- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
What is GPG 13 compliance?
The Good Practice Guide 13 (GPG 13) is a framework with 12 protective monitoring controls (PMCs) for all His Majesty's Government (HMG) organizations. It is defined by the Communications-Electronics Security Group , Britain’s information assurance authority. When it comes to user access to networks and systems, GPG 13 requires organizations to record:
- Unauthorized application access.
- File access attempts to sensitive information.
- Successful logins and logouts.
- Unsuccessful logins and logouts.
- Privileged system changes (e.g., account management, policy changes, device configuration).
- Logs for at least six months.
How can you comply with GPG 13?
Compliance with GPG 13 is crucial for organizations dealing with sensitive data and connected to government networks. It helps protect privacy, prevent data breaches, and enhance overall cybersecurity. To comply with GPG 13, you need to implement all 12 PMCs. While adhering to GPG13 may be difficult for organizations facing constraints such as limited resources or small IT security teams, it is necessary to ensure the security and integrity of critical systems and sensitive information.
Who is expected to follow GPG 13?
Although the regulatory directives of GPG 13 primarily target HMG departments and agencies, service providers may also be obligated to adhere to it. Service providers that have access to government data are also expected to meet GPG 13's stipulated obligations.
Related content
Discover the simplified approach to GPG 13 compliance with EventLog Analyzer
Log management
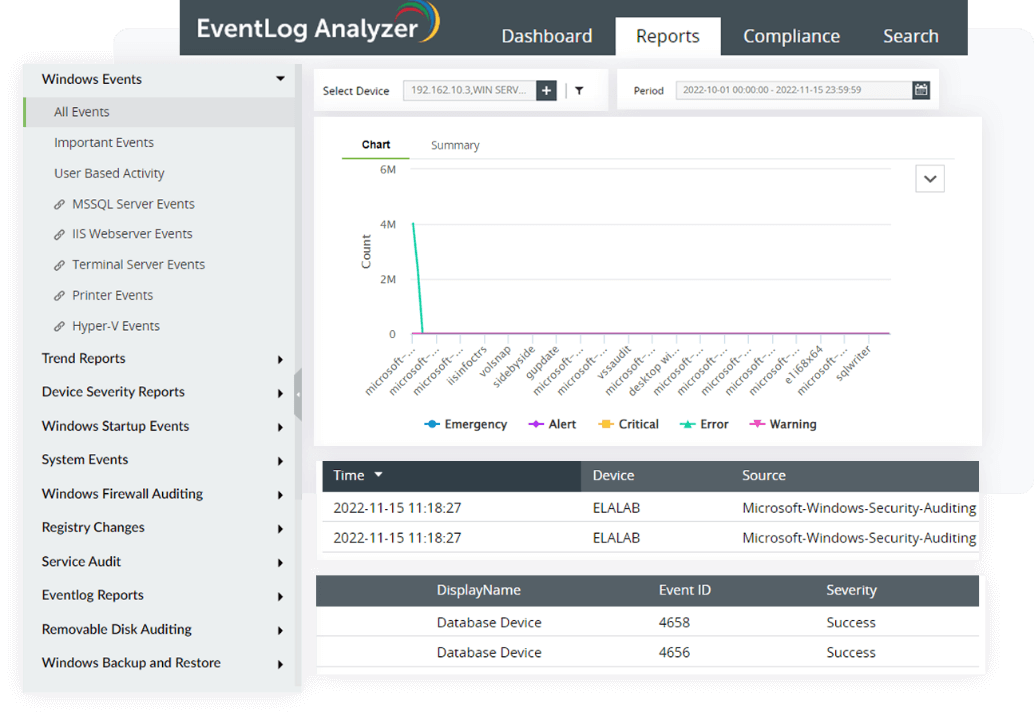
EventLog Analyzer is a log monitoring solution that collects logs from various log sources present in your network environment, like Windows systems, Unix/Linux systems, applications, databases, firewalls, routers, switches, and IDS/IPS. The solution also monitors Windows devices, workstations, servers, and operating systems to conduct in-depth auditing and generate reports that can help you comprehend security logs . This feature will help you record logs from all network connections, which helps you meet PMC 6.
