| Article |
Compliance aspect |
Reports |
| 16.3, 13.6 |
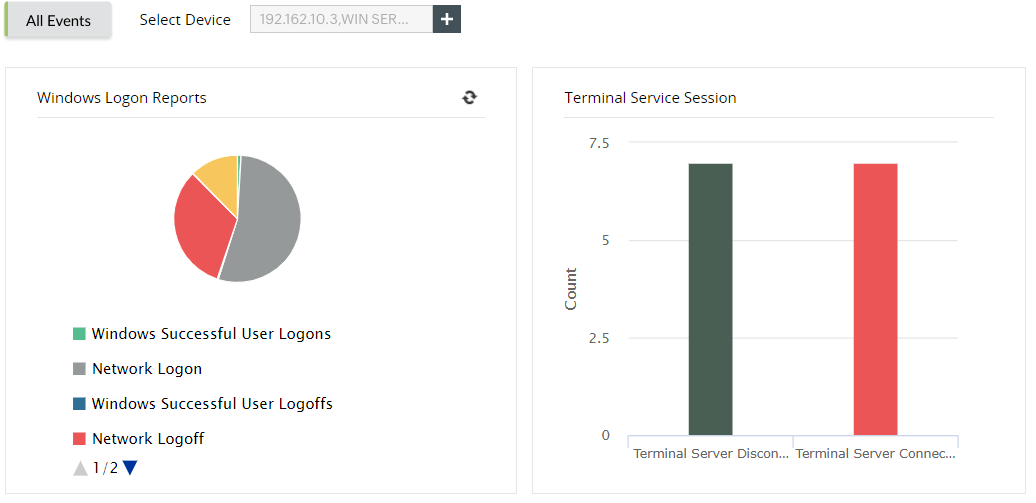
Logons |
- Successful user logons
- Successful user logoffs
- Unsuccessful user logons
- Terminal service session
|
| 12, 13, 19.3, 30.4, 30.6, 20.5 |
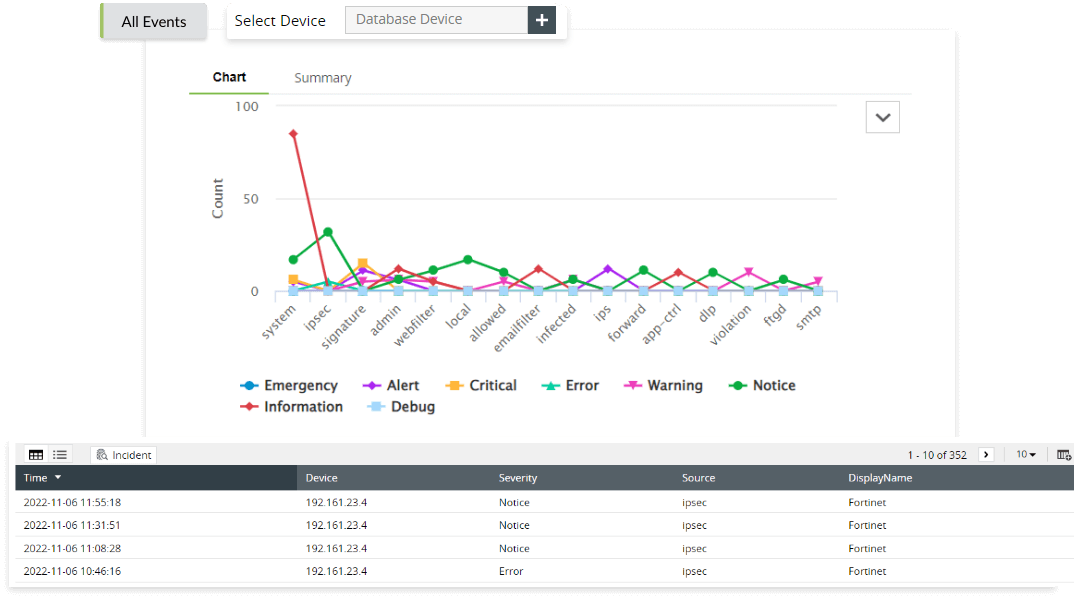
Object accesses |
- Object accessed
- Object created
- Object modified
- Object deleted
- Object handled
|
| 16.3, 18.1, 19.3, 30.6 |
User accesses |
|
| 16.3, 18.1, 19.3, 30.6 |
Policy changes |
- User policy changes
- Domain policy changes
- Audit policy changes
|
| 20.2, 20.3 |
Firewall logons |
- FortiNet failed logons
- FortiNet failed VPN logons
- SonicWall failed VPN logons
- SonicWall denied connections
- PaloAlto failed logons
- PaloAlto denied connections
- Huawei failed logons
- Huawei denied connection
|
| 20.2, 20.3, 20.10 |
Firewall attacks |
- FortiNet possible attacks
- FortiNet critical attacks
- SonicWall critical attacks
- SonicWall website traffic
- PaloAlto possible attacks
- PaloAlto critical attacks
- Huawei possible attacks
|
| 20.2, 20.3, 20.10 |
Firewall attacks |
- FortiNet possible attacks
- FortiNet critical attacks
- SonicWall critical attacks
- SonicWall website traffic
- PaloAlto possible attacks
- PaloAlto critical attacks
- Huawei possible Attacks
|
| 18.1, 20.1, 20.3 |
Firewall configurations |
- FortiNet configuration changes
- FortiNet commands failed
|
| 16.3, 30.6 |
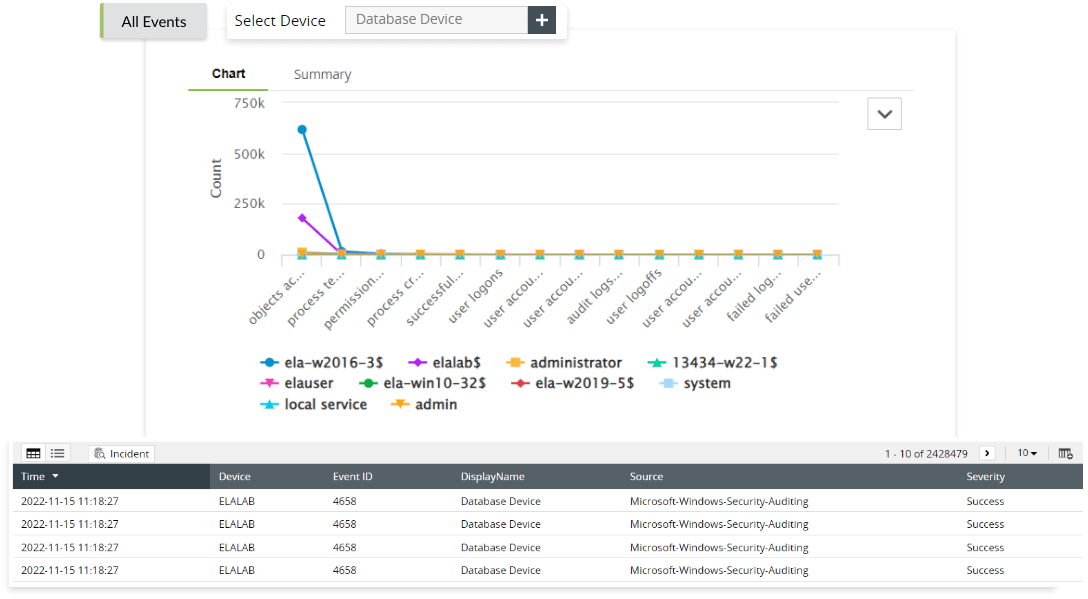
Account logon |
- Successful user account validation
- Unsuccessful user account validation
