What is vulnerability management?
Vulnerability management is a continual process of scanning, detecting, analyzing, and remediating security vulnerabilities in software, applications, and endpoints in a network.
Vulnerability management is vital to endpoint security and is one of the most proactive approaches to weed out security weaknesses before they lead to a breach. In this article, we'll discuss the basics of vulnerability management and step-by-step remediation using a vulnerability management tool.
In this article, we'll cover:
- Why do you need vulnerability management?
- What are the challenges in vulnerability management?
- Benefits of vulnerability management
- What are the 4-steps of vulnerability management?
- Vulnerability management with Vulnerability Manager Plus
- Benefits of opting for Vulnerability Manager Plus
- Frequently asked questions on vulnerability management
Why do you need vulnerability management?
According to a Forrester report:
On top of that, over 38,500 vulnerabilities have been disclosed in 2024 so far, a steep 34% increase since 2023 - highlighting the importance for organizations to include vulnerability management and vulnerability remediation to improve their security posture.
Before implementing vulnerability remediation in your enterprise, it is imperative to understand the current landscape and the challenges faced in vulnerability management.
What are the challenges in vulnerability management?
In most organizations, there are literally too many vulnerabilities to track manually, and not all of them pose equal risk. Now, imagine tracking multiple vulnerabilities across thousands of heterogeneous assets in a distributed network. With the window between disclosure of vulnerabilities and their exploit by malicious actors shrinking, organizations need to be swift in their remediation.
With limited time and resources and without the risk background necessary to prioritize issues, your vulnerability management efforts may be futile. Adding to this, many vulnerability management tools in the market offer patching through a third-party integration, but juggling multiple tools for vulnerability assessment and patch management results in a fragmented and inefficient workflow.
If a malicious actor does use a vulnerability as a gateway into the network, it's the overlooked misconfigurations that they'll leverage to laterally move and exploit other machines within the network. This is why every loophole must be addressed along with software vulnerabilities to gain a strong security strategy and minimize the attack surface.
While issuing vendor-published patches to affected machines is the ideal remediation option, having a fail-safe plan to retreat to in case of unpatchable circumstances such as end-of-life software and zero-day vulnerabilities is essential.
Benefits of vulnerability management
With the exponential rise in the number of vulnerabilities in the last few years, the cyber forefront of organizations is at extreme risk. All that the threat actors need is one vulnerability exploitation, which is enough to land your enterprise into a tangle of cyber compliance fines and lost business.
If you're unsure how vulnerability management and timely vulnerability remediation can benefit your network, read below:
