Ransomware response playbook : A complete guide to prevent, protect, and recover from ransomware attacks
Chapter 1: Introduction
What would you lose if you were locked out of your device right now? You probably have information like banking details, family photos, and work data saved and are always logged in to your social media and email accounts for easy access. Yes, there's a cloud backup and you can change all your passwords. However, you're still at great risk of having private and confidential information exposed. One misstep could cause a breach of privacy, financial loss, or even cost you your job. For most of us, the thought of losing something valuable creates fear, an emotion cybercriminals try to take advantage of with ransomware, the most dangerous form of malware.
An organization with endpoints in its network should focus on three functions: management, observability, and security. Endpoint security is still the IT team's responsibility in many organizations. When there are different solutions and agents for each function, agent maintenance becomes the system administrator's responsibility. This is an extra load for them on top of their long list of duties. ManageEngine's unified endpoint management (UEM) solution provides complete management for endpoints. Our next goal is to extend this reach to security. We hope to make our management solution an all-encompassing endpoint protection tool which will cover EDR, beginning with anti-ransomware.
Fortify IT with EDR
Endpoint detection and response (EDR) is a cybersecurity technology that monitors endpoints for suspicious activity and protects devices from threats in real time. EDR usually works at the system level and is used to minimize the impact caused by ransomware.
A ransomware attack could happen anytime, anyplace. Technology is advancing rapidly and is often experimental, sometimes at the cost of security. This means more avenues and loopholes for malicious actors to prey upon innocent users. New techniques are emerging every day. EDR goes one step beyond the traditional antivirus approach and is designed to reduce the probability and impact of cybersecurity attacks.
This e-book is for anyone who uses a device. Whether it's personal or professional, your device contains valuable data. If you're part of an organization, there's more at stake. EDR only works when used in tandem with responsible user practices. Think of a house equipped with smart cameras. It alerts you when there's movement and identifies suspicious activity. That's your EDR. It helps protect your private space from potential threats. What happens if you decide, "Oh, it's probably just the cat," and ignore the alerts? The whole system fails and you pay the price when there's an incident. It is your duty to be well informed of security threats like ransomware and how to combat them. In this e-book, we'll help you gain a deeper understanding of:
- Ransomware 101: We'll start off by understanding the fundamentals—what ransomware is, how it works, its evolution over the years, and some notable incidents in history.
