Group Policy
What is Group Policy in Active Directory?
Group Policy is used to regulate user and computer configurations within Windows Active Directory (AD) domains. It is a policy-based approach that can be applied to the whole organization or selectively applied to certain departments or groups in organizations. Group Policies are enforced by Group Policy Objects (GPOs).
What are GPOs?
GPOs comprise of the user and computer configuration settings that will be applied to domains or organizational units (OUs). GPOs need to be linked to an AD unit (domain or OU) to be applicable. Both the user and computer configuration policies have Software Settings, Windows Settings, and Administrative Templates. The Windows Settings contain important security policies like password and account lockout policies, software restriction, and registry settings. Administrative Templates are used to regulate access to the Control Panel, system settings, and network resources.
What is Group Policy used for in AD?
As mentioned earlier, Group Policies centralize management of organizational resources. Some Group Policy examples include execution of login scripts upon startup of a computer, user password settings, disabling users from changing the system time, and many other user and computer configurations. Group Policy benefits include:
Wide scope of application: These policies can be applied based on organizational hierarchy by linking them to AD sites, domains, and OUs.
Ease of management: Group Policy settings can be easily managed via GPOs. Multiple GPOs can be linked to one domain. A single GPO can be linked to multiple domains. When linked to parent units, say a domain, the policies are applied to all child units within the domain.
Priority-based application: GPOs have link order precedence, which helps resolve clashing policy settings. For example, a GPO with link order "1" will take precedence over another GPO with link order "2." Thus, the GPO with link order "1" will be applied last, overriding all the other GPOs. The link order can be changed by sysadmins in the Group Policy Management Console (GPMC).
Hierarchical application: Besides link order precedence, Group Policy adheres to a strict hierarchy. Always, policies are processed in this order: Local > Site > Domain > OU. Further, computer configuration policies override user configuration policies regardless of link or precedence order. These features ensure that the most relevant settings for the smallest unit (OU) are pushed.
Types of Group Policy
Group Policies can be categorized into three segments based on where or how they can be applied. The three types include:
| Local Group Policy | Group Policy in AD | Starter Group Policy |
|---|---|---|
| Local Group Policy manages policies for individual (non-domain) computers. More than one local GPO can be created for different local users. | These are an aggregate set of policies that can be applied to all domain-joined