On this page
Casper couldn't believe his eyes. He'd just received an email from his inspiration, the CEO himself, who seemed to convey his trust in Casper by requesting that he transfer funds from a company account to another account immediately. The CEO claimed that the person in charge wasn't responding to his messages. Casper knew how important this acquisition was to the company and completed the transaction. It wasn't long before he received another email from the CEO which read, "Dear Staff, I regret to inform you that there has been an account breach. Kindly avoid responding to any of the messages you receive in my name".
But it was too late. Casper had been phished!
What just happened to Casper? Could he have been more cautious? How can we avoid being the next Casper? In this blog, we'll explore:
- What is spear phishing?
- How is it different from phishing?
- What are the different kinds of spear phishing attacks?
- How do you prevent them?
What is a spear phishing attack and how is it different from regular phishing?
Spear phishing is a type of targeted phishing attack, where the attacker sends personalized emails or messages to a target victim, with the aim of cracking into the network, and obtaining sensitive data. In this attack, bad actors spend time researching open source intelligence to collect information and understand their target.
Cybercriminals use a variety of techniques to make the attack a success, including:
- Trusted domains or compromised email addresses, that will help them get past traditional email security.
- Spoofing or masking a real email address, website, or even IP addresses.
- Social engineering tactics like creating urgency or a pretext, thus inducing pressure.
A phishing attack, on the other hand, is like fishing. The fisherman (attacker) throws a casting net (sends 'n' number of emails or messages to numerous people in an organization) and waits until a prey takes the bait. They might use phone calls too.
One might fall prey to a spear phishing attack by clicking on a deceptive link which initiates the downloading of a malicious attachment, or which directs the user to a counterfeit website that compromises security.
Spear phishing with links
A malicious link will be sent and the message attached to the email might either urge you to either click on it, or paste that URL into your search bar so that you are redirected to a spoofed website. This malicious website may request login credentials or contain socially engineered messages encouraging you to take an action or download files. These messages usually contain enticing offers, gift coupons, and competitor data.
Spear phishing with attachments
The attacker sends malicious attachments in email. When these attachments are downloaded, the software or malware program runs, detects vulnerabilities and exploits them. These attachments are usually in .docx; .pdf; .xls; or .zip formats, or sometimes in double extension formats (like .docx.exe) with names like customer invoice, or payment details.
Spear phishing via service
Here, instead of directly communicating with the target via email, attackers use a third party to create trust. For example, the bad actor might create a business account on social media, attempt to build a good customer relationship with the target, and then send personal emails with malicious links.
Types of spear phishing attacks
Though spear phishing with links, attachments, or via service are popularly called types of spear phishing, they are the variants of a spear phishing attack that involve where the spear phishing attack took place.
Let's discuss the types of spear phishing attacks.
Business Email Compromise (BEC)
As the name suggests, these type of attacks use emails to lure in the victim. Most of the time, the hacker poses as a trusted person and asks the target to share personal or sensitive information, or transfer some amount of money.
The five ways a BEC attack can be executed are:
- CEO fraud: The attack we described at the beginning of this blog is an example of CEO fraud. The culprit impersonates the CEO (they either hack or spoof the CEO's account), and urge the victim to give them their credentials, or make an immediate fund transfer.
- Data theft: The attackers target various individuals from departments to try and steal personally identifiable information of employees within the organization. This information can be further be used to carry out other attacks in the future.
- Account compromise: Attackers use malware to get unauthorized access to managers' accounts and use them to steal data or money.
- False invoice scheme: The attacker impersonates a supplier the company deals with and emails fake invoices that lure the target to a spoofed website.
- Impersonating an advocate: As the name suggests, the attackers either spoofs, hacks, or impersonates a trusted advisor, such as a lawyer or an accountant, and then emails fake invoices to the organization.
People fall prey to these kinds of attacks because the hackers' impersonations are spot on. The bad actors often conduct research using open sources that can reveal a lot about both the victim (Casper) and the target (the CEO), making it easier for them to craft compelling messages.
Brand Impersonation
Instead of using an individual's name and address, attackers send emails mimicking brands. For example, the cyberfraudster can use the same logo, fonts, designs, and colors as that of a popular brand in the email sent with malicious links or attachments.
Extortion
In this type of attack, the culprits use credentials from past data breaches to demand a ransom in exchange for the sensitive data they claim to have (although, in reality, they might not have any of it).
Conversation hijacking
The attackers manage to either place themselves in the middle of a business conversation, or initiate a conversation with vendors using the information they have collected over time.
Though it sounds like a man-in-the-middle attack, it is not the same. In man-in-the- middle attacks, the hacker silently manipulates or extracts the data that is required, whereas in conversation hijacking the hacker breaks the channel and takes over the communication. The attacker is not a third person in the channel, but rather enters the channel through the compromised account.
How does a spear phishing attack take place?