- Improved visibility and control over the managed endpoints, ensuring hardened security against exploits. Regular scans and patching schedules by vulnerability management tools can help identify vulnerabilities and weaknesses in the network.
- Efficient cyber-risk management, thereby negating human errors such as unrequired open ports, weak passwords, and so on.
- Streamlined operations by reducing downtime, data protection, and lesser recovery time, in the case of an exploit.
- Adhering to regulatory compliances with continual scanning, regular patching, in-depth reports, and enhanced audits.
What are the 4-steps of vulnerability management?
Vulnerability management, being a continual process works best when automated using a vulnerability management tool. Explained below are the 4-steps of vulnerability management.
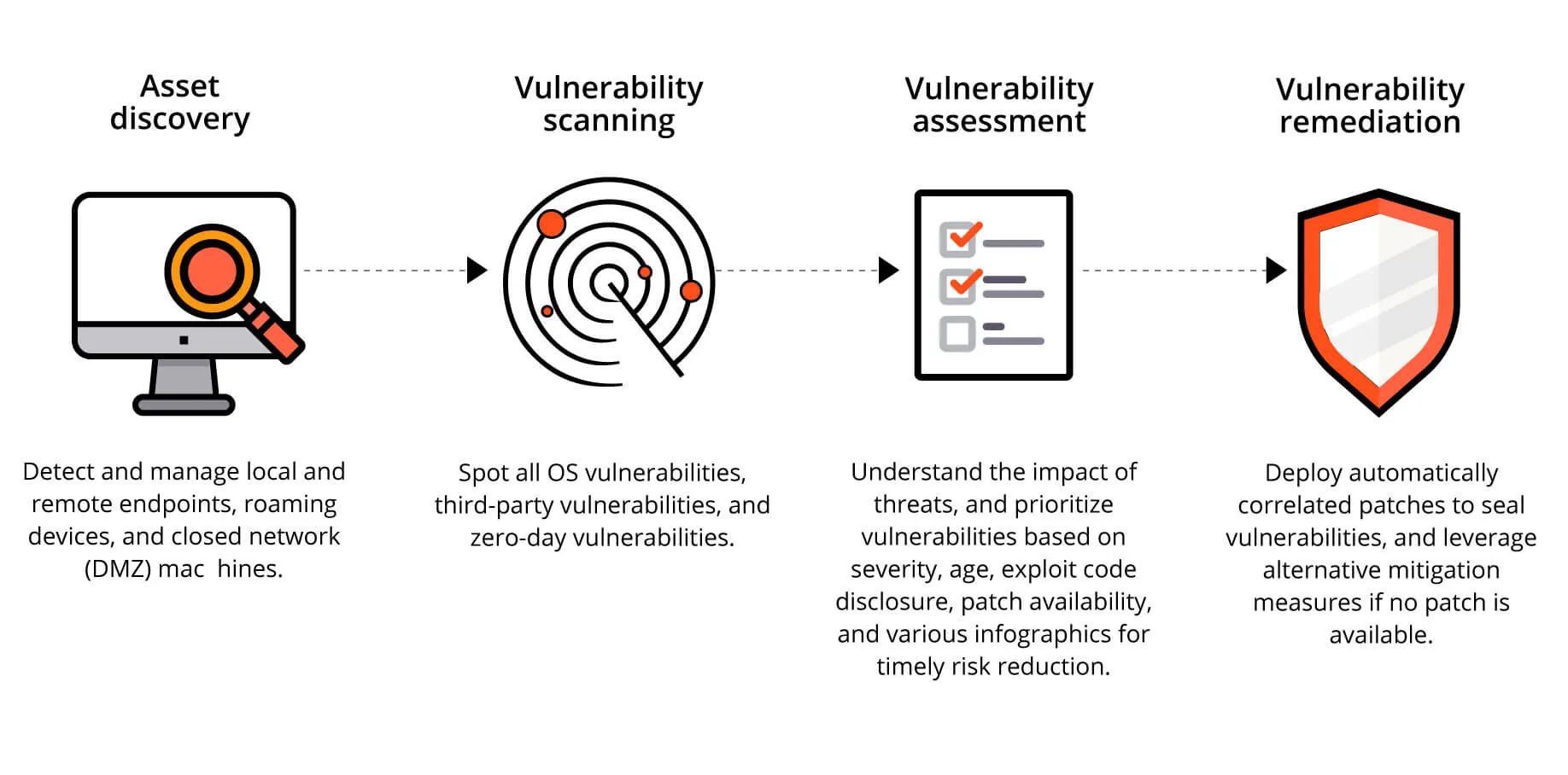
Step 1: Asset Discovery
The asset scanning module of the vulnerability management software scans the network for newly added endpoints. On an endpoint level, it scans them to add or modify any newly added software or applications.
Step 2: Vulnerability Scanning
The network endpoints and installed applications are periodically scanned for vulnerable software, open ports, web server misconfigurations, and other vulnerabilities that can exploit the network.
The vulnerability scanner, which forms an integral part of any vulnerability management tool tallies a publicly available database of vulnerabilities and exploits to associate the known vulnerabilities with the ones scanned in the network endpoints and applications.
Step 3: Vulnerability Assessment
The next step in vulnerability management is prioritization. Prioritizing the vulnerabilities enables IT security teams to mitigate the ones that are most likely to cause an exploit in the network. One prioritization method is via CVSS scores (as mentioned in the table below).
| CVSS v3.x Ratings | CVSS v4.0 Ratings | ||
|---|---|---|---|
| Severity | Severity Score Range | Severity | Severity Score Range |
| Low | 0.1-3.9 | Low | 0.1-3.9 |
| Medium | 4.0-6.9 | Medium | 4.0-6.9 |
| High | 7.0-8.9 | High | 7.0-8.9 |
| Critical | 9.0-10.0 | Critical | 9.0-10.0 |
While these scores help to prioritize mitigation, the risk possessed by certain vulnerabilities also depends on other factors, hence risk-based prioritization.
Step 4: Vulnerability Remediation
Last but not least comes mitigation. Once the vulnerabilities are detected and prioritized, they are mitigated by one of the following means:
- Deploying the latest patches to prevent further exploitation.
- Quarantining the vulnerable systems or uninstalling the vulnerable applications in case patches are not available or no fix has been released by the vendor.
- Marking as exclusions in case of known/internal vulnerabilities or when the chances of exploitation are less likely.
These four steps together make up vulnerability management. To bolster the enterprise network, it is recommended to automate the vulnerability management process.
How to manage vulnerabilities with Vulnerability Manager Plus?
"Keep your friends close, but your enemies closer" says Don Corleone In Godfather. It's just as much applicable to vulnerability management. You can't fix what you can't see, which is why IT admins and security personnel need to know about the threats and vulnerabilities in their network at all times. This is where Vulnerability Manager Plus steps in.