computers. Both user and computer configurations for all domain users can be managed centrally. | Starter Group Policies are templates to be used within AD. Sysadmins can create one starter policy and then go on to create multiple similar Group Policies based on the starter policy. |
| The policy is stored on the computer on which it is configured. The settings can be managed using the local Group Policy editor on the computer. (Run gpedit.msc to open the editor.) | The Group Policies can be managed from the GPMC in the domain controller. Note that for domain-joined machines, AD Group Policies override local Group Policy settings. | Starter Group Policies are available within the GPMC in the Server Manager tools. |
How to create a Group Policy
To create a Group Policy, head to the GPMC in Server Manager > Tools.
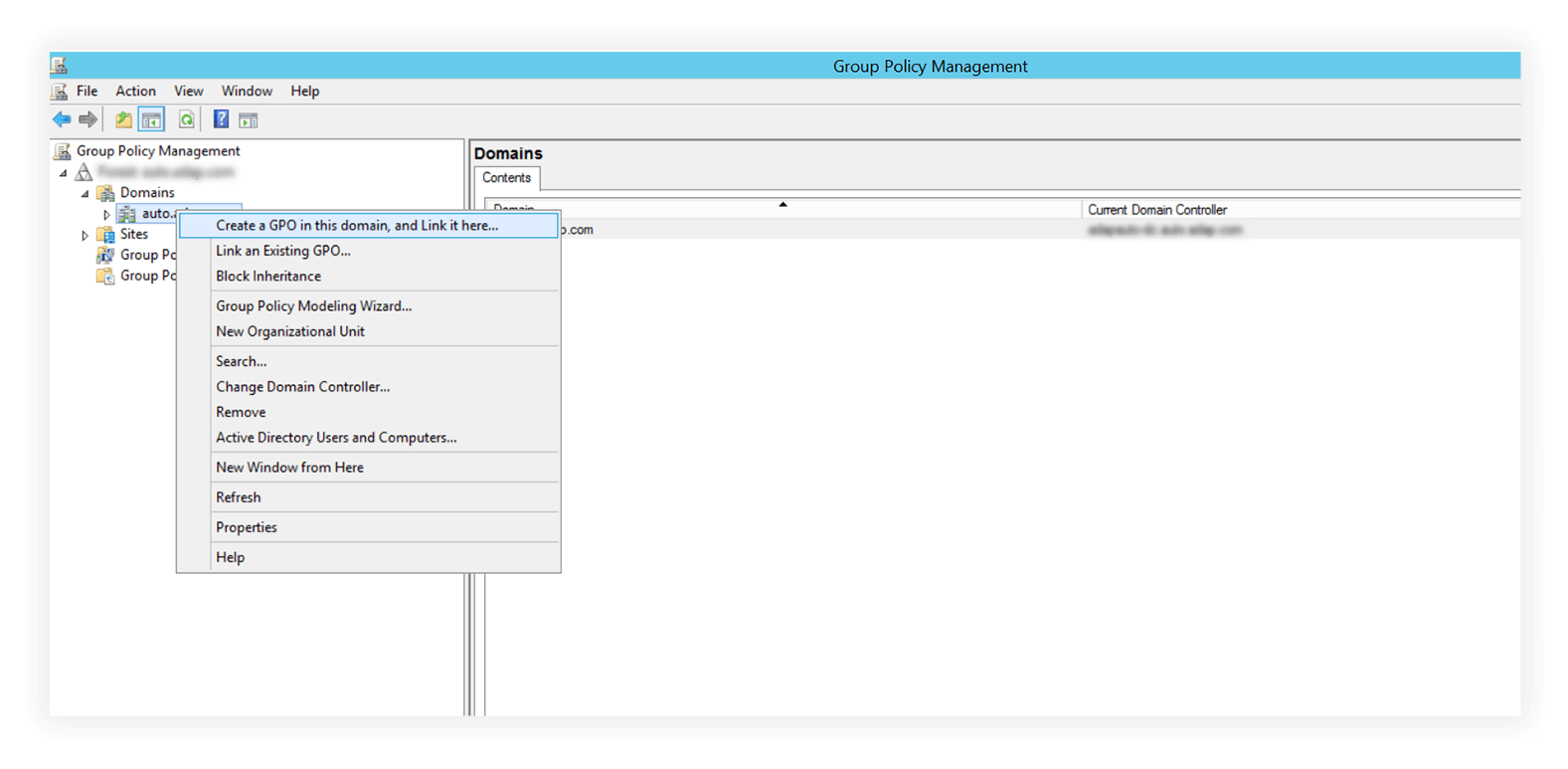
1. In the GPMC, right-click the desired AD unit, say a domain. Select Create a GPO in this domain, and Link it here. Provide the Name, say AD-GPO, and click OK.
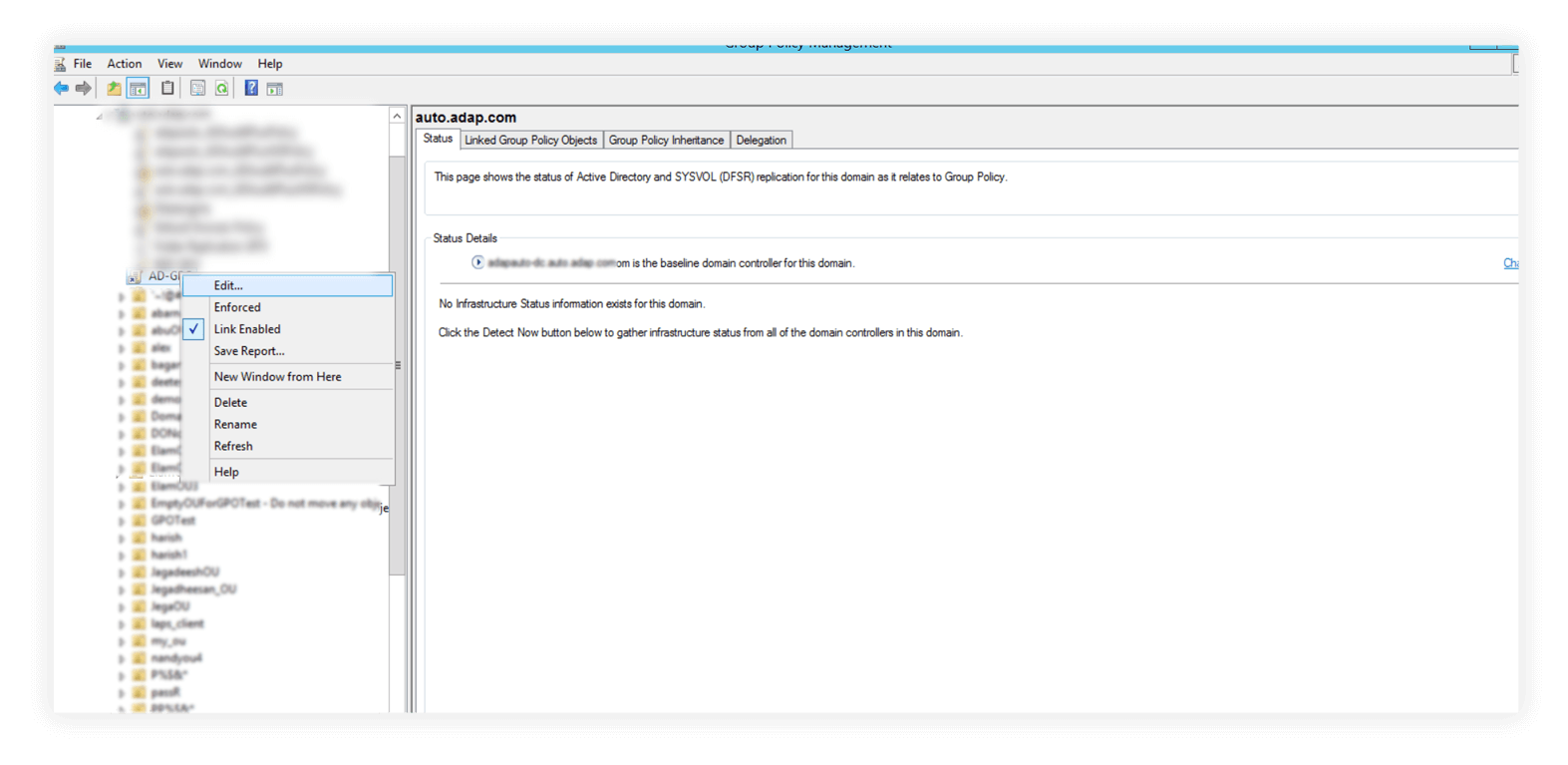
2. Find the policy under the domain. Right-click the policy and click Edit to open the Group Policy Management Editor.
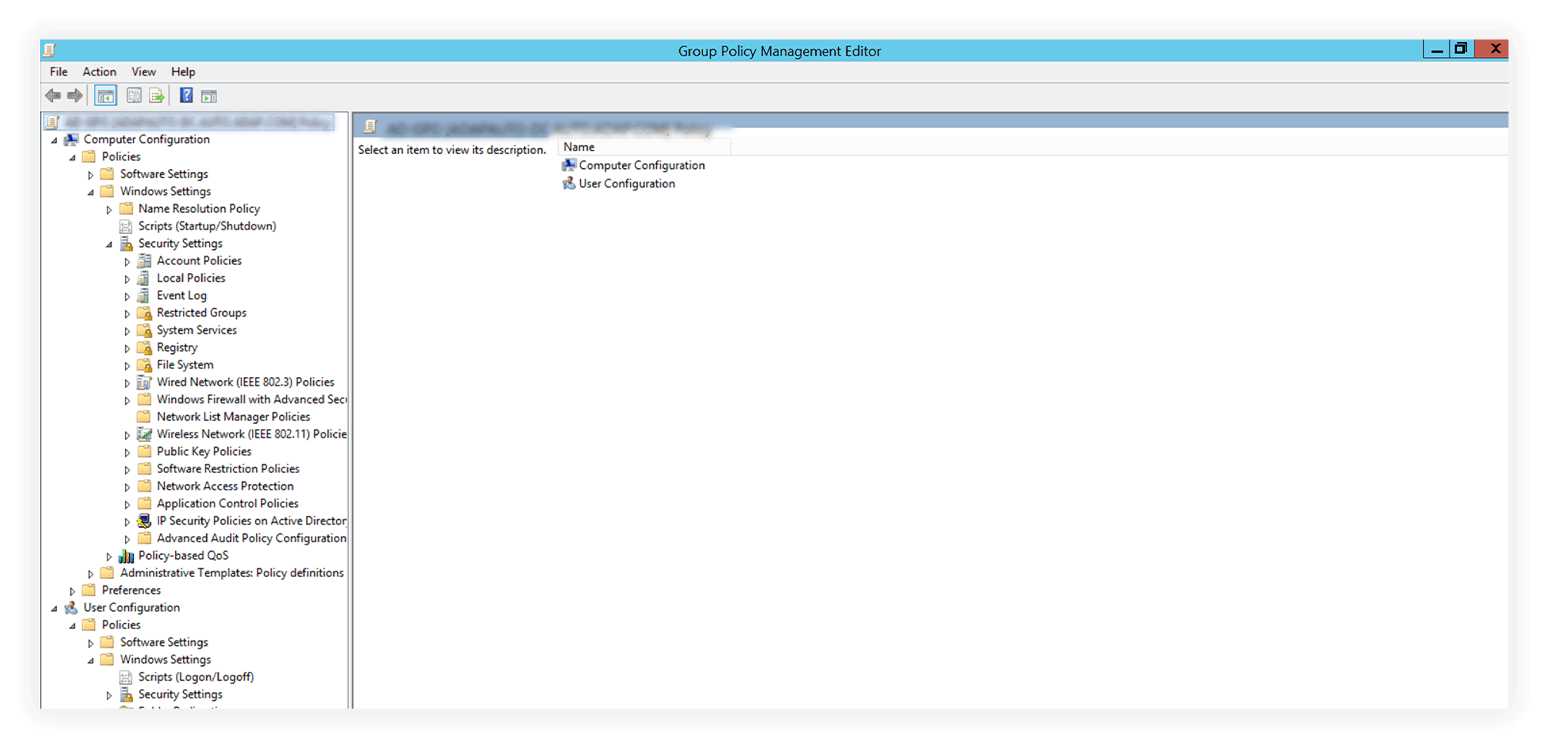
3. Configure the required settings for users and computers by expanding the setting folders in the left pane. User Configuration settings are enforced after a user logs in, whereas Computer Configuration settings are enforced after a user machine starts up.
