- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
An enterprise network consists of numerous log sources. Centrally monitoring these log sources can help keep data threats and cyberattacks at bay. A comprehensive log monitoring solution like EventLog Analyzer can automate log management processes, identify malicious activities by correlating logs, and help meet IT compliance requirements.
Here's how EventLog Analyzer helps with different types of log monitoring:
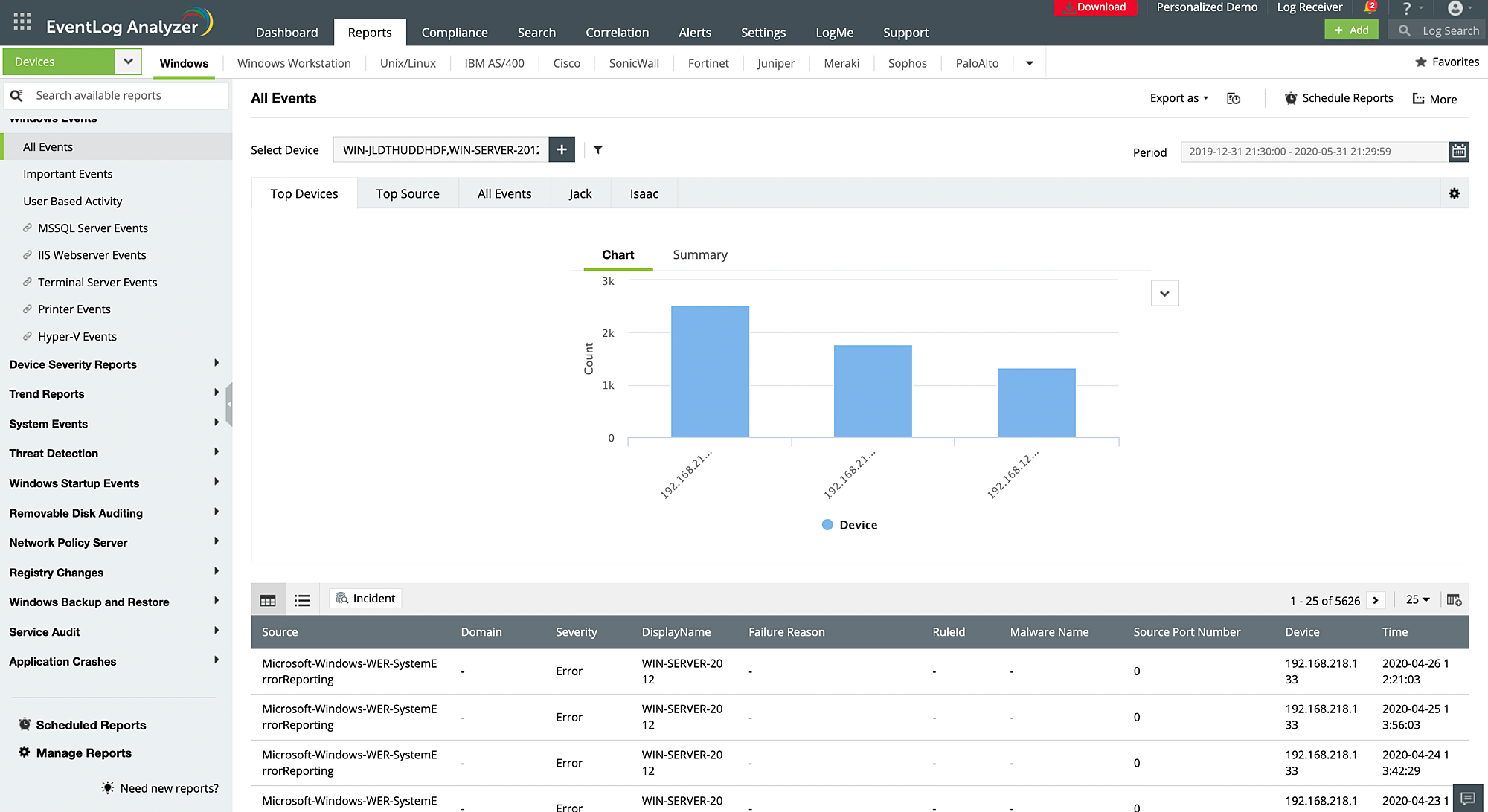
Windows event log monitoring
Auto-discover and collect Windows log sources in your network with EventLog Analyzer. The event log monitoring solution detects Windows devices, workstations, servers, and operating systems to conduct in-depth auditing and generate reports that can help you comprehend logs with security information. You will find detailed, out-of-the-box reports about user activities, Windows startup or shutdown events, device severity, system events, registry changes, access denial, threat detection, and more.