File integrity monitoring
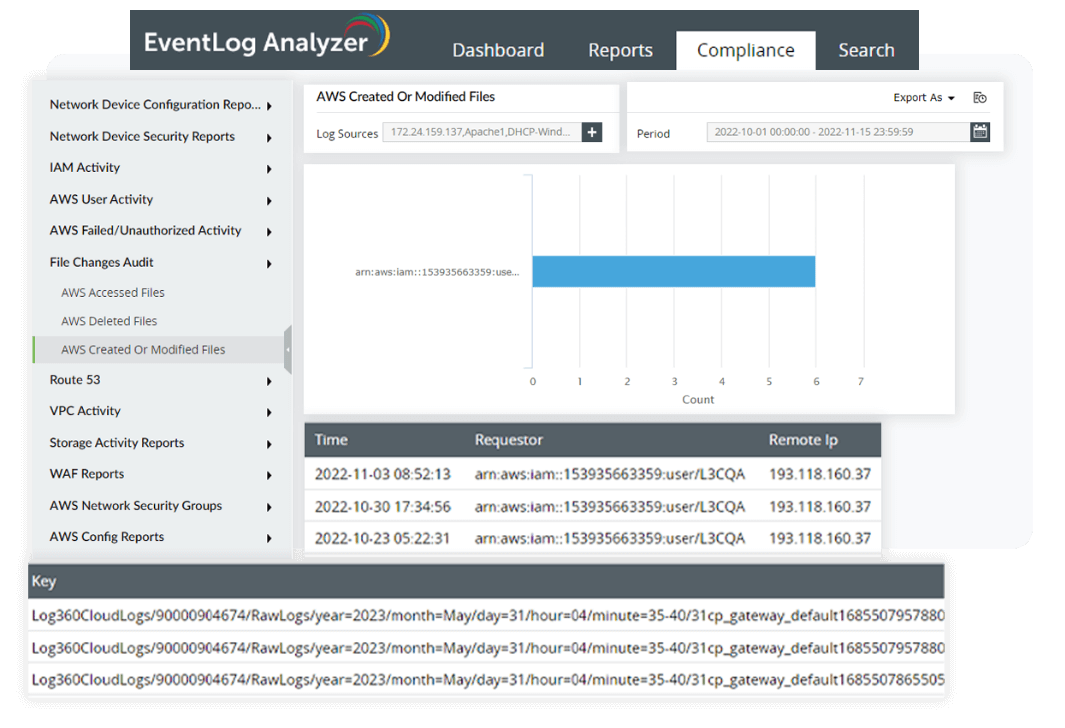
File integrity monitoring secures your organization's data from unauthorized and unwanted modifications, security threats, and breaches. It keeps track of any changes made to files or folders in real time to detect any security incidents quickly and generate alerts to the relevant stakeholder , who can then review the issue and take the necessary steps to resolve it. You can also keep tabs on changes to security privileges, such as permissions, ownership, and others, with the FIM module to comply with PMC 4.