|
| 18.1 |
Account management |
- User account changes
- Computer account changes
- User group changes
|
| 12, 13, 19.3, 30.4, 30.6, 20.5 |
Microsoft SQL/Oracle DDL changes |
- Microsoft SQL database created
- Microsoft SQL database deleted
- Microsoft SQL table created
- Microsoft SQL table dropped
- Microsoft SQL procedure created
- Microsoft SQL procedure deleted
- Microsoft SQL schema dropped
- Microsoft SQL schema modified
- Oracle database created
- Oracle database deleted
- Oracle table deleted
- Oracle table modified
- Oracle procedure created
- Oracle procedure deleted
- Oracle cluster deleted
- Oracle cluster modified
|
| 12, 13, 19.3, 30.4, 30.6, 20.5 |
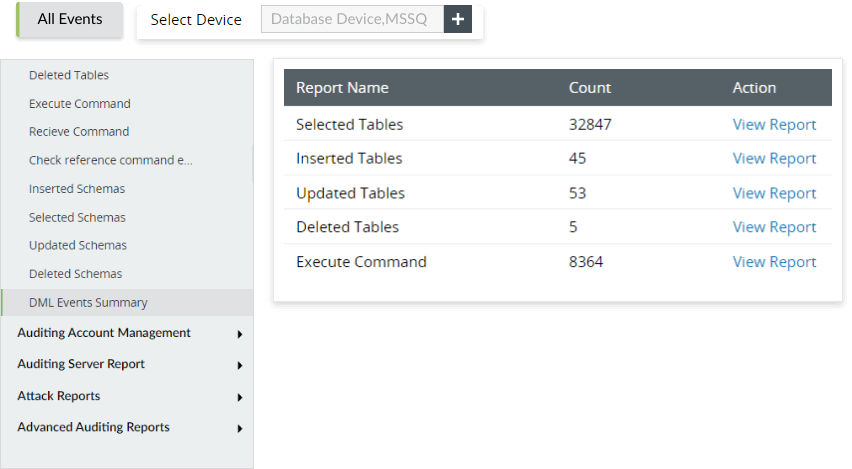
Microsoft SQL/Oracle DML changes |
- Microsoft SQL table updated
- Microsoft SQL table deleted
- Microsoft SQL execute command
- Microsoft SQL receive command
- Microsoft SQL schema updated
- Microsoft SQL schema deleted
- Oracle table inserted
- Oracle table deleted
- Oracle procedure altered
- Oracle trigger created
- Oracle trigger deleted
|
| 12, 13, 19.3, 30.4, 30.6, 20.5 |
Microsoft SQL/Oracle security changes |
- Privilege abuse
- Unauthorized copy
- Account lockouts
- SQL injection
- Denial of service
- Oracle SQL injection
- Oracle failed logons
- Oracle account lockouts
- Oracle denial of service
|
| 12, 13, 19.3, 30.4, 30.6, 20.5 |
Printer reports |
- Printer documents printed
- Printer documents deleted
- Printer paused documents
- Printer corrupted documents
- Printer insufficient privilege to print
|