Gain unparalleled visibility, detect threats in real time, and ensure compliance with the security monitoring and analytics platform.


Ingest log data from various sources, including Windows and Linux servers, endpoints, databases, business apps, cloud environment, and more.
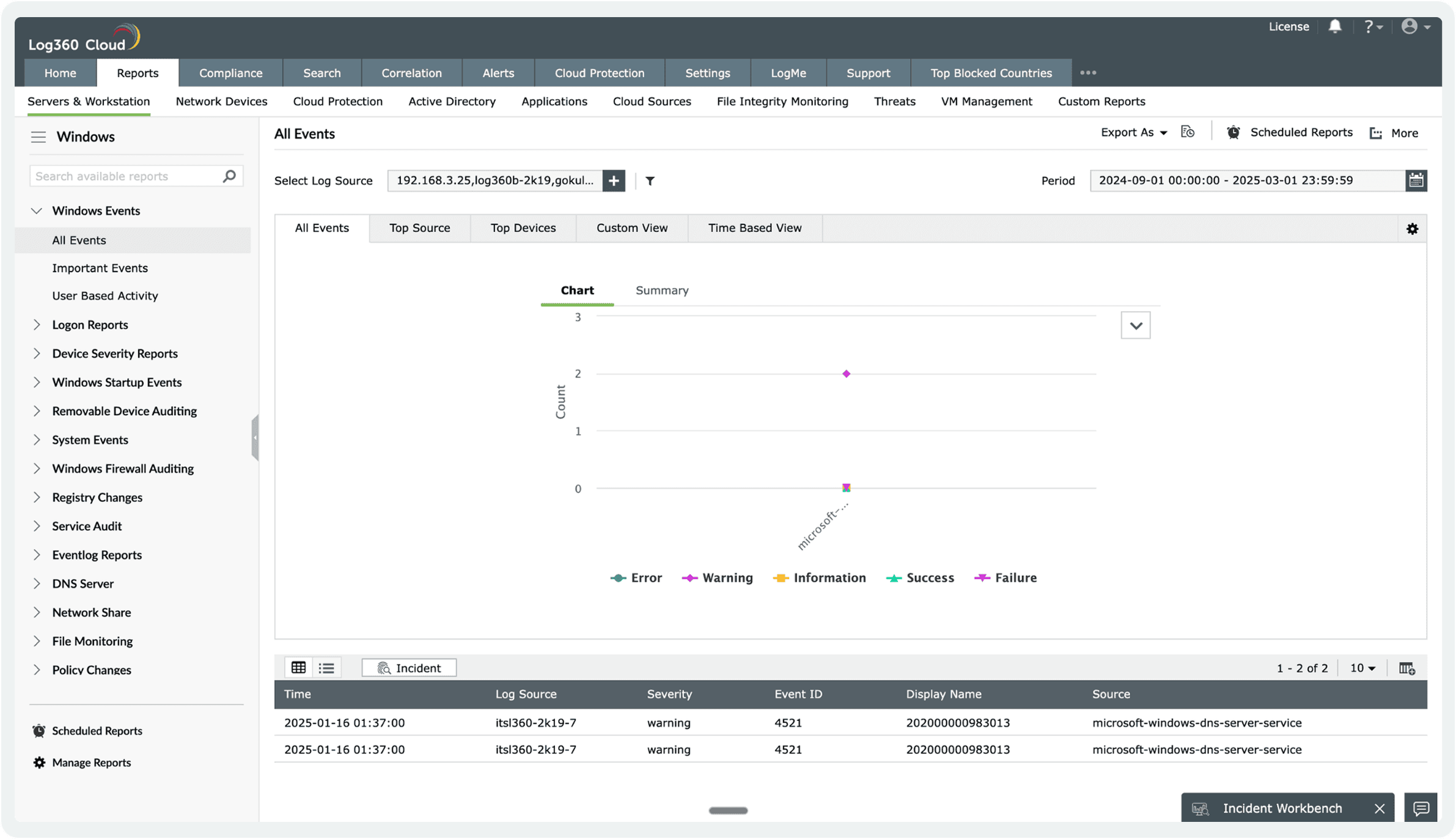
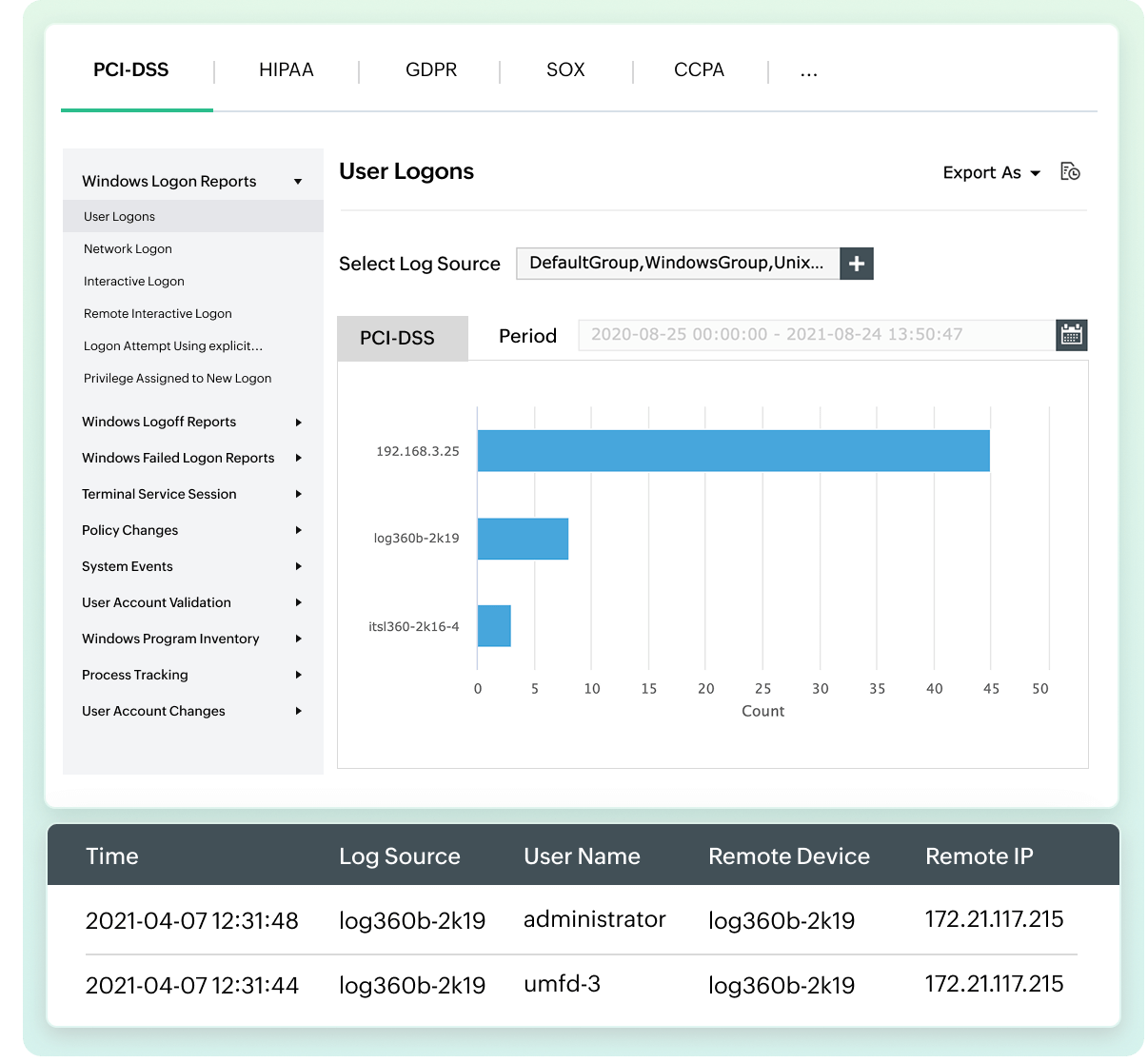
Investigate critical security incidents thoroughly by examining who performed actions, their location, and the timestamps, all facilitated by predefined security audit reports
