Kerberos authentication
What is Kerberos authentication?
Kerberos authentication is a network protocol developed for user identity authentication and in single-sign on implementations. It was developed by the Massachusetts Institute of Technology in the 1980s and is being continuously enhanced to keep up with current security needs. The Kerberos protocol is more secure than the New Technology LAN Manager (NTLM) authentication, widely used in the '90s, which sends password hashes through the network during the authentication process, leaving the system open to pass-the-hash attacks. Kerberos is widely preferred for authentication and is supported by major operating systems in use including Microsoft Windows, Apple macOS, and Linux.
How does Kerberos authentication work?
Kerberos uses symmetric key cryptography, where the same or similar keys are used for both encryption and decryption of the cipher text. It also requires the use of trusted third-party authorization where the third-party validates the interactions between the client and server. Accordingly, aside from the client and server, there is a third participant: the key distribution center (KDC). The Kerberos process needs the following participants:
- The client, or user device, that sends the request to authenticate.
- The Windows domain controller that supports the Kerberos service by hosting the KDC role.
- The application server that hosts the service or resources the user needs access to.
Kerberos authentication steps
The Kerberos authentication process can be depicted as shown below:
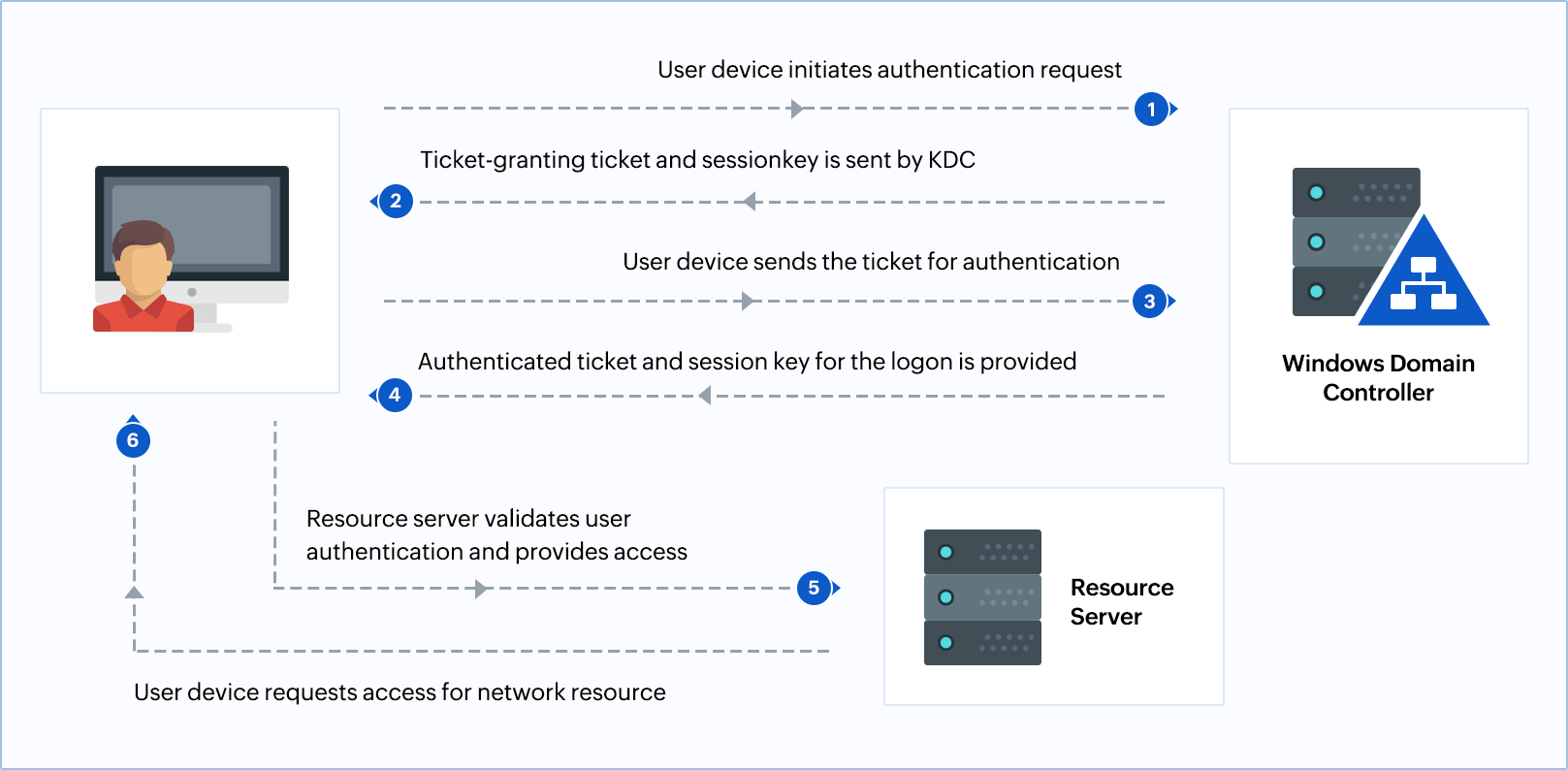
To summarize the interaction between the client, KDC, and the authenticating server or domain controller:
- The user submits the credentials when prompted by the client. This triggers a request for authentication to the server hosting the Kerberos service.