User session monitoring
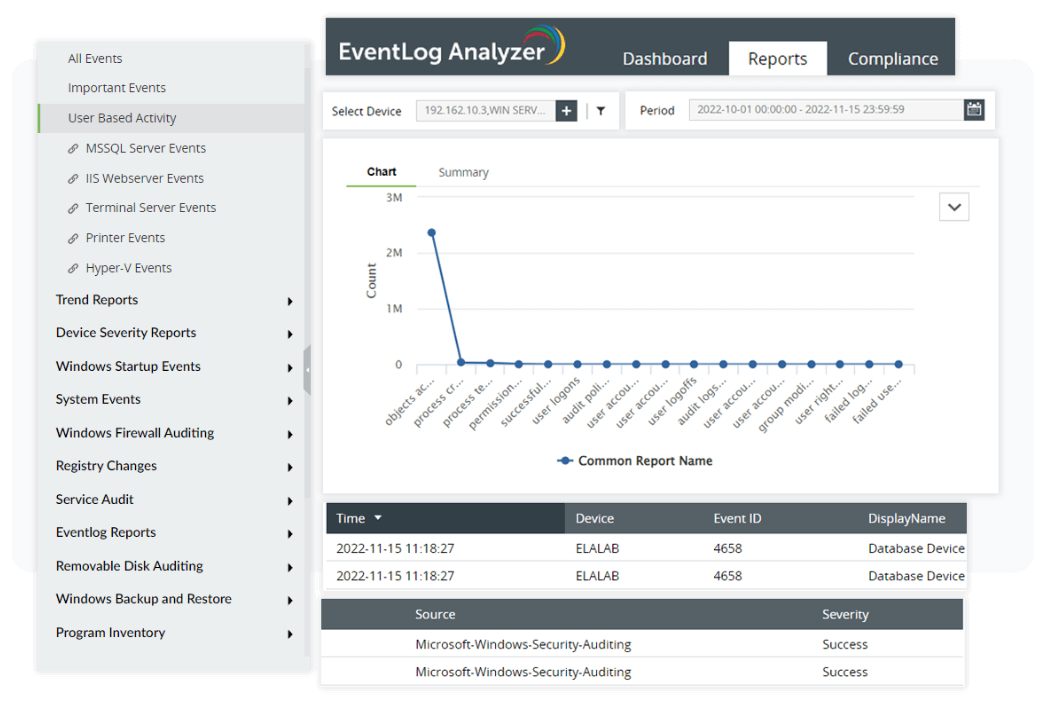
It's important to monitor user activity, as threats can come from internal or external users. EventLog Analyzer's user session monitoring feature helps detect any data misuse by monitoring user activity on the network. It tracks your users' real-time activities and also provides exhaustive reports of all user activities, like user logons, user logoffs, failed logons, or user account changes, that took place after the user logged in. This feature facilitates the recording of user and workstation session activities (PMC 7), as well as detecting suspicious internal network activities (PMC 5).
Incident response
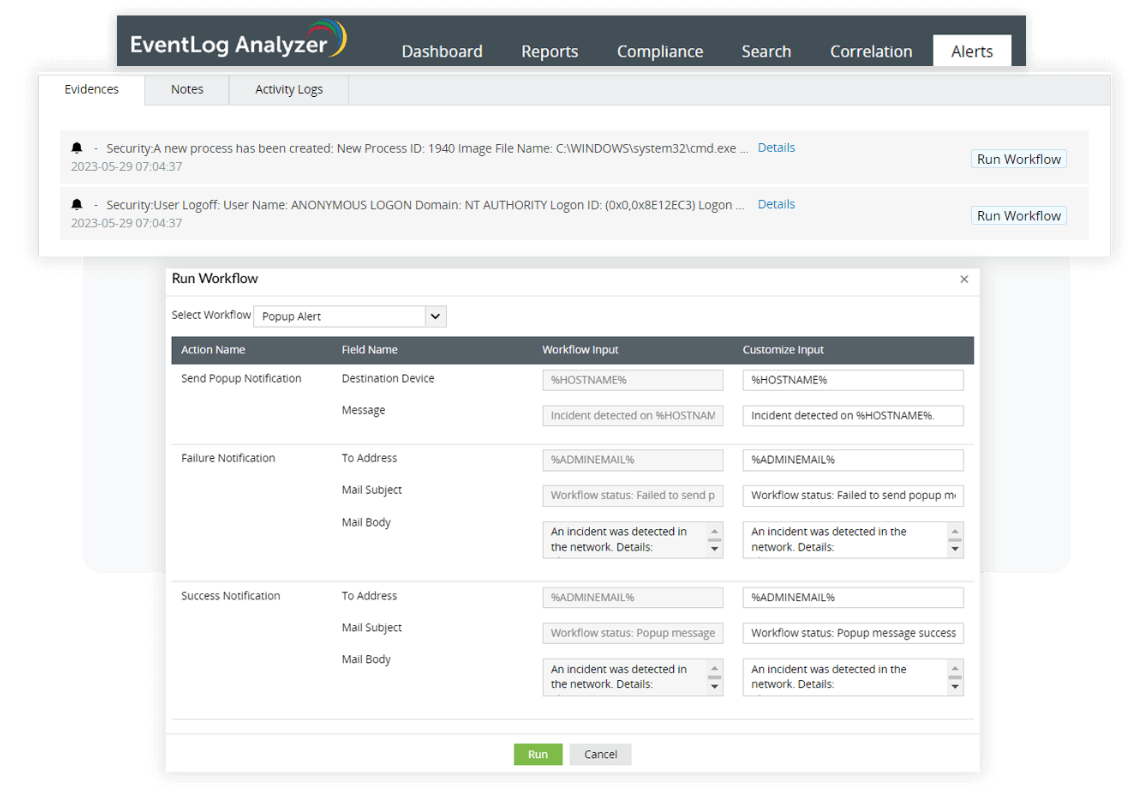
EventLog Analyzer offers a real-time alerts feature with 500 predefined alert criteria or the option of building custom alert profiles tailored to your specific needs. You organization can be alerted of any suspicious event with notifications via email or SMS, helping you meet PMC 9.
