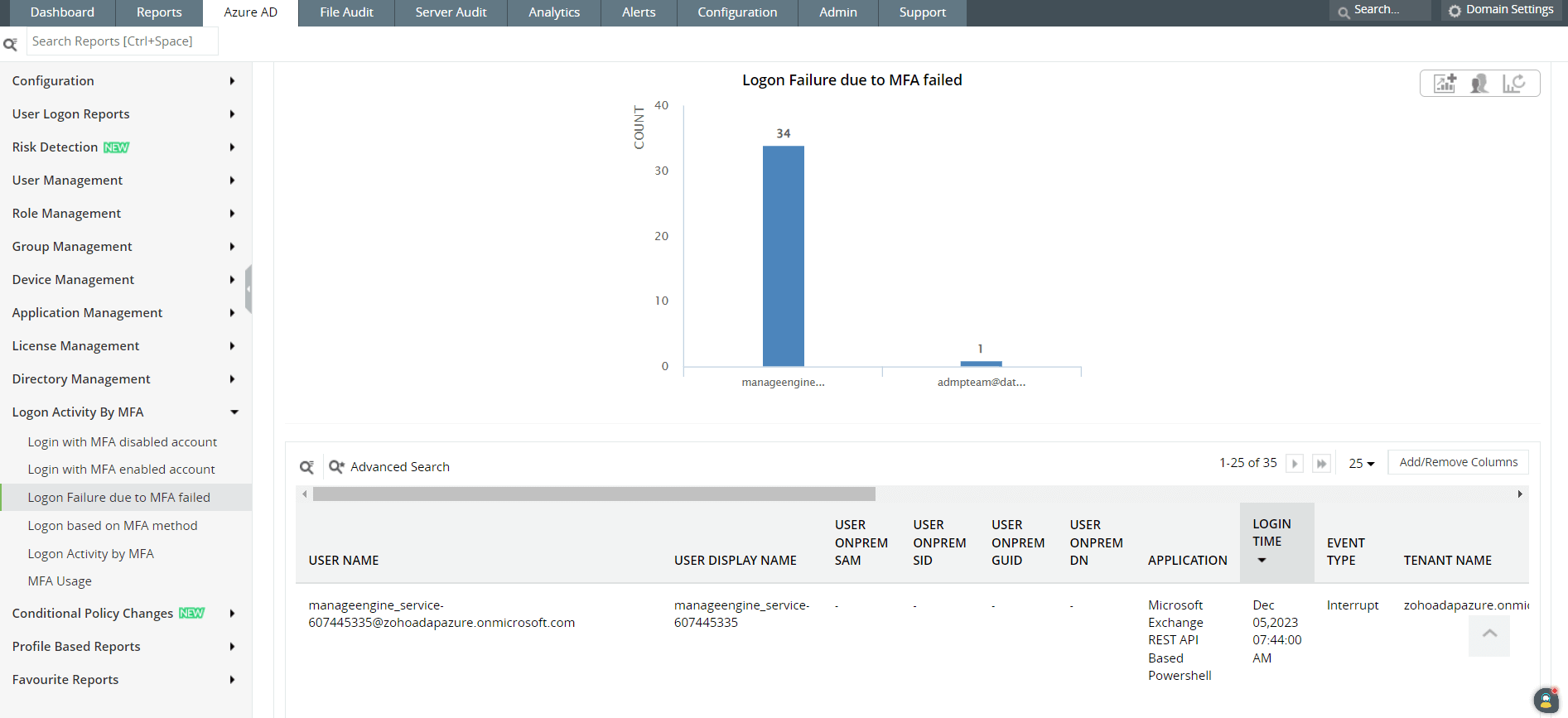 Figure 2: An admin or security manager can also view logon activity based on MFA.
Figure 2: An admin or security manager can also view logon activity based on MFA.
Databases are attractive targets for attackers since that's where organizations store sensitive material. If you see a significant rise in database reads, file downloads, or modifications to the database content that aren't consistent with your usual baseline, your SOC team should look into it. As a SOC manager, you may have to look into such activity personally, especially if it's happening on a critical server, to confirm that your databases are secure. Figure 3 shows server audit reports in Log360.
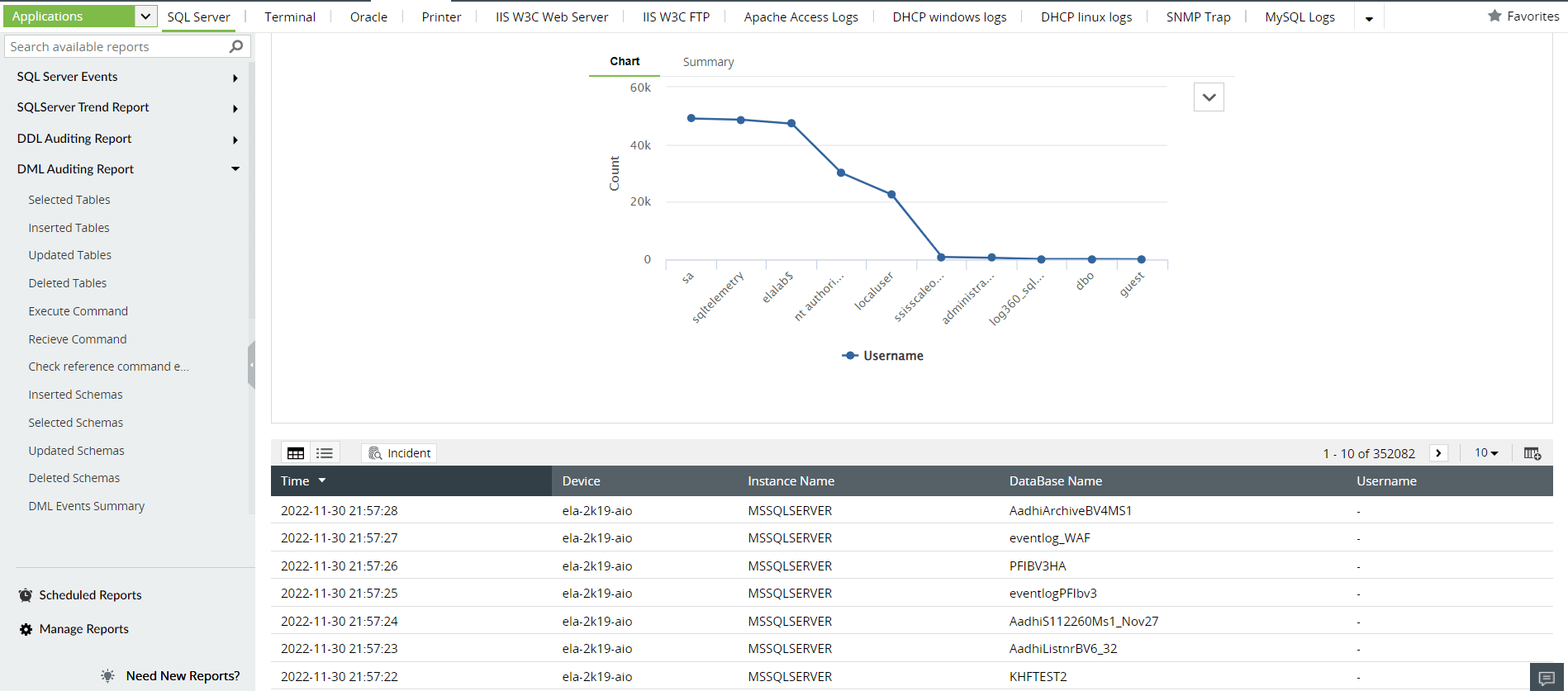 Figure 3: Log360 has several built-in reports that show server activity including auditing of data definition language (DDL) and data manipulation language (DML).
