- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
What is HIPAA?
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal law designed to refine the movement and continuity of health insurance coverage in individual and group markets.
Title I of HIPAA compliance: HIPAA ensures health insurance coverage for employees and their families when there is a shift in or loss of jobs.
Title II of HIPAA compliance: Also known as the Administrative Simplification provisions, this section encourages the electronic exchange of healthcare information. These provisions outline the standards and policies for protecting personally identifiable information maintained by healthcare bodies. They also require the establishment of standards for electronic healthcare transactions and national identifiers for providers, health insurance plans, and employers.
The Omnibus Rule: The Omnibus Rule defines privacy and security requirements for healthcare providers, health plans, and other entities that process health insurance claims. It encompasses requirements for business associates of these entities that hold access to protected health information.
What are the three main rules of HIPAA?
There are three key rules that form the core of HIPAA:
- The privacy rule: It protects the privacy of protected health information (PHI) , balancing patient confidentiality with the need to protect public health.
- The security rule: HIPPA sets forth standards for safeguarding electronic PHI (ePHI). It mandates that covered entities enforce extensive administrative, physical, and technical measures to ensure the security of ePHI.
- The breach notification rule: In situations where there is a breach of unsecured PHI, covered entities along with their business associates are bound to notify the affected individuals, the secretary of health and human services, and in certain circumstances, inform the media.
Related content
HIPAA Compliance management made easy
- Simplify adherence to compliance mandates with a unified log management tool that monitors network logs at a granular level and provides out-of-the-box compliance reports.
- Track all network activities to gain extensive information on data access, privilege abuse, user activity, logons and logoffs, and more.
- Receive instant email or SMS alerts on anomalies, data breaches, and compliance violations to mitigate security threats as soon as possible.
Learn how EventLog Analyzer simplifies HIPAA compliance demonstration
Object access auditing
Monitor and review access to electronic protected health information and satisfy HIPAA's object access auditing clause with EventLog Analyzer's file integrity monitoring. The solution provides in-depth reports on actions performed in sensitive files or folders, changes in access control, user and system details, and the status of these operations. This helps network administrators identify insider threats, audit privileged user activity, and prevent insider attacks.
Logon and logoff monitoring
Implement procedures to monitor login attempts and report discrepancies and possible abuse with a comprehensive log management solution. EventLog Analyzer satisfies HIPAA's logon and logoff audit requirements with its out-of-the-box reports. Gain details about successful or failed login attempts; usernames, dates, times, and reasons for events; terminal server session statuses; and more with these reports. Monitoring these activities in real time is also a proactive measure to mitigate breach attempts at the intrusion stage.
System events auditing
Adhere to HIPAA's system events audit requirement and ensure network security by monitoring system activities. EventLog Analyzer identifies and provides readily available reports on local system processes, like system startup or shutdown or changes to the system time or audit log. Additionally, the solution also maintains audit log records by parsing, analyzing, and archiving them securely. You can make use of the EventLog Reports to address section 164.308 (a) (3) of HIPAA.