EventLog Analyzer also tracks critical Windows event IDs to spot anomalies, malicious activities, and data breaches at the initial stages to avoid cyberattacks. You can also track Windows Sysmon logs to gain information regarding network connection process creation, and modifications made to file creation time.
Syslog monitoring
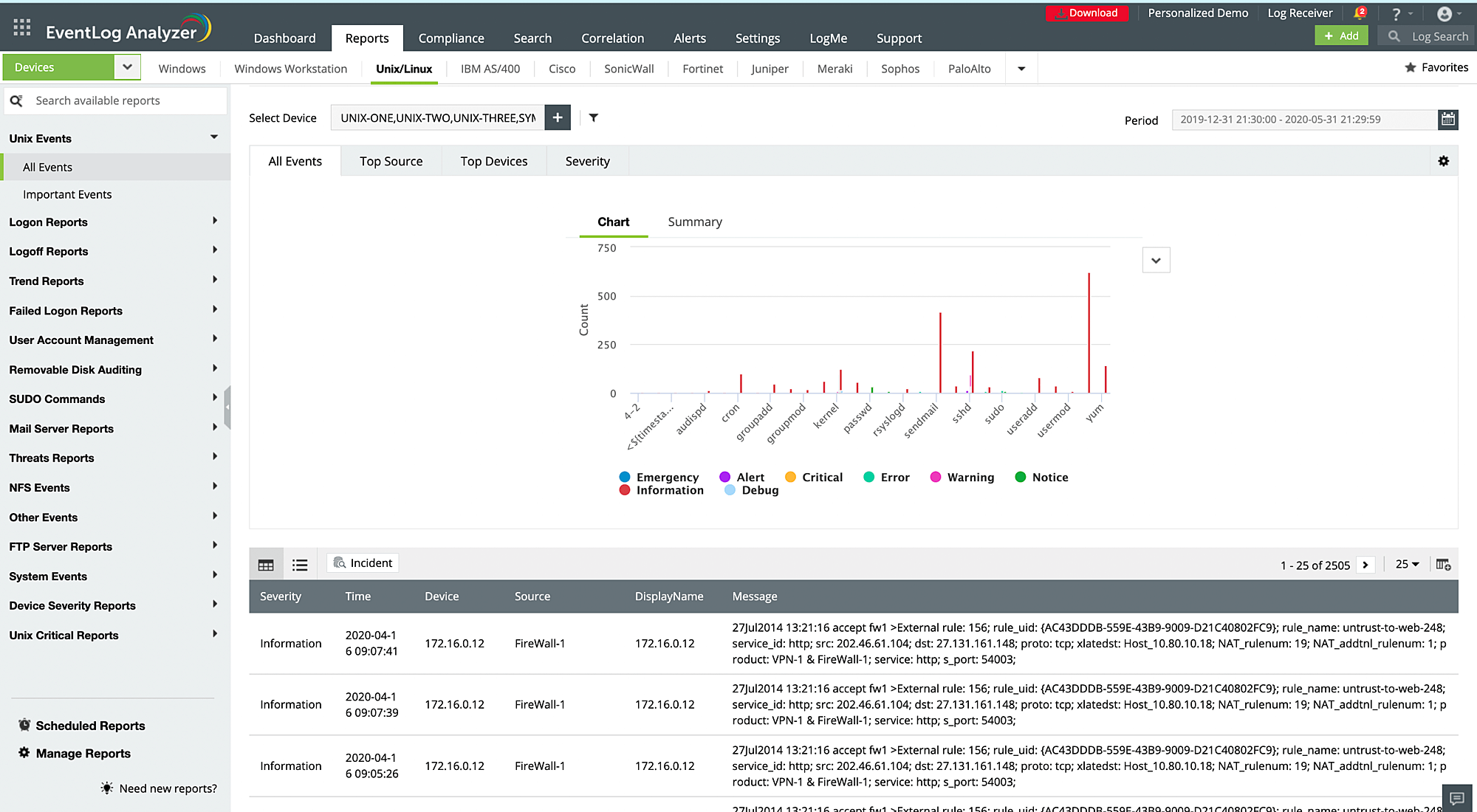
Collect and monitor syslogs from Linux and Unix-based systems, routers, switches, and firewalls in real time with EventLog Analyzer. The syslog monitoring solution functions like a syslog daemon or a syslog server, collects syslog messages by listening to the UDP syslog ports of selected devices, analyzes the collected logs, and provides insights in the form of reports. You can also use the solution's syslog forwarder to receive the logs and send the data to third-party servers.
