Just-In-Time Access
Just-In-Time Access Explained
Just-in-Time (JIT) access in Endpoint Central's Application Control allows administrators to grant temporary, limited privileges to users for specific tasks. This reduces security risks associated with providing continuous administrative rights and allows for granular control over application elevation policies. With JIT access, users are granted access only when they need it and for the specific tasks they require for a limited period of time. It can also be configured to be applied only to specific applications based on a wide range of criteria.
The Importance of Just-In-Time Access
JIT access enhances security by granting limited, temporary privileges. It effectively minimizes the potential for unauthorized access and reduces the risk of insider threats. This approach ensures that users have the required access to perform their tasks without compromising overall security by granting continuous administrative rights. Implementing JIT access is a strategic decision that can strengthen the organization's security posture and minimizes the potential for data breaches.
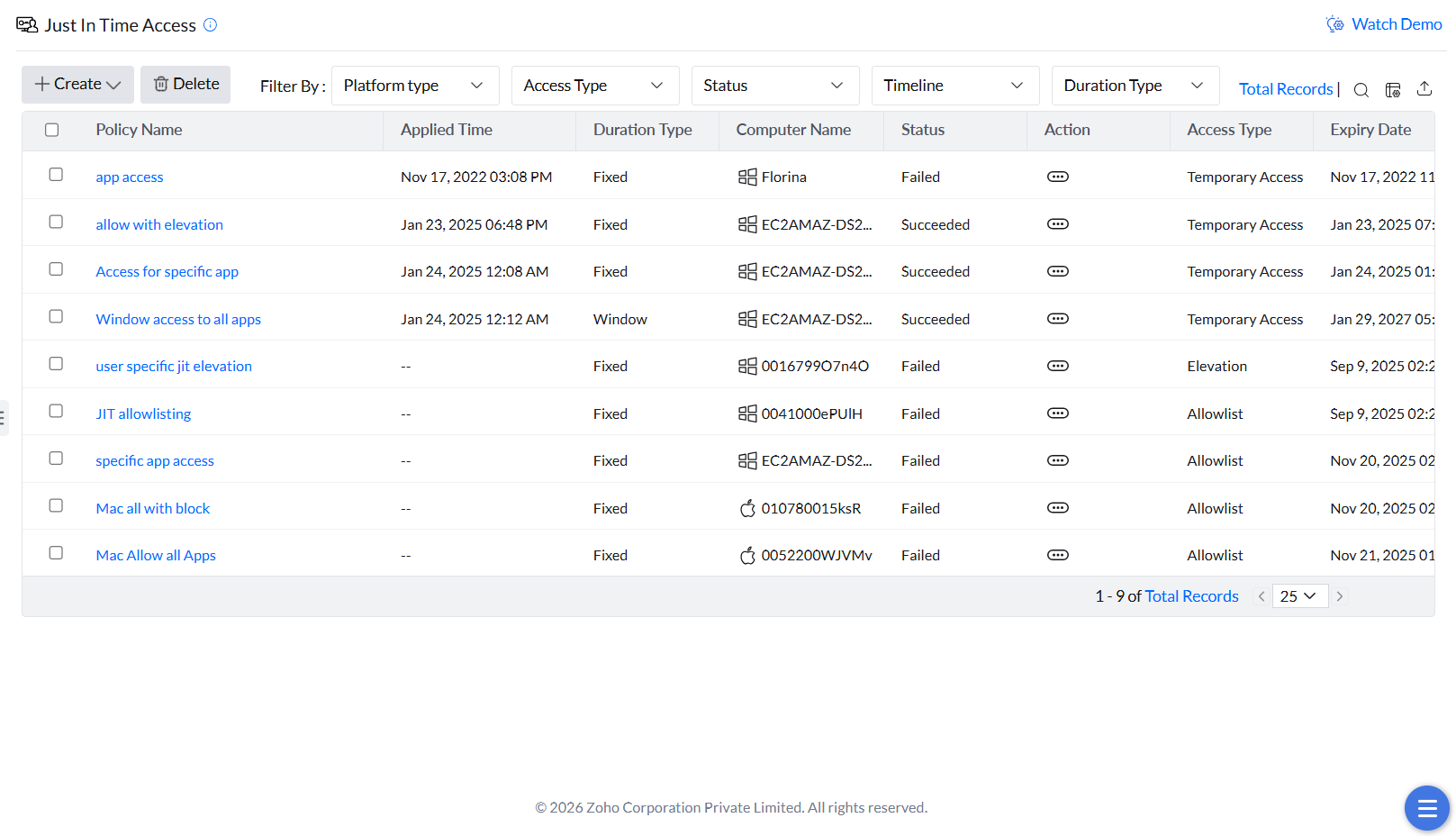
Configuring Just-In-Time Access
The temporary access can be provided to specific computers through the following steps:
- Login to the Endpoint Central web console and navigate to Application Control -> Just in Time Access.
