Did you know that the cause of 80% of hacking incidents is stolen or reused login information? Passwords, credit card numbers, and other sensitive data can be stolen with a successful SQL injection attack. In 2022, SQL injection accounted for 33% of global critical web application vulnerabilities.
SQL injection attacks are a common issue that SOCs face, and they're constantly on the hunt for ways to remediate them. Creating a secure code would prevent the introduction of a harmful code into an application. A lack of strict separation between user-provided (or external) input and program instructions (i.e., code) is the root cause of injection attacks. Therefore, a data snippet can easily be injected with a malicious code. Due to the absence of this separation, an application may run a malicious code created by an attacker.
In this blog, we will cover:
SQL injection (SQLi) is a popular attack method that uses malicious SQL code to manipulate backend databases and access data that was not meant to be displayed. Various information, including private customer information, user lists, or sensitive corporate data, may be included in this data.
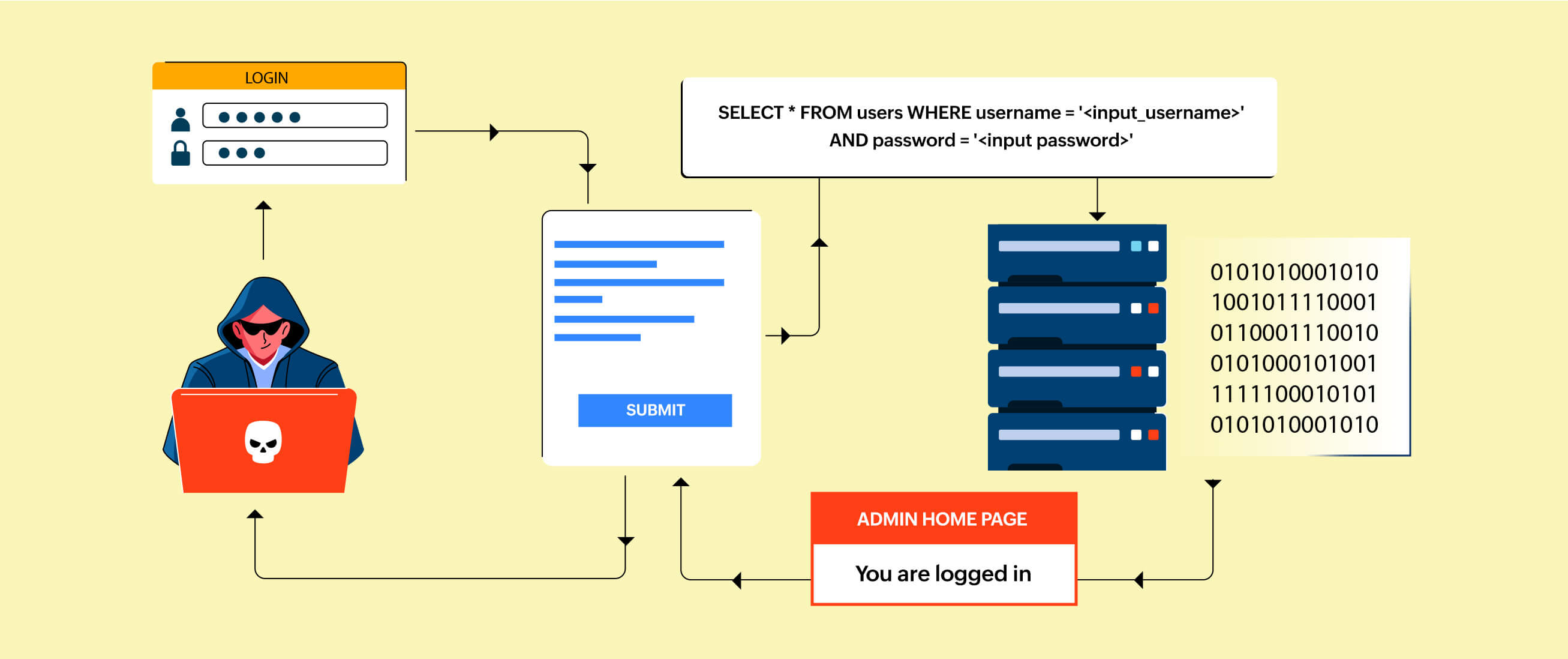 Figure 1: SQL Injection
Figure 1: SQL Injection
By successfully carrying out a SQLi, attackers can:
A SQL injection attack's objective is to change or steal data from a database that the application communicates with. These control characters provide access to or retrieve data components from a backend database server when used with standard SQL commands (such as SELECT, FROM, and DELETE).
