Want to know more about how you can detect and prevent rogue devices from your network
Read our e-book, Rogues on the rise - Is your network secure enough?
The address resolution protocol (ARP) is a fundamental enabler of network communication. Acting as a bridge between your network's internet layer and network link layer, this networking protocol translates the network addresses (IPs) to physical layer addresses (MAC addresses). The address translation enabled by ARP protocol plays a critical role in facilitating communication between different network components in the same LAN.
Being a primary protocol to enable network communication, ARP is also a common target for network attackers. Helping attackers intercept and manipulate network communication, ARP spoofing attacks, also known as ARP poisoning, can cause serious damage to network integrity and security. It's important for network admins to setup a proactive ARP spoofing detection tool to enhance security and reliability of modern IT networks.
While ARP is one of the widely used network protocols, it offers weak security capabilities. Being a stateless protocol, ARP enables accepting data packets from sources in the same LAN as the ARP hosts, even without sending out a request. Updated ARP data in the host's ARP cache does not go through any security considerations by default. This means ARP spoofing is fairly simple for any attacker with the right tools.
Without an advanced network scanning tool, detecting ARP spoofing in your network can be tedious. ManageEngine OpUtils eliminates this hassle by enabling you to automatically get notified of ARP spoofing in real-time with its ARP spoofing detection capability.
The more visibility you have into your network endpoints and gateways the more effectively you can detect ARP spoofing. Since components, such as routers, layer 3 switches, and gateway servers in your network, act as the entry points to carry out ARP spoofing attacks, tracking the ARP cache of these components is vital.
OpUtils enables you to track these components with ease. You can add these components by manually specifying their IP and SNMP configuration details, or through bulk import using CSV files. Once you have added these components to be monitored, OpUtils starts to track their ARP cache for IP-MAC association details.
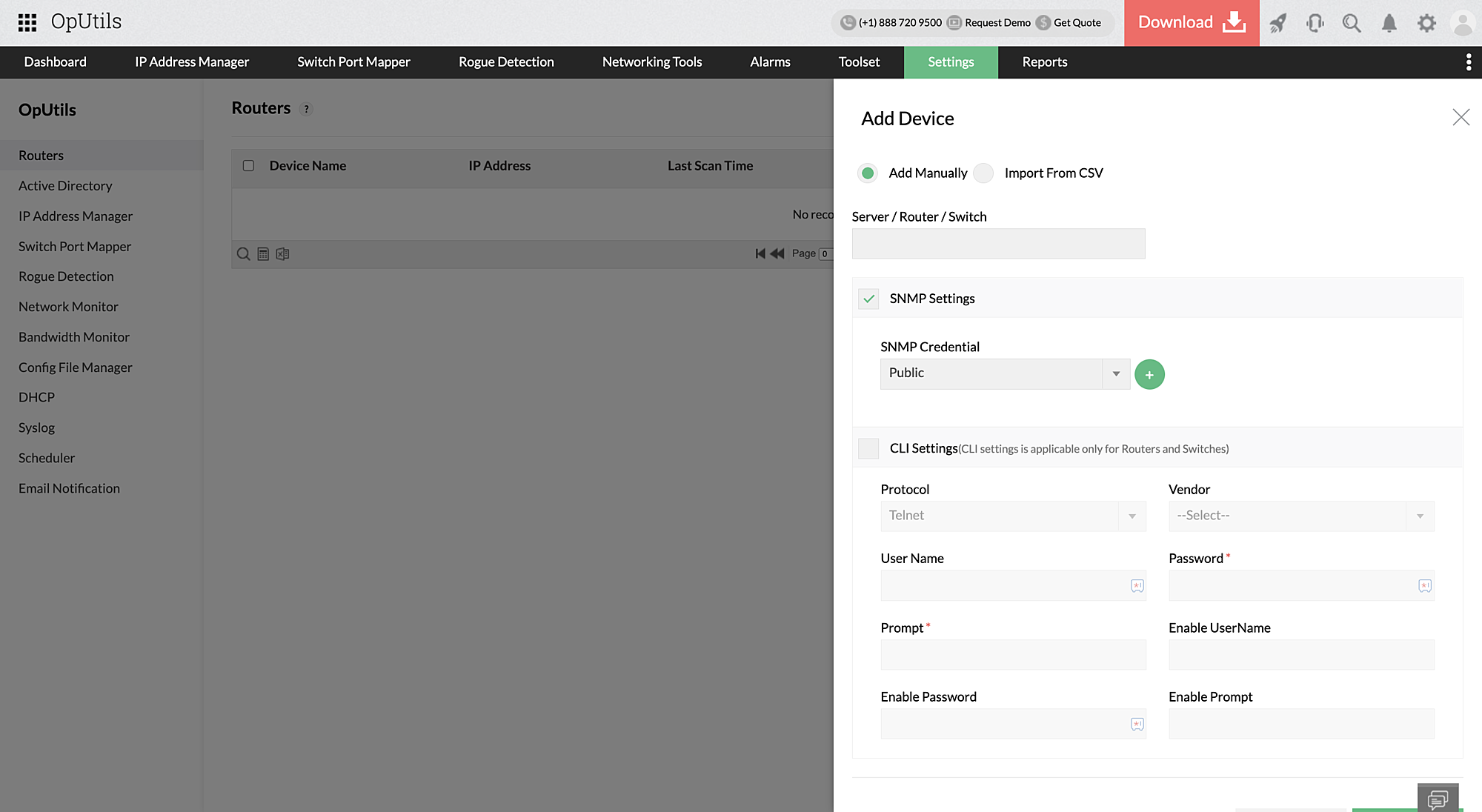
Proactively detecting ARP spoofing requires network admins to constantly scan their network gateways and routers to track IP to MAC address association. Since ARP cache's are updated whenever an IP to MAC association update is sent by network devices, periodical network scanning is critical.
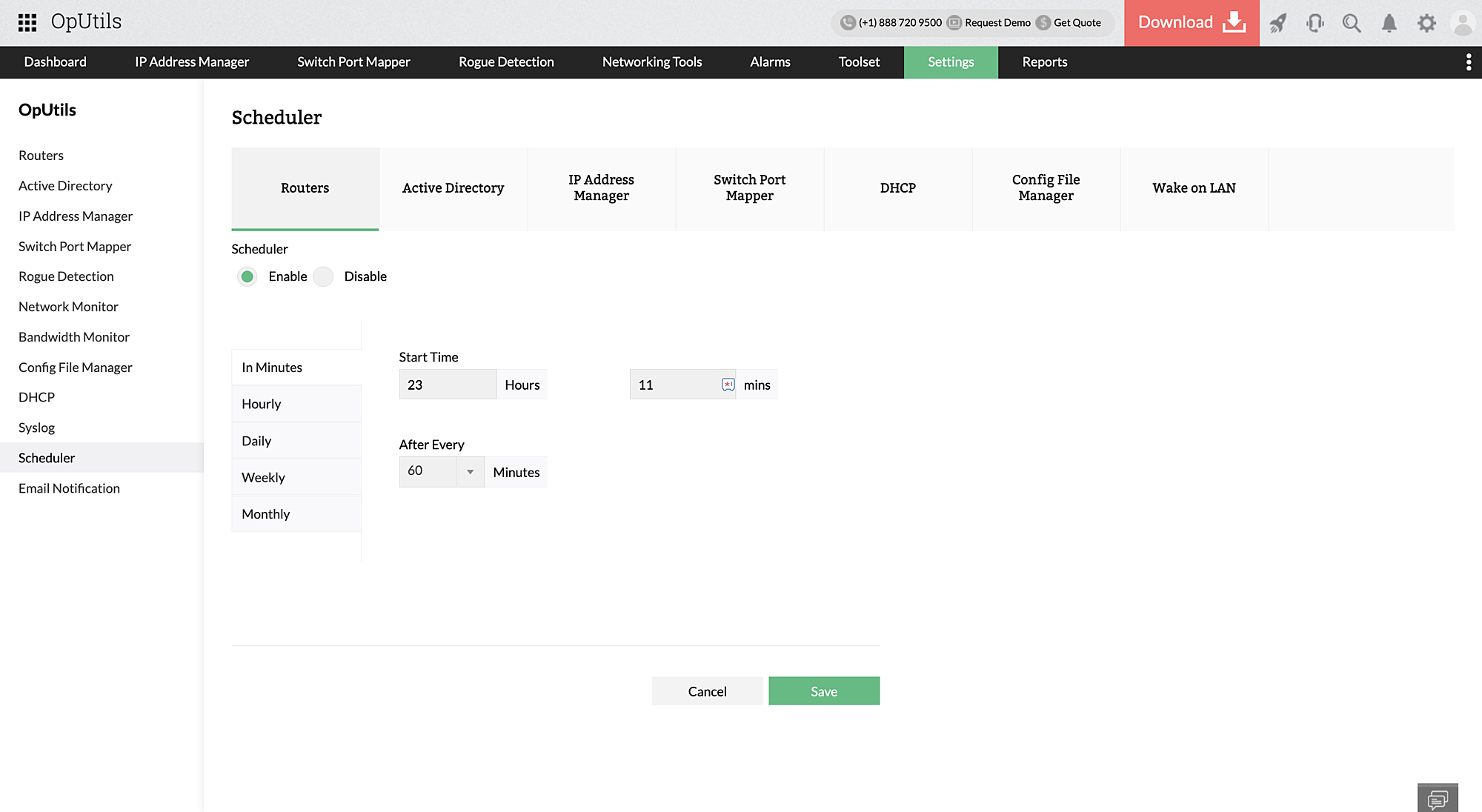
OpUtils simplifies this process by offering an automated scan scheduling capability. Using the Scheduler option, network admins can set up custom scan schedules for different network components. Once the scan period is configured and scanning is enabled, OpUtils automatically scan the components at the set intervals. This ensures ARP data monitoring is proactive.