- Click Create to delegate a new JIT access policy and select Application Elevation.
- Provide the Name and Description for the policy.
- Provide the Computer Name for which you want to provide JIT access and select the User Name.
- Select the specific user or to grant access to all users on this computer, select All users.
- Select the duration type: Fixed or Window. If the duration type is fixed, provide the duration of access and if it's a window, provide a window time frame for which you want to provide the JIT Access.
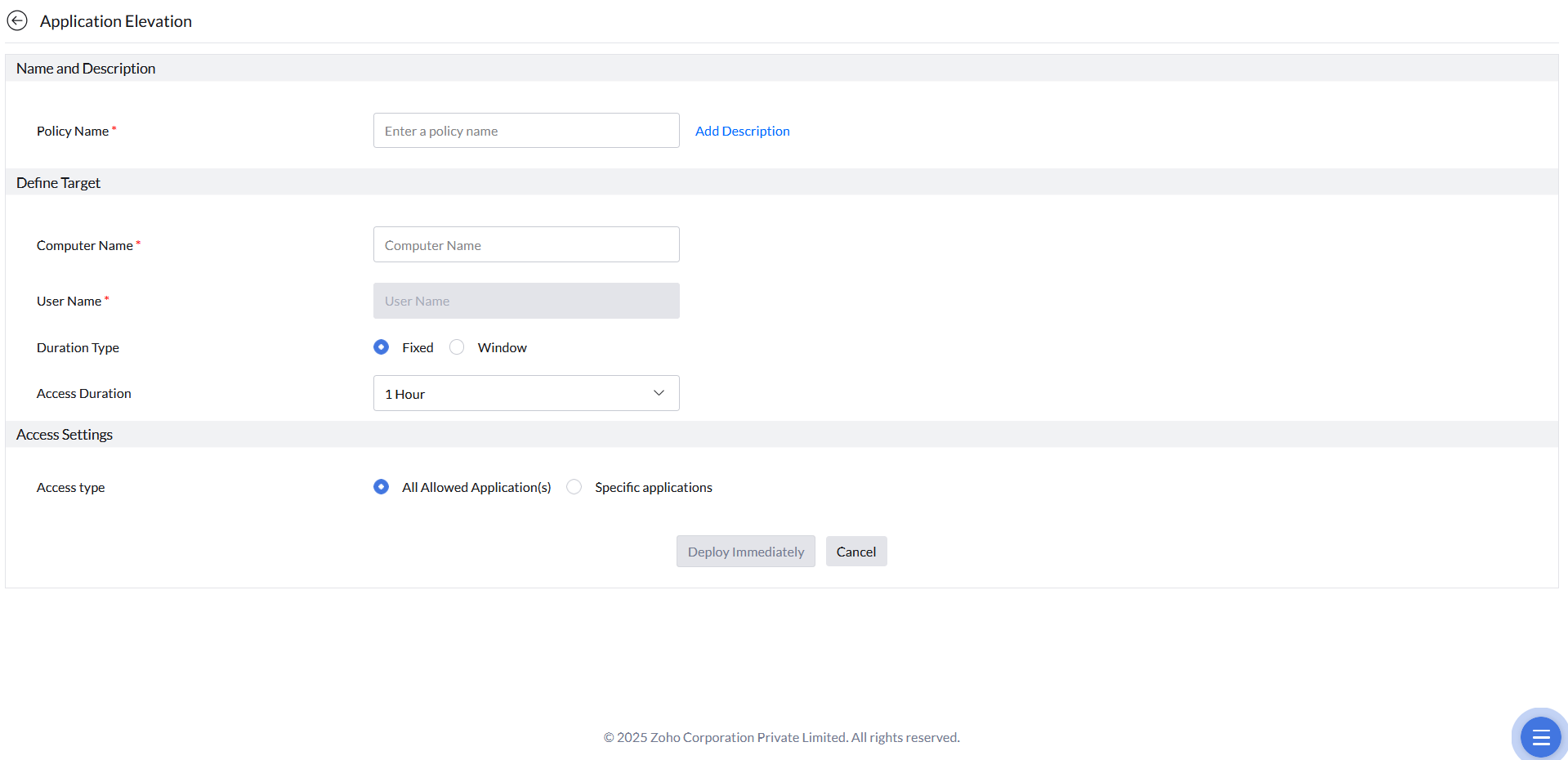