User account validation auditing
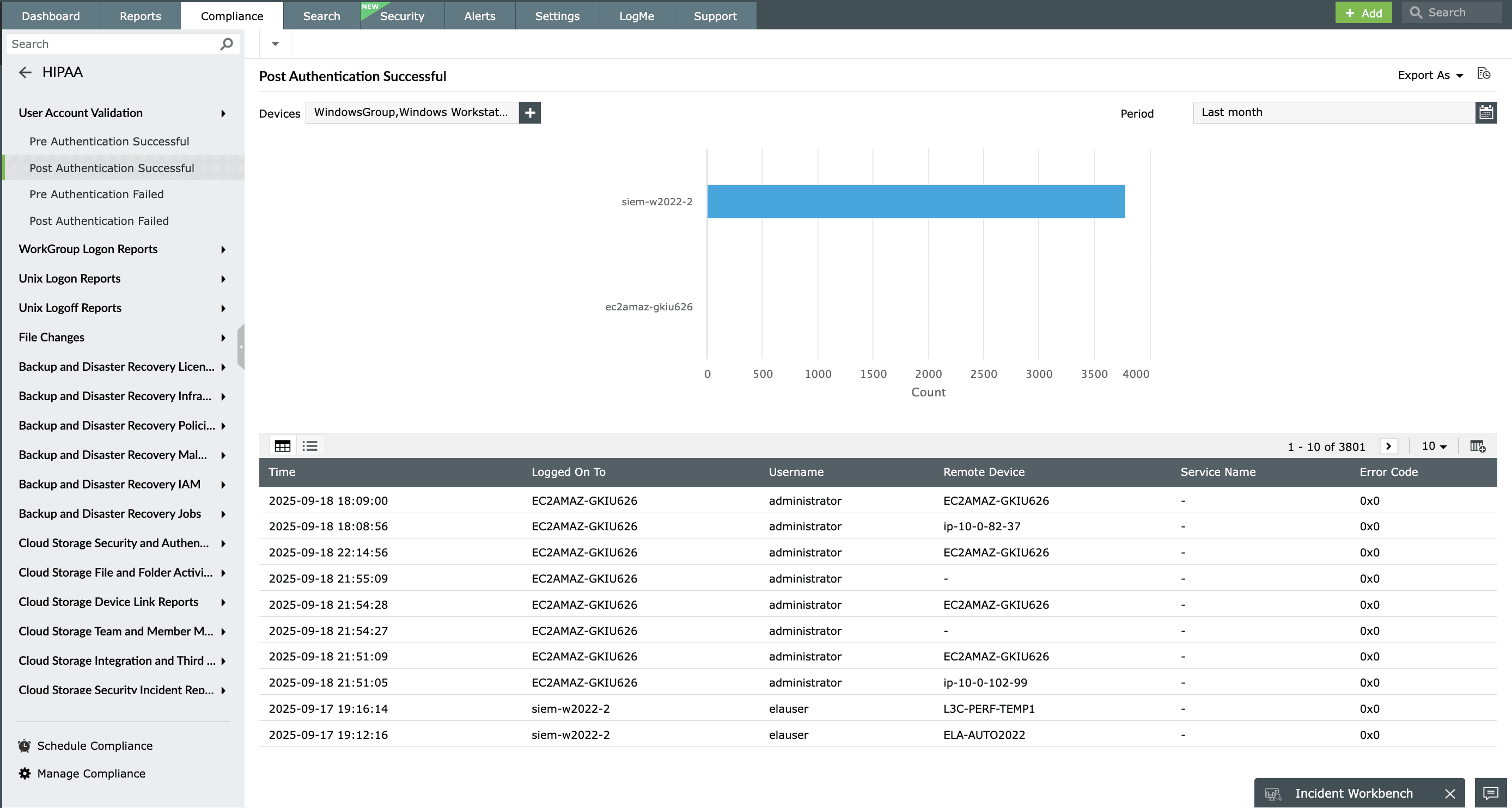
Satisfy HIPAA's user account validation clause, which mandates the implementation of procedures for monitoring the authorization and supervision of user accounts with access to confidential patient health information. EventLog Analyzer audits successful and unsuccessful user account logon events, which are generated when a domain user account is authenticated on a domain controller. The User Account Validation reports give you detailed insights on the pre-authentication and post-authentication statuses.
Become HIPAA compliance ready with EventLog Analyzer
| HIPAA compliance | EventLog Analyzer reports |
|---|---|
| Sec 164.306 (a) (1) "Ensure the confidentiality, integrity, and availability of all electronic protected health information the covered entity or business associate creates, receives, maintains, or transmits." |
|
| Sec 164.306 (a) (1) (i) "Implement policies and procedures to prevent, detect, contain, and correct security violations." |
|
| Sec 164.308 (a) (1) (ii) (D) "Implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports." |
|
| Sec 164.308 (a) (3) (ii) (A) "Procedures for the authorization and/or supervision of workforce members who work with electronic protected health information or in locations where it might be accessible." |
|
| Sec 164.308 (a) (4) (ii) (B) "Policies and procedures for granting access to electronic protected health information, for example, through access to a workstation, transaction, program, process, or other mechanism." |
|
| Sec 164.308 (a) (5) (ii) (C) "Procedures for monitoring log-in attempts and reporting discrepancies." |
|
| Sec 164.308 (a) (6) (ii) "Identify and respond to suspected or known security incidents; mitigate, to the extent practicable, and document security incidents and their outcomes." |
|
| Sec 164.308 (a) (7) (i) "Policies and procedures for responding to an emergency or other occurrence that damages systems that contain electronic protected health information." |
|
What else does EventLog Analyzer provide?
A powerful correlation engine
Detect network anomalies and trace security threats with a powerful correlation engine that holds over 30 predefined correlation rules and a drag-and-drop custom rule builder.
Learn moreIn-depth auditing and reporting
Audit every entity in your network and obtain a detailed overview of what's happening in the network in the form of intuitive dashboards and reports.
Learn moreAutomated incident management
Assign tickets in an external help desk console for security events of interest to speed up incident resolution.
Learn moreAugmented threat intelligence
Detect malicious IP addresses, URLs, or domain interactions with the built-in global IP threat intelligence database and STIX/FEED processor.
Learn moreFrequently asked questions
HIPAA is designed to secure the protected health information of patients. This includes all individually identifiable health details like test results, medical history, insurance details, demographic data, and other details specific to a patient and their healthcare services.
EventLog Analyzer is a unified log management solution that automates log collection and parsing, analyzing, correlating, and archiving your network's log data. The solution makes sense of the network activities and presents them in the form of intuitive dashboards and reports. EventLog Analyzer's in-depth auditing capabilities address IT compliance mandates like HIPAA by monitoring sensitive object access, user account behavior, logon and logoff events, and more. The solution also supports other common compliance mandates.
EventLog Analyzer provides instant alerts when any compliance violation is identified in the network. The comprehensive reports provided by the solution simplify compliance management.











