- Home
- Logging guide
- AWS S3 bucket activity monitoring
AWS S3 bucket activity monitoring
In this page
- Common use cases of AWS S3
- Why is it important to monitor AWS S3 buckets?
- Key metrics to monitor in AWS S3
- AWS S3 monitoring using CloudTrial
- Analyzing AWS S3 logs
Amazon S3 is built to store and retrieve any amount of data from anywhere on the web, offering multiple tiers of storage for various use cases. S3 buckets are fundamental containers within Amazon S3 that store objects. Each object in a bucket contains data and metadata. Each bucket can range in size from a minimum of zero bytes to a maximum of five TB. Each bucket is given a unique name within the AWS region and comes with configurable settings like access permissions, versioning, and logging.
Common use cases of AWS S3
Amazon S3 is a versatile storage service used in a wide range of specific scenarios. Here are some detailed use cases:
- Media hosting for streaming services: Streaming platforms use S3 to store and deliver multimedia content such as movies, TV shows, and music. S3's high durability and integration with CDNs, like Amazon CloudFront, ensure seamless, high-quality streaming experiences for users worldwide.
- Backup and disaster recovery for enterprises: Enterprises leverage S3's versioning and cross-region replication features for a robust backup for critical data. This helps the data to be quickly restored in case of data loss or corruption.
- Data lake for big data analytics: Companies use S3 as a central data lake to store raw and processed data for big data analytics. Tools like Amazon Athena, AWS Glue, and Amazon Redshift can directly query data stored in S3, enabling advanced analytics and ML applications without data movement.
- Static website hosting for e-commerce platforms: E-commerce platforms host static websites on S3 to deliver fast and scalable online shopping experiences. By storing HTML, CSS, Javascript, and image files in S3, and leveraging CloudFront for content delivery, these platforms ensure high availability and quick loading times for their customers.
Why is it important to monitor AWS S3 buckets?
Monitoring AWS S3 buckets is essential for several reasons:
Security: AWS S3 monitoring helps detect unauthorized access or changes to data, ensuring only authorized users and applications are accessing S3 resources.
Compliance: AWS S3 monitoring ensures compliance with industry regulations by tracking and logging all access and modifications to sensitive data.
Data integrity: Monitoring AWS S3 helps maintain the integrity and availability of data by monitoring for accidental deletions or overwrites.
Operational insight: In order to gain visibility into data usage patterns and trends, AWS S3 monitoring aids by taking informed decisions about data management and storage policies.
Performance optimization: AWS S3 monitoring helps to make sure that the S3 resources are running efficiently and effectively by monitoring and analyzing the performance of data retrieval and storage operations.
Key metrics to monitor in AWS S3
When monitoring Amazon S3, there are several key metrics you should keep an eye on to ensure optimal performance, security, and cost management. These metrics can be divided into categories such as usage, performance, and security.
Usage metrics
1) Bucket size
- Monitors the total amount of data stored in an S3 bucket.
2) Number of objects
- Tracks the number of objects stored in an S3 bucket.
Performance metrics
1) First byte latency
- Measures the time it takes for the first byte of an object to be received from S3.
2) Total request latency
- Tracks the total time taken for a request, from the moment it is made until the response is fully received.
3) HTTP status codes
- Monitors the distribution of HTTP status codes returned by S3, such as 2xx (successful requests), 3xx (redirects), 4xx (client errors), and 5xx (server errors).
Request metrics
1) Get requests
- Counts the number of GET requests made to S3.
2) Put requests
- Tracks the number of PUT requests made to S3.
3) Delete requests
- Counts the number of DELETE requests made to S3.
4) List requests
- Tracks the number of LIST requests made to S3.
Security metrics
1) Bucket policies
- Monitors changes to bucket policies to ensure they comply with security standards.
2) Access control list (ACL) changes
- Tracks changes to ACLs on buckets and objects.
3) Public access
- Monitors whether any buckets or objects are publicly accessible.
Data management metrics
1) Replication status
- Tracks the status of S3 replication (if configured).
2) Lifecycle rule compliance
Monitors compliance with S3 lifecycle rules (e.g., transitioning objects to different storage classes, expiring objects).AWS S3 monitoring using CloudTrial
Creating a Trail in CloudTrail
1) Sign in to the AWS Management Console and open the CloudTrail console.
2) Create a trail:
- In the navigation pane, choose Trails, then Create trail.
- Enter a name for the trail.
- For Storage location, choose an existing S3 bucket or create a new one where the logs will be stored.
