- Free Edition
- Quick links
- Active Directory management
- Active Directory reporting
- Active Directory delegation
- Active Directory permissions management and reporting
- Active Directory automation
- Governance, risk, and compliance
- Microsoft 365 management and reporting
- Microsoft 365 management and reporting
- Microsoft 365 management
- Microsoft 365 reports
- Microsoft 365 user management
- Microsoft 365 user provisioning
- Microsoft 365 license managementn
- Microsoft 365 license reports
- Microsoft 365 group reports
- Dynamic distribution group creation
- Dynamic distribution group reports
- Exchange management and reporting
- Active Directory integrations
- Popular products
Access certification campaign
Access certification campaigns are a critical component of a robust identity governance and administration (IGA) solution. These solutions ensure that access rights are regularly reviewed and that users only have the privileges they need to perform their duties. Access certification campaigns help organizations automate users' access management, mitigate access-related attacks, and demonstrate compliance with IT regulations like the GDPR, PCI DSS, HIPAA, and more.
Access recertification—an integral part of the access certification process—plays a key role in maintaining an organization's security and compliance posture. By periodically reviewing and revalidating users' access privileges, organizations can ensure that employees, contractors, or third parties only retain access to systems and data necessary for their roles. Integrating access recertification into access certification campaigns ensures a proactive approach to access management, bolstering an organization's overall security framework.
Significance of access certification in compliance
Adherence to regulations—like the GDPR, HIPAA, PCI DSS, and more—is essential in today's data-driven world, where organizations heavily rely on and generate data. Failure to comply with these regulations can lead to legal repercussions like lawsuits and penalties as well as increase the risk of data breaches and cyberattacks. Preventing unauthorized access and protecting sensitive information is one vital requirement set forth by IT mandates, and organizations must establish measures and policies that guarantee authorized individuals have access to appropriate resources to ensure the security of their networks. Access recertification helps reinforce these policies, ensuring only the right people have access to sensitive data and systems.
Managing access permissions for employees may appear straightforward, but it is actually a challenging task. It is error-prone, time-consuming, and can increase administrative overhead. That's why it is essential to invest in a reliable solution that not only helps automate the entire process but also facilitates auditing through access certification and access recertification.
ADManager Plus' access certification campaigns
ADManager Plus is an IGA solution that offers access certification capabilities to organizations to streamline their access control methods. Access certification campaigns can be utilized to assign, recertify, and revoke users' access rights and implement the principle of least privilege, segregation of duties, and role-based access control. Organizations can implement these principles to thwart privilege abuse attacks and safeguard their networks. With the access certification campaigns in ADManager Plus, user access rights—like NTFS permissions or Microsoft 365 roles and applications—can be validated in bulk, resulting in improved operational efficiency. These access certification efforts ensure ongoing compliance with internal and external audit requirements.
ADManager Plus also enhances life cycle management by automating user provisioning, password management, and group management and by providing custom workflows for multi-level approvals and real-time notifications.