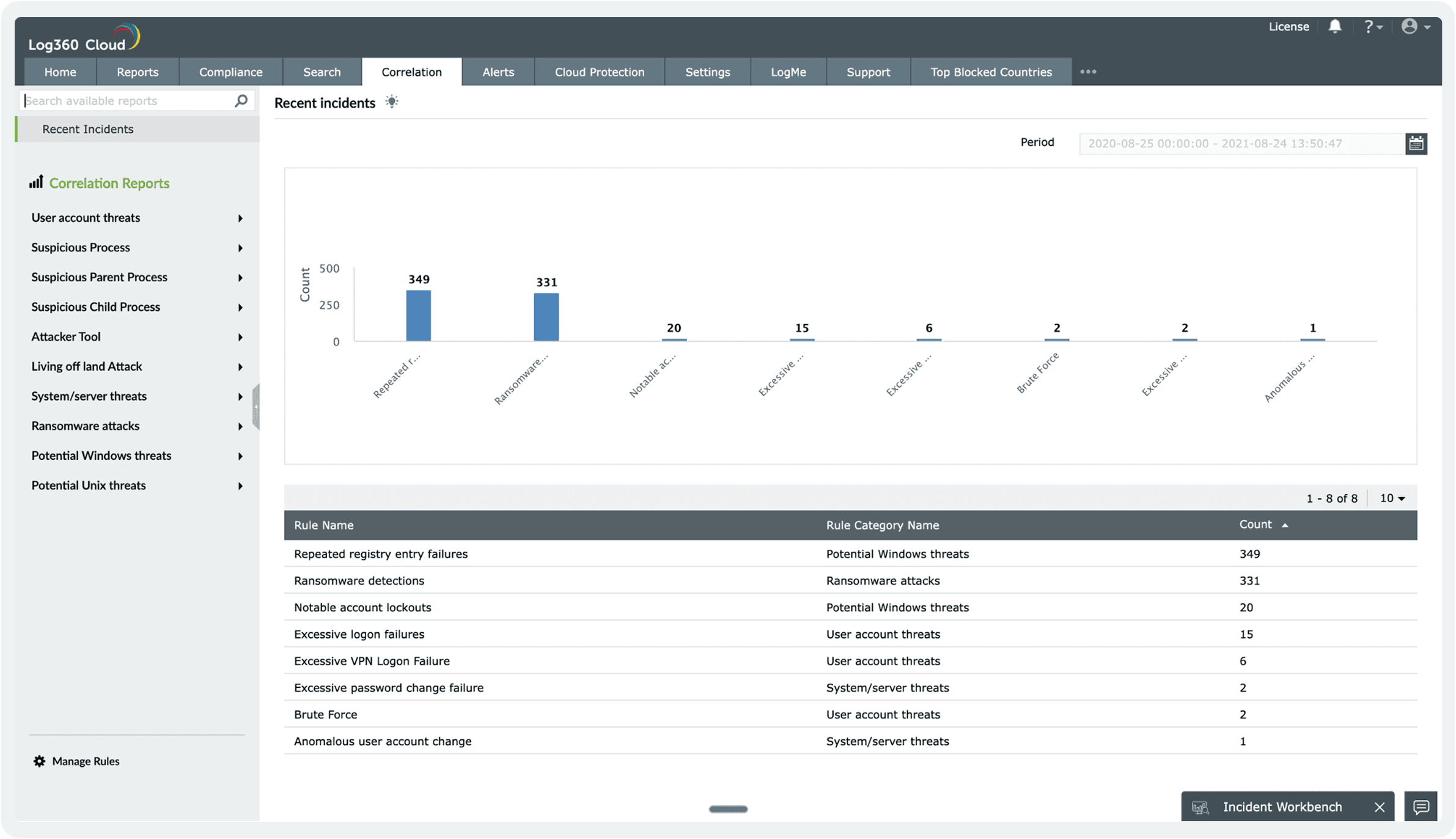
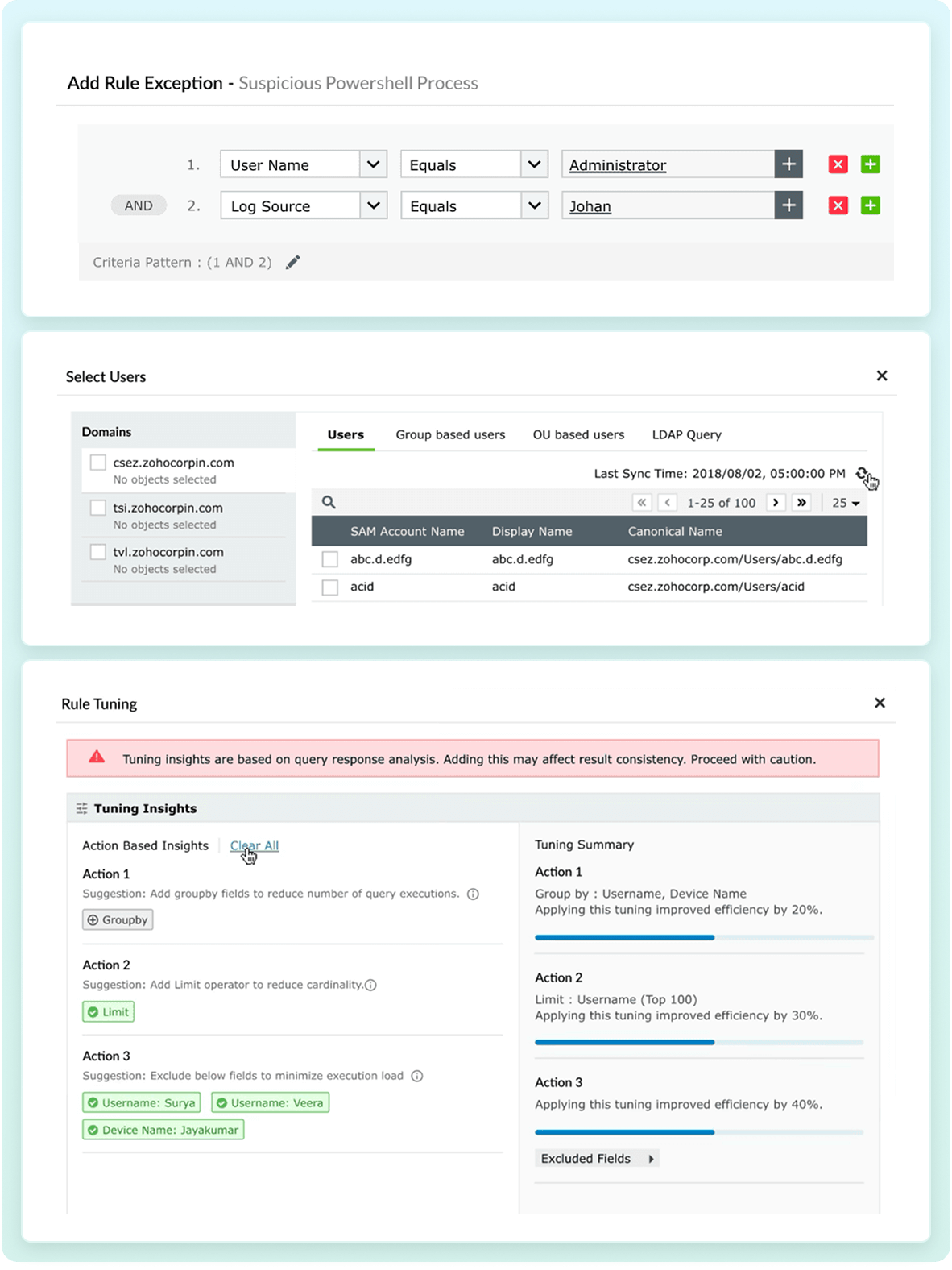
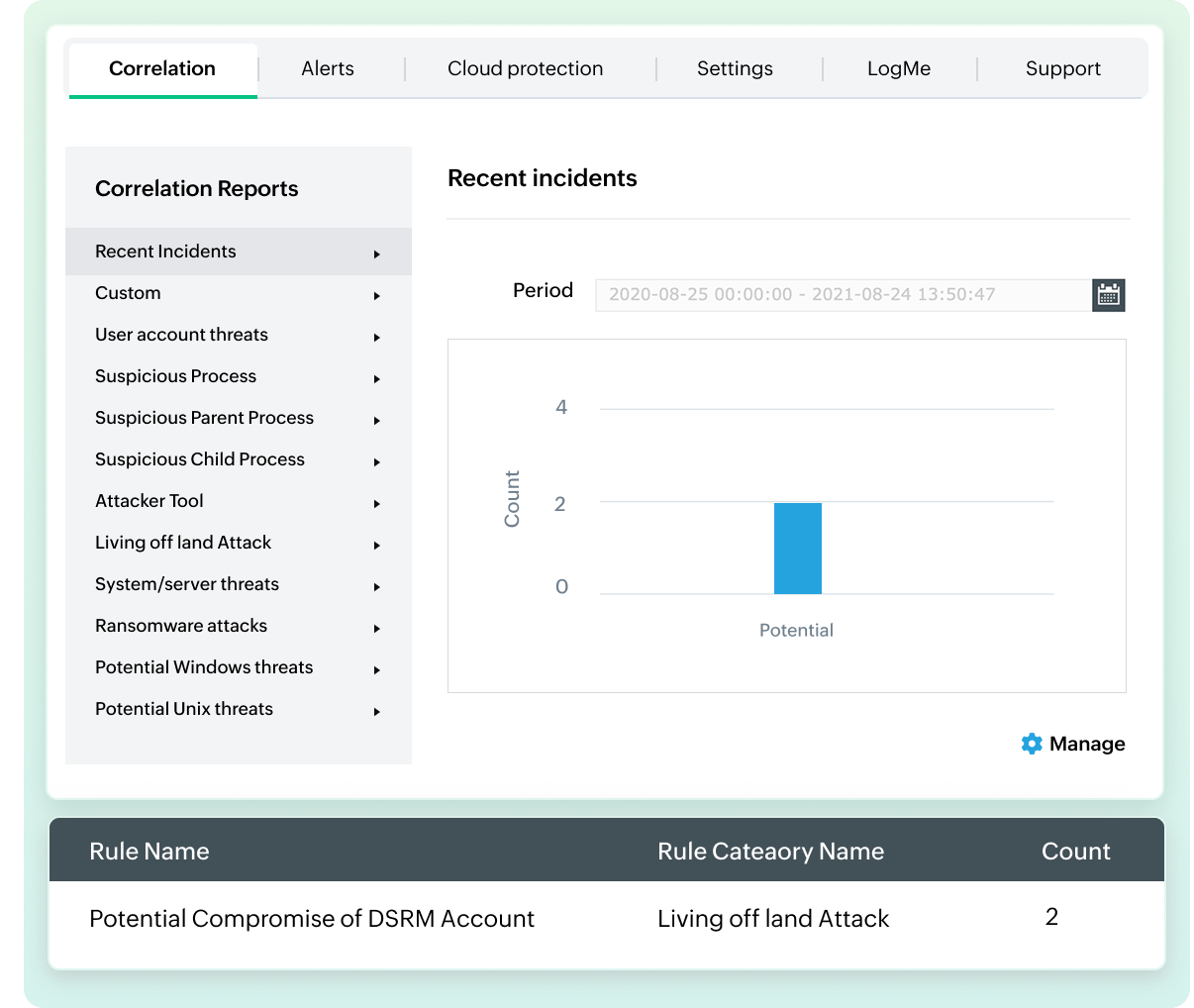
Instantly identify complex threats by correlating events across your entire network. The engine analyzes