Let's take a closer look at Vulnerability Manager Plus' architecture to gain a thorough understanding of what it has to offer.
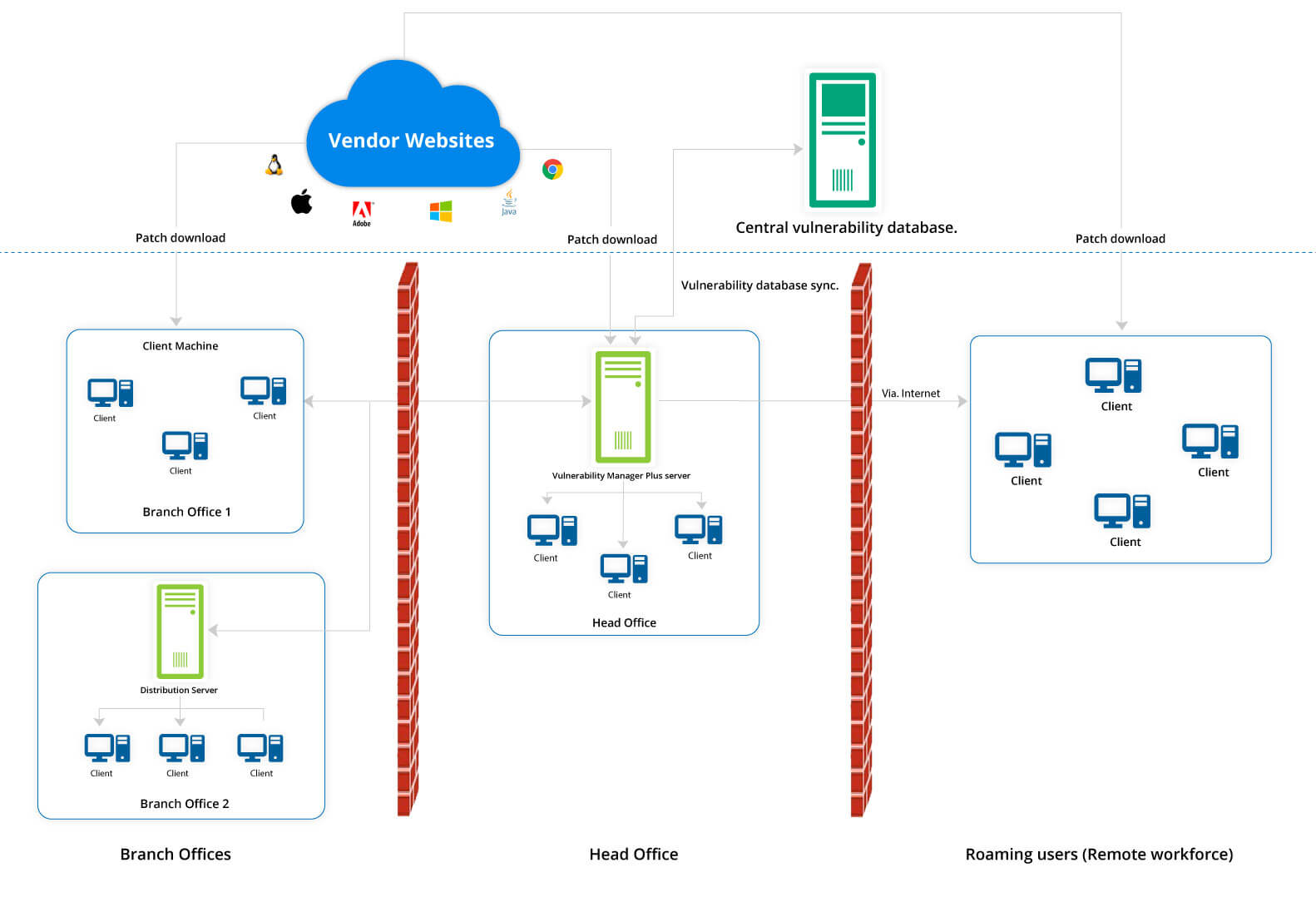
Vulnerability Manager Plus works on a client-server architecture. The Vulnerability Manager Plus server, which is located at the customer's location, has an integral database which is kept up to date with the latest scan and remediation information by periodically synchronizing with the central vulnerability database located at the Zoho Corp site.
At Zoho, after thorough analysis, the final consolidated data set on scanning, remediation, and patch information is hosted in the central vulnerability database. This information serves as the baseline for vulnerability management in the enterprise.
