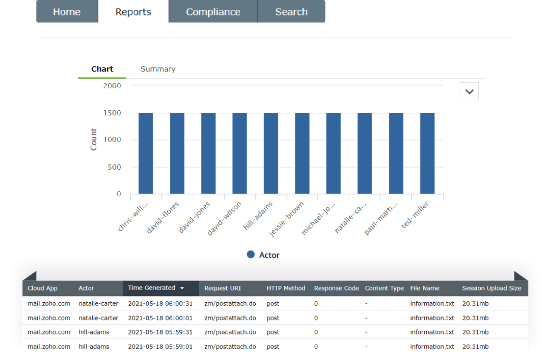
Consider that an employee constantly interacts with an adaptive learning AI model to speed up their tasks everyday.
If the AI tool used is a third-party tool, the tool will now have access to volumes of sensitive information. Either the tool could be breached to reveal sensitive data or the tool can malfunction and expose this newly learnt sensitive data to other users.
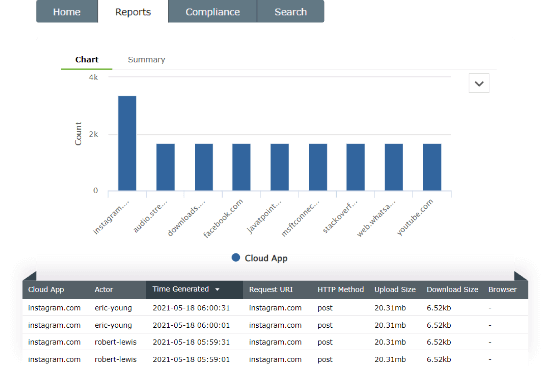
Cloud Access Security Broker (CASB) can help you detect the use of AI tools and other untrusted applications, called shadow applications.
If a shadow application is accessed in your network, you will receive real-time notifications and you can block the use of such applications in your network.
A CASB can also help you detect file uploads to sensitive cloud platforms and provide real-time notifications to help prevent the threat.