Points to keep in mind:
Some policies configured may be processed during foreground policy application (upon computer startup or user logon) or background refresh (by default, Group Policies are refreshed every 90 minutes if changes are detected in GPOs). If you change an existing policy, enforce the new settings using the gpupdate command.
How to apply Group Policy to specific users or computers
By default, Group Policies are applied to the Authenticated Users group. However, Group Policies can be applied to selective users or computers using the security filtering option. To apply Group Policy selectively:
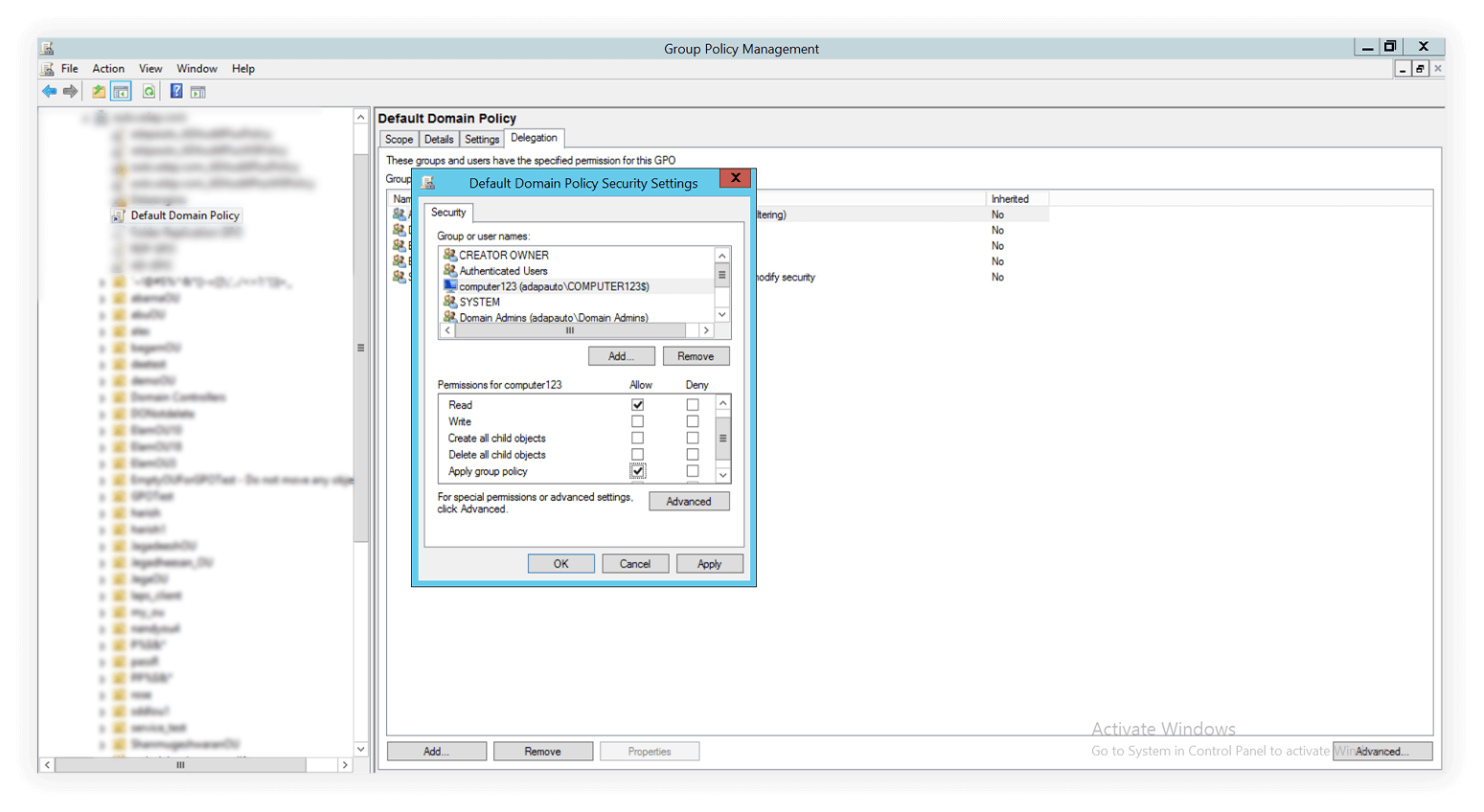
1. Click the GPO, say Default Domain Policy.