Figure 3: Log360 has several built-in reports that show server activity including auditing of data definition language (DDL) and data manipulation language (DML).
A SOC team equipped with the right tools will find that outbound traffic can reveal a lot about what an attacker is doing in the network. Anomalies in your outbound traffic that should be taken seriously include: communication from workstations using unusual protocols, large amount of data leaving your network, and signs of communication with known malicious IPs or with IPs from new geographical locations. These indicators will let your SOC team know if there is communication with an attacker's C&C servers, or if data is being transferred to suspicious recipients. Figure 4 shows how a well-organized Log360 dashboard gives you an overview of network activity.
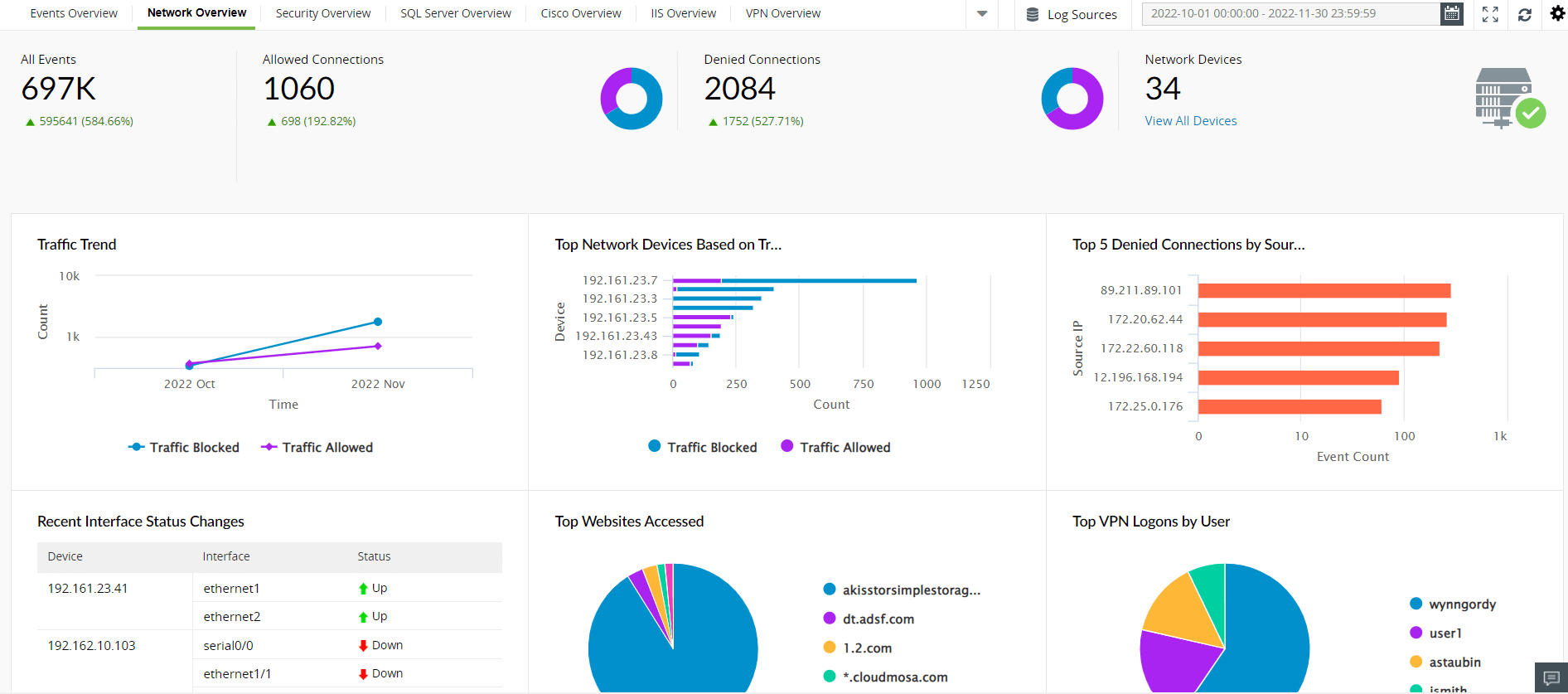 Figure 4: A SOC manager can have an overview of the network and monitor traffic-related data.
Figure 4: A SOC manager can have an overview of the network and monitor traffic-related data.