The syslog reports provided by EventLog Analyzer give you insights on failed and successful logon and logoff attempts, executed SUDO commands, user account management, Unix critical reports, risk trends, FTP server events, NFS events, device severity reports, and more. These reports can help you secure your devices from insider threats and external breach attempts, and reduce troubleshooting time.
Network log monitoring
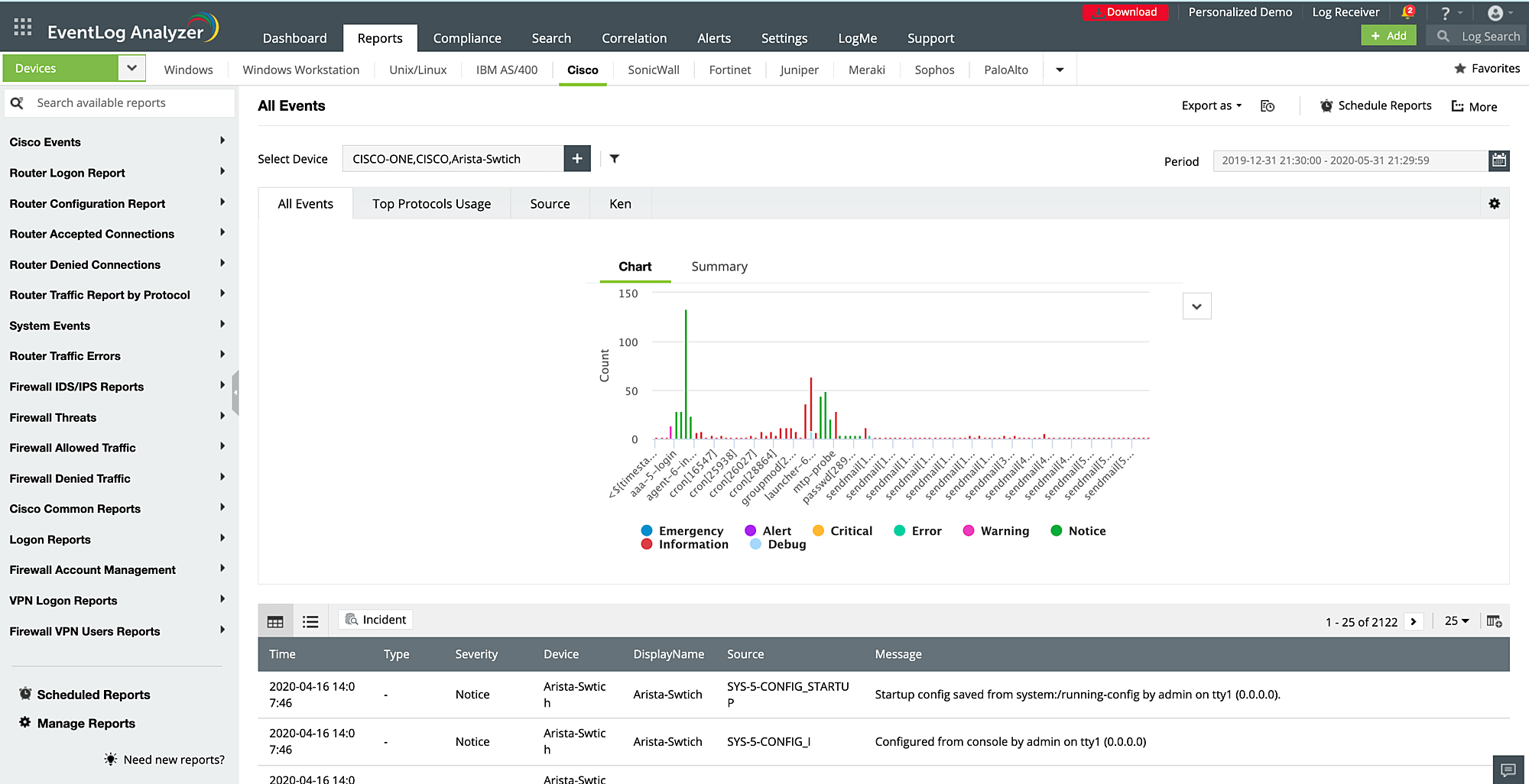
Keep track of the activities in your network devices with EventLog Analyzer's network device monitoring. The solution safeguards perimeter network devices such as firewalls, routers, switches, and IDSs and IPSs from intrusions.
EventLog Analyzer monitors and reports on traffic, configuration changes, logon activities, allowed and denied connections, VPN logons and usage, security threats along with the user and source details, and more. You can view these reports by log source and schedule them to be emailed to you periodically. This real-time monitoring will help you identify malicious incoming traffic, unauthorized access, user account changes, privilege escalations, failed logon attempts, and more.
Application log monitoring
Audit business-critical applications in your network to gain detailed reports on operational and security vulnerabilities. EventLog Analyzer manages logs from database platforms, web servers, DHCP servers, file servers, and mail servers, including MS SQL servers, Oracle servers, Apache web servers, IIS web servers, and MySQL logs.
The reports provided by this application log monitoring tool help you detect application-related threats like SQL injection, DoS attacks, port scanning attacks, and unauthorized access to accounts with sensitive corporate data. The solution accomplishes this by tracking server activities, DDL or DML changes, malicious URL requests, server errors, usage patterns, logon and logoffs, etc.