logs in real-time, triggering alerts on suspicious patterns and anomalies.
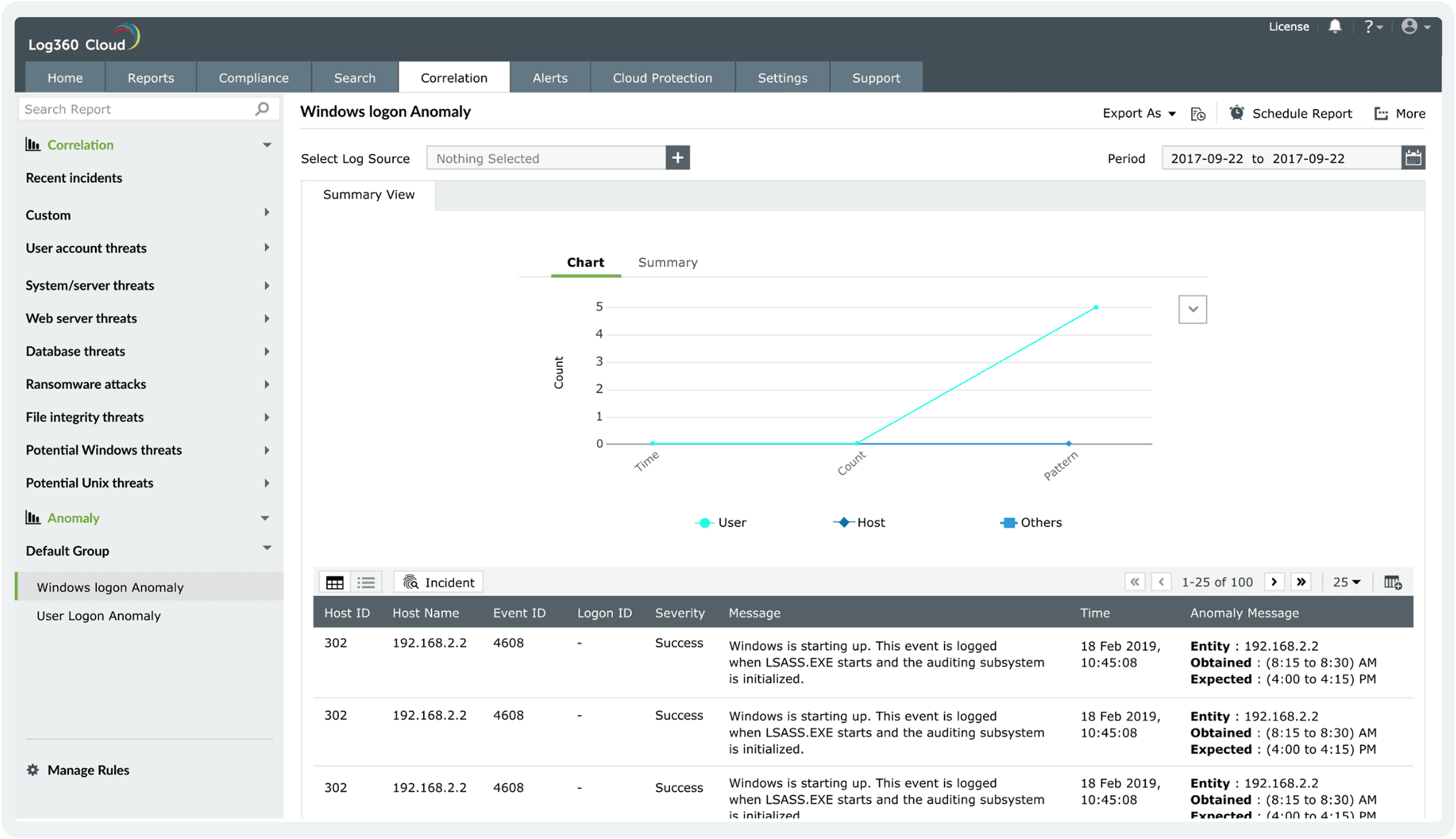
Proactively hunt for slow-moving and evasive attacks. ML-powered analytics continuously learns and adapts, identifying patterns that