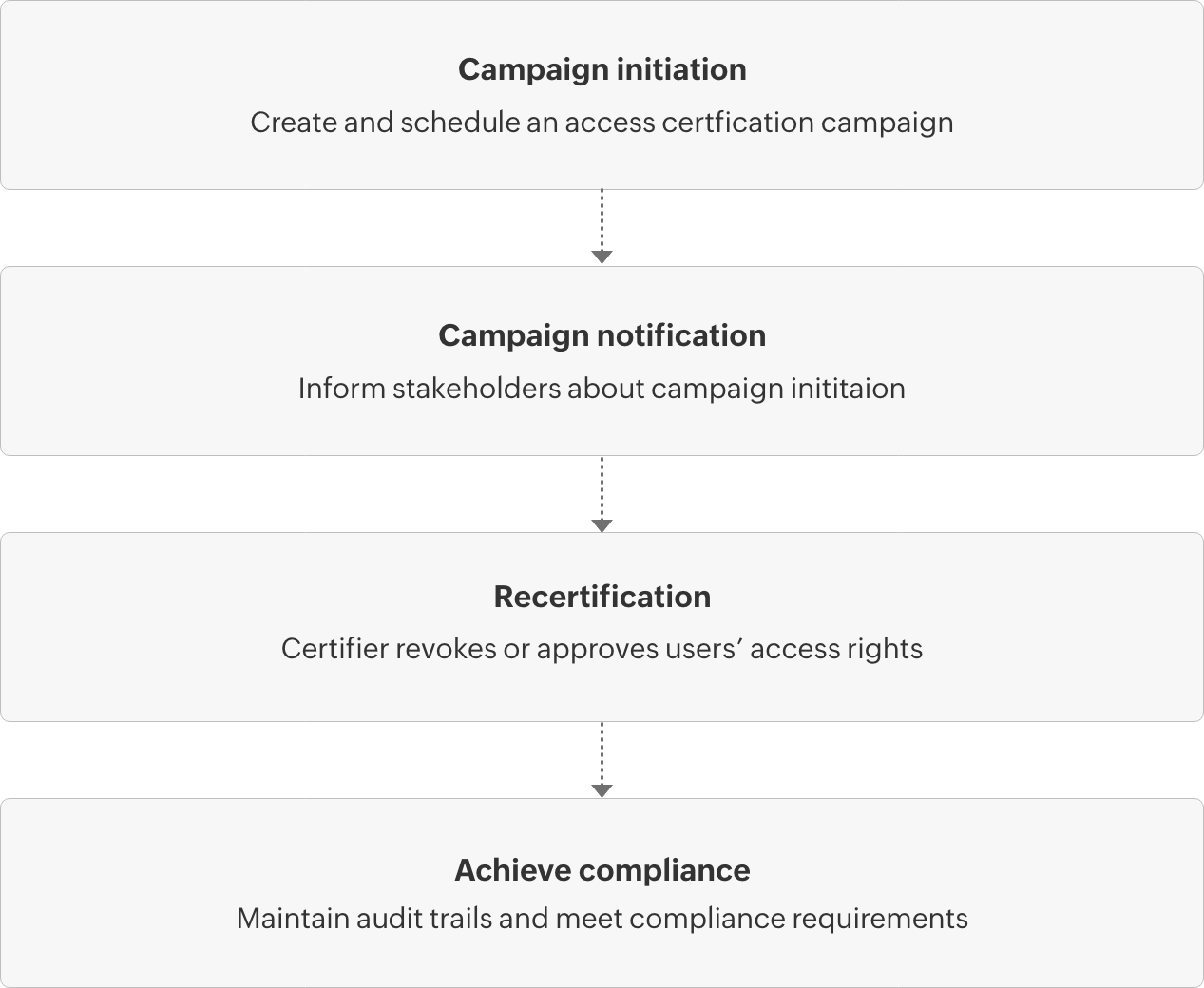
Components of an access certification campaign
Certifier
A key stakeholder in the process who audits users' access rights and takes action on them. A certifier can be an administrator, help desk technician, a user's manager, or the role can be customized to an organization’s needs.
Certification campaigns
Audit campaigns with policies and criteria that can be used to assess users' access rights. These campaigns can be scheduled and prioritized based on the entitlements that are to be reviewed. Access recertification is a part of this continuous effort to ensure proper access.
Entitlements
Users' group memberships and access permissions that will be validated by the certifier.
Certifier assigning rules
Rules that can be configured to dynamically assign certifiers.
Make informed decisions with smart access recommendations
When reviewing access during certification campaigns, ADManager Plus goes a step further by offering smart access recommendations. These suggestions are based on peer comparison and behavioral baselines, helping reviewers quickly identify unusual or excessive permissions. With this, reviewers can:
- Detect abnormal or excessive access.
- Speed up decision-making with contextual insights.
- Reduce errors and ensure policy-aligned access revocations.
How to make the most out of access certification
ADManager Plus also offers a risk exposure management feature that can be used alongside access certification to strengthen an organization's overall AD security. This capability gives a clear view of an organization's AD threat landscape by helping admins visualize potential attack paths in their AD environment.
Here's how using risk exposure management and access certification together can enhance an organization's security posture:
- Prioritize and launch targeted certification campaigns around high-priviled accounts.