As soon as it’s up and running in your network, Vulnerability Manager Plus automatically discovers your Active Directory and workgroup assets. Scaling up? No problem. Since Vulnerability Manager Plus is constantly in sync with Active Directory, new assets will be brought under management as soon as they enter your network, leaving no opportunity for new threats to go unnoticed.
Leveraging endpoint agent technology, Vulnerability Manager Plus scans your laptops, desktops, servers, databases, workstations, and virtual machines across your entire global hybrid IT environment every 90 minutes, irrespective of whether they're within the corporate boundary or not.
You can set up distribution servers, which replicate primary server commands, for your remote offices simplify management and conserve bandwidth. You can even manage assets within a closed network like a DMZ.
Identified systems are probed for different attributes: operating systems, open ports, installed software, user accounts, file system structure, system configurations, and more. Using the library of up-to-date scan data, Vulnerability Manager Plus checks the discovered assets for threats and vulnerabilities and delivers appropriate remediation.
Generally, patches are downloaded directly from vendor sites, stored centrally in the server's patch store, and replicated to your network endpoints to conserve bandwidth. For remote workers, you can have the client machines download essential patches from trusted vendor sites without bottlenecking the limited bandwidth of the VPN gateways.
The web console is the heart of vulnerability management. It allows you to monitor your security posture and carry out all tasks anywhere, anytime.
Vulnerability management features
Vulnerability Manager Plus packs a powerful array of security features such as security configuration management, automated patching, web server hardening, and high-risk software auditing to help you establish a secure foundation for your endpoints, even in the absence of a security perimeter.
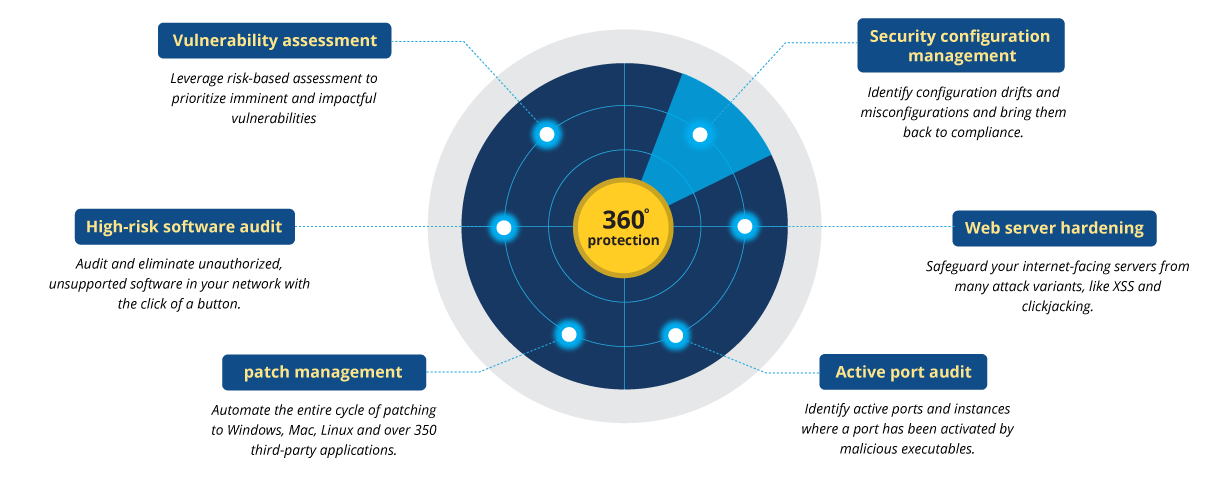
Prioritize what to patch with comprehensive vulnerability assessment:
- Identify vulnerabilities along with their context, such as CVSS and severity scores, to ascertain priority, urgency, and impact.
- Know whether exploit code has been publicly disclosed for a vulnerability.
- Keep tabs on how long a vulnerability has resided in your network.
- Filter vulnerabilities based on impact type and patch availability.
- Gain recommendations on high-profile vulnerabilities procured based on above risk factors.
- Leverage a dedicated tab on publicly disclosed and zero-day vulnerabilities, and utilize work-arounds to mitigate them before the fixes arrive.
- Isolate and identify vulnerabilities in critical assets, namely databases and web servers, that hold critical data and perform crucial business operations.
- Automatically correlate vulnerability intelligence and patch deployment.
Learn more about vulnerability assessment.
Establish a secure foundation with security configuration management:
- Identify misconfigurations in operating systems, applications, and browsers, and bring them under compliance.
- Audit your firewalls, antivirus, and BitLocker status.
- Prevent brute-force attempts by enforcing complex password, account lockout, and secure logon policies.