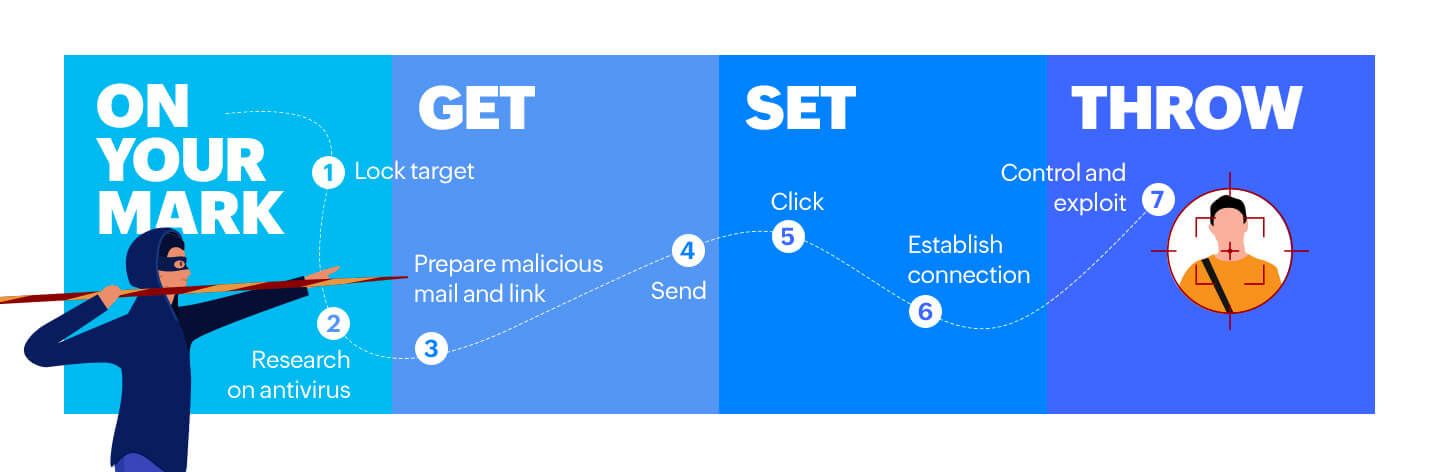
Let's understand this through an example. Z-gang is a hacker group that wants to obtain some sensitive documents from a financial institution. Here are the sequence of actions taken to launch the spear phishing attack.
-
Choose the target: With the help of open source platforms like social media, they come across Mr. K who, on his LinkedIn profile, mentions he lead a team during a major acquisition. Z-gang conducts target reconnaissance to gain a complete understanding of him: his background, personality, and responsibilities.
-
Dodging the antivirus: Email antivirus helps detect suspicious activity and block emails which have malicious attachments or links. Z-gang searches for open IT security jobs in the financial institution, and finds a job listing that reveals the antivirus as well as other security tools the organization uses. Z-gang now understands the vulnerabilities and then test sends the phishing email.
-
Evading egress filtering: This process controls outbound network traffic. Egress filters detect a malicious attachment because of the unusual payload in the network. So, hackers will encrypt the email with payloads such as reverse_tcp or reverse_http which help to establish a separate channel for communication, thus evading filters and firewalls.
-
Setting the bait: Z-gang's research revealed that Mr. K is a fan of Formula 1 and has been searching for tickets on the internet. To set the bait, the hackers create a webpage that poses as an F1 fan page that has a lot of followers, and sends an email with a malicious link in it. The message in the email creates a sense of pressure and calls for immediate action.
-
The eureka moment: Once Mr. K receives the link and clicks on it, the hacker receives a request on his server. Mr. K is redirected to the malicious website.
-
The attack: This website contains a code that runs on the victim's device, taking advantage of the vulnerabilities detected in his web browser or operating system. The malware gets installed and the payload is delivered. Once this is done, the hacker establishes a communication channel through which the compromised device is exploited and controlled.
How do we protect ourselves from a spear phishing attack?
At an individual level:
-
Be aware of the different social engineering red flags.
-
Limit sharing personal information online.
-
Keep your system security updated and enable MFA.
At an organizational level:
-
Educate your employees about attacks like these.
-
Red teams, often internal IT employees who pretend to be hackers, should conduct phishing simulations to identify vulnerable employees.
-
Have a SIEM tool in place that detects and alerts you of account compromises, unusual network traffic, and malware activities in real time.
-
Have policies such as Domain Keys Identified Mail, Sender Policy Framework, and Domain-based Message Authentication Reporting and Conformance enabled.
Contemplating which cybersecurity tool to bank on? Consult with one of our solution experts to see our resource in action and receive answers to your product questions by scheduling a free ManageEngine Log360 demo. We'll demonstrate how you can:
- Utilize Log360's Exchange Server audit reports to help you stay alert to unusual mailbox login attempts or permission changes.
- Match events to identify risk using Log360's rule-based correlation engine that finds suspicious event patterns in your network logs and notifies the security team immediately.
- Spot malicious intruders with Log360's ML-based user entity and behavior analytics (UEBA) capability. Efficiently perform user behavior profiling based on time, event pattern, and number of events triggered.
- Leverage the MITRE ATT&CK framework, integrated in Log360, to help you detect and provide comprehensive reports on the various techniques used by spear phishers.
Fear not because Log360 helps you detect even the sharpest spear.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement Zero Trust and the principles of least privilege with AD360.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Detect compromised credentials, reduce breach impact, and lower compliance risk exposure with Log360.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