- Drill down into each identity’s permissions and security posture.
- Take action by revoking or modifying risky privileges.
This ensures that access reviews are not just routine checks, but strategic, risk-driven validations that strengthen overall security.
Ensure regulatory compliance with Access Certification Campaigns in ADManager Plus
Ensuring proper access controls isn't just good practice—it's a requirement. Here's how leading compliance standards emphasize robust access management:
| Compliance | Section/Article | Description |
|---|---|---|
| HIPAA | 45 CFR 164.308(a)(3)(i) |
Implement policies and procedures to ensure that all members of its workforce have appropriate access to electronic protected health information |
| 45 CFR 164.308(a)(3)(ii)(B) |
Implement procedures to determine that the access of a workforce member to electronic protected health information is appropriate | |
| 45 CFR 164.308(a)(4)(ii)(C) |
Implement policies and procedures that establish, document, review, and modify a user's right of access to workstations, transactions, programs, or processes | |
| PCI DSS v4.0 | Requirement 7.2.3 | Required privileges are approved by authorized personnel |
| Requirement 7.2.4 | All user accounts and related access privileges are reviewed at least once every six months to ensure accounts and access remain appropriate based on job function | |
| Requirement 7.2.5.1 | All access by application and system accounts is reviewed periodically based on targeted risk analysis frequency | |
| SOX | Section 302(a)(4)(A) | Signing officers are responsible for establishing and maintaining internal controls |
| Section 404 | Management assessment of internal controls over financial reporting | |
| ISO 27001:2022 | Control 5.15 | Rules to control physical and logical access to information and other associated assets shall be established and implemented based on business and information security requirements |
| Control 5.18 | Access rights to information and other associated assets shall be provisioned, reviewed, modified, and removed in accordance with established policies | |
| Control 8.3 | Access to information and other associated assets shall be restricted in accordance with established access control policies | |
| GDPR | Article 32(1)(b) | Implement appropriate technical and organizational measures to ensure ongoing confidentiality, integrity, availability, and resilience of processing systems |
| Article 25 | Data protection by design and by default: Implement appropriate technical and organizational measures to ensure data protection principles are integrated into processing | |
| NIST CSF 2.0 | PR.AC-1 | Identity and access management processes and procedures are established and implemented |
| PR.AC-4 | Access permissions and authorizations are managed, incorporating the principles of least privilege and separation of duties | |
| NIST SP 800-53 | AC-2 | Account Management: An organization manages system accounts, including establishing conditions for group membership, identifying authorized users, and reviewing accounts |
| COBIT 2019 | APO13.01 | Establish and maintain an information security management system |
| DSS05.04 | Manage identity and access rights: Ensure appropriate access to systems and data through proper identity and access management | |
| FISMA | Control AC-2 | Account management: An organization manages information system accounts, including authorizing access and reviewing accounts |
| Control AC-6 | Least privilege: An organization employs the principle of least privilege, allowing only authorized access necessary to accomplish assigned tasks | |
| NERP CIP | CIP-004-6 R4 | Personnel access authorization: Verify that individuals have authorization for access to designated storage locations of BES Cyber System Information |
| CIP-004-6 R5 | Personnel access authorization: Review access permissions to physical and electronic access rights to applicable systems at least once every 15 months | |
| FFIEC | Information Security Booklet | Access rights administration: Financial institutions should implement processes to grant, review, and revoke user access rights |
| COSO | Internal Control Framework | Control Activities: Policies and procedures that help ensure management directives are carried out |
How Access Certification Campaigns address these compliance requirements
ADManager Plus Access Certification Campaigns provide a comprehensive solution for meeting the diverse compliance mandates outlined above through systematic access governance and automated review processes. These campaigns directly address regulatory requirements by enabling periodic validation of user access rights, ensuring that employees maintain only the permissions necessary for their current job functions while providing the documentation and oversight required by auditors and regulatory bodies.