- The authentication server (part of the KDC server) verifies and authenticates the client based on the database of credentials stored. Upon successful validation, the authentication server issues the ticket-granting ticket (TGT) and a session key, both encrypted based on the user's password.
- The client decrypts the TGT and session key, and sends it to the ticket-granting server (also part of the KDC server). This server then, decrypts the TGT and issues the ticket needed for service. The final ticket is sent to the application server by the client to gain access to the required resource.
Advantages and disadvantages of Kerberos authentication
As established earlier, Kerberos offers a lot of advantages over NTLM authentication. But it is not without its disadvantages. Some of the advantages and disadvantages include:
| Advantages | Disadvantages |
|---|---|
| It is supported by major operating systems in use. | It has a single point of failure: the KDC. If there's only one KDC to authenticate, any downtime may make it impossible for authentication. |
| The tickets issued are valid for a limited period. If stolen, there is a short time period when attackers can misuse the tickets. This is unlikely, and this process is considered secure. | If the KDC is compromised, credentials of the user may be revealed to attackers. |
| User passwords are not sent over the network in the authentication process. | Kerberos authentication is susceptible to dictionary attacks. If users have weak passwords that include common dictionary words, attackers can use password crackers to retrieve the credentials. |
| User credentials input during the interactive logon will be used to authenticate all service requests. The user does not have to input them again. | Kerberos requires time synchronization across servers and clients to work effectively. |
Auditing Kerberos authentication service
Every step in the Kerberos authentication process generates an event in the event viewer. For example, when a user enters the correct credentials and it has been verified, event ID 4768 is logged. When the user input credentials that cannot be verified, a failure event with the ID 4771 is logged. Correlating and analyzing these events, especially failure events, will help detect suspicious behavior. A high volume of failed logon events can indicate a potential brute-force attack. It is not easy to scour through the numerous security logs recorded in the Windows Event Viewer. You can effectively track security logs for malicious events with the help of the right tool.
How ADAudit Plus helps in streamlining Active Directory auditing
ManageEngine ADAudit Plus helps sysadmins audit, analyze, and secure Active Directory and Azure AD, file servers, Windows servers, and workstations. ADAudit Plus is a UBA-driven change auditor providing visibility through over 250 out-of-the-box reports and real-time alerting. With ADAudit Plus, you can:
- Inspect and troubleshoot account lockouts effectively with our account lockout analyzer.
- Analyze Active Directory logon failures using user logon failure auditing tool.
- Spot insider threats and malware attacks in time with insider threat detection.
- Gain comprehensive insights into changes across users, devices, groups, and more via the Azure AD reporting tool.
- Capture unauthorized file changes with the help of our file change monitoring tool for Windows, NAS, Synology, Hitachi, and more.
- Track changes to group policy settings with the GPO change auditor.
- Monitor regular and remote workers' attendance with our employee productivity tracker.
- Achieve data regulatory compliance with ease using Active Directory compliance reporting for the GDPR, HIPAA, PCI DSS, and other mandates.
Try all these features and more for 30 days with a free, fully-functional trial. Alternatively, you can also schedule a personalized demo for a guided walkthrough of ADAudit Plus.
Don't wait for your annual compliance audit.
- Audit your AD and Azure
- Monitor user logon
- Troubleshoot AD lockouts
Thanks!
Please check your inbox for demo details.