- Home
- Logging Guide
- How to detect and prevent a TCP 445 exploit and attack using firewall log analysis?
How to detect and prevent a TCP 445 exploit and attack using firewall log analysis?
In this page
- What is the use of port 445?
- How do attackers exploit port 445?
- How to detect a 445 port exploit by analyzing firewall logs?
- Leveraging ManageEngine EventLog Analyzer to prevent port 445 exploits
The US-CERT advisory reveals that the best practice to follow for Server Message Block (SMB) is to block TCP port 445, used by Microsoft Directory Services along with UDP ports 137, 138 and TCP port 139.
Port 445 was exploited in 2017 by the WannaCry ransomware attack, which caused huge damage across the globe targeting businesses, banks and other public bodies.
What is the use of port 445?
Port 445 is a Microsoft networking port which is also linked to the NetBIOS service present in earlier versions of Microsoft Operating Systems. It runs Server Message Block (SMB), which allows systems of the same network to share files and printers over TCP/IP.
This port shouldn't be opened for external network. All microsoft devices mostly have port 445 open as the port is used for LAN communication.
How do attackers exploit port 445?
The attackers can perform port scanning using open source tools like Nmap, Metasploit, and NetScan Tools Pro. These scanning tools identify the services that utilize port 445 and gather critical information about the devices. After getting to know the device details, the attackers launch malware and ransomware attacks by exploiting this port.