- ManageEngine's response strategy: Learn about the best policies for tackling ransomware, important roles and responsibilities for incident response, the stages of a ransomware response plan, and real-life scenarios showing the different outcomes of a ransomware detection solution.
- AI and best practices: Understand the role AI plays in ransomware attacks and prevention, and pick up a few tried-and-tested best practices to improve your security posture.
Types of ransomware
Ransomware can occur in a few ways. The goal is the same: Victims are expected to pay within a time frame to protect their data. This amount could go up to hundreds of thousands of dollars, typically paid in cryptocurrency. Global reports show an increase in ransomware attacks in the last five years, and these numbers are expected to go up exponentially.
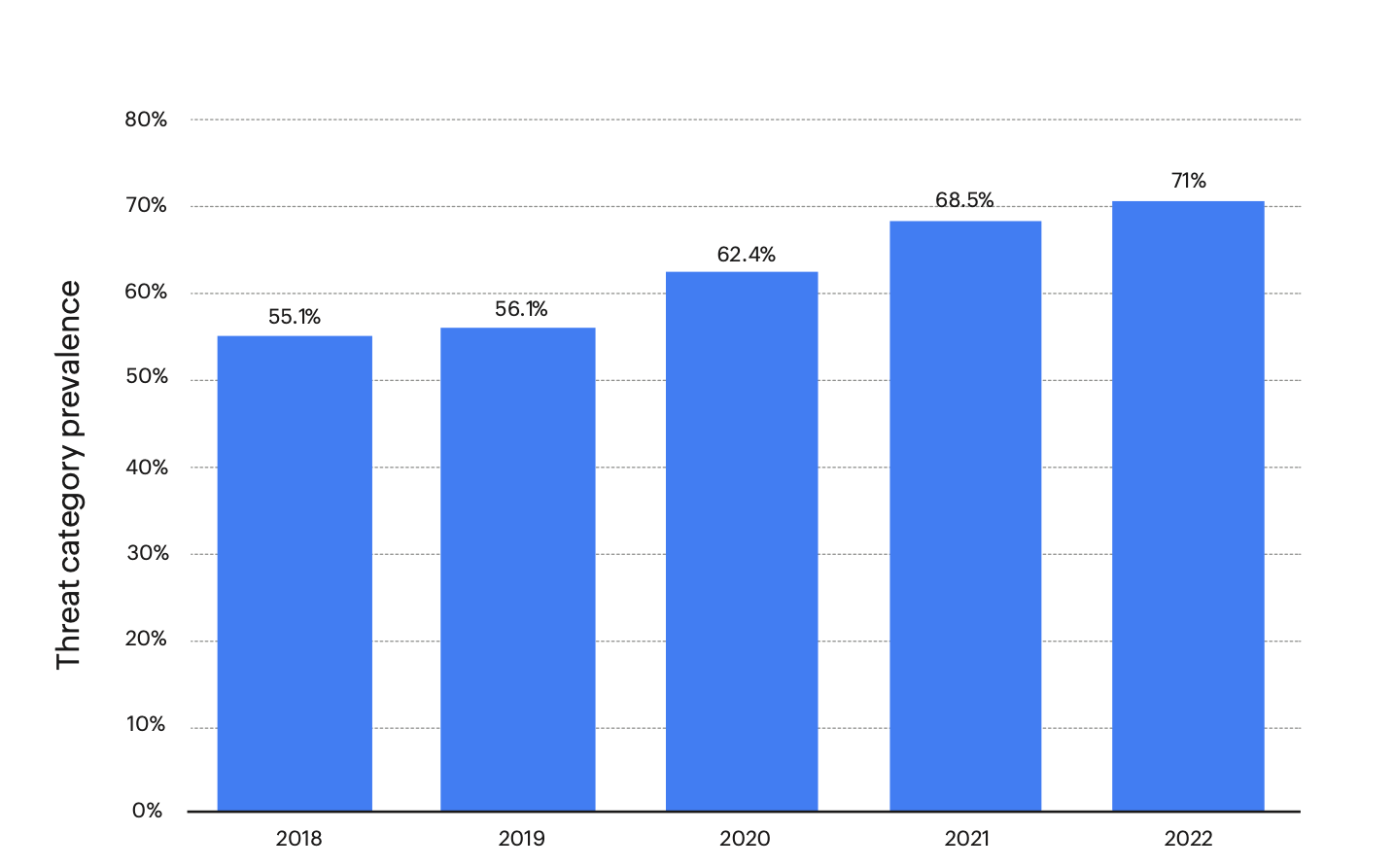
Percentage of organizations victimized by ransomware attacks worldwide. (Source: Statista)
Let's take a look at a few common types of ransomware:
- Crypto ransomware: Cyberattackers enter the system through phishing techniques to encrypt some or all files and block access to the data. Two decryption keys are required to restore access, which comes at a price. Hackers hold one key and extort small amounts in cryptocurrency from victims. Often, they provide the decryption key for one file for free to establish trust.
- Locker ransomware: While crypto ransomware prevents access only to encrypted files, locker ransomware locks users out of their device completely. Hackers then demand a ransom through a message displayed on the screen. This type of malware also limits functionality. Other than interacting with the hacker and making payments, users will not be able to carry out any actions. For example, hackers can allow only the usage of specific keys on the keyboard.
- Doxware/Leakware: In addition to stealing and encrypting confidential data, hackers threaten to expose it if the ransom is not paid. Derived from the phrase dropping documents, doxing involves intentionally publicizing private information. This is especially dangerous for organizations handling sensitive data like healthcare and government organizations, which are often the target of these attacks.
- Scareware: For any ransomware to be effective, it needs to cause panic and a sense of urgency in the victim's mind. Scareware manipulates users by claiming their device has been affected by a cybersecurity issue. These pop-up messages or emails claim to offer a resolution for a reasonable fee that must be paid quickly. Scareware often results in credit card theft.
- Ransomware-as-a-service (RaaS): Cybercriminals can buy or rent malware from the dark web and use it to extort victims. It works like a SaaS business model, but with negative intentions. This gives hackers with limited technical knowledge the opportunity to carry out sophisticated attacks with ease. Customers can pay a subscription fee or make a one-time payment for the malicious code or tools. They can also follow an affiliate model, where the creator gets a portion once the ransom is paid.