bypass traditional rule-based security
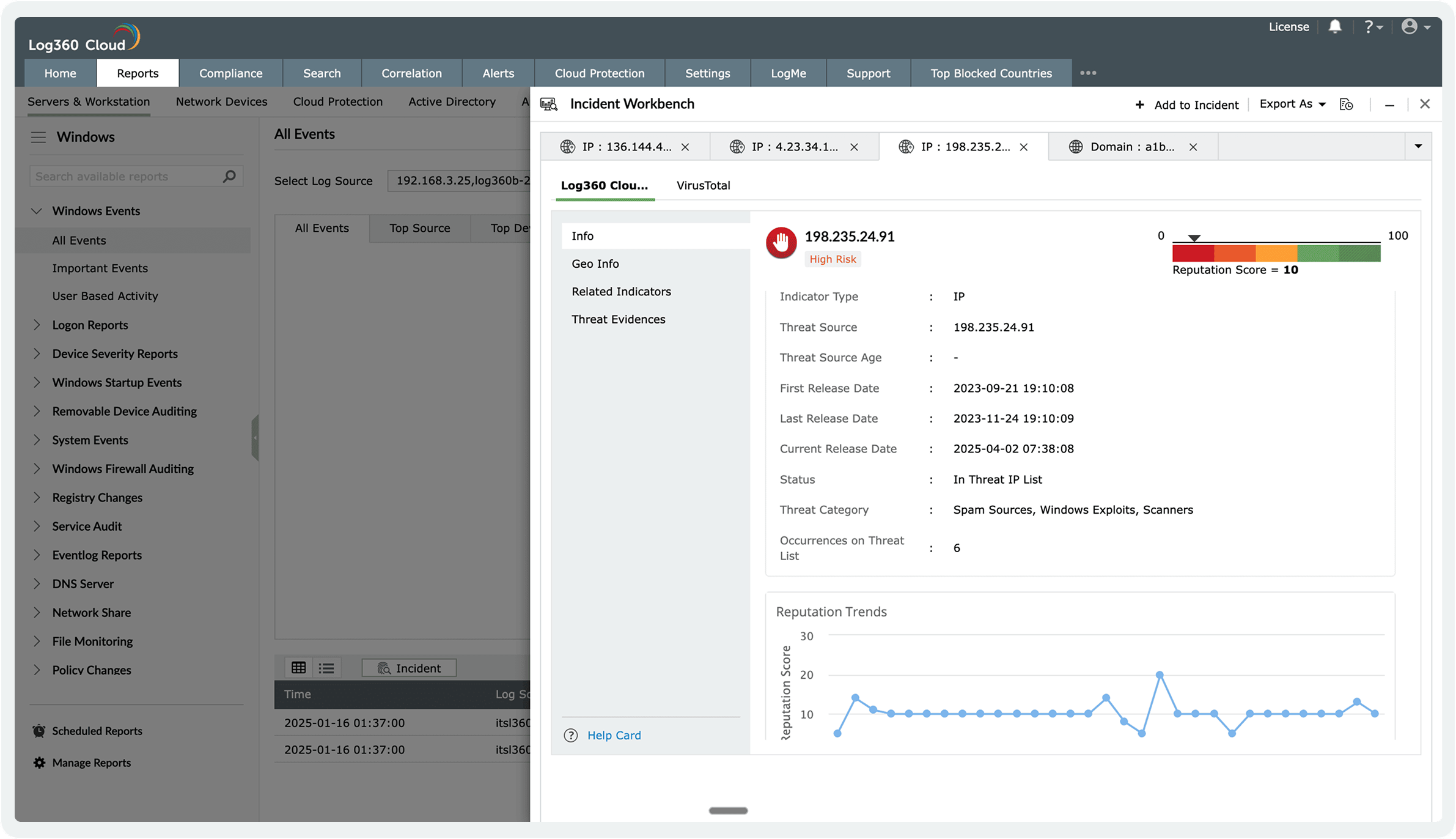
Accelerate incident response with enriched context. The workbench consolidates user, device, and threat intelligence, providing a comprehensive view for rapid investigation.