Since cryptocurrency became a lucrative venture, attackers have devised devious ways of utilizing an organization's CPU resources to mine cryptocurrency. Physical indicators of systems overheating, and other indicators of performance issues from your performance monitoring tools might be a signal that your network is under attack.
Numerous attempts to access a particular file could be an important signal, because an attacker may be using various ways to gain access to the file. Following this signal with relevant metadata can make this an important indicator of compromise that you dont want to miss out on. Figures 5 and 6 show file monitoring reports in Log360.
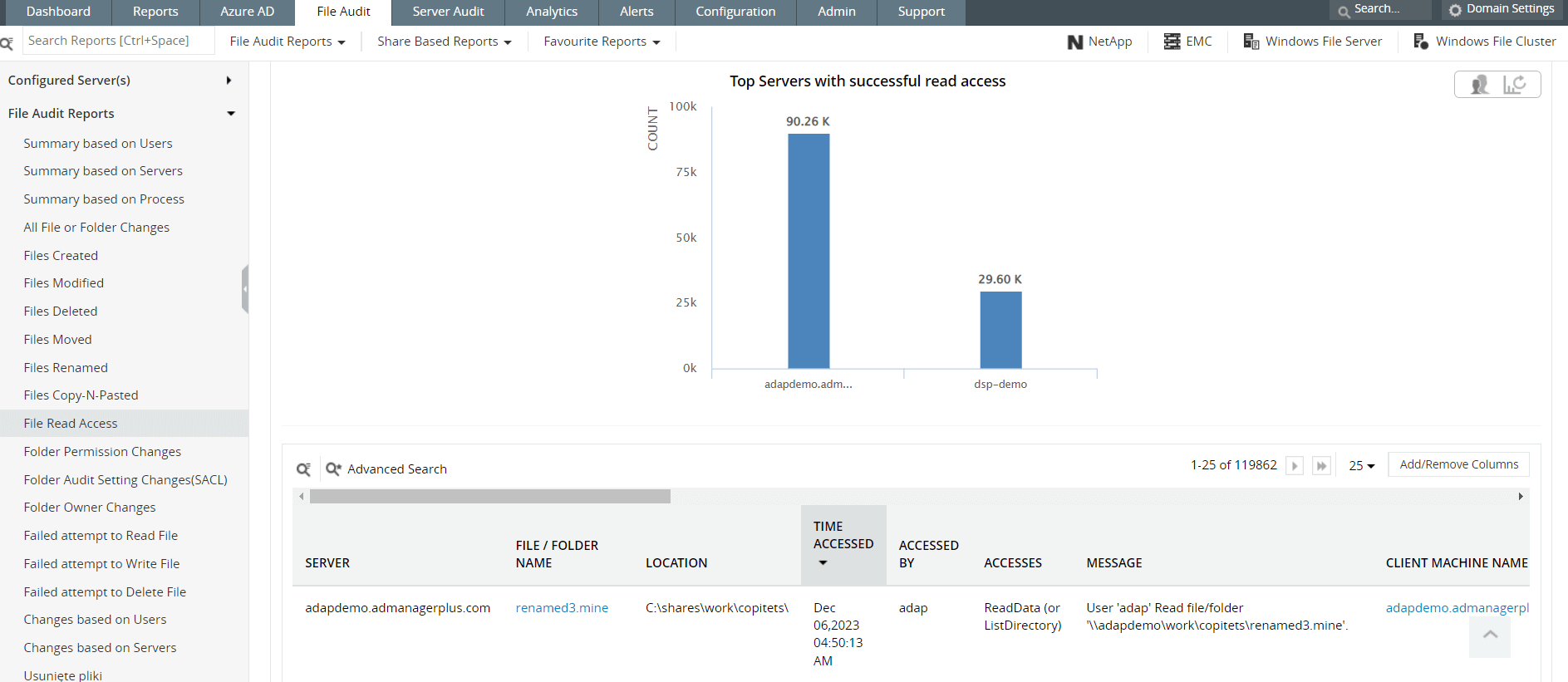 Figure 5: Log360 offers several reports on file audits, including file creations, deletions, modifications, and read accesses.
Figure 5: Log360 offers several reports on file audits, including file creations, deletions, modifications, and read accesses.
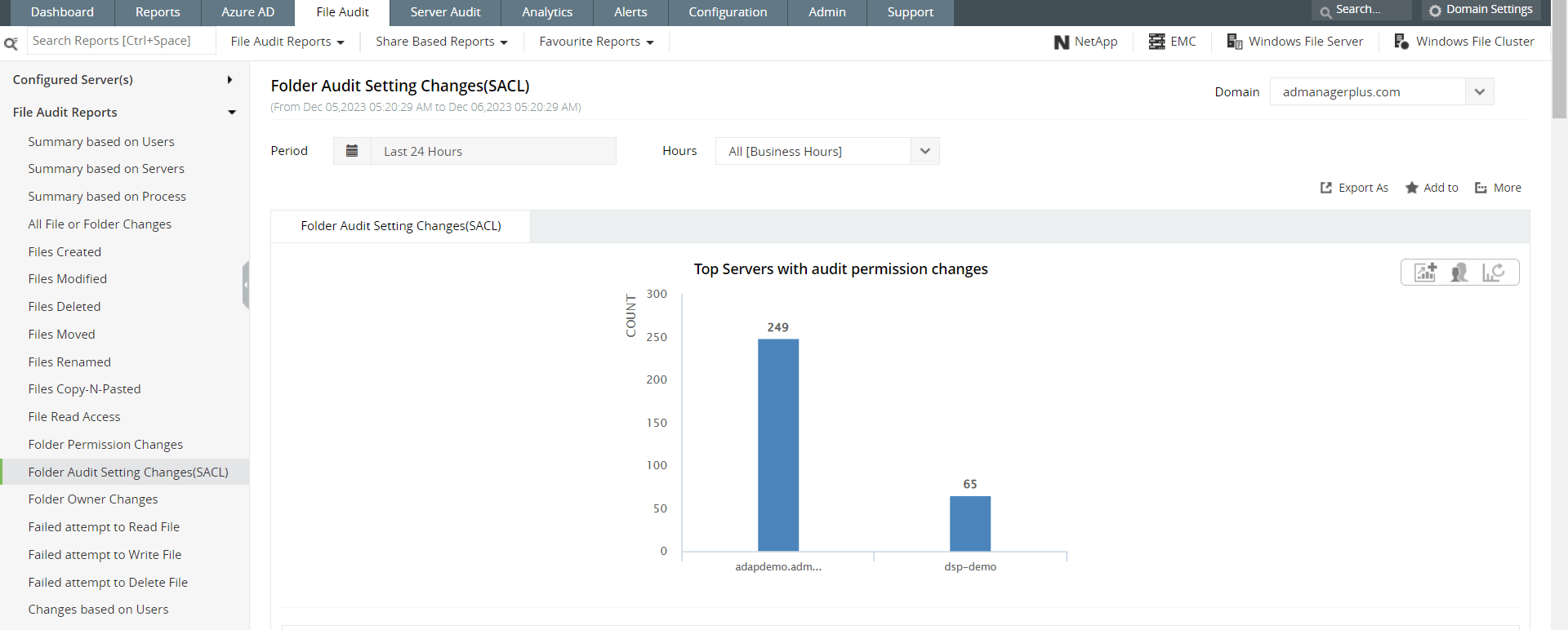 Figure 6: A security manager can also view reports on file permission changes and file audit changes.
