- Quick Links
- Related features
- Windows log management
- Syslog management
- Server log management
-
Application log management
-
Network device monitoring
- Log management
- Related products:
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are among the most sophisticated network security devices in use today. They inspect network packets and block suspicious ones, as well as alert administrators about attack attempts. These systems' logs contain valuable network threat information about attack types, devices being targeted, and more.
With ManageEngine EventLog Analyzer, you can monitor IDS and IPS logs and extract the information they provide to secure your network further. It makes network device monitoring simple by automatically collecting IDS/IPS logs and storing them in a central location. Predefined reports cover various aspects of your network and help you gain perspective on your network's overall security standing. Instant alerts ensure you're the first to know when something suspicious is detected. For instance, malicious traffic alerts let you know when intruders try to access your network.
EventLog Analyzer also allows you to search the collected logs using several powerful search options and securely stores logs for as long as you need them.
EventLog Analyzer generates IDS/IPS security reports that provide information on:
The most targeted devices on your network.
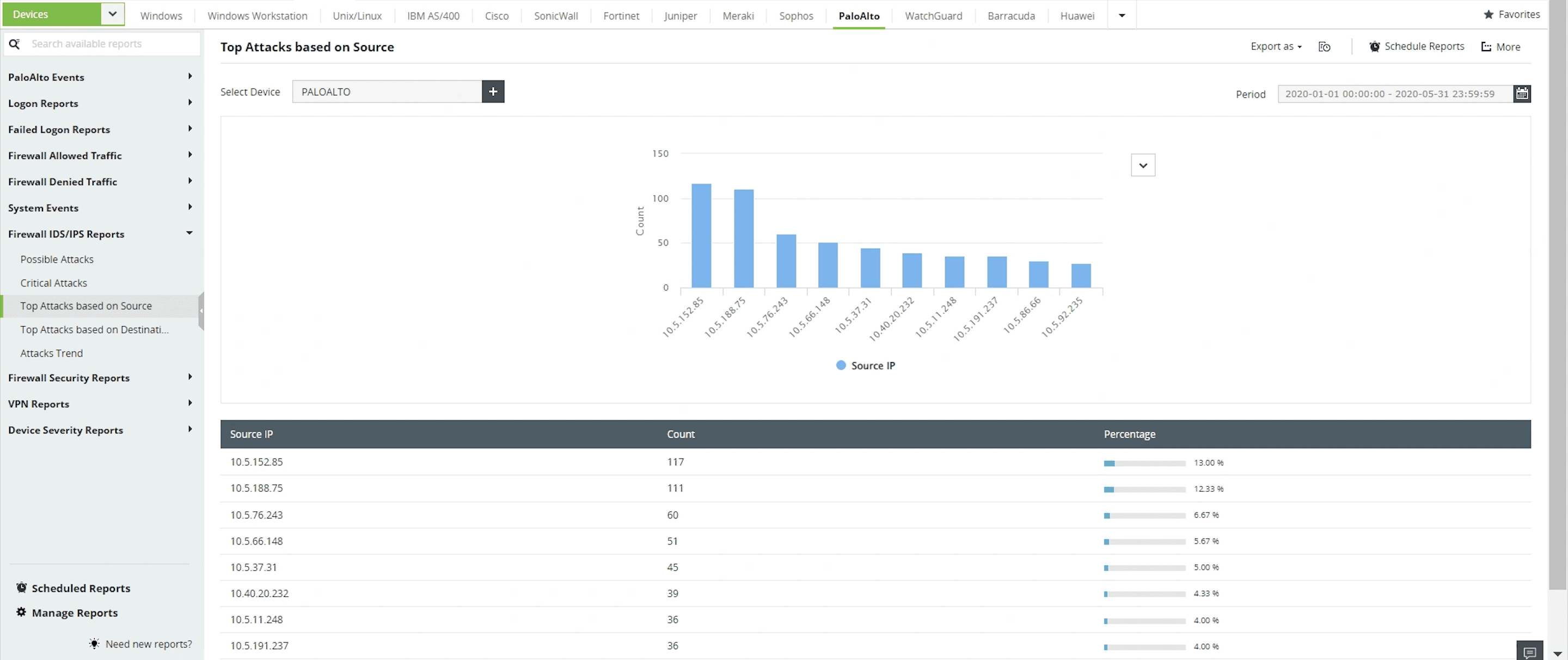
Attacks occurring on your network, with information on the most frequent attacks and the source of these attacks.