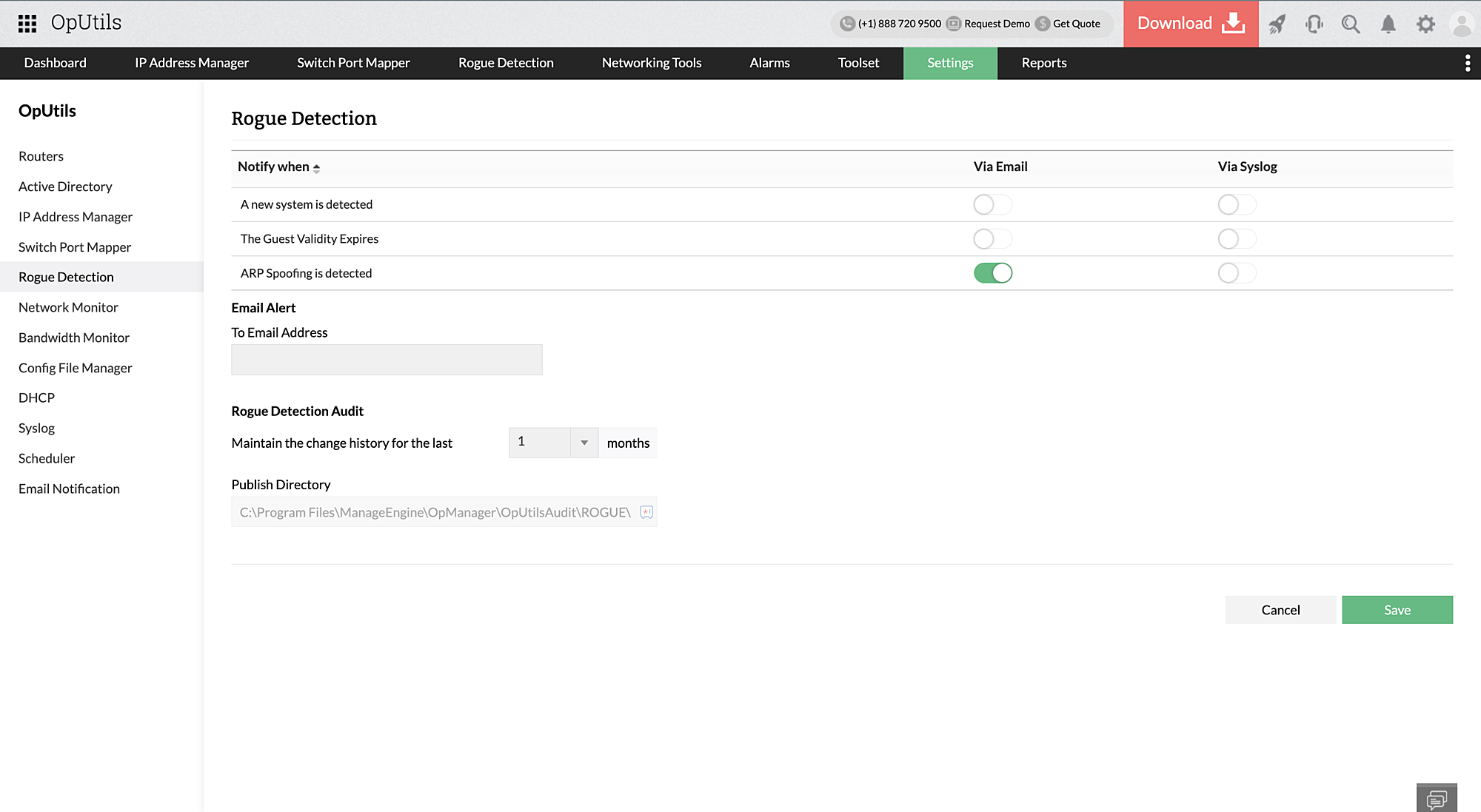
Once network components are discovered and periodic scan scheduling is enabled, detecting ARP spoofing is just a click away with OpUtils. Network admins, on selecting the preferred mode of alerting when ARP spoofing is detected, can easily stay informed about ARP spoofing as and when it occurs. OpUtils will monitor your network for ARP spoofing and provides instantly alerts to the configured email, or logs an entry in the syslog file.