- Make sure memory protection settings, such as Structured Exception Handling Overwrite Protection, Data Execution Prevention, and Address Space Layout Randomization are enabled.
- Put an end to legacy protocols with risks that outweigh the benefits
- Manage share permissions, modify user account controls, and disable legacy protocols to reduce your attack surface.
- Safely alter security configurations without interrupting business operations with critical deployment warnings.
Learn more about security configuration management.
Automated patch management:
- Automate patching for Windows, macOS, Linux, and over 500 third-party applications.
- Customize deployment policies for hassle-free deployment.
- Test and approve patches before rolling them out to production machines.
- Decline patches to specific groups.
Learn more about patch management.
Audit high-risk software:
- Stay vigilant on legacy software that has or is about to reach end of life.
- Obtain real-time information on peer-to-peer software and remote sharing tools that are deemed unsafe, and eliminate them at the click of a button.
Learn more about high-risk software auditing.
Audit active ports:
- Continuously monitor active ports in your network systems.
- Identify whether the port is UDP or TCP.
- Filter active ports based on port range such as system ports (0-1023) and registered ports (1024-49151)
- Identify the number of instances of each active port.
- View the number and details of the executables listening on a particular port on each system.
Learn more about active port audit.
At-a-glance vulnerability management dashboards
The Vulnerability Manager Plus web console features a score of interactive dashboards that provide you all the vulnerability intelligence you need in the form of graphs, charts, trends, and more to help you make informed decisions.
Vulnerabilities dashboard
Gain a bird's-eye view of your network security posture, see what matters the most through various graphs and matrices, analyze vulnerability trends in your network, and track how well your vulnerability management efforts are paying off. Receive constantalerts on the top 10 vulnerabilities in your network and much more.
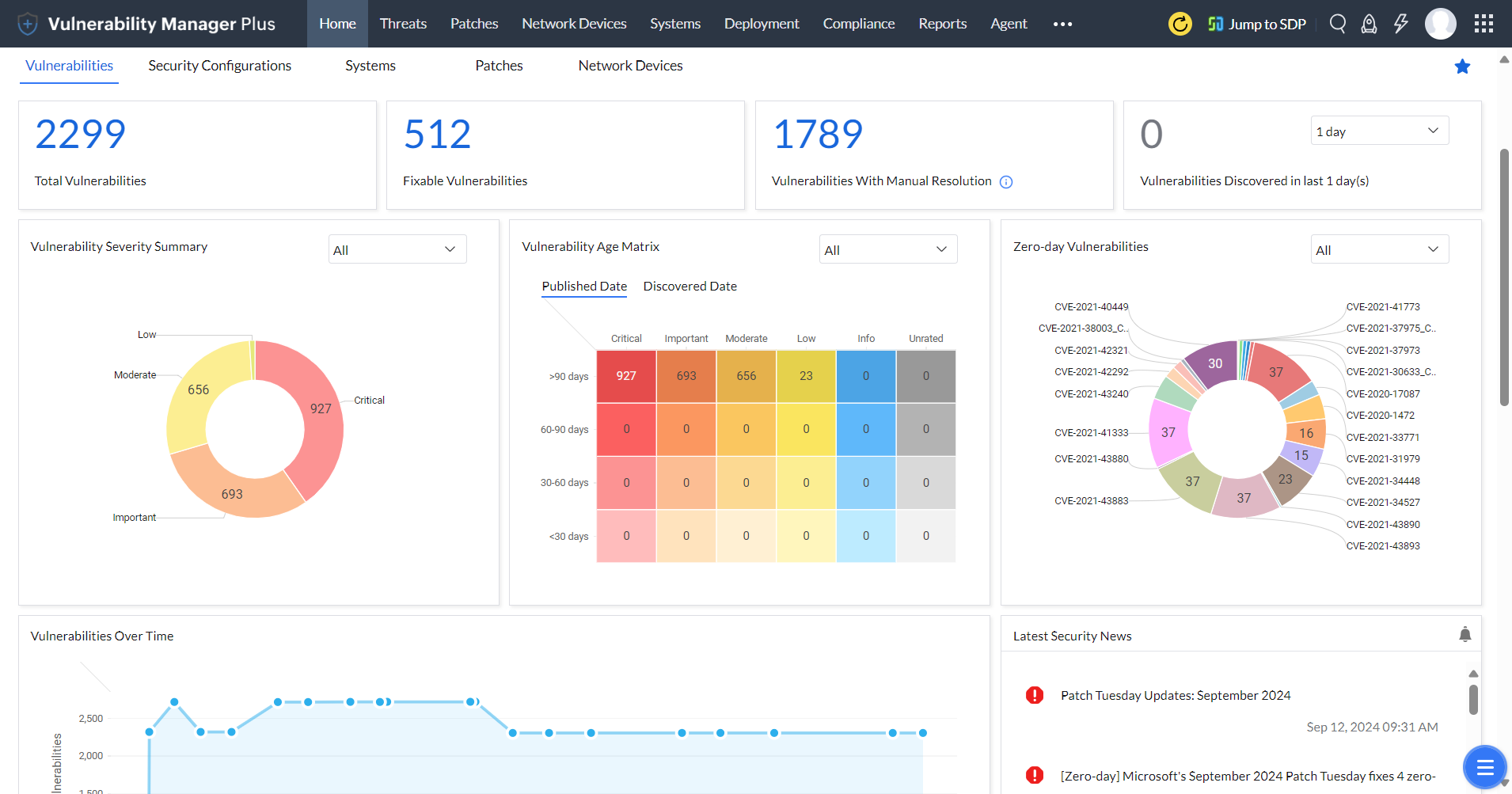
Dive in to learn how you can utilize vulnerability assessment dashboard to better orient your vulnerability management process.