The campaigns support compliance-mandated review frequencies across different standards—from PCI DSS's six-month cycles to NERC CIP's 15-month requirements—through flexible scheduling that can be configured to meet specific regulatory timelines. Designated approvers and reviewers validate access appropriateness, ensuring that required privileges are approved by authorized personnel as mandated by frameworks like PCI DSS and HIPAA. This systematic approach supports the principle of least privilege by identifying and removing excessive access rights during regular review cycles, directly addressing requirements from NIST CSF, FISMA, and ISO 27001.
For healthcare organizations subject to HIPAA, the campaigns ensure that workforce access to electronic protected health information is continuously validated and appropriately restricted. Financial institutions benefit from structured access rights administration that meets FFIEC guidelines and supports SOX internal control requirements with documented approval workflows and management oversight. Critical infrastructure operators can maintain compliance with NERC CIP standards through verified access authorization processes and mandated review cycles for personnel accessing sensitive energy systems.
The solution generates comprehensive audit trails and documentation that support compliance assessments across all frameworks, from SOX Section 404 internal control evaluations to ISO 27001 certification audits. Risk-based scheduling capabilities align with targeted risk analysis requirements found in PCI DSS and COBIT 2019, while management acknowledgment workflows ensure executive oversight of access decisions as required by multiple compliance standards.
By automating these traditionally manual processes, Access Certification Campaigns reduce compliance burden while strengthening security posture, enabling organizations to demonstrate regulatory adherence through systematic access governance, documented review processes, and comprehensive audit-ready reporting across multiple compliance frameworks simultaneously.
How Access Certification Campaigns address compliance standards
Systematic access governance and validation
Periodic validation of user access rights:
- Employees maintain only permissions necessary for current job functions
- Documentation and oversight required by auditors and regulatory bodies
- Comprehensive audit trails for compliance assessments
Compliance-mandated review frequencies:
- PCI DSS: Six-month cycles | NERC CIP: 15-month requirements
- Flexible scheduling configured to meet specific regulatory timelines
- Risk-based scheduling aligned with targeted risk analysis requirements
Authorized personnel validation:
- Designated approvers and reviewers validate access appropriateness
- Required privileges approved by authorized personnel (PCI DSS, HIPAA)
- Supports principle of least privilege (NIST CSF, FISMA, ISO 27001)
Management oversight and documentation:
- Executive approval workflows for access decisions
- Comprehensive audit-ready reporting across multiple frameworks
- Reduced compliance burden through automated processes
Industry-specific compliance benefits
Tailored support across sectors
Healthcare organizations (HIPAA):
- Continuous validation of workforce access to electronic protected health information
- Appropriately restricted access to sensitive patient data
- Documentation of access decisions supporting HIPAA Security Rule compliance
Financial institutions (SOX, FFIEC, PCI DSS):
- Structured access rights administration meeting FFIEC guidelines
- Documented approval workflows supporting SOX internal control requirements
- Six-month review cycles for PCI DSS compliance with management oversight
Critical infrastructure (NERC CIP):
- Verified access authorization processes for BES Cyber System Information
- Mandated 15-month review cycles for personnel accessing sensitive energy systems
- Compliance documentation for regulatory assessments
Federal agencies (FISMA, NIST):
- Account management and authorization processes per NIST SP 800-53
- Least privilege enforcement aligned with FISMA requirements
- Security control implementation supporting federal compliance mandates
Benefits of access certification campaigns
Enhanced security
Reduce the risk of unauthorized access by identifying and removing users' inappropriate access rights through access certification.
Compliance demonstration
Comply with mandates and organizational policies by maintaining an auditable record of access reviews, including access recertification and changes.
Minimized insider threats
Periodically reviewing users' access rights can help detect and revoke unnecessary privileges and keep malicious insiders at bay.
Resource optimization
Reviewing and revoking users' access to enterprise resources and group memberships helps reduce license and subscription costs.
-
Prevent privilege creep
Regularly review access permissions through access recertification to avoid the accumulation of privileges.
-
Improved efficiency
Streamline access management processes by running automated campaigns, including access recertification, to identify and revoke access for over-privileged accounts.
Accelerated certification
Make quicker, more informed certification decisions and simplify reviews with access recommendations.