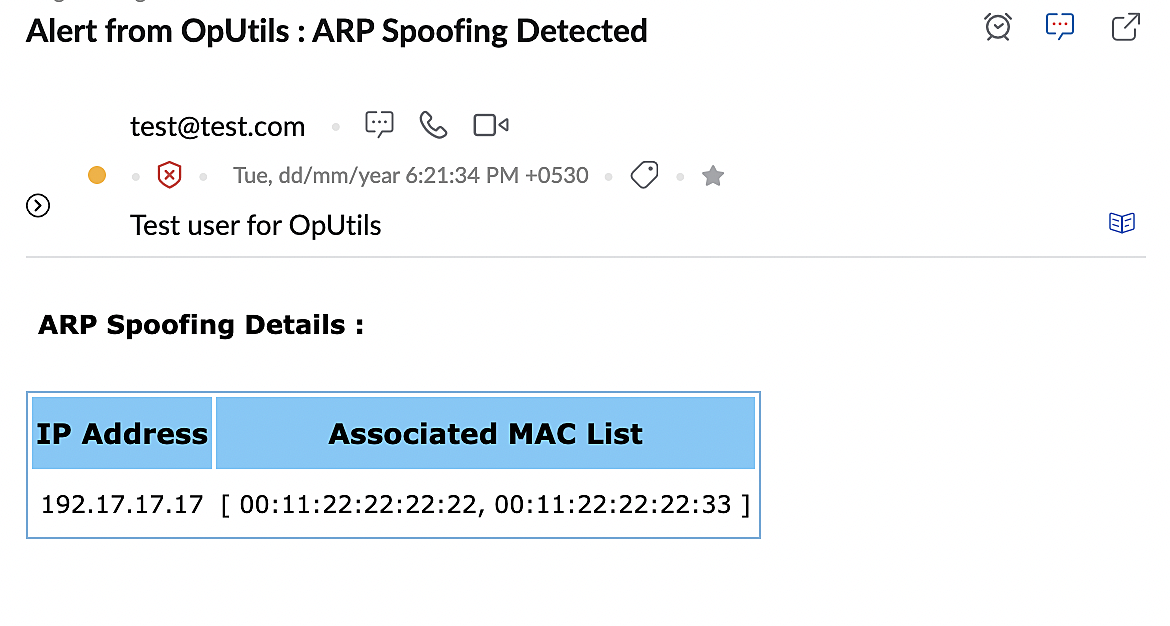
The alert message triggered to the configured email addresses displays the target IP of the ARP spoofing attack and the MAC address perpetuating ARP spoofing. Network admins can use these details to effectively mitigate the ARP spoofing attack by carrying out security measures, such as blocking the switch port that enables access for the MAC address, and more.
By discovering their network components and automating periodic scanning, network admins can seamlessly detect ARP spoofing and enhance network security with OpUtils.
ManageEngine OpUtils offers advanced IP address management and switch port mapping capabilities that enables you to ensure seamless networking. With its rogue detection and prevention module aiding network admins to identify, inspect, and tackle rogue devices intruding their network, network admins can stay clear of nefarious devices. Not just the ARP spoofing detection capability, but explore all the useful features OpUtils has to offer by scheduling a personalized live demo with our product experts.
New to OpUtils? Download a free 30-day trial and explore OpUtils hands-on now!