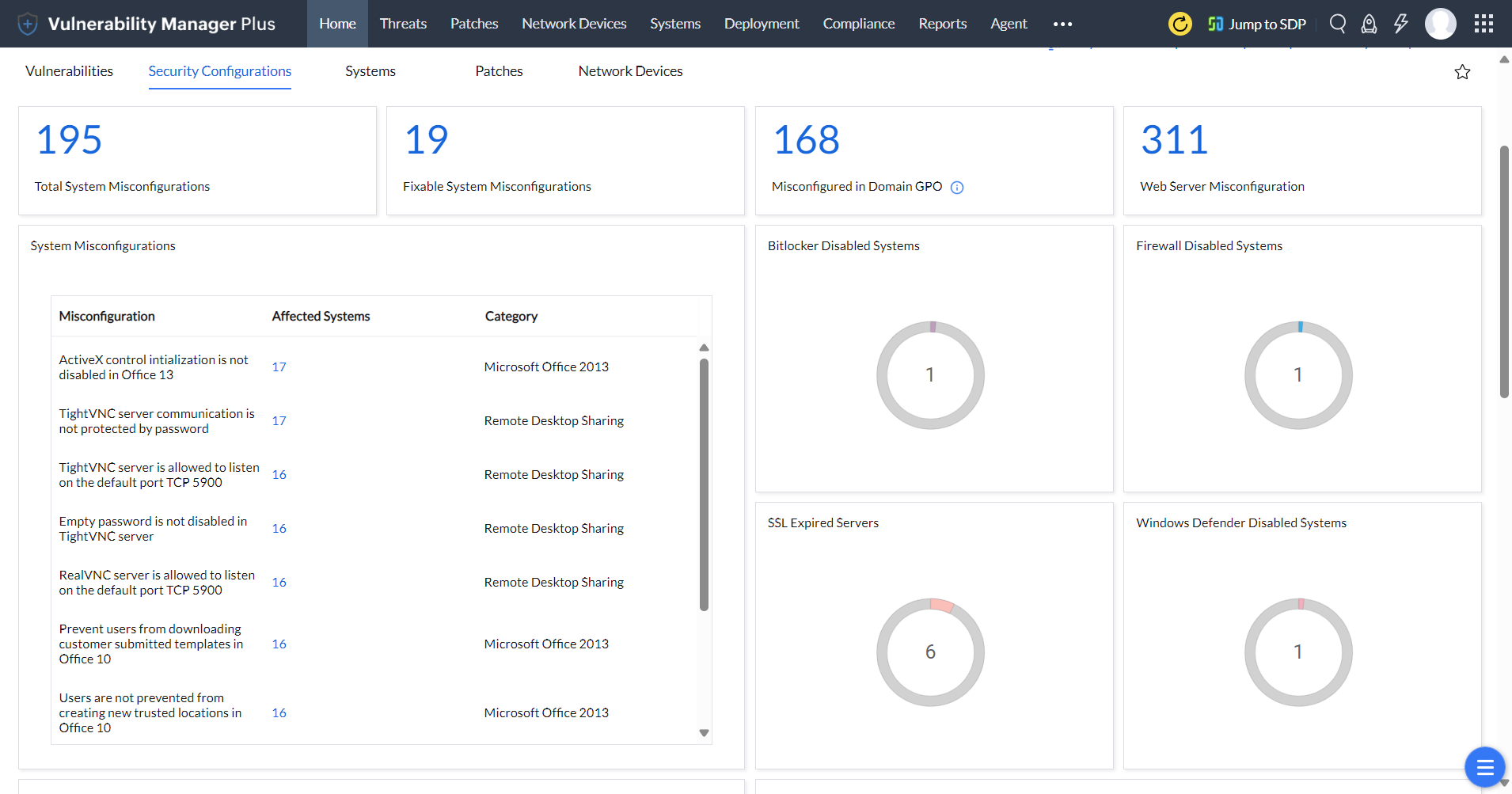
Security Configurations management dashboard:
Equip yourself with the Security Configurations management dashboard, built exclusively to track and combat misconfigurations in systems and servers, and audit firewall, antivirus, SSL, and BitLocker statuses. Learn more.