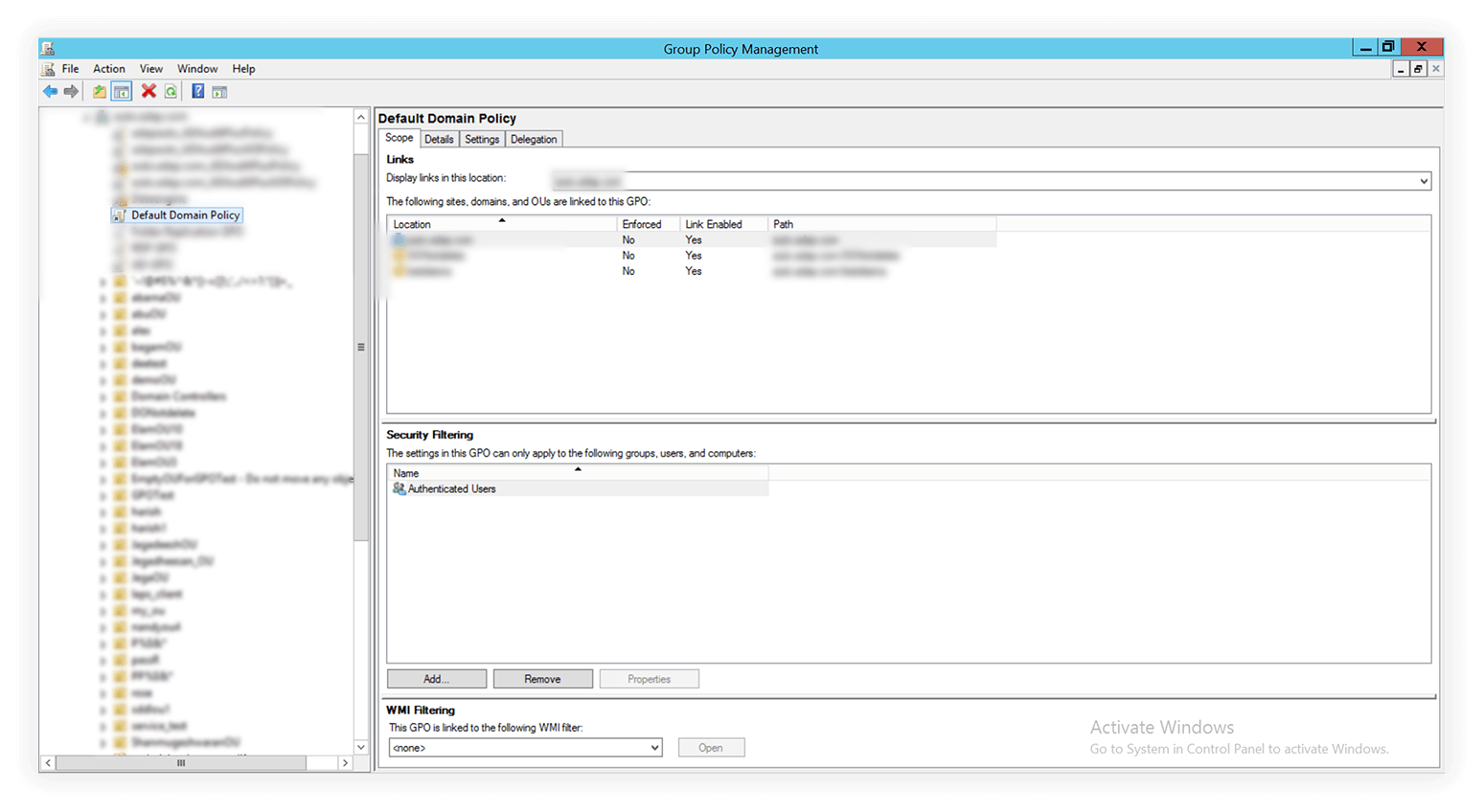
2. Head over to the the Delegation tab in the left panel. Click Advanced in the bottom-left corner.
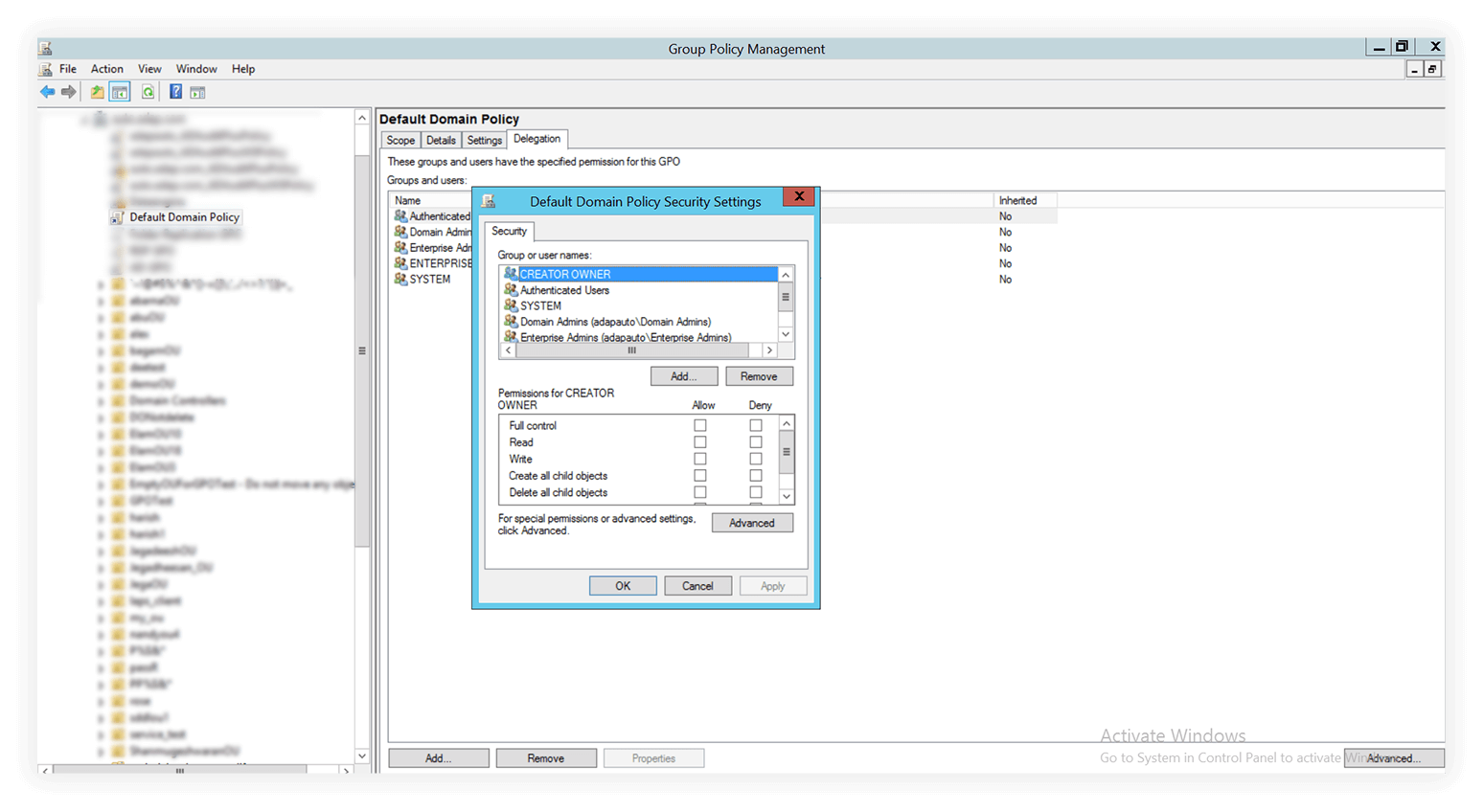
3. Select the Authenticated Users group. Edit the permissions below by de-selecting the checkbox for Apply group policy. Retain the Read permission. Click Apply.