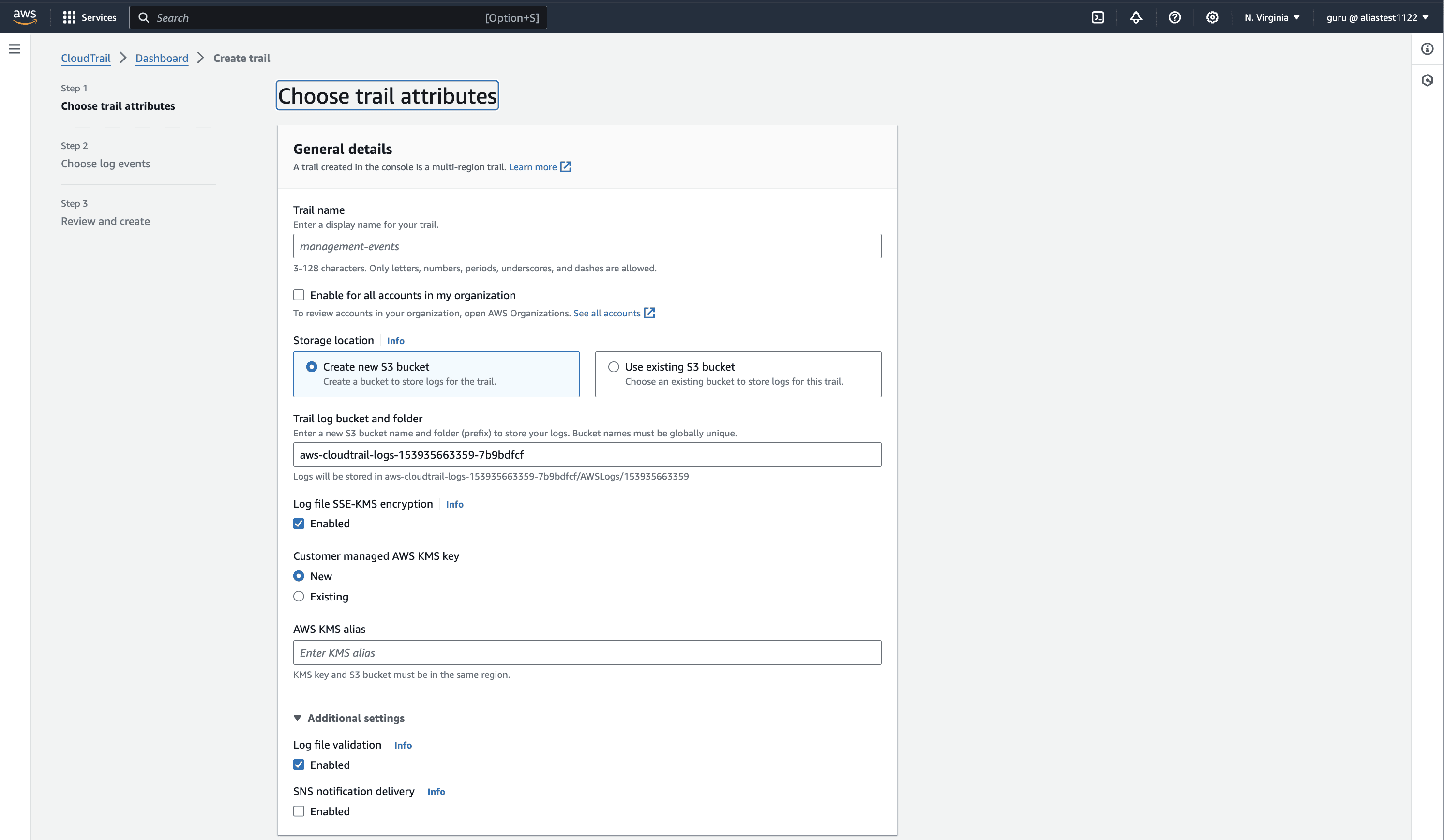
3) Configure the trail settings:
- Under Management events, ensure that Read/Write events is selected based on your requirements.
- For Data events, select S3 and choose the specific S3 bucket you want to monitor. You can select All current and future S3 buckets to log events for all S3 buckets in the account or select specific buckets.
- Ensure that both Read events and Write events are selected to capture all types of access and changes.
4) Optional (but recommended) settings:
- Enable Log file validation for additional security.
- Enable CloudWatch Logs to stream CloudTrail logs to CloudWatch for real-time monitoring and alerting.
5) Review and create the trail.
Note: Ensure that the CloudTrail has the necessary permissions to log events to the S3 bucket. If not, configure the necessary bucket policy.
Analyzing AWS S3 logs
Once CloudTrail is configured to log S3 bucket events, it's important to note that CloudTrail itself does not perform log analysis. Instead, you can analyze the logs using several methods:
1) AWS CloudWatch Logs:
- If you enabled CloudWatch Logs integration, navigate to the CloudWatch console to access and search through the logs.
- Set up CloudWatch Alarms to receive notifications for specific events or anomalies detected in the CloudTrail logs.