Prevention of port 445 exploit:
The best way to prevent port 445 exploit is to ensure that your firewall is configured properly and there are no unnecessary 445 open ports in your network.
Steps to prevent port 445 exploit:
Make sure port 445 is blocked in all unused devices and in devices that have connectivity outside your network.
How can you do this? Create a firewall rule as mentioned below:
- Source: Any (or External, if you want to use the port for file sharing within the network).
- Source Port: Any
- Destination: Any
- Destination Port: 445.
- Action: Drop or Deny.
How to detect a 445 port exploit by analyzing firewall logs?
Port 445 exploit can be detected using network security solutions such as Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), and also by security information and event management (SIEM) solutions. Monitor firewall logs and see if they indicate:
- Outbound traffic for SMB v1's ports TCP 445 and 139.
- If port 445 is unresponsive for a long time (could be a stealth attack).
- Multiple port scanning requests to UDP ports 137 and 138.
These events indicate a 445 port exploitation targeted on the system. When you see these indicators in your network, block all 445 ports and conduct investigation to identify the target systems.
Leveraging ManageEngine EventLog Analyzer to prevent port 445 exploits
ManageEngine EventLog Analyzer is a comprehensive log management solution that collects, monitors, analyzes, and archives logs from network devices on your network, including port 445. EventLog Analyzer utilizes its correlation engine and real-time alerts to detect systems from suspicious SMB traffic patterns and authentication attempts to port 445.
EventLog Analyzer's out-of-the-box reports summarizes findings related to denied connections on port 445. These reports visually categorizes network traffic based on sources, destinations, protocols, and ports, along with timestamps. This enables security administrators to track and analyze network traffic patterns to effectively hunt down threat actors trying to sabotage your network.
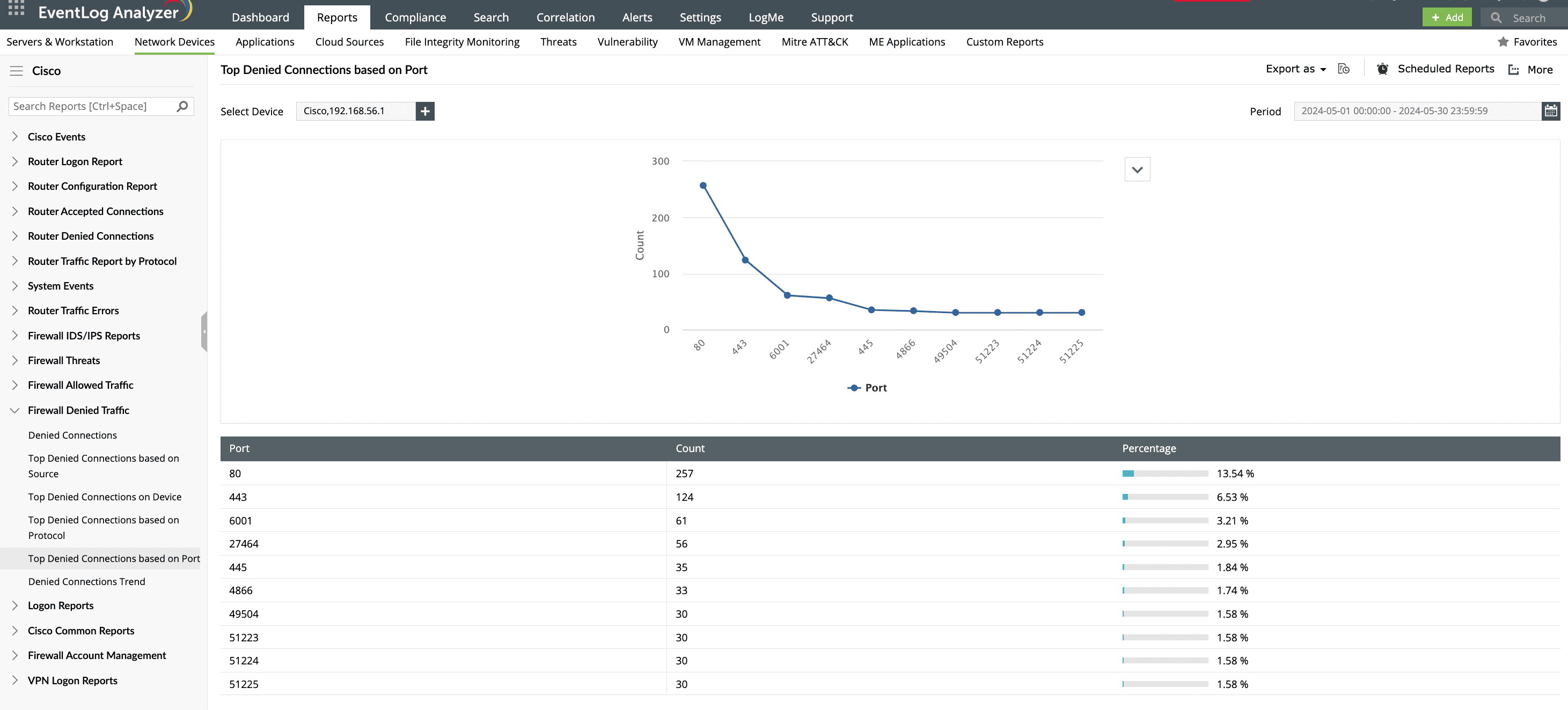
The denied connections report provides insight into any blocked access attempts targeting port 445. This report also helps gain visibility into the high frequency of such questionable attempts, especially within a short time frame, enabling you to detect potential brute-force attacks.
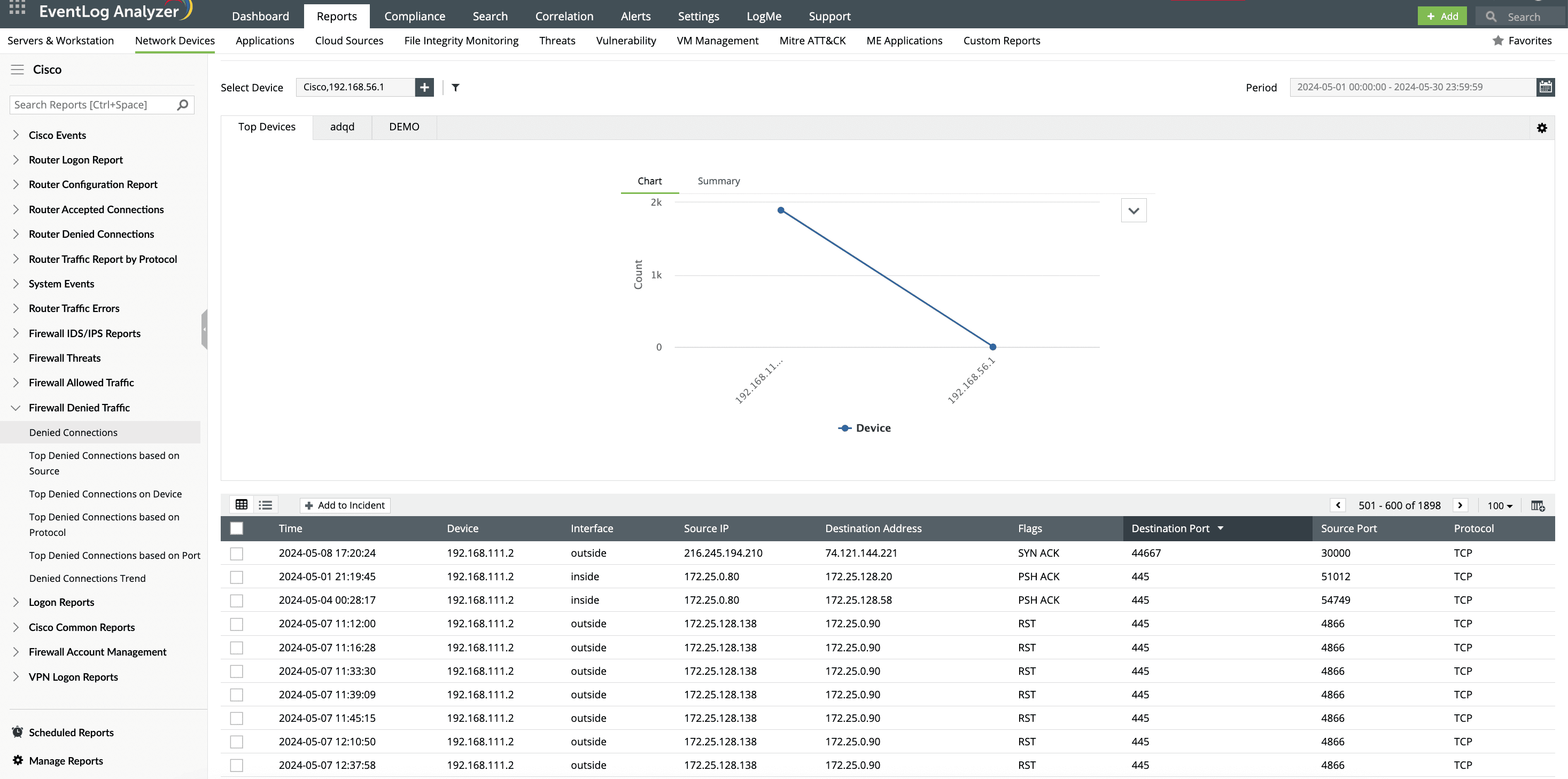
EventLog Analyzer can correlate security logs with network and application logs to provide a comprehensive view of potential threats. This correlation helps in identifying whether the denied connections align with other suspicious activities, such as unusual outbound traffic or logins within a short time frame involving port 445.
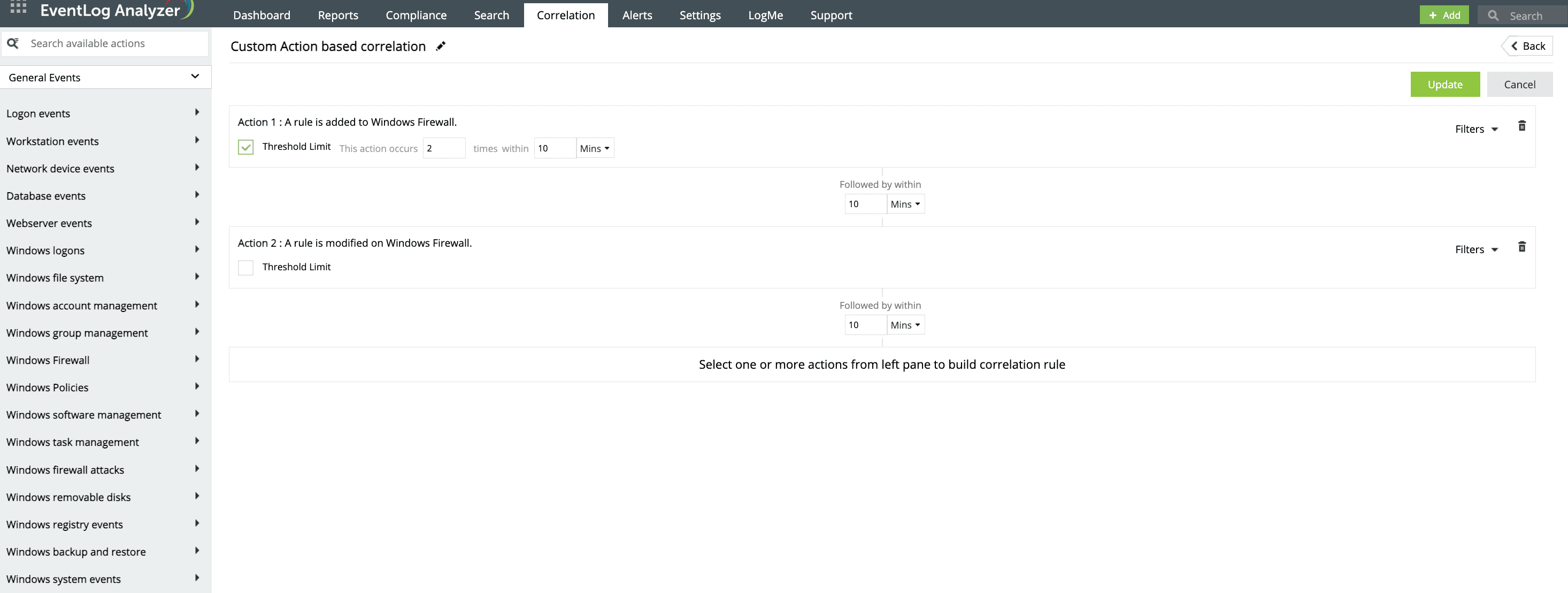
EventLog Analyzer enables you to set up alerts for any suspicious activity related to port 445. It identifies where the attack originated within the network and the network resource that was compromised during the exploit attempt.