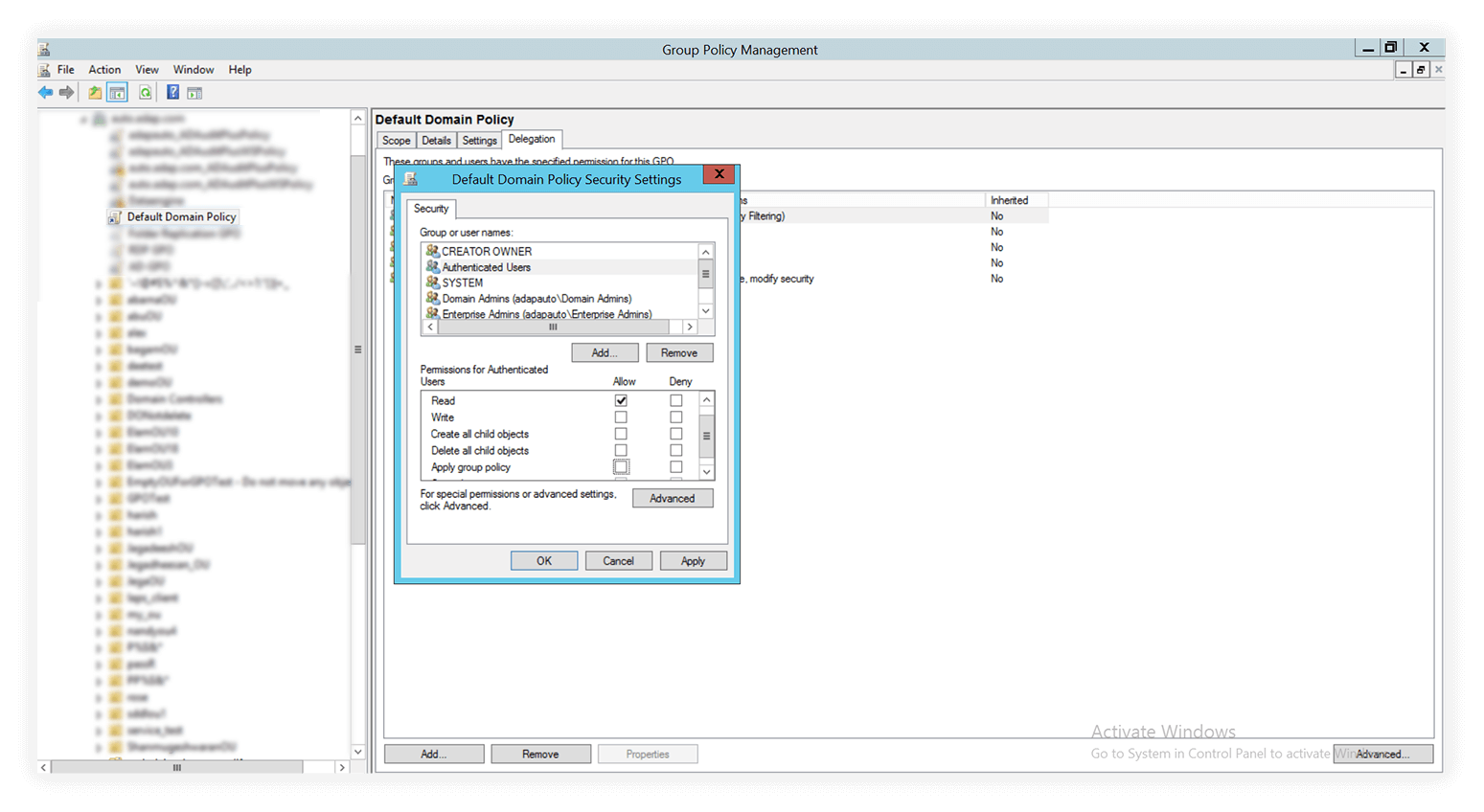
On the same page, click Add... below the Group or user names box. Click Object Types... next to the Select the object type field. Check the Computers option. Click OK.
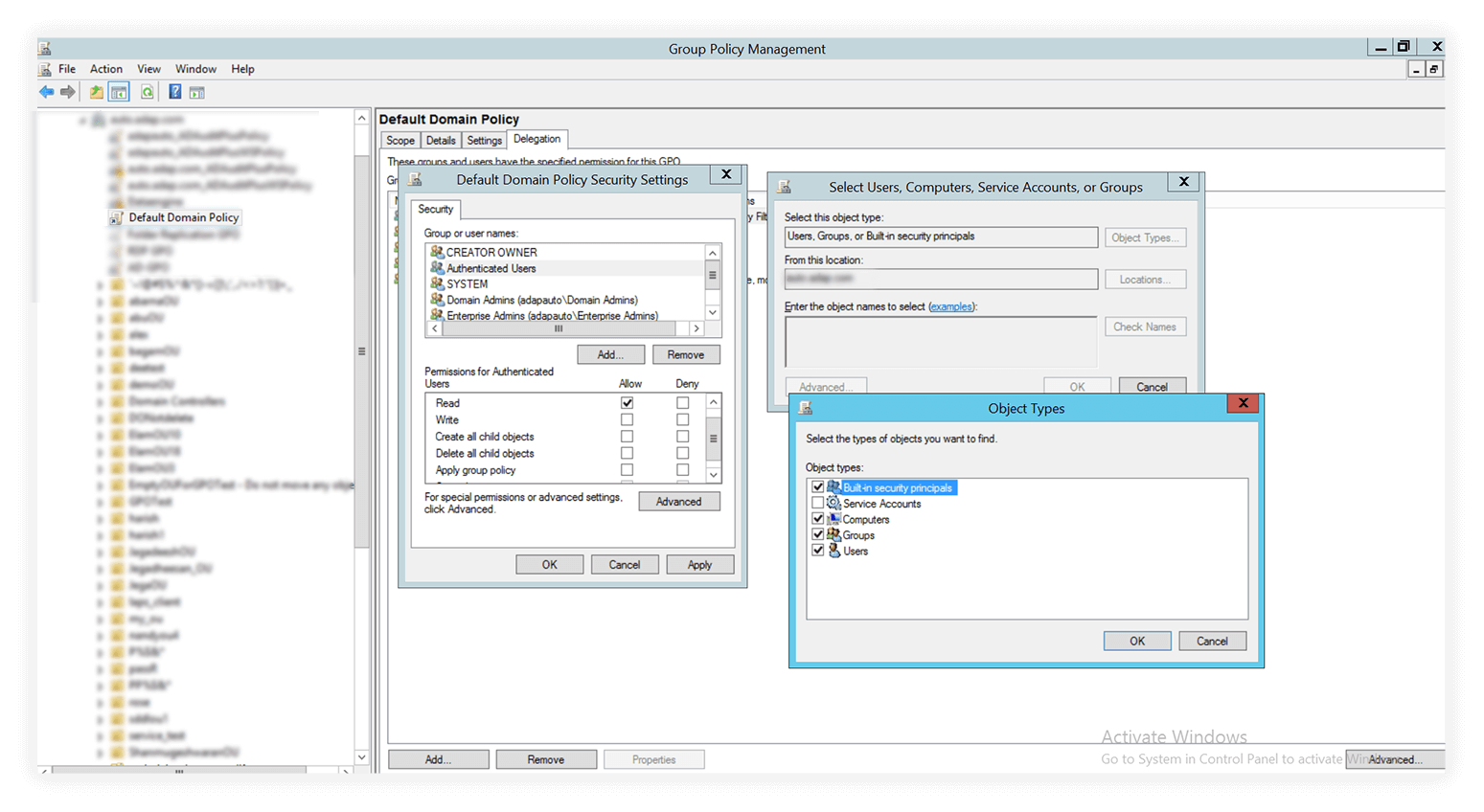
5. In the Select Users, Computers, Service Accounts, or Groups box enter the name of the computer you want to add and click OK. You can also choose to add specific users here.
6. Back in the Default Domain Policy Security Settings, select the user or computer name and modify permissions below by enabling Apply group policy. Click OK.
What are Group Policy preferences?
In addition to policies, preferences can also be configured for users or computers in the Group Policy Management Editor. Unlike Group Policies, preferences are not enforced. Users may be able to modify the preferences configured by sysadmins. However, when the preference configuration is implemented, it is permanent. Unlinking a GPO will remove the Group Policy settings, but the preferences will remain unchanged. Preferences can only be set in the GPMC; there are no local Group Policy preferences in endpoints. Some Group Policy preference examples include scheduling tasks in computers or mapping drives for users.
How ADAudit Plus helps sysadmins streamline GPO and AD auditing
ManageEngine ADAudit Plus helps sysadmins audit, analyze, and secure AD and Azure AD, file servers, Windows servers, and workstations. ADAudit Plus is a UBA-driven change auditor providing visibility through over 250 out-of-the-box reports and real-time alerting. With ADAudit Plus, you can:
- Track GPOs that have been created, modified, or deleted with the GPO change auditor.
- Examine GPO link changes and view the historical trail of GPO changes with our GPO reporting tool.
- Audit changes made to policy settings within user and computer configurations with the Group Policy change reporter.
- Inspect and troubleshoot account lockouts effectively with our account lockout analyzer.
- Analyze AD logon failures using the user logon failure auditing tool.
- Spot insider threats and malware attacks in time with insider threat detection.
- Gain comprehensive insights into changes across users, devices, groups, and more via the Azure AD reporting tool.
- Capture unauthorized file changes with the help of our file change monitoring tool for Windows, NAS, Synology, Hitachi, and more.
- Monitor regular and remote workers' attendance with our employee productivity tracker.
- Achieve data regulatory compliance with ease using Active Directory compliance reporting for the GDPR, HIPAA, PCI DSS, and other mandates.
Try all these features and more for 30 days with a free, fully-functional trial. Alternatively, you can also schedule a personalized demo for a guided walkthrough of ADAudit Plus.
Don't wait for your annual compliance audit.
- Audit your AD and Azure
- Monitor user logon
- Troubleshoot AD lockouts
Thanks!
Please check your inbox for demo details.