Figure 6: A security manager can also view reports on file permission changes and file audit changes.
Most well-known malware contains code that can make changes to your system files or registry. Often, this indicator of compromise shows that an attacker is achieving persistence on your network by manipulating the settings. Figure 7 shows you a Log360 report that can help you track your registry.
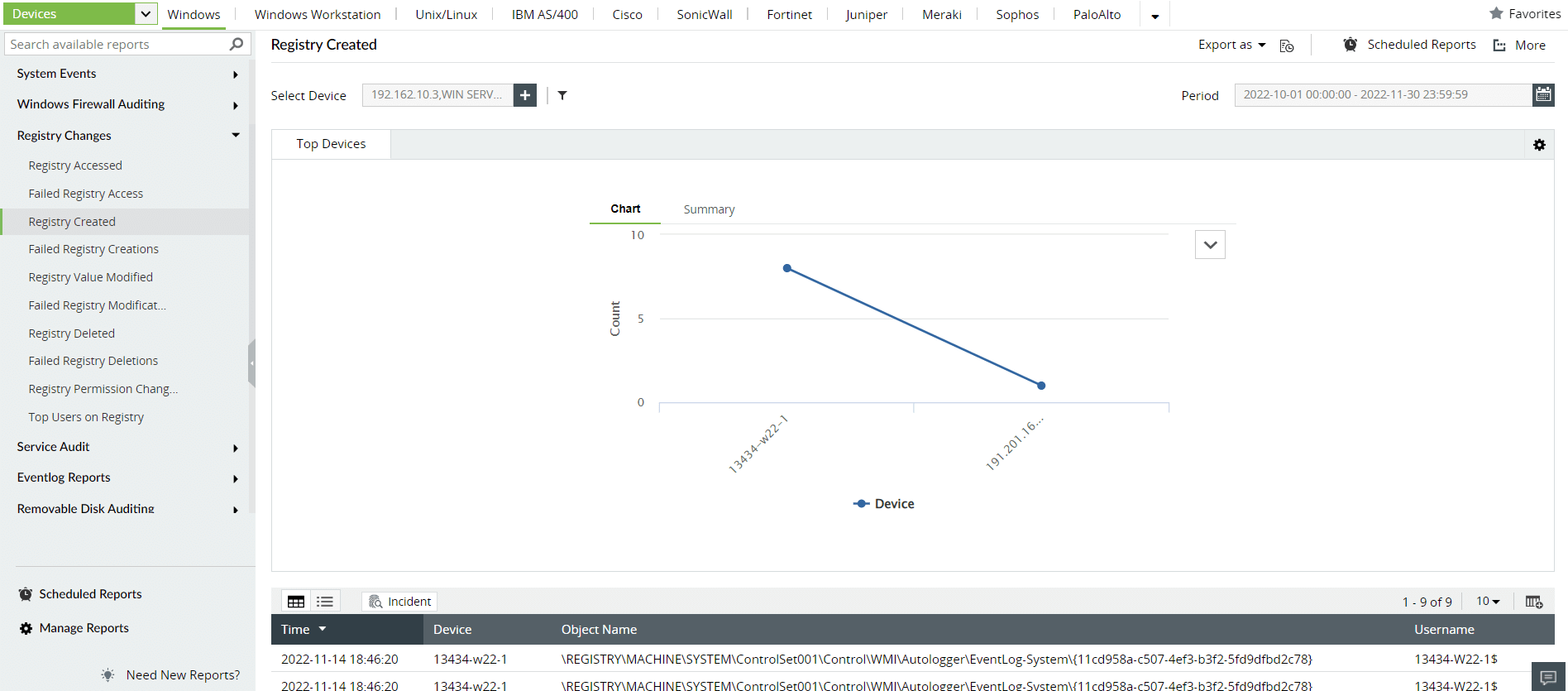 Figure 7: Log360's built-in reports on registry changes help SOC managers monitor registry modifications.
Figure 7: Log360's built-in reports on registry changes help SOC managers monitor registry modifications.
Another breadcrumb a threat actor might leave on your network are strange digital artifacts that haven't been a part of your network inventory. So if your team spots unknown devices or devices that were disabled, logs of unusual protocols, strange file names, or extensions, you can flag these and treat these as indicators of compromise. Figures 8 and 9 show how you can track newly added objects and other file activity on your network with Log360.