Here is a representation of a typical SQL injection attack:
Attackers identify input fields on a web application that communicates with a database. Text boxes, search bars, login forms, and other user input devices that are used in database queries can all be used as these input fields.
The attackers must comprehend the structure of the SQL queries that are being utilized by the application in order to carry out a SQL injection. To collect this information, they may examine the HTML source code, intercept network traffic, or carry out other types of reconnaissance.
In the input field, the attacker inserts the malicious SQL code. This code's purpose is to alter the SQL query that the application is running. Typically, the injected code is included in the input as a parameter, such as a username or search term.
Attackers frequently employ SQL injection to bypass authentication safeguards. For instance, the attacker might be able to log in without using a legitimate username and password if the inserted code causes the query to always return true (for example, "1"="1").
The attackers will extract private information from a database. They can retrieve data they shouldn't have access to by inserting a SQL code that modifies the query's functionality. For instance, they can retrieve usernames, passwords, credit card numbers, or other private information.
SQL injection can be used to edit or delete data in the database, in addition to extracting it, depending on the permissions of the database user account used by the application.
Attackers often purposefully insert SQL code that results in errors. These errors could provide useful insights into the design of the database or aid attackers in improving their injection methods.
Attackers can conduct attacks using strategies like blind SQL injection in situations where error messages are not returned to them. This entails injecting code that compels the program to behave differently depending on whether certain criteria are true or untrue. Based on these conditional actions, the attacker can then draw conclusions about the target.
As a result, SQL injection attacks may result in serious consequences like data breaches, loss of data, and unauthorized access.
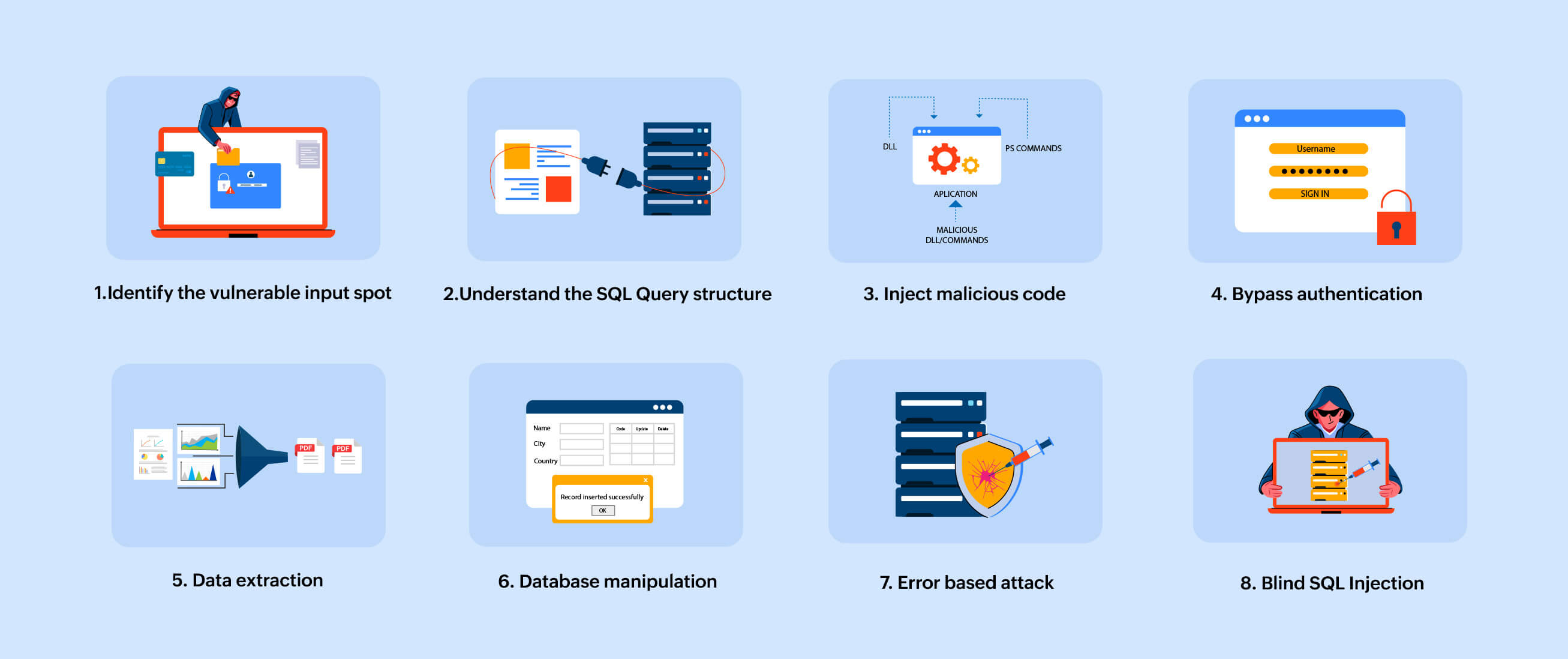 Figure 2: SQL Injection attack working flowchart
Figure 2: SQL Injection attack working flowchart
There are 3 types of SQL injection attacks:
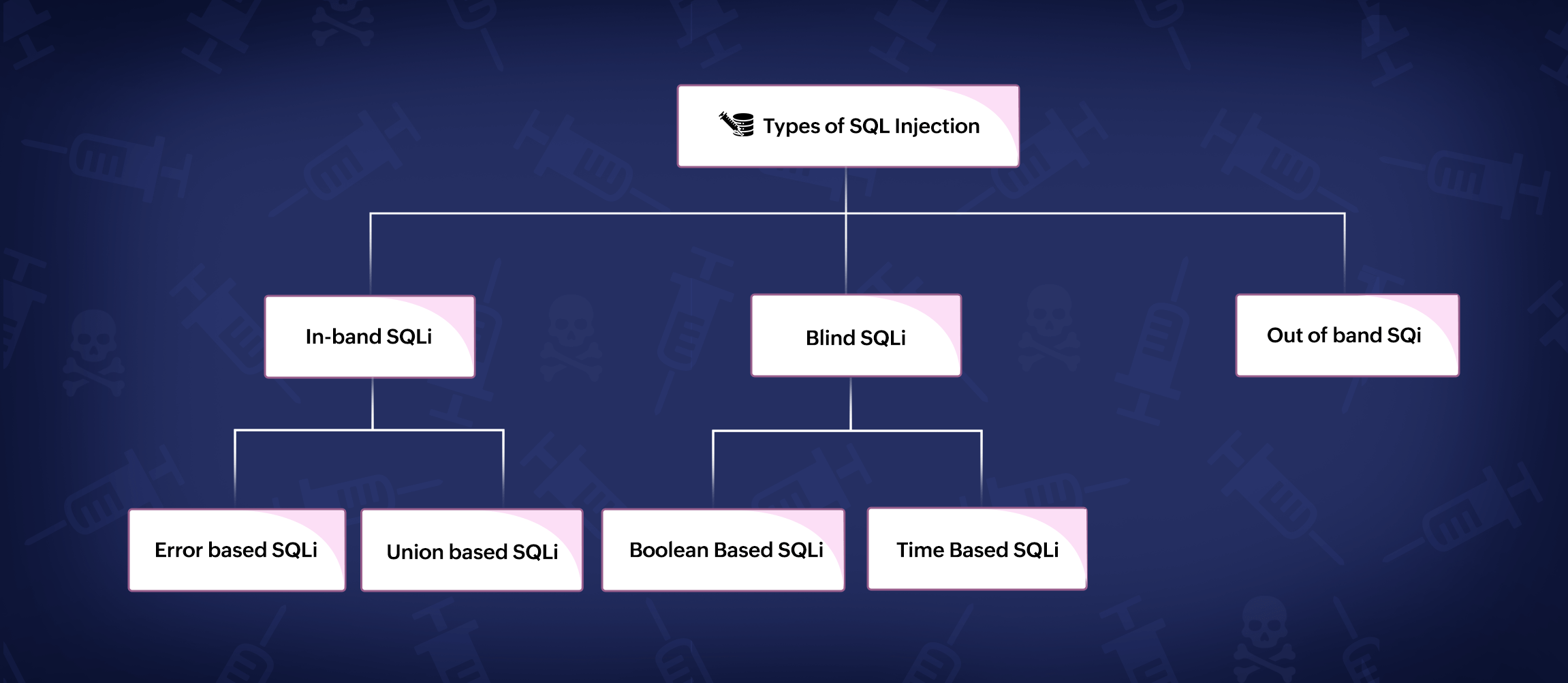 Figure 3: SQL Injection attack types
Figure 3: SQL Injection attack types
In-band SQL injection, sometimes referred to as Classic SQL injection or Error-based SQL injection, is one of the more prevalent kinds of SQL injection attacks. It takes place when a hacker accesses a database's data via the same channel that was utilized to begin the attack. In other words, the attacker can instantly observe the results of the SQL query they inserted through the application's responses or error messages.
Here's how in-band SQL injection typically works:
Here's an example of an in-band SQL injection:
SELECT * FROM users WHERE username = '<input_username>' AND password = '<input_password>'
' OR '1'='1' --
SELECT * FROM users WHERE username = ' ' OR '1'='1' --' AND password = '<input_password>'
Since the query always evaluates to true, the attacker can get in without knowing a legitimate username or password.