Attack trends.
These reports help you understand what types of attacks your network is susceptible to, which network devices need to be secured further, how to decide which malicious traffic sources to target, and more.
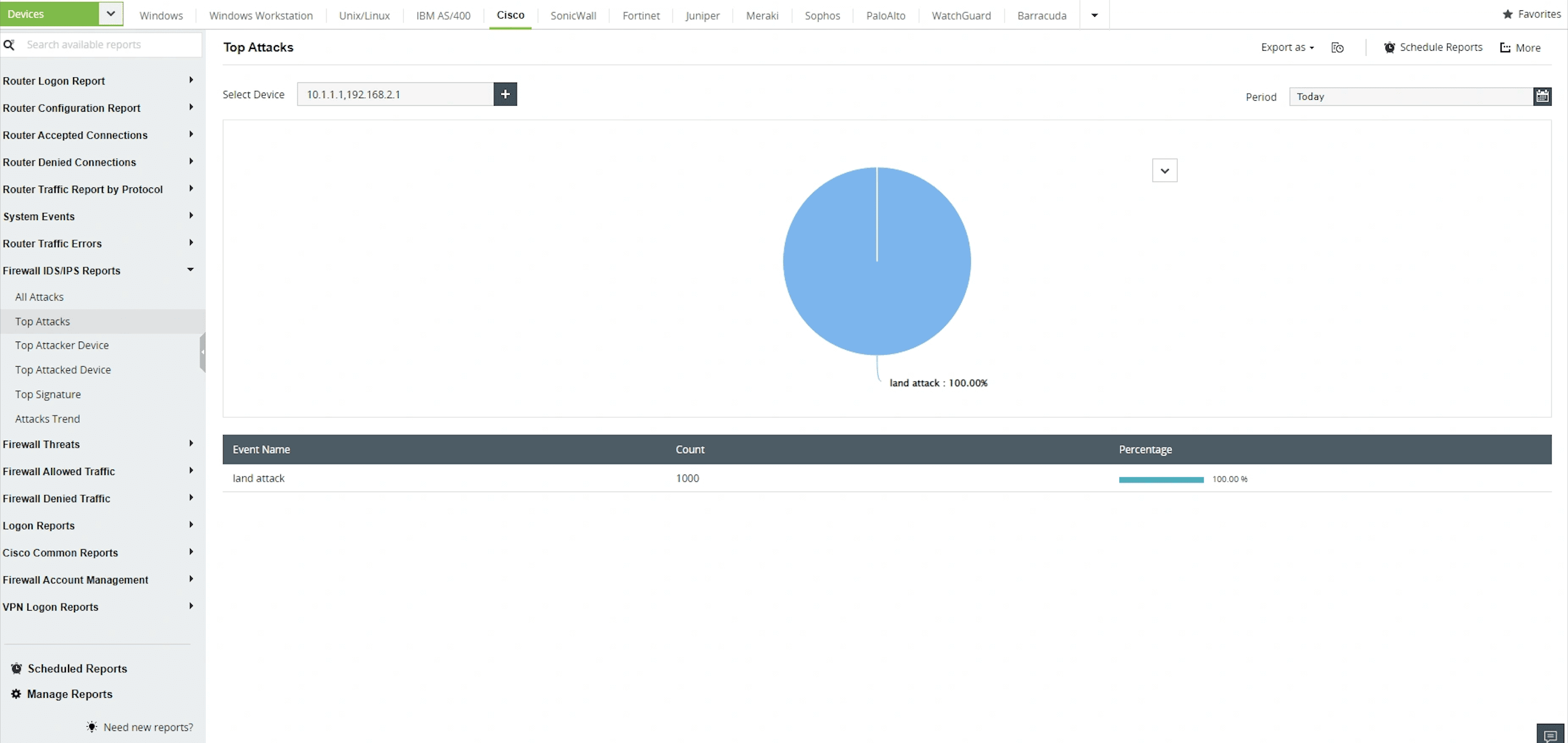
Prevent network intrusions by analyzing attacks occurring on your network classified on the basis of source and destination addresses.