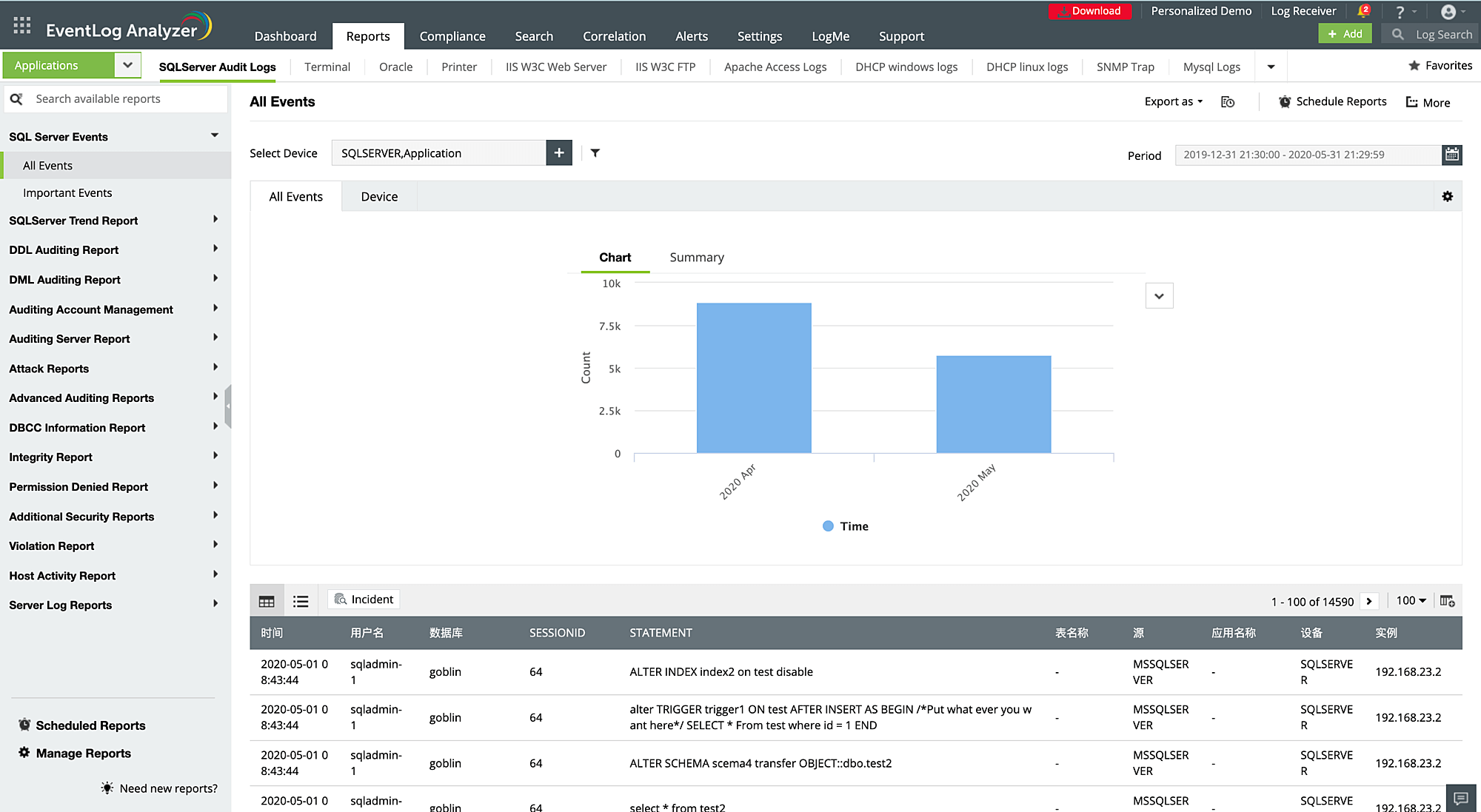
Other supported log formats
EventLog Analyzer servers as centralized log monitoring and analysis software that accounts for logs from other sources in your network like SNMP traps, vulnerability scanners, terminal servers, print servers, virtual machines, and endpoint solutions. By bringing all your logs in a single console, this solution gives you an exhaustive overview of your network activities to improve your security posture and prevent attacks. You can view all the supported data sources here.