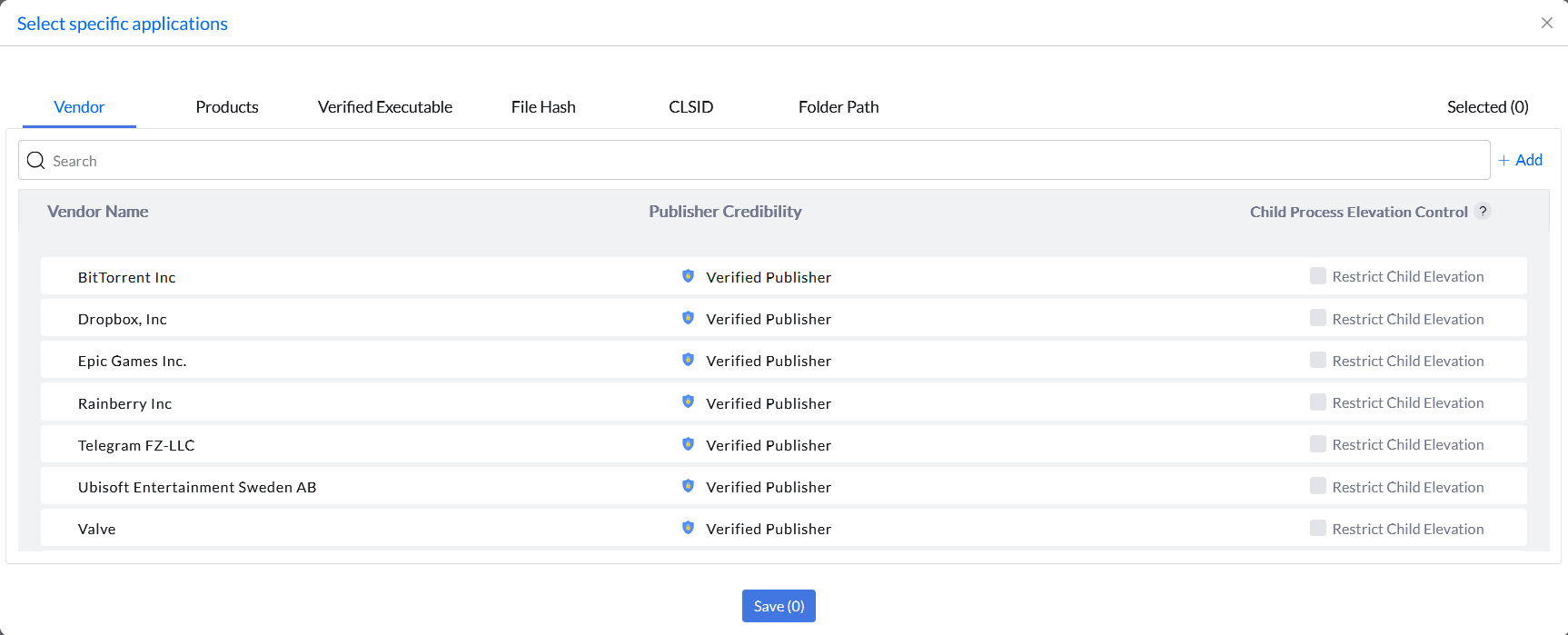
- In the Access Settings, the Just In Time Access for self-elevation option will grant the user to self-elevate their privileges to all allowed applications or specific applications. If you choose All Allowed Application(s), the user can self-elevate any allowlisted application. If you choose Specific applications, the user can self-elevate only the applications selected. The specific applications for elevation can be added using the rule types such as Vendor, Products, Verified Executable, File Hash, CLSID, and Folder Path.