Use cases
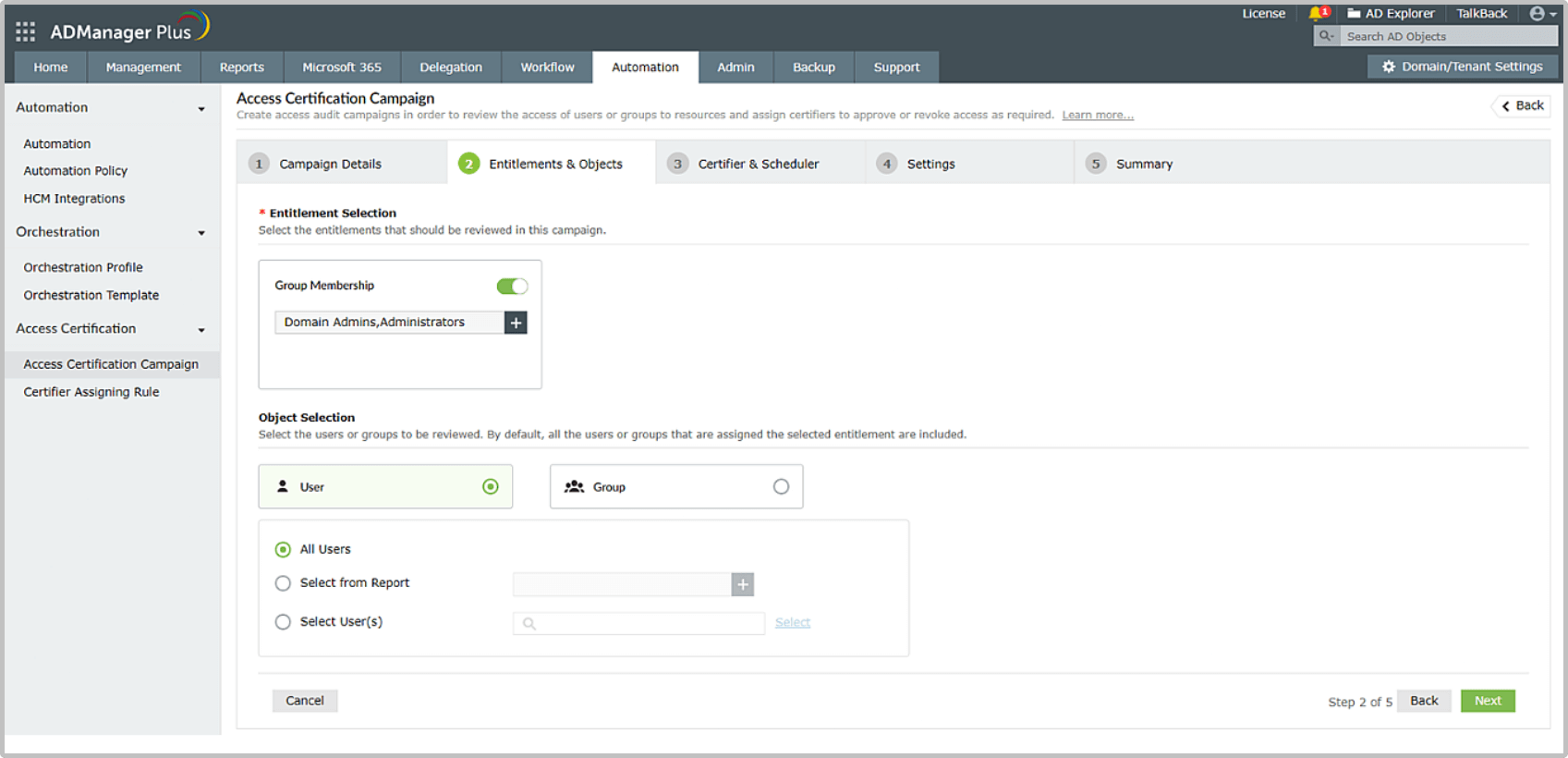
Use case 1: Secure privileged accounts
Run a customized certification campaign to manage the privileges of accounts with access to sensitive information and revoke privileges as and when needed.