Monitor and protect devices on your network that were targeted by attackers on a regular basis.
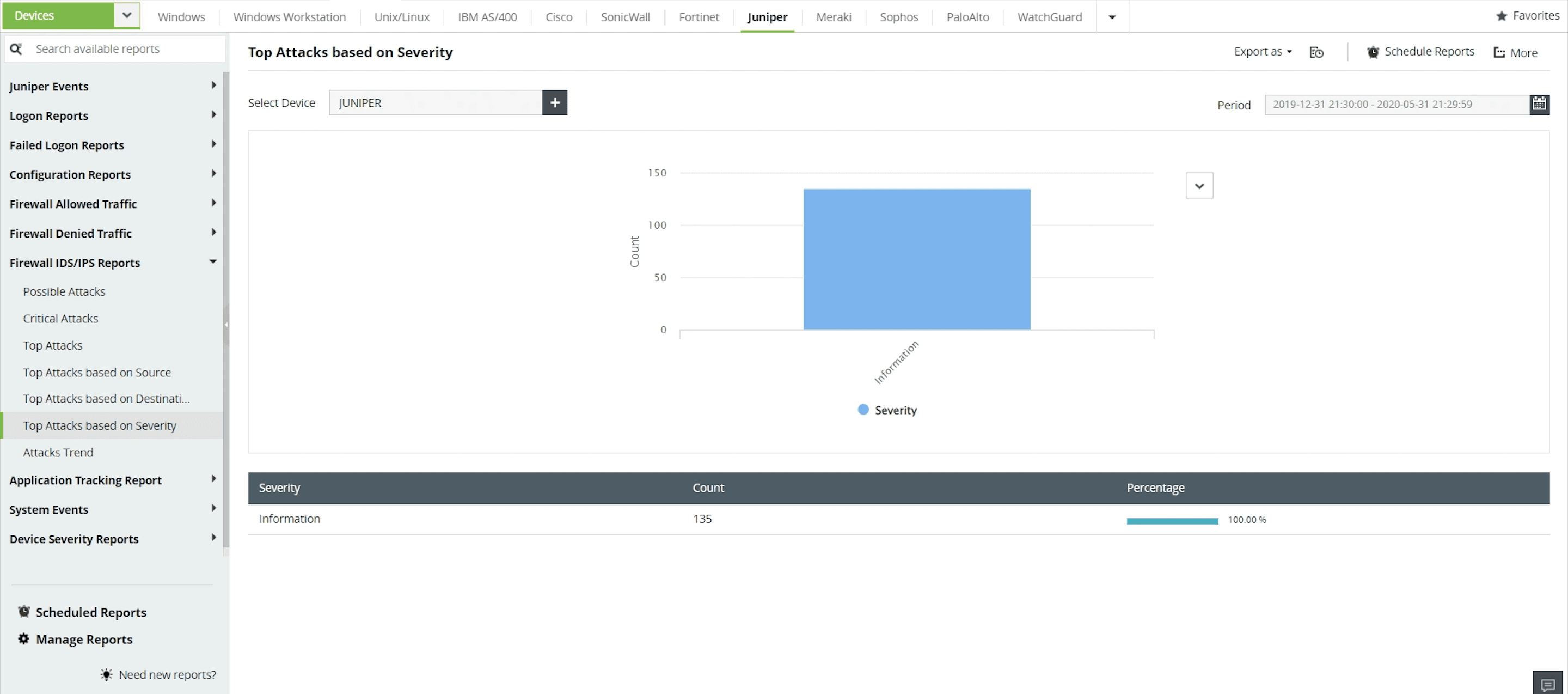
Analyze attacks in your IDS/IPS devices by categorizing them on the basis of their status: Emergency, Alert, Critical, Error, Warning, Notice, Information, or Debug.