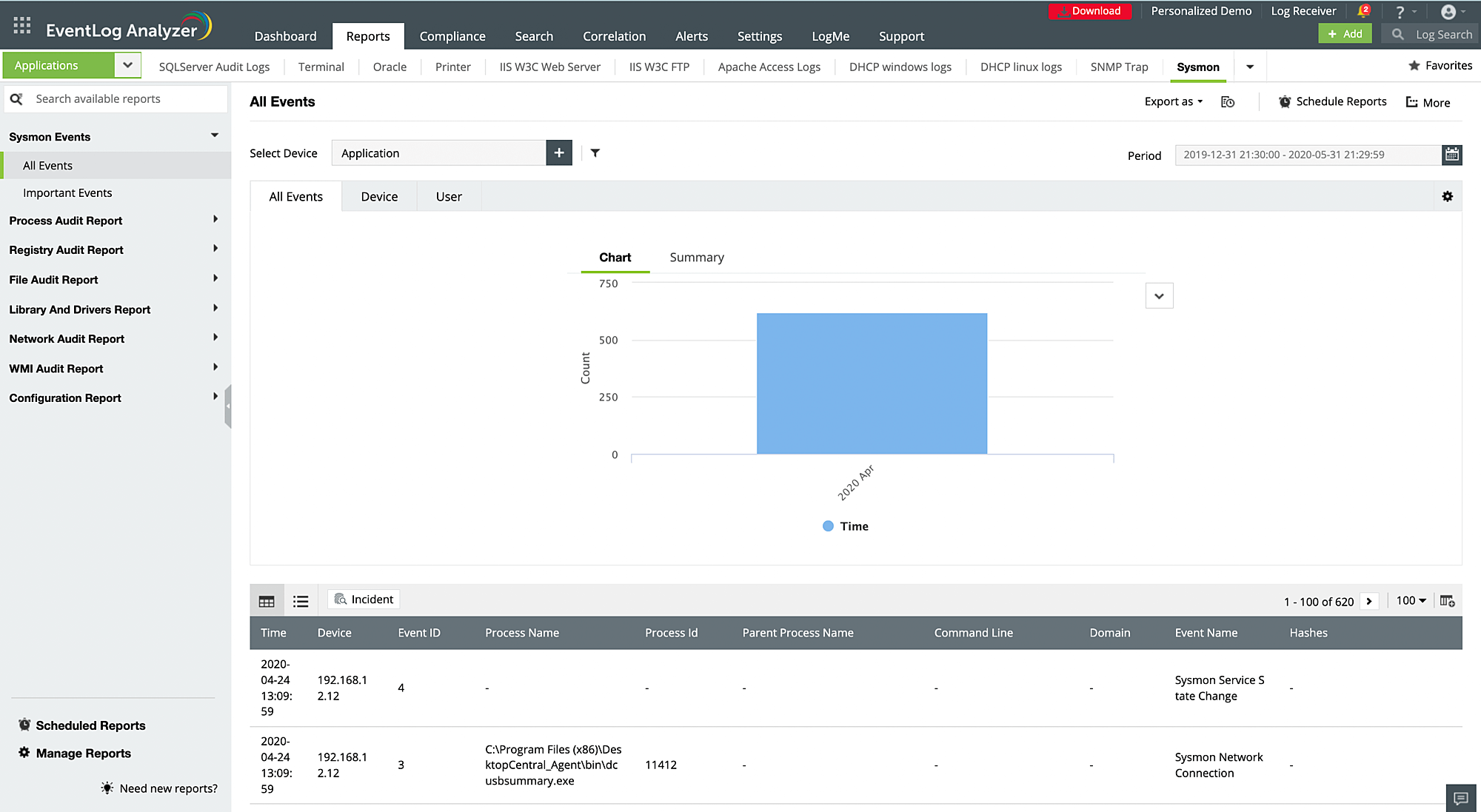
Other solutions offered by EventLog Analyzer
Privileged user monitoring
Identify privileged user abuse by monitoring the activities of users with access to business-critical information.
File integrity monitoring
Monitor sensitive files and folders in your network by auditing object access and modifications.
Threat analytics
Spot threats by analyzing malicious IPs, URLs, and domains that interact with your network.
IT compliance management
Adhere to IT compliance regulations like the GDPR, PCI DSS, HIPAA, and SOX with audit-ready reports generated based on real-time network auditing.