- Click Deploy Immediately.
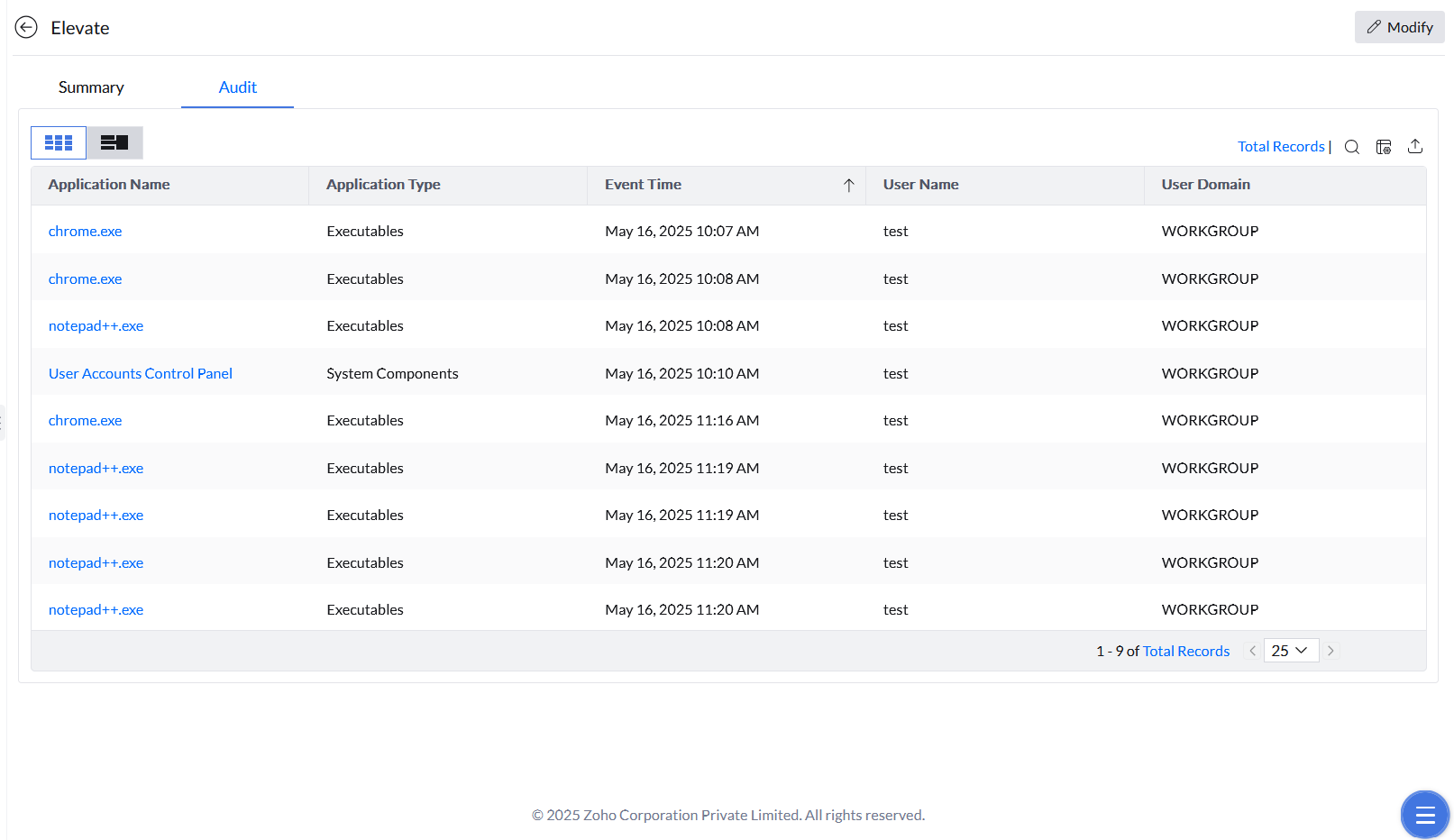
Just-In-Time Events Report
The events occurring under each JIT policy are accessible by clicking the desired policy and selecting the Audit tab.