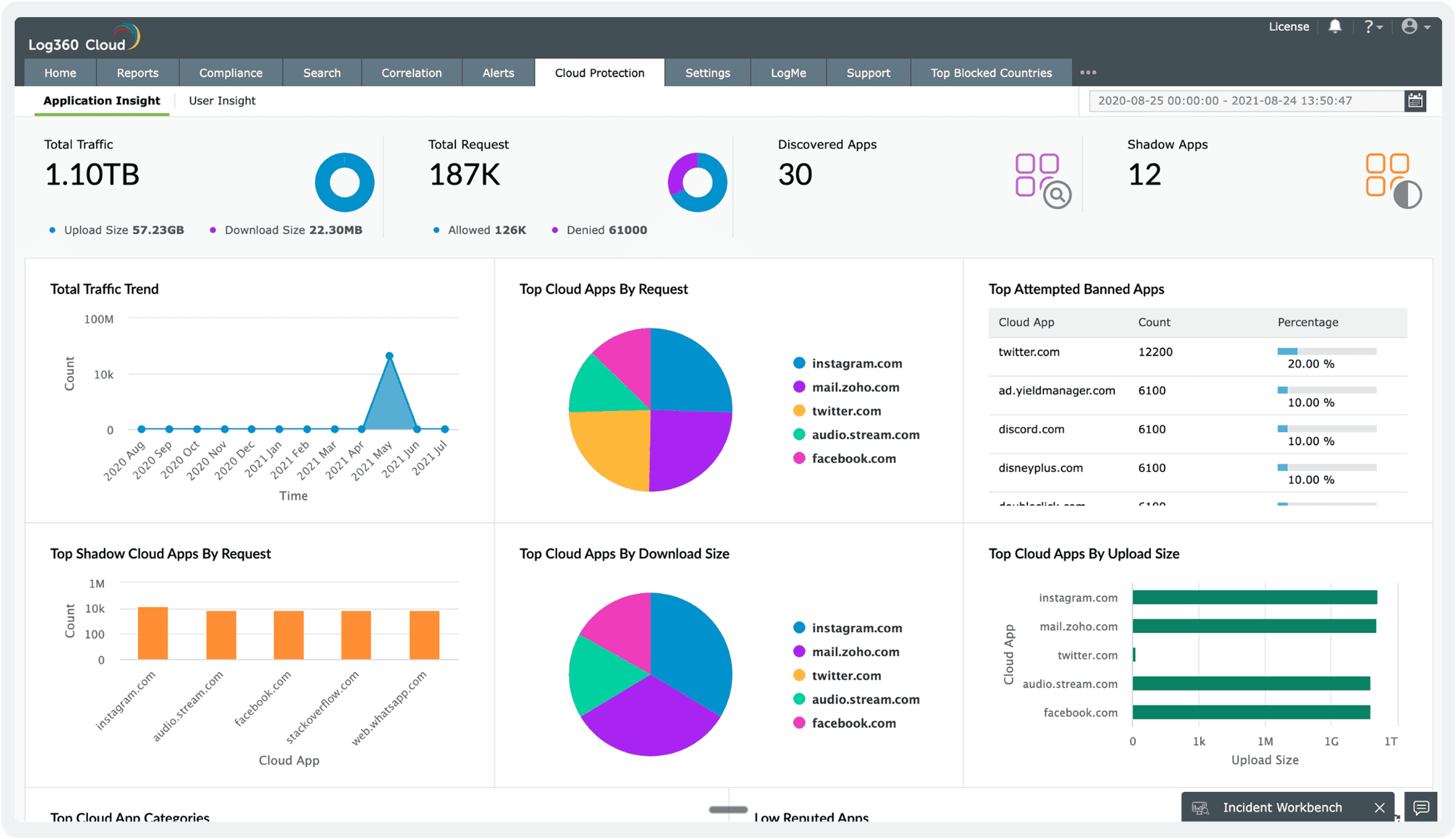
Track cloud app usage, detect shadow IT, and enforce security policies. Monitor both sanctioned and unsanctioned apps to safeguard sensitive data.

A cloud SIEM solution uses cloud technology to collect, analyze, and correlate security data from various sources within an organisation’s IT infrastructure. It provides real-time threat detection, incident response, and compliance management capabilities, all from the cloud. It uses cloud-native architecture for greater flexibility and ease of access when managing cybersecurity. It reduces the complexity of deploying a SIEM solution on-premises.
Experience the power of cloud-based log management with Log360 Cloud. Gain deep insights into security, access, system, and application logs across your network. With Log360 Cloud, you can:
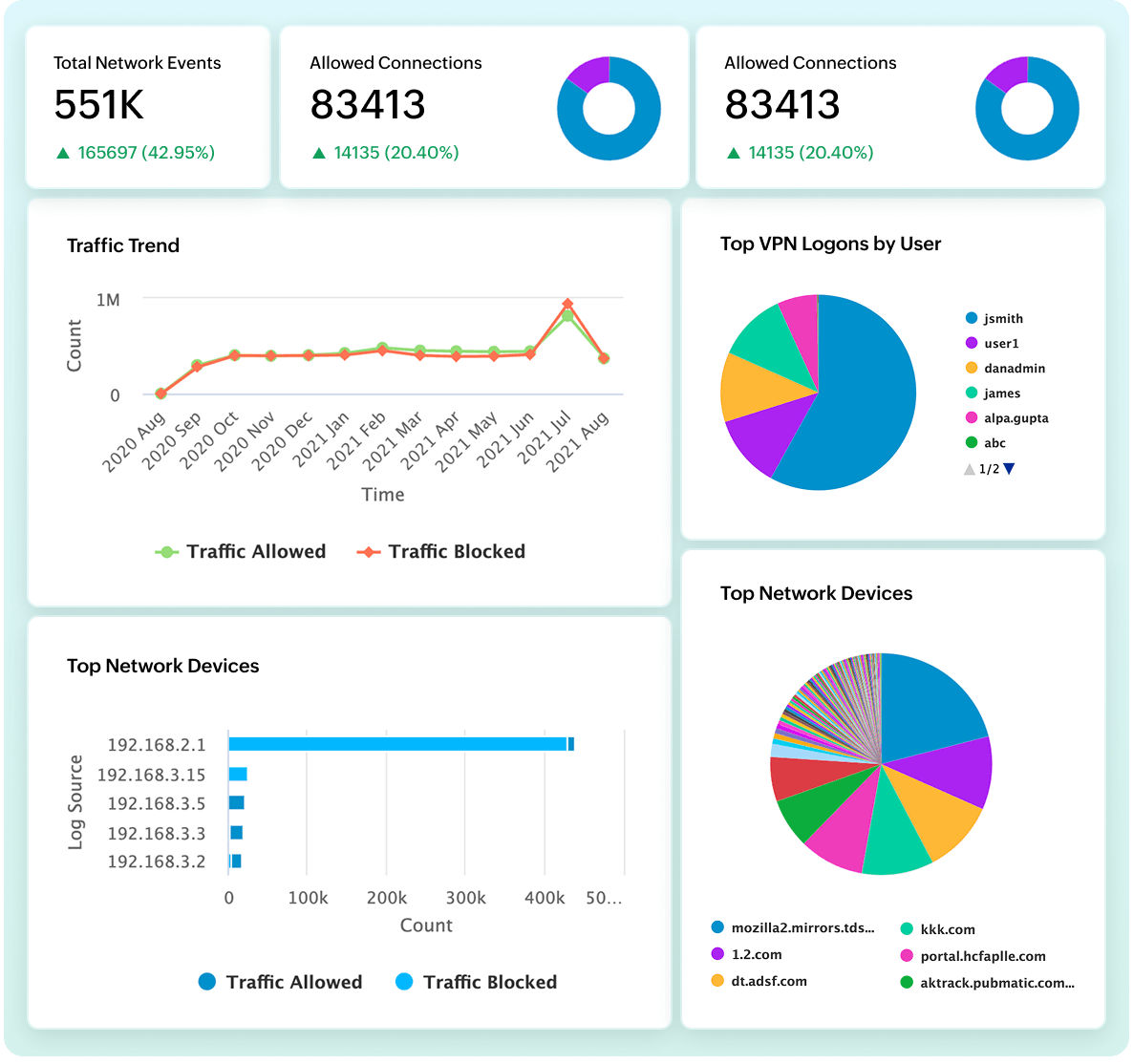
Cut through the noise with threat detection built for precision. Log360 Cloud delivers 2000+ MITRE-mapped detection rules covering correlation, anomaly, and threat intelligence, designed to reduce false positives and surface real threats. With Log360 Cloud, you can:
Go beyond traditional rule-based detection by identifying deviations in user and entity behavior patterns using anomaly rules. Detect potential insider threats like logon anomalies, compromised accounts, and data exfiltration attempts, before they escalate. With UEBA, you can:
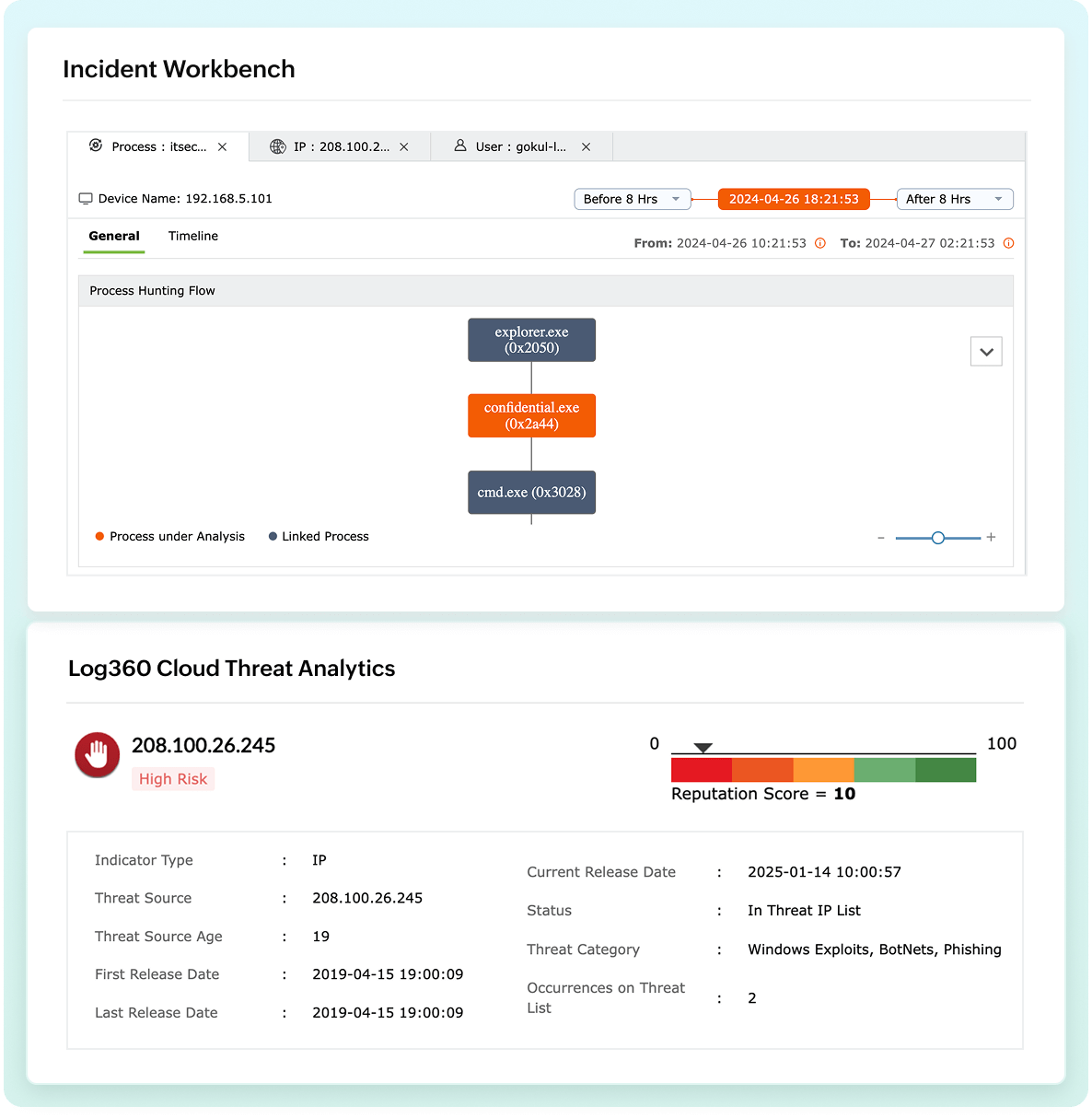
Empower your defenses with a threat intelligence database featuring over 600 million malicious URLs, domains, and IP addresses. With Log360 Cloud's integrated platform, you get:
Log360 Cloud streamlines compliance while enhancing your security posture. It provides:
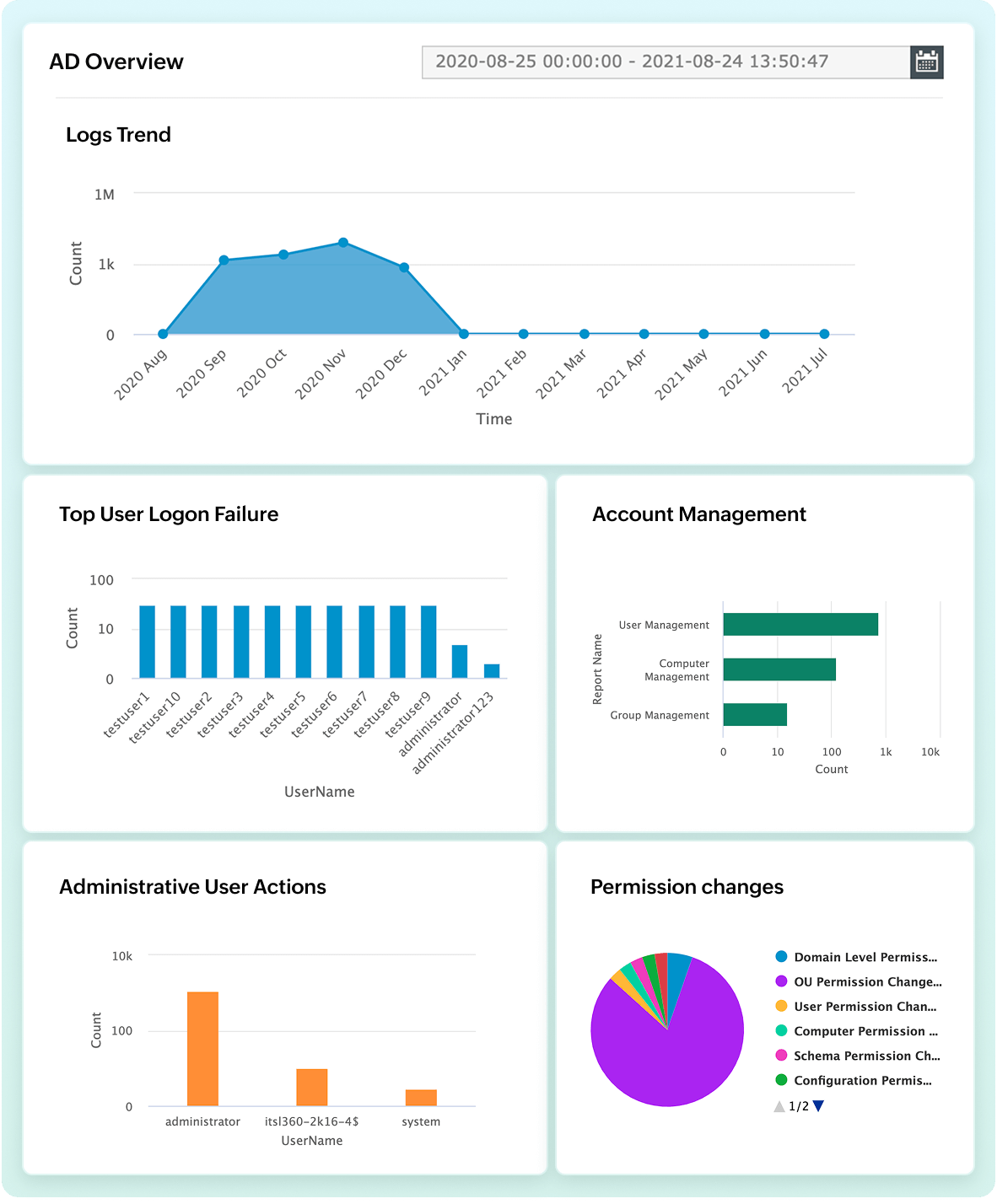
Protect identities during your cloud transition with Log360 Cloud. By monitoring Active Directory, it helps you:
Enhance your security services with Log360 Cloud MSSP edition. Deploy centralized log management, threat analysis and compliance management at scale.
Try for freeNo credit card required.
For more than 20,000 GB (20 TB) storage, please contact our sales team at sales@manageengine.com Get a personalized quote
Experience the transformative power of cloud-based log management with Log360 Cloud.
Know moreExperience a unified cybersecurity platform that combines advanced correlation techniques for threat detection, robust CASB features for cloud data security, and streamlined compliance through effective auditing and monitoring. Our cloud-native SIEM empowers organizations to achieve seamless security operations and protect their valuable assets.
Equip your security team for smarter threat response with Zia Insights in Log360 Cloud. This AI-driven feature delivers concise, contextual summaries of security events, maps threats to MITRE ATT&CK® techniques, and provides precise mitigation guidance, enabling faster, more confident incident investigation and response.
Learn moreGain complete control over your cloud environment with Log360 Cloud’s CASB. Monitor cloud application usage to identify unauthorized shadow IT, gain deep insights into user activity, and quickly detect potential threats. Integrating CASB with cloud-based SIEM helps uncover shadow applications and build actionable context around threat actor behavior.