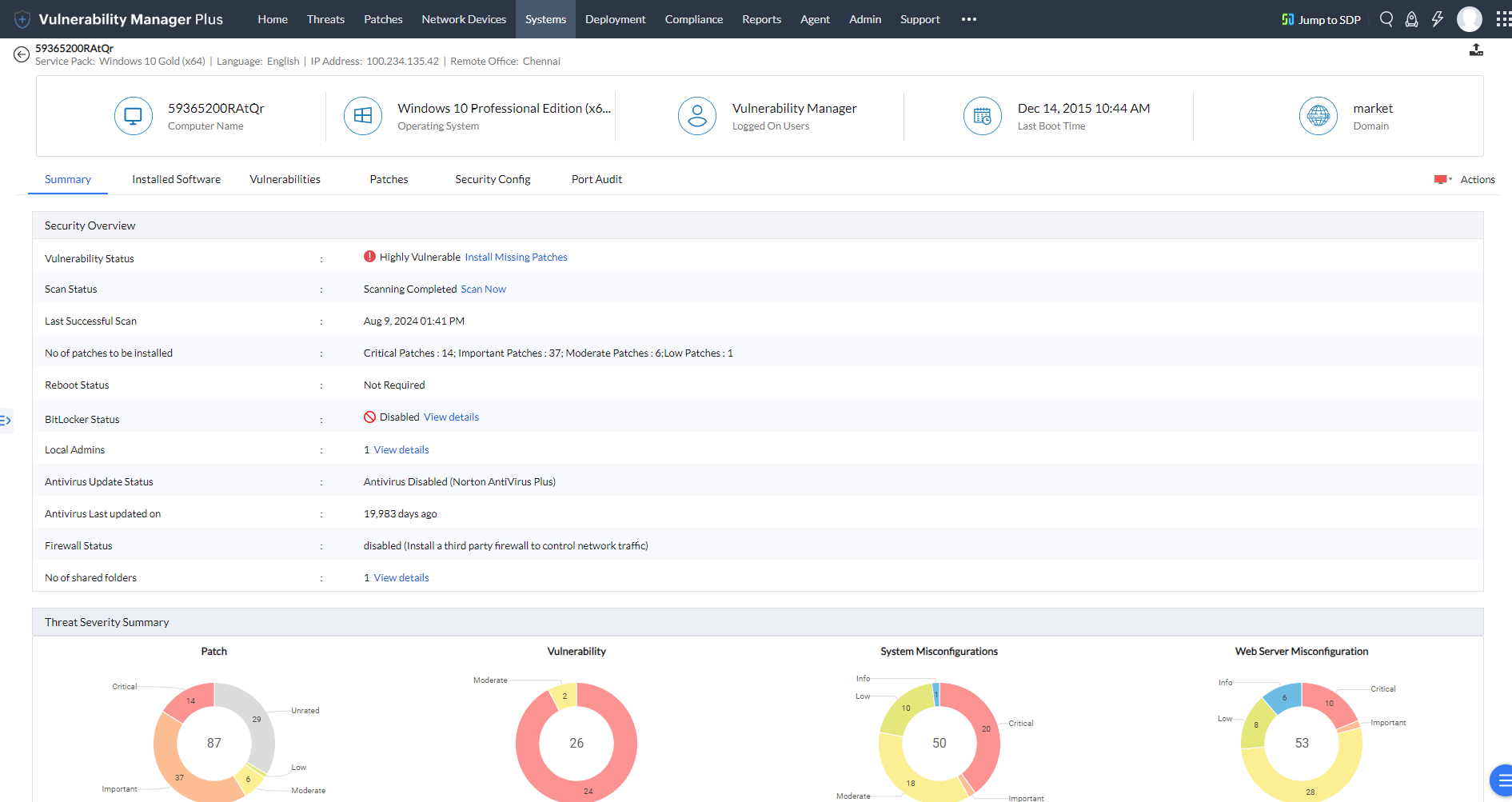
Individual system view
Furthermore, you'll be able to get a clear picture of the security overview of individual systems from the detailed resource view that pops up when you click on the system name.