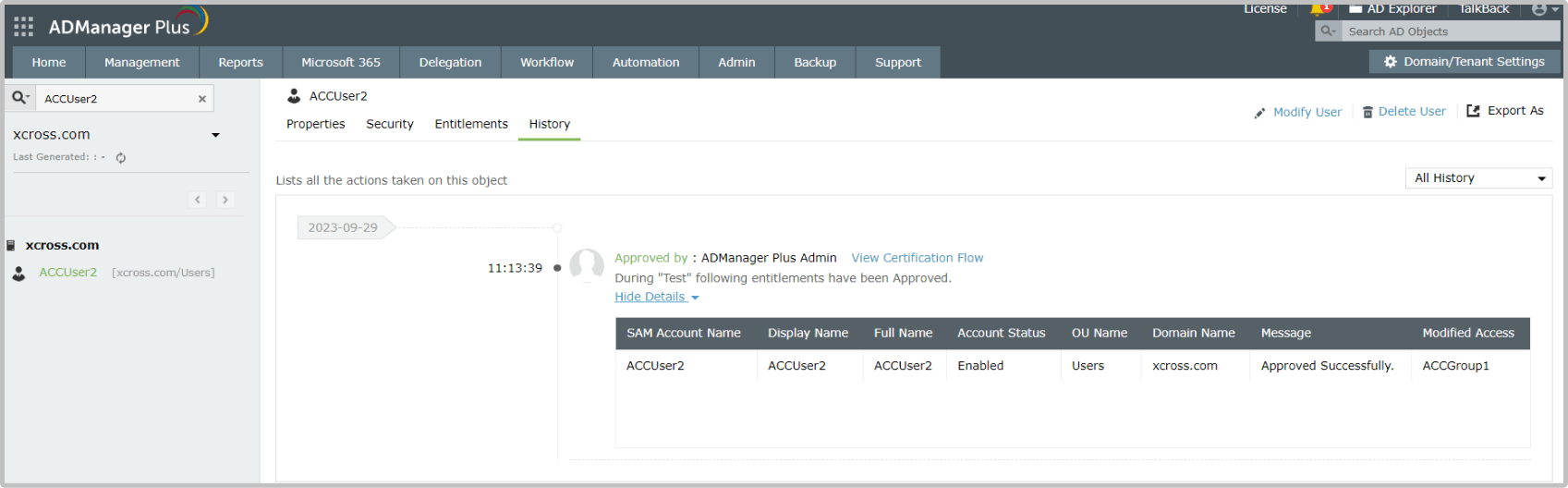
Use case 2: Meeting compliance and audit requirements
Each certification campaign that is conducted in ADManager Plus is stored and can be viewed by stakeholders. A detailed history of the campaign, including certifier name, action performed, comments added by the certifier, and more, is recorded. Auditors and compliance staff can use this during audit trials.
Use case 3: Recertifying user access
Schedule and run access certification campaigns frequently at a desired time to review and recertify users' access rights, ensuring that users' access is consistently validated and aligned with current roles and responsibilities.
Other features
Active Directory Management
Make your everyday Active Directory management tasks easy and light with ADManager Plus's AD Management features. Create, modify and delete users in a few clicks!
Active Directory password management
Reset password and set password propertied from a single web-based console, without compromising on the security of your AD! Delegate your password-reset powers to the helpdesk technicians too!
Active Directory computer reports
Granular reporting on your AD Computer objects to the minutest detail. Monitor...and modify computer attributes right within the report. Reports on Inactive Computers and operating systems.
Microsoft Exchange Management
Create and manage Exchange mailboxes and configure mailbox rights using ADManager Plus's Exchange Management system. Now with support for Microsoft Exchange 2010!!
Active Directory Cleanup
Get rid of the inactive, obsolete and unwanted objects in your Active Directory to make it more secure and efficient...assisted by ADManager Plus's AD Cleanup capabilities.
Active Directory automation
A complete automation of AD critical tasks such as user provisioning, inactive-user clean up etc. Also lets you sequence and execute follow-up tasks and blends with workflow to offer a brilliant controlled-automation.