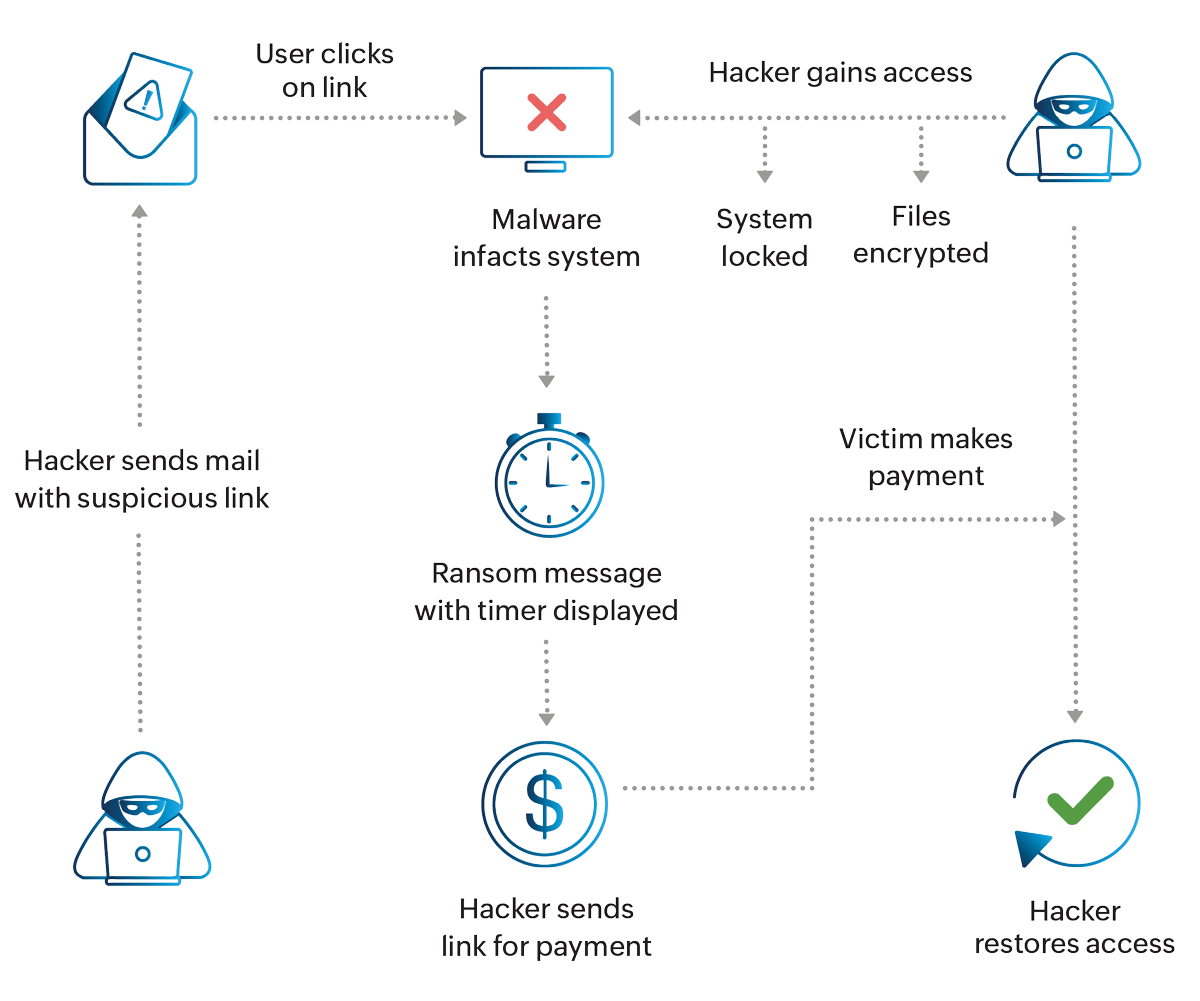
At a glance: How ransomware works
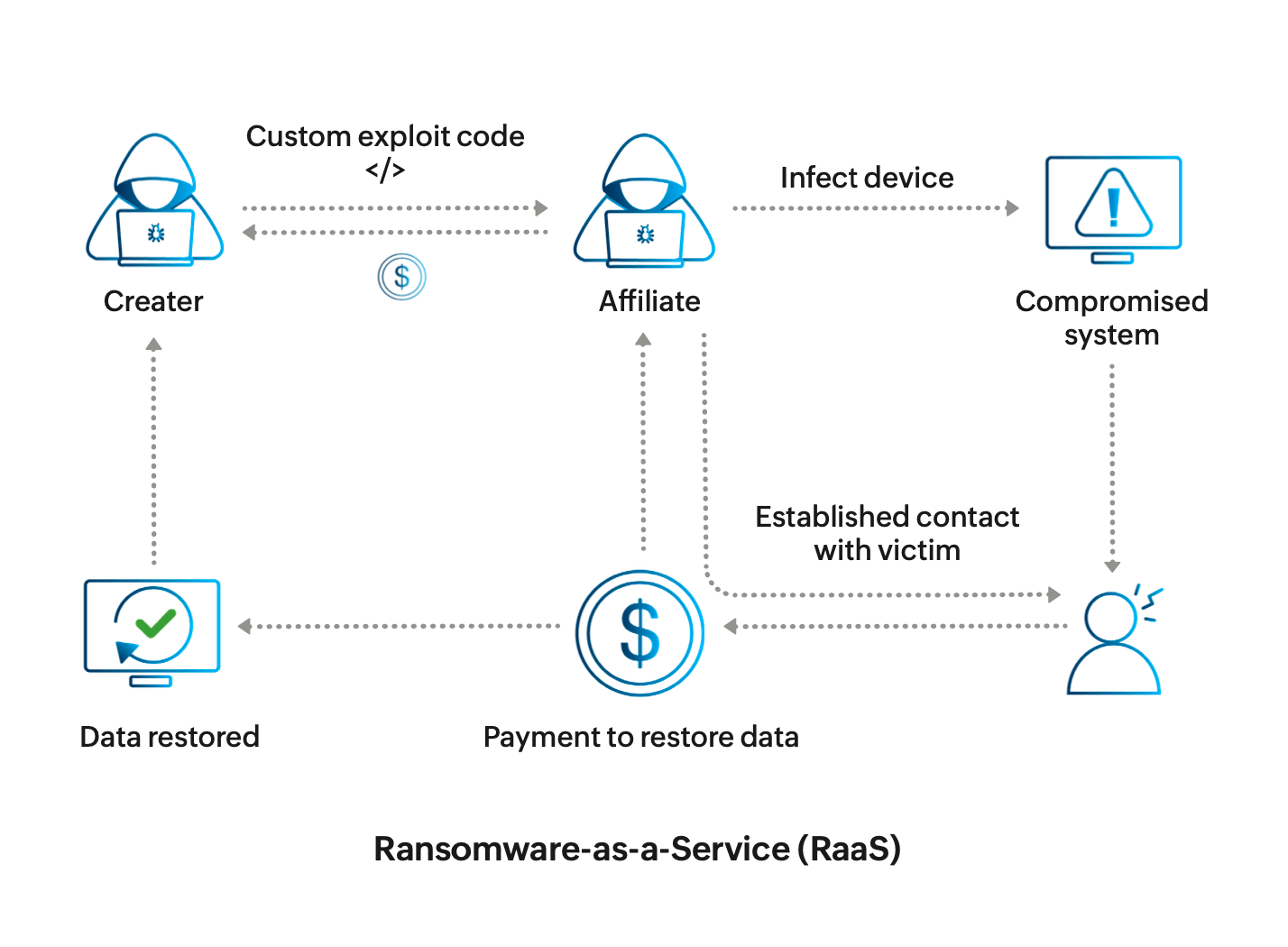
Ransomware-as-a-Service (RaaS)
Time and again, we hear the phrase, "Humans are the weakest link in the security chain." This is why ransomware attacks have evolved to trick users and gain access to sensitive information. This typically begins through a phishing attack, targeting one individual or system. Here's the dilemma: Do you comply with their demands? There's a huge risk involved because you don't have any guarantee that the attacker will return your data. You could lose money and data. Paying up also gives hackers the upper hand and encourages them to continue attacking other organizations or even attempt a second attack. The best way to avoid putting yourself in this precarious situation is by investing in a ransomware protection solution.
Ransomware archives

To understand ransomware as it is today, we need to look back and understand history and how ransomware has evolved over the years. The concept of virus in computers started off as harmless experiments within the academic community. In the 1980s, the first ransomware, AIDS Trojan,
made its appearance in the medical research field. The malware was distributed through floppy disks (remember them?) posing to offer information on AIDS. It encrypted file names on the victim's computer, demanded a ransom, and declared that there is no cure for AIDS. The creator of this ransomware, a scientist himself, was arrested.
Things were pretty quiet for a decade or so...until ransomware made its dreaded comeback. As computers became more prevalent in the workplace, so did the idea of stealing information for leverage. By the early 2010s the world saw a number of ransomware attacks of varying degrees like GPCode, Archiveus, CryptoLocker, and Reveton. They had a superpower the AIDS Trojan didn't have: the internet. This, combined with the invention of Bitcoin in 2008, made ransomware a lucrative option for criminals. Since then, ransomware attacks have gotten bolder and more complex, targeting large corporations for hefty sums of money.
Common entry points
- Phishing: Malware phishing is the most employed mode of entry. Users receive an attachment via mail, cleverly disguised as information from a trusted source, like an invoice or coupon. In some instances, users may also receive links that mimic legitimate websites. Users are encouraged to click on the link or download a file. When they take the bait, hackers can enter the system or network.