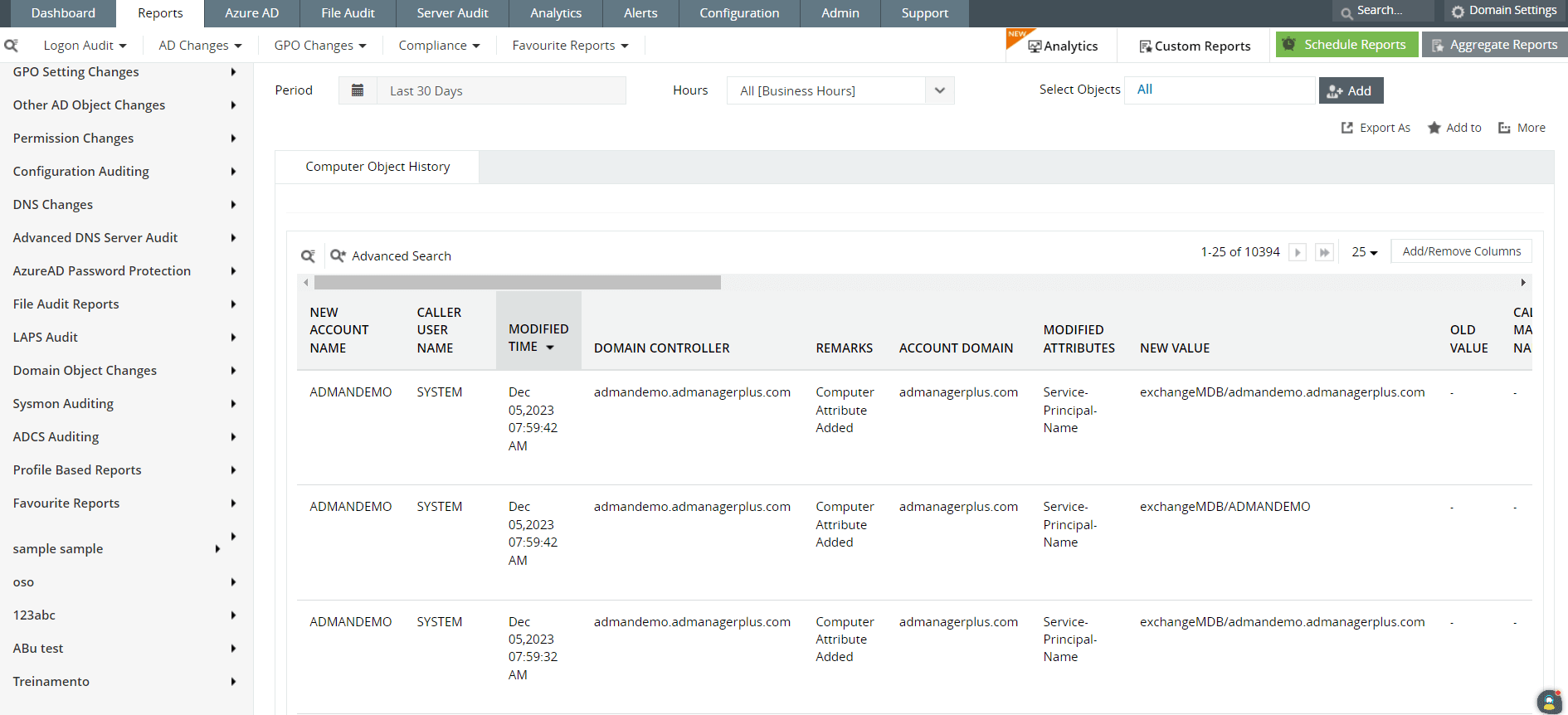 Figure 8: SOC managers can view Log360 reports on computer management and object history to track any devices or artifacts being added to the network.
Figure 8: SOC managers can view Log360 reports on computer management and object history to track any devices or artifacts being added to the network.
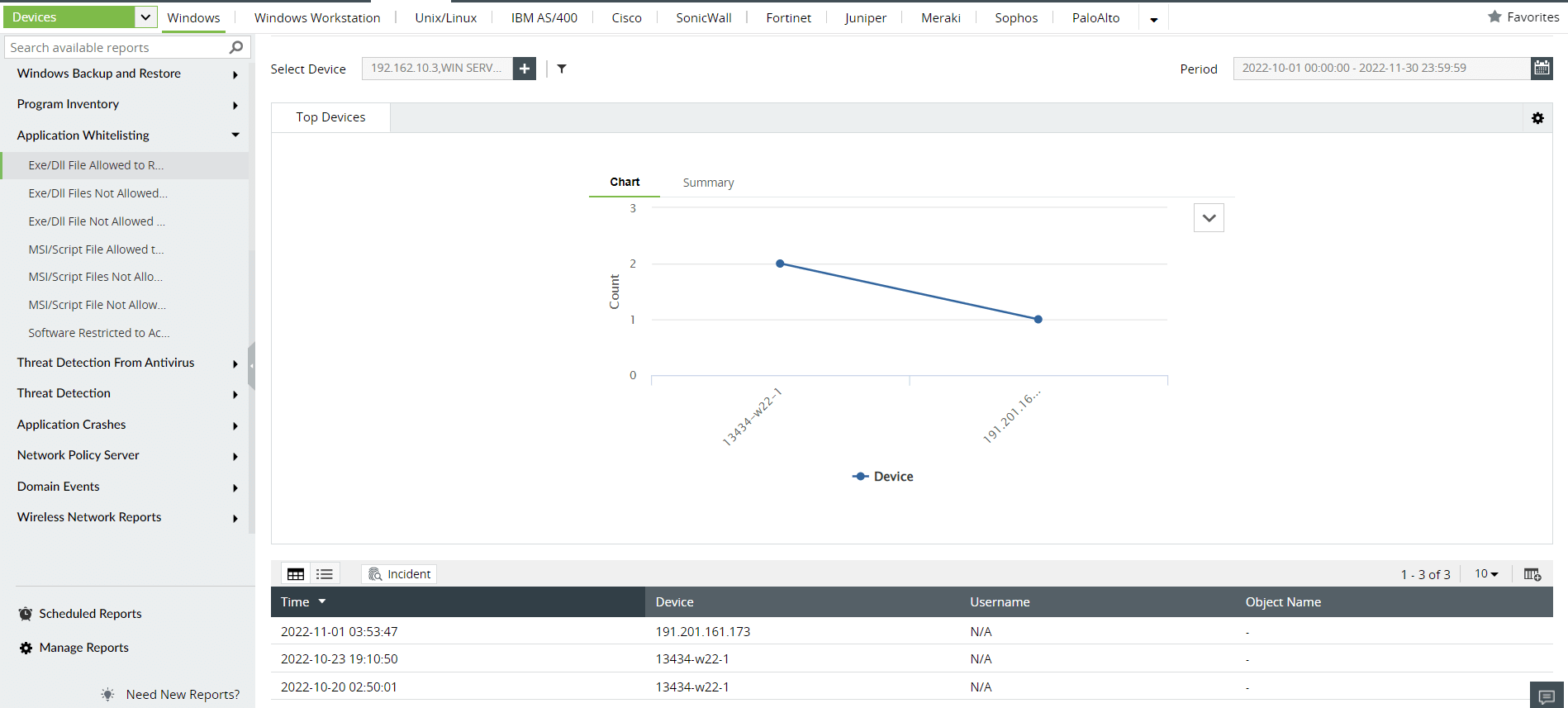 Figure 9: Log360 shows reports on EXE/DLL file activity on the network.