There are two primary categories of in-band SQL injection:
Error-based SQLi: Here, the result returned to the attacker is a database error string.
Let us consider an example:
SELECT * FROM users WHERE user-id = '<input_userid>'
1'
SELECT * FROM users WHERE user-id = ' 1' '
The database reports an error because of the doubled single quotation at the end of the query. The attacker might receive a similar message to the one below, if the web server is set up to show faults on screen:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax.
As a result, the attacker can concentrate on MySQL-specific assaults since the error message clearly indicates that the program uses a MySQL database.
Union-based SQLi: Here, the Union SQL clause is used by the attacker to get a result that blends valid data with sensitive data.
Let us consider an example:
SELECT * FROM users WHERE user-id = '<input_userid>'
1=1' UNION SELECT name, dcode--'
SELECT * FROM users WHERE user-id = ' '1'='1' ' UNION SELECT name, dcode--' '
As a result, the attacker would gain the information related to the name and dcode from the database.
When in-band approaches cannot be utilized because of security measures or when the attacker wishes to be concealed, blind SQL injection is frequently used. In a blind SQL injection attack, the results of the injected SQL query are not immediately visible to the attacker in the application's answers or error messages. Instead, the attacker uses the application's behavior to detect whether the SQL query was injected correctly or incorrectly, and then they take data from the database based on these true/false criteria.
Depending on how the application and database server behave, the attacker might be able to:
There are two primary categories of a blind SQL injection:
Boolean-based Blind SQL Injection: The attacker often employs conditional expressions (e.g., IF, CASE, AND, OR) to design SQL queries that indirectly retrieve information from the database. In this type of blind SQL injection, the attacker injects SQL code that depends on the application's response to true/false conditions.
Let us consider an example of a hospital's webpage. This displays the details about the patients once they enter the required credentials.
http://www.sthospitals.original/pid.php?id=22
SELECT code, case, ward, paymentdetails FROM patient_table WHERE id =22
http://www.sthospitals.original/pid.php?id=22 and 1=2
(Note: '' AND" operator will consider the results of both the statements. Even if one of the statements is false, the result will be taken as FALSE)
SELECT code, case, ward, paymentdetails FROM patient_table WHERE id =22 and 1=2
(Note: 1=2 is not true, thus the result of this condition will always be taken as FALSE)
This will cause the query to return FALSE and no details will be displayed.
http://www.sthospitals.original/pid.php?id=22 and 1=1
SELECT code, case, ward, paymentdetails FROM patient_table WHERE id =22 and 1=1
(Note: 1=1 is true, thus the result of this condition will always be taken as TRUE)
This returns TRUE, and the details about the patient with ID as 22 will be displayed. This is a clear indication that the page is vulnerable.
Time-based Blind SQL Injection: In this case, the attacker will inject SQL code that causes the database to perform a time-intensive operation. By measuring the time it takes for a response to arrive, the attacker can infer whether the injected condition is TRUE or FALSE.
Based on the previous example, first, the attacker would find out the actual response time of the web server. Then, they would issue the following request with a "sleep" operation:
http://www.sthospitals.original/pid.php?id=22 and if(1=1, sleep(10))
(Note: SLEEP pauses the MySQL process for a given duration)
The web application is identified to be vulnerable if the response is delayed by 10 seconds.
In out-of-band SQL injection attacks, the attacker uses the vulnerable application to trigger actions that send data to a location they control. This data transfer can happen through various means such as DNS requests, HTTP requests, or other network protocols.
Here is an example of out-of-band SQL injection attacks:
DNS Exfiltration: In this instance, the attacker inserts malicious SQL code that, when the application executes it, causes the database server to make DNS requests to a domain and causes the attacker to gain control of the domain. These DNS queries encrypt the data stolen from the database and share information with the attacker to recreate the database.
user_input = get_user_input()
query="SELECT*FROM database WHERE name = "'+user_input+'";"
execute_query(query)
' UNION SELECT DNS_QUERY(LOGS)FROM DUAL--
As a result, the attacker will get the data related to the logs that is available in the particular domain.
The attacker can now inspect their DNS server logs to extract the data that was exfiltrated.
We can clearly understand that to detect and mitigate a SQLi attack, security analysts need a comprehensive network security tool that analyzes and correlates log data from your web servers and databases. With the help of a SIEM tool like ManageEngine Log360 you can,
If you want to protect your organization from such attacks, sign up for a personalized demo of ManageEngine Log360, a unified SIEM solution with data security and cloud security capabilities.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.