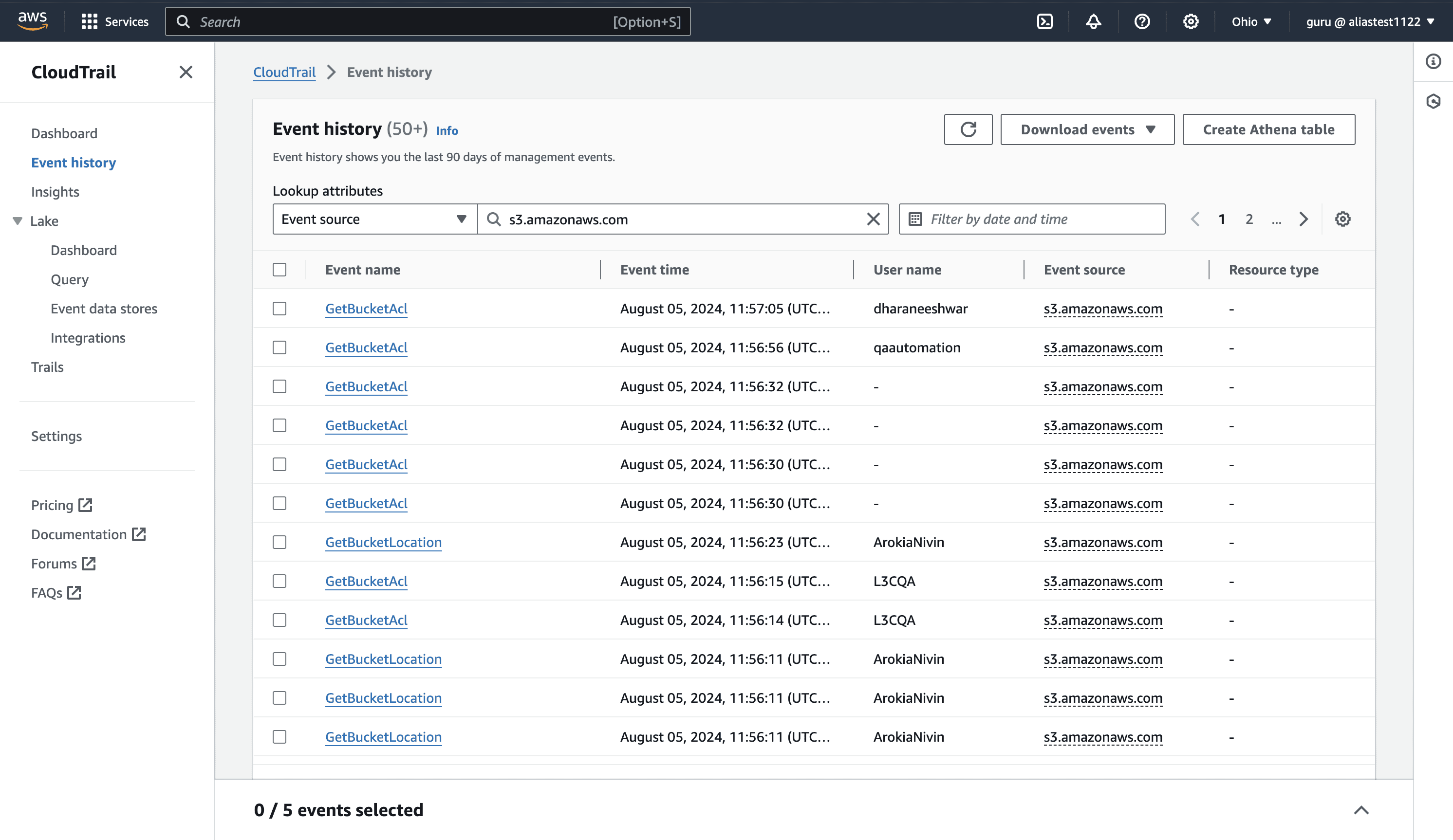
2) AWS Management Console:
- Navigate to the CloudTrail console and select Event history to view recent events.
- Utilize filters to narrow down to specific events related to your S3 bucket, such as ListBucket, GetObject, PutObject, etc.
3) Third-party SIEM
The most effective way to monitor your entire AWS environment, and not just S3, would be to use a third-party SIEM solution that can integrate with your AWS environment. All it takes is one step: Configuring your AWS account, and you’re set to comprehensively monitor and manage your AWS resources.
SIEM solutions can oversee your entire network, encompassing both on-premises and cloud devices, making them the perfect choice for hybrid or multi-cloud environments.
They offer many features to ease your cloud monitoring efforts:
1) Log correlation and analysis: Automatically correlate and analyze logs from both on-premises and cloud environments. This process extracts meaningful insights from the vast amount of data, identifying access patterns, detecting anomalies, and recognizing potential security threats across your cloud resources.
2) Automated report generation: Simplify compliance auditing processes by generating detailed reports based on the collected logs. These reports can be customized to meet specific regulatory requirements or organizational needs, providing clear visibility into activities across your entire network.
3) Real time alerts and notifications: Facilitate setting up real time alerts and notifications based on predefined rules and patterns identified in the logs. This proactive approach ensures that security incidents or operational issues related to your cloud resources are promptly detected and addressed.
4) Integration with cloud services: Seamlessly integrate with other cloud services such as AWS CloudTrial and Microsoft Azure for advanced querying and visualization.
5) Customizable dashboards: Visualize activity trends and security posture across all your cloud environments through intuitive dashboards. This empowers your team with actionable insights for informed decision-making and continuous improvement of your cloud security practices.
So, what next?
Try Log360 Cloud for efficient AWS S3 bucket activity monitoring
Log360 Cloud is ManageEngine's cloud-based SIEM solution that offers comprehensive visibility and security management across on-premises and cloud environments in a single platform. Enhance your security posture with real-time log analysis and threat detection.