Figure 9: Log360 shows reports on EXE/DLL file activity on the network.
Now that you've got a hang of known indicators and how to manage new ones, you can use the list of indicators below to identify some well-known attacks.
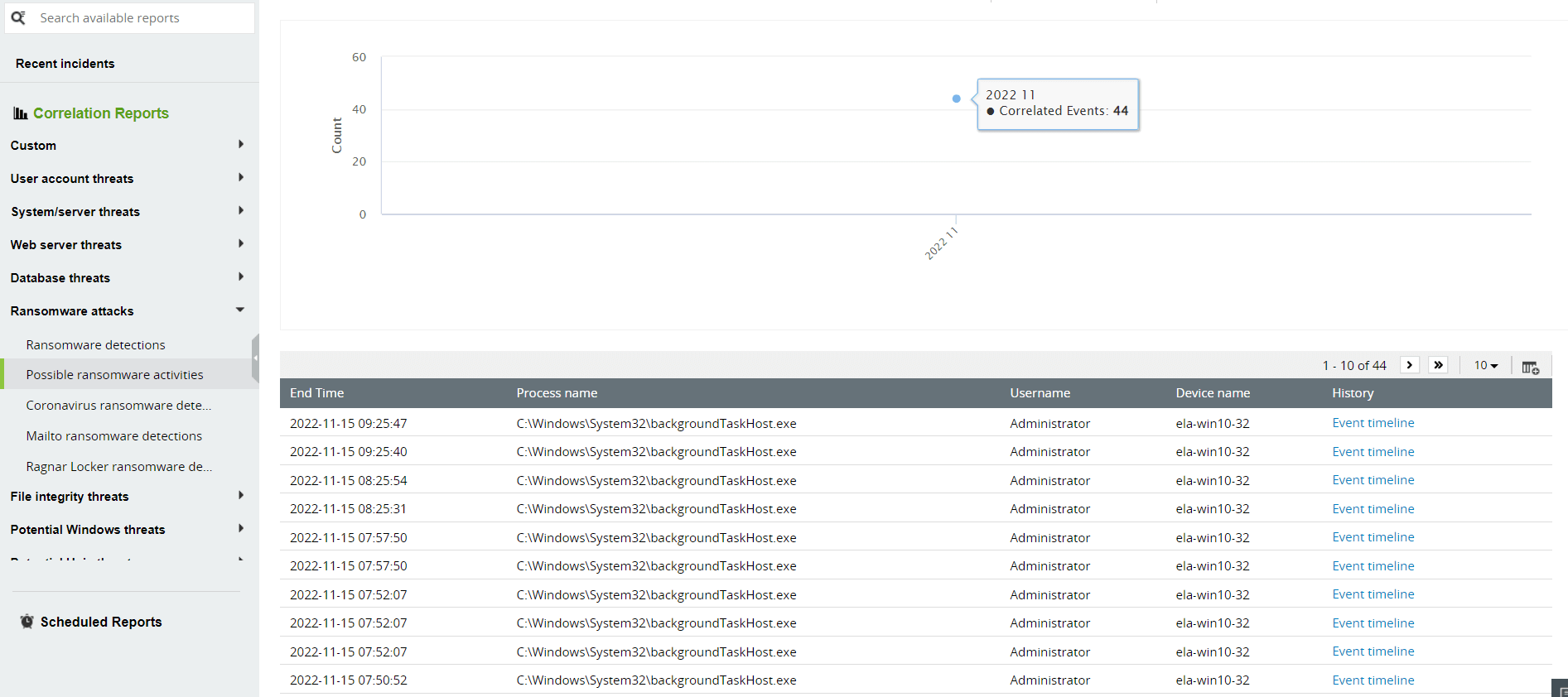 Figure 10: Built-in correlation reports in Log360 help SOC teams track possible ransomware activity.
Figure 10: Built-in correlation reports in Log360 help SOC teams track possible ransomware activity.