Vulnerability management reports
All your vulnerability management efforts are essentially futile if you can't evaluate and understand your progress. Vulnerability Manager Plus offers a massive library of executive reports, granular report templates, and customizable query reports that you can use to scrutinize your network security, communicate risks, track progress, and report on security regulations to executives.
These reports are available in different formats, including PDF, CSV, and XLSX. You can either generate reports on-demand or schedule them to be sent directly to security executives, administrators, and enterprise risk management teams with just a click from the console.
Benefits of using ManageEngine Vulnerability Manager Plus
Vulnerability Manager Plus streamlines vulnerability management through efficient scanning, prioritization, and remediation guidance, enabling organizations to enhance their security posture and mitigate threats effectively.
- Early identification of imminent threats that require little to no intervention.
- Avoid hefty fines by conforming to cybersecurity regulations and compliance.
- All the capabilities of Vulnerability Manager Plus are now available as an add-on to Endpoint Central. Learn more about the benefits of purchasing the vulnerability management add-on.
- Eliminating the need for third-party integration for patching. Now, the entire vulnerability management cycle, from scanning, assessment and prioritization to deployment, can be carried out from a central console.
- Bid adieu to occasional scanning. The lightweight, all-purpose, self-updating agents reside on the assets they monitor—no scan windows, credentials, or firewall changes needed. Vulnerabilities are found faster, and the impact on the network is minimal.
- Define roles and delegate tasks to technicians based on enterprise needs.
- Built-in remediation for security configurations.
- With the failover server set up to take over in case the primary server fails, and with database backups in place, you can keep your business running without impacting your crucial business operations.
- By configuring the WAN agents of remote clients to access the product servers via a secure gateway, you can secure the Vulnerability Manager Plus server and its contents from threat actors.
- Easy to use and intuitive.
- Vulnerability Manager Plus is now available in 18 languages.
There's no silver bullet solution that renders your network impenetrable to cyber exploits. But by constantly reevaluating and strengthening the security stance of your network with Vulnerability Manager Plus, you stand a much better chance against detecting and thwarting cyber trespassers in your network.
To see the tool in action yourself, download a free, 30-day trial now.
FAQs about vulnerability management
1) What is a vulnerability in cybersecurity?
Vulnerabilities are faulty piece of code in a software that causes it to crash or respond in ways that the programmer never intended. Vulnerabilities can be leveraged by hackers to gain unauthorized access to, or perform unauthorized actions on, a computer system.
2) What is an exploit?
Exploits are automated scripts or sequences of commands that attackers use to manipulate vulnerabilities to their advantage. Exploit takes advantage of the vulnerability to break into the system and delivers the payload, which could be malware with instructions to disrupt system functions, steal sensitive data, or establish a connection with the remote hacker's systems.
3) What are the differences between Vulnerabilities, Threat & Exploit?
Vulnerabilities are weaknesses or flaws in systems that could be exploited. Threats refer to potential sources of harm or attacks that exploit vulnerabilities. Exploits, on the other hand, are specific techniques or tools used to take advantage of vulnerabilities, typically performed by threat actors to compromise systems or gain unauthorized access.
4) What are the risk factors needed to assess vulnerabilities?
For a sophisticated analysis, risk factors such as CVSS scores, severity ratings, exploitability, asset criticality, vulnerability age, and patch availability must be taken into account to understand the impact and urgency of vulnerabilities. Explore more about the role of these risk factors in the vulnerability assessment process.
5) What is the difference between vulnerability assessment and vulnerability management?
Vulnerability assessment involves identifying and analyzing system vulnerabilities. It focuses on evaluating weaknesses and determining their impact whereas vulnerability management encompasses the entire lifecycle of vulnerability mitigation, including identification, assessment, prioritization, and remediation. It ensures a proactive and comprehensive approach to addressing vulnerabilities and reducing risks.
6) What is the difference between vulnerability management and patch management?
Vulnerability management involves the proactive identification, assessment, and mitigation of vulnerabilities in an enterprise network. It encompasses scanning, prioritization, and remediation. Patch management, on the other hand, specifically focuses on the application of software patches and updates to address known vulnerabilities. Patch management is a subset of vulnerability management that deals with specific remediation actions.
7) Who uses a vulnerability management program?
Modern enterprises are rooted in technology and often rely on applications and browsers to carry out business processes. In order to prevent their systems and the data stored in them, such as personal end-user information and customer payment information, from being breached and to prevent denial of service attacks and unauthorized exploits, organizations conduct regular and thorough vulnerability management process to ward off any threats and vulnerabilities.