- Brute force via RDP: RDP enables users to access a Microsoft system remotely, a key feature bad actors can abuse to enter a network. While its actual purpose is to make remote troubleshooting easier, RDP makes it just as accessible for cybercriminals. All they have to do is enter the IP address and password. How would they know a user's password? Well, is there anything the internet can't do? There are software programs that can guess weak passwords and even sellers on the dark web offering leaked passwords at a low price. RDP brute-force attacks can be successfully carried out in as little as a few hours. Once attackers are in, it's easy to encrypt files and demand a ransom.
- System vulnerabilities: Hardware and software vulnerabilities are often the cause of severe damage in ransomware attacks. Some examples of vulnerabilities include:
- VPN
- Patch
- Elevation of privilege
- Remote code execution
- Microsoft Exchange Server
Exploit kits are used in these types of attacks. An exploit kit is a toolkit or highly automated program that operates in stealth mode to take advantage of known vulnerabilities and attack a user's device. It relies on a compromised website or malicious advertising (also called malvertising) on a trusted website that discreetly redirects traffic to a landing page. Here, the code embedded in the landing page begins its analysis. Its role is to sieve out systems that don't meet their criteria and pick the easy targets. If a vulnerability is detected, the traffic is directed to the exploit and the malware can be downloaded and executed.
Other vectors like social media, insider threats, and weakened security measures (e.g, no MFA) also play a role in ransomware and can be used as an entry point by malicious actors.
Major ransomware attacks
CryptoLocker
Social engineering attacks are a common way to introduce malware into a system, which is exactly what CryptoLocker did. This ransomware sent malicious attachments via email. These often looked like legitimate invoices and users were tricked into downloading the files, which would infect the system. Files were then encrypted using an encryption key, and the hackers demanded a ransom in exchange for the decryption key. The first CryptoLocker attack was discovered in 2013. Before its dissolution in 2014, CryptoLocker raked in nearly $3 million from its victims. Since then, hackers have used the CryptoLocker code to create CryptoWall, a ransomware which operates in a similar manner.
WannaCry
On May 12, 2017, the WannaCry cryptoworm took the world by storm and infected nearly 250,000 systems across 150 countries. WannaCry took advantage of a protocol vulnerability in Microsoft Windows systems and targeted users who failed to update their software. Its victims included high-profile organizations like the UK's National Health Service, FedEx, Hitachi, and Renault. Attackers encrypted files and demanded a ransom of $300 in bitcoin, doubling the amount and threatening to delete files as they got closer to the end of the stipulated payment window of three days. Marcus Hutchins, a security researcher also known as MalwareTech, discovered a kill switch in the ransomware that stopped WannaCry, and by May 15, 2017, the number of new infections reported dropped significantly. Cybersecurity experts advised against paying the ransom, but the damage was done. The hackers behind this attack made almost 55 BTC, which is valued at nearly $1.5 million today. The global net loss from WannaCry is an estimated $4 billion.
SamSam
Unlike other ransomware attacks that target random users, the SamSam actors selected their victims with a purpose. They chose organizations that would most likely pay up, like the government agencies and hospitals in the US. The malware exploited vulnerabilities in Microsoft servers and mainly used brute force attacks or stolen credentials and gained unlawful access through the Remote Desktop Protocol (RDP), thereby eliminating the need for social engineering attacks. Since RDP is used to connect with other systems in the network, SamSam was able to spread with minimal user interaction. Once the malware entered the system, users received a ransom note, demanding 0.8 BTC for each affected system or 4.5 BTC for all systems. The first SamSam attack was discovered in 2015. In 2018, two Iranian nationals were indicted in the US for their involvement in the attacks. The FBI detailed the damages as "more than 230 entities infected, $6 million in ransom payments extorted, and an estimated $30 billion in damages to the affected public and private institutions."
NotPetya
Petya and its successor NotPetya made headlines in 2017 for a global attack specifically targeting Ukraine. Petya, named after a weapon satellite system in the James Bond film, GoldenEye, operated like a typical ransomware, encrypting data and demanding funds for the decryption key. NotPetya, on the other hand, encrypted the entire hard disk and displayed a ransom note with a Bitcoin address. There was a catch—the Bitcoin address was fake. Although it looked like other ransomware programs, it was designed to delete files permanently with no modes of recovery. It quickly became evident that the goal was not financial gain, but to cause catastrophic levels of destruction. NotPetya's fiscal impact is estimated to be $10 billion dollars, surpassing WannaCry, which also attacked the tech world earlier that year.