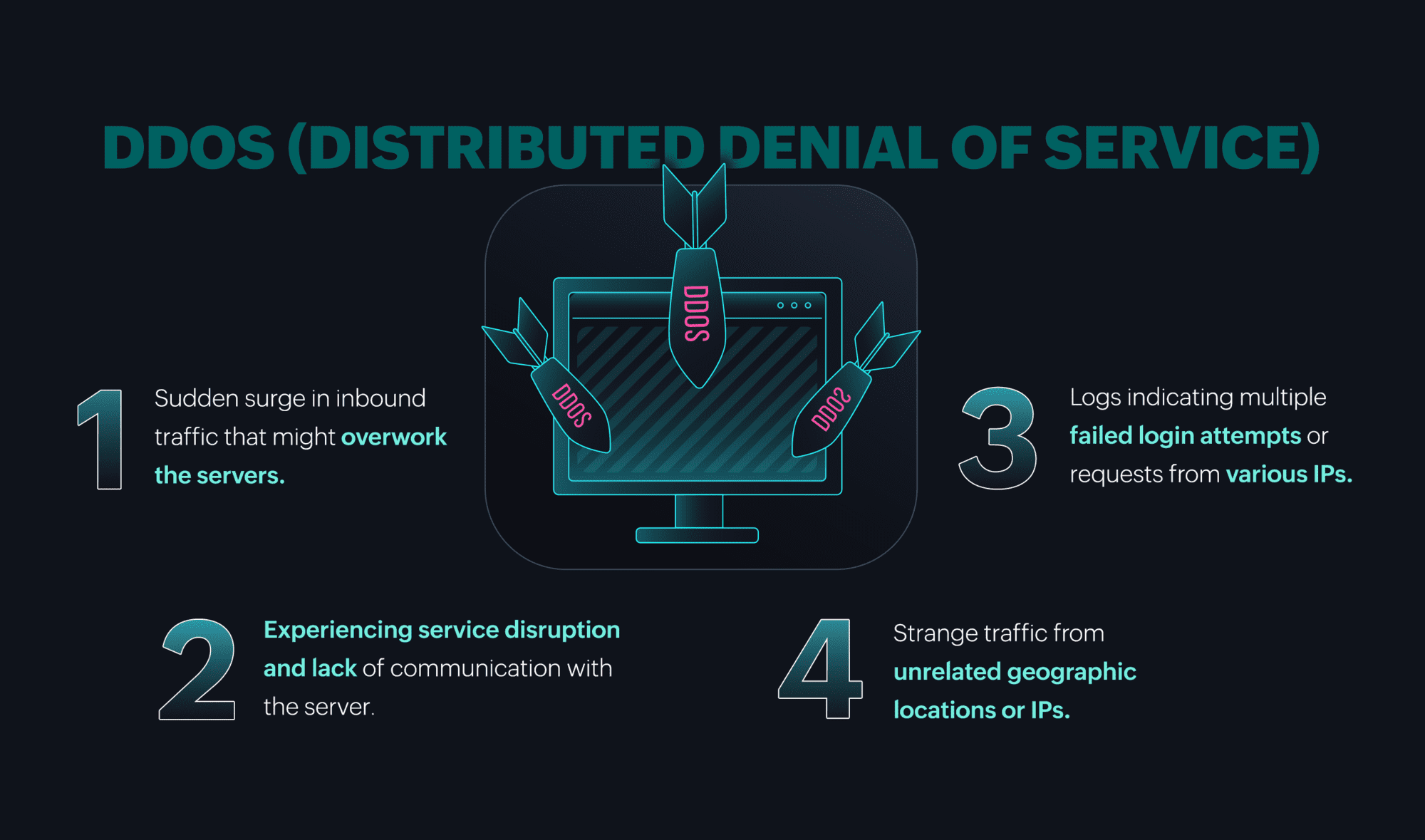
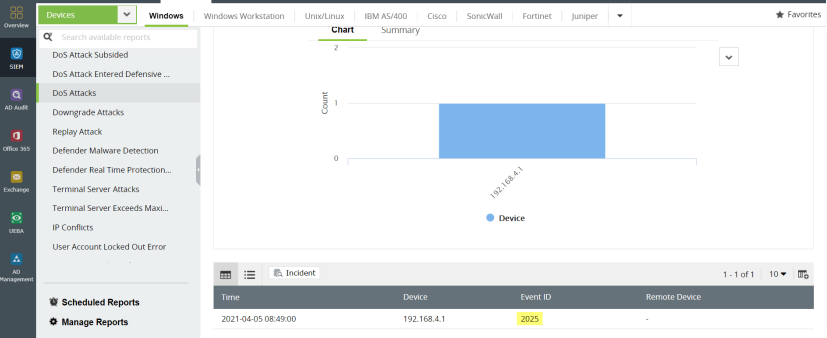 Figure 11: Built-in correlation capabilities in Log360 can detect DDoS attacks.
Figure 11: Built-in correlation capabilities in Log360 can detect DDoS attacks.
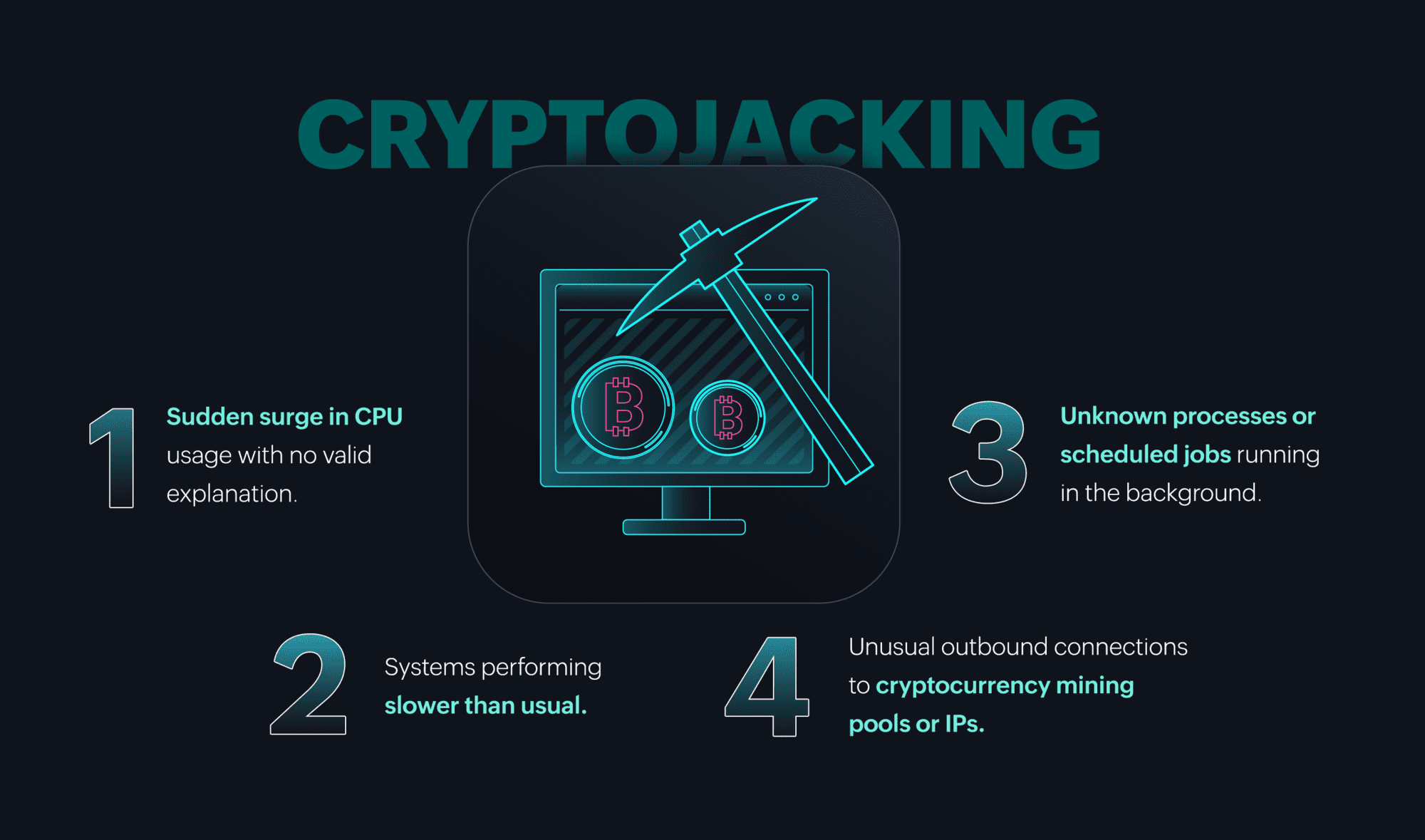
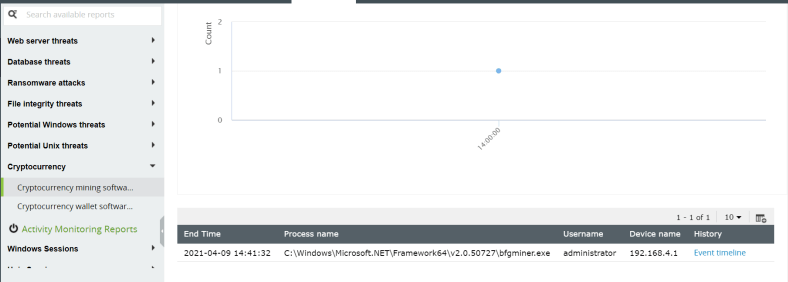 Figure 12: Built-in correlation capabilities in Log360 can detect presence of cryptomining software.
Figure 12: Built-in correlation capabilities in Log360 can detect presence of cryptomining software.
It's important to remember that IoCs don't remain the same throughout. They go through a life cycle of discovery, implementation, and eventually become irrelevant as the threat landscape changes. So, it's important to know just what happens when a new IoC comes into existence and what goes into the management of IoCs.
A team of security analysts might often encounter strange patterns or signals that they have to look into meticulously. Through thorough research on artifacts like malware samples, behavioral patterns, and traffic, a team of analysts might conclude that they have an undiscovered IoC on their hands.
To determine that a certain digital clue is an indicator of compromise, some experts suggest that an IoC has to satisfy the following conditions.
The discovery and related knowledge of a new IoC now has to be distributed between various security stakeholders. IoCs have to be entered into a threat intelligence repository for all stakeholders to be able to access. Always ensure that new IoCs have enough contextual information like the name of the attack group that is associated with it, what possible attack goals were associated with it, and the estimated lifetime of that indicator of compromise based on your assessment. Details like this help incident responders, analysts, and other security team members to make informed decisions if they ever come across the same IoC again.
The newly discovered indicator of compromise now has to become a part of threat intelligence, IDS systems, and your overarching SIEM solution. Setting up real-time monitoring, alerts, correlation rules, and even custom reports (if you're using Log360) are all great ways of flagging this new IoC and bringing it to the attention of your team. You can also create automated incident response workflows for immediate action against the specific IoC.