Learn moreTake full control of your security with Log360's unified platform approach. Seamlessly integrate your security tools through Open APIs, visualize data exactly how you need it, and extend functionality with custom extensions to meet your evolving needs. Build a security ecosystem that works exactly how you want it to work.
Learn moreBenefit from intuitive log collection, analysis, search, and storage with Log360 Cloud. Perform high-speed searches and meet compliance retention requirements using a flexible pricing plan paired with adaptive storage options. This scalable, cost-effective solution eliminates the need for upfront hardware investments and ongoing infrastructure maintenance.
Learn moreSIEM-as-a-service (Security Information and Event Management) is a cloud-based solution that provides real-time analysis of security alerts generated by various network hardware and applications.
Key features include:
Cloud SIEM eliminates the need for organizations to maintain complex on-premises SIEM infrastructure, offering a more flexible and often more cost-effective security solution.
A security information and event management (SIEM) solution is a cybersecurity cornerstone, empowering security operations centers to rapidly detect, prioritize, and respond to threats. It ensures compliance, strengthens security posture, and streamlines incident response. By ingesting and analyzing logs and security telemetry from across the network, SIEM tools employ advanced techniques like correlation and behavior modeling to proactively identify and mitigate security risks.
Organizations should consider cloud SIEM over on-premises solutions in the following scenarios:
To decide between an on-premise and a cloud SIEM, read our detailed blog on the topic here.
Log360 Cloud employs multiple layers of security to protect your sensitive log data:
ManageEngine is a division of Zoho Corp.