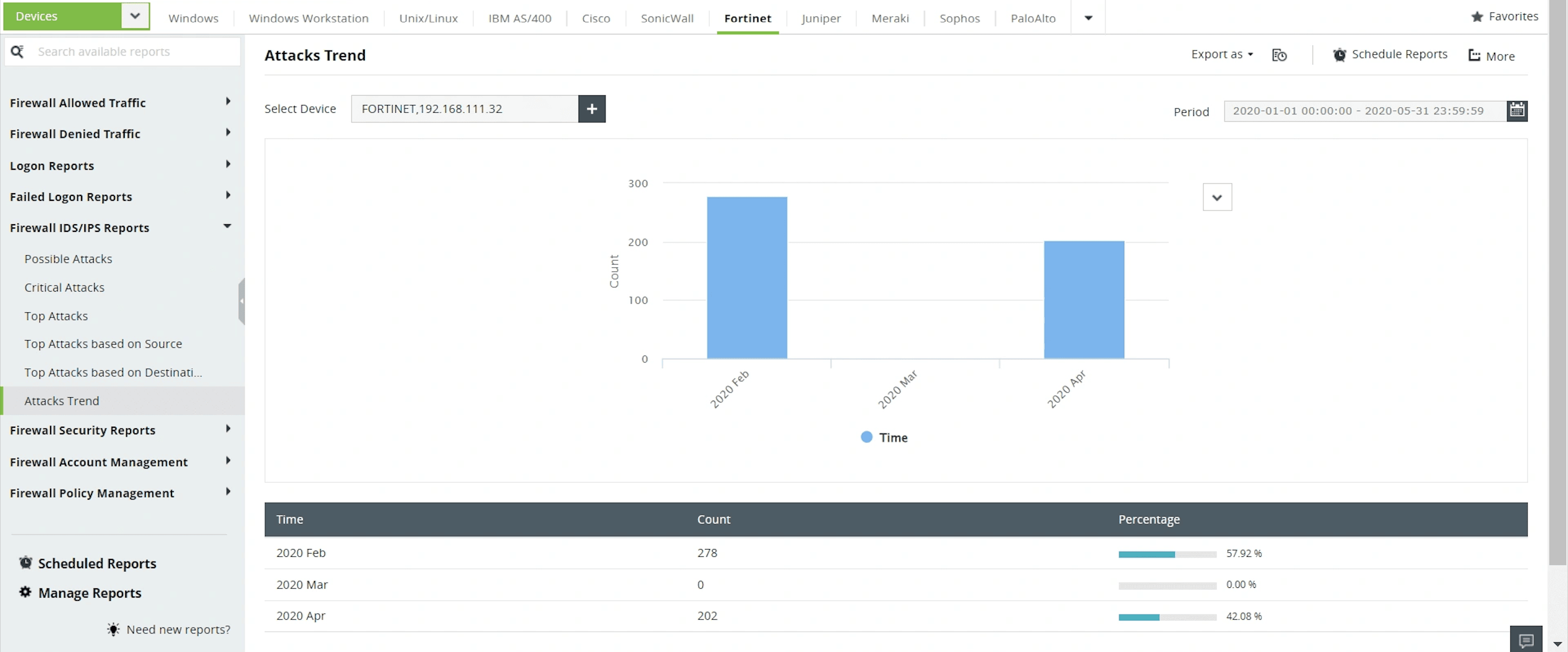
The Attacks Trend report gives you a timeline of various attacks that occurred over a given period of time.
Analyze firewall traffic, security threats, policy changes, logons and more for firewall solutions from top vendors including Cisco, Checkpoint, Fortinet, Watchguard, and Sonicwall.
Search through raw and formatted logs with EventLog Analyzer's powerful log search engine, then perform a root cause analysis to identify the cause of a security attack.
Comply with various regulations such as ISO 27001, HIPAA, FISMA, PCI DSS, GLBA, and more with pre-defined compliance reports and compliance violation alerts.
Visualize log data collected from multiple sources and gain valuable insights into important network security events using EventLog Analyzer's intuitive dashboards and graphical reports.
Gain actionable insights into your network activities by collecting, parsing, and analyzing logs from heterogeneous devices in your organization network.
View important security information obtained from your logs in the form of graphical reports. EventLog Analyzer comes with 1,000+ pre-defined reports that are generated automatically upon log collection.
Identify suspicious activity in your organization network by correlating logs from multiple devices. Utilize 30+ pre-defined correlation rules or create rules as per your requirements using EventLog Analyzer's correlation rule builder.
Limit the time taken to detect and respond to security incidents with EventLog Analyzer's incident detection and response system. Handle security incidents quickly by automatically assigning tickets to appropriate security administrators.
Integrate with commercial and open source threat feeds to detect malicious sources interacting with your organization network.