As the threat landscape changes constantly, the indicators of compromise that were once on your watch list will also become irrelevant. Outdated malware signatures, IP addresses that were once red flags but no longer in existence, old file hashes, are all examples of indicators of compromise that no longer hold any value. Keeping these alive in your SOC tools will only lead to false positives and disorganized IoC management for your team.
As a SOC manager you've probably heard of IoCs and IOAs being used frequently in the context of security. There's a fine difference that exists between these terminologies that mainly spring from the difference in the nature of the evidence and the timelines they fall under.
| Indicators of compromise | Indicators of attack |
|---|---|
| IoC's are generally digital artifacts you discover on the network that indicate a security incident or potential breach has occurred. | IoAs are abnormal behavioral patterns that indicate malicious intent. |
| Examples: Strange IP addresses, domain names, file hashes, known malware signatures, unauthorized file modifications, or system changes | Examples: Unusual file execution behavior, lateral movement across the network, privilege escalation attempts, or abnormal access patterns. |
| The discovered artifacts are normally associated with historical threats. | The anomalous behaviors seen can be unfamiliar to threat intelligence sources. |
| A SOC team can rely on IoCs for reactive security strategies based on known patterns or signatures from past attacks. IoCs are usually relied on by threat hunting teams. | A SOC team relies on IoAs for proactive security strategies like understanding the tactics, techniques, and procedures (TTPs) of attackers, often leveraging behavioral analytics. |
ManageEngine's SIEM solution, Log360, offers enhanced incident management and response, built-in SOAR capabilities, and ADmanagement and auditing, all in one tool. Its UEBA component, which is powered by ML algorithms, provides greater visibility into threats with score-based risk assessment for users and entities through its dashboard. It provides more context to the risk scoring process by using dynamic peer grouping. Learn more about how Log360, ManageEngine's new-age SIEM solution with autonomous SOC capabilities, can add value to an organization's security posture and help you bridge the gap between where you are today and where you should be. Sign up for a personalized demo.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.