Along with real-time alerts, EventLog Analyzer's automated incident response takes the necessary steps to reduce the impact of the attack right after a security incident, before the alerted security personnel takes a closer look. The incident response module has multiple built-in workflows, allowing organizations to save a great deal of time responding to incidents while also minimizing or eliminating potential damage.
How does EventLog Analyzer meet GPG 13 requirements?
| Requirement | How EventLog Analyzer helps with compliance | EventLog Analyzer reports/features |
|---|---|---|
| PMC 1 Accurate time stamp |
Prevents anyone from tampering with log timestamps. | S ecure log storage. |
| PMC 2 Recording of business traffic crossing a boundary |
Records traffic that passes through IIS and Apache web servers in the PMC 2 reports. |
|
| PMC 3 Recording of suspicious activity at the boundary |
Displays all connections that have been denied and possible attacks on network perimeter devices in the PMC 3 reports. |
|
| PMC 4 Recording of internal workstation, server, or device status |
Detects and records any suspicious activity, including configuration changes, privileged access, unexpected system and application restarts, software installation, removable media insertion and removal, and sensitive file access. |
|
| PMC 5 Recording of suspicious internal network activity |
Records policy changes and helps identify if an inside user is carrying out malicious activity. |
|
| PMC 6 Recording of network connections |
Records all Windows, Unix, and network perimeter device logons. |
|
| PMC 7 Recording of session activity of users and workstations |
Tracks entire user sessions from logon to logoff, including details of their activity during the session. |
|
| PMC 8 Recording of data backup status |
Records failed backups and restoration events. |
|
| PMC 9 Alerting when critical events occur |
Sends real-time alerts via email and SMS when any anomalous activity happens in the network. A program can be assigned to run when an alert is generated. | The incident response and management console alerts the users when critical events occur. |
| PMC 10 Reporting on the status of the audit system |
Tracks the clearing of all security logs and event logs. |
|
| PMC 11 Production of sanitized and statistical management reports |
Offers a highly customizable reporting function. Admins can configure existing reports to suit their specific requirements or create new ones. | All predefined reports can be customized and scheduled. |
| PMC 12 Providing a legal framework for protective monitoring activities |
Ensures that all data is collected and analyzed for forensic validity. | Centrally collects, archives, searches, analyzes, and correlates machine-generated logs obtained from heterogeneous systems, network devices, and applications and generates forensic reports. |
Related solutions offered by EventLog Analyzer:
Privileged user monitoring
Track privileged user accounts and detect any suspicious events like unauthorized logons, logon failures, user account changes, user group changes, audit logs cleared, audit policy changes, and access attempts during non-working hours. EventLog Analyzer also provides reports that help to identify user behavior that may indicate privilege abuse.
Learn moreLog archiving
With help of EventLog Analyzer, archive all collected logs and automatically store them securely after the retention period is complete. By configuring the retention period details in EventLog Analyzer, you can adhere to GPG 13, which requires logs to be retained for at least six months.
Learn moreLog forensic analysis
EventLog Analyzer's forensic analysis feature provides organizations with the capabilities necessary to conduct in-depth investigations into security incidents and identify root causes.
Learn moreApplication auditing
Audit all your critical application servers like Apache, IIS, SQL, and other custom applications. The tool collects, analyzes, and correlates any application logs and provides actionable insights about network events.
Learn more