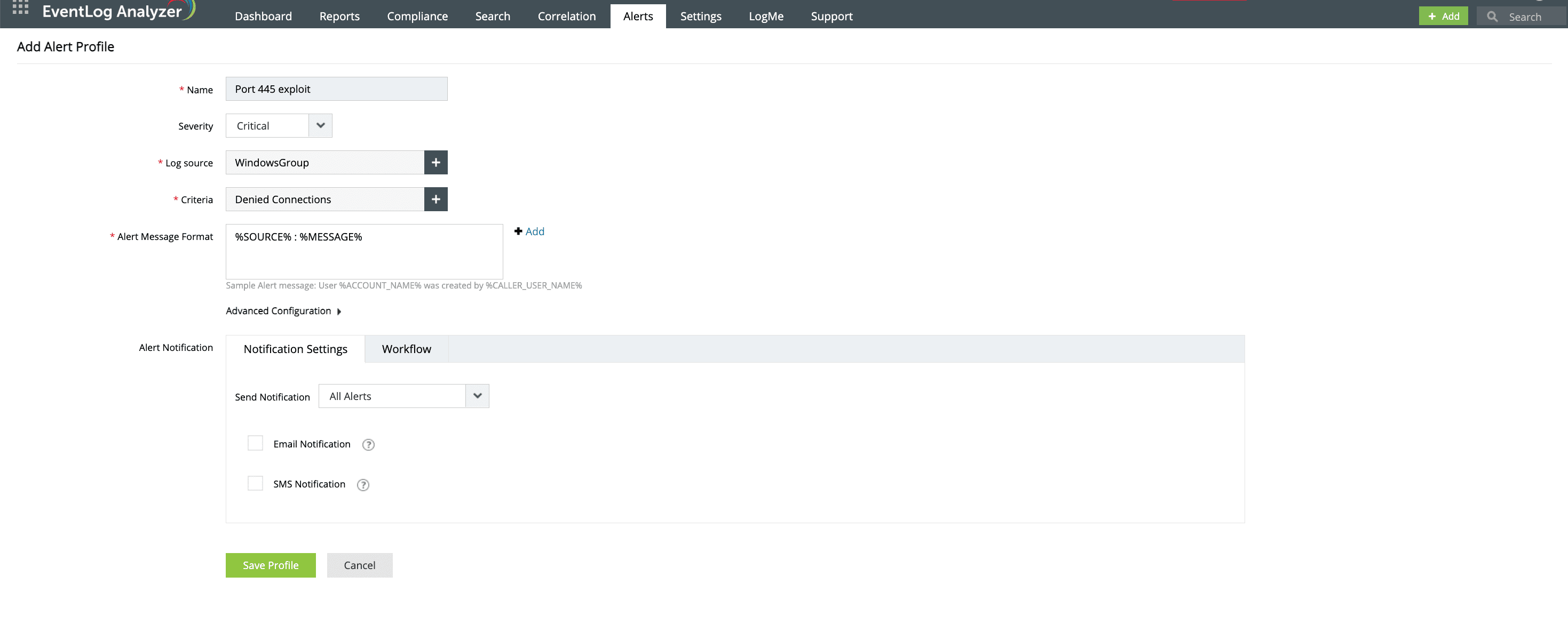
When an exploit is detected, it triggers real-time alerts to notify security administrators immediately, allowing for blocking malicious IP addresses, adjusting firewall rules, and conducting thorough investigations following an alert.











