In recent times, supply chain attacks have become commonplace. With increasing software dependencies, threat actors have shifted their focus from the downstream chain affecting end users alone to the upstream chain affecting vendors, customers, and end users altogether. Reports augment this fact, with 12% of organizations identifying a software supply chain attack as the source of a data breach.
In the first part of this three-part blog series, let's embark on our journey by comprehending the basics of supply chain attacks. This blog answers the following:
In typical business terms, a supply chain refers to a chain of activities encompassing each stage of value addition. Also known as a value chain, the process starts from procuring raw materials from suppliers and extends to the delivery of end products to the consumer. In between procurement and delivery lies a series of stages including manufacturing, packaging, warehousing, and transporting, which together constitute a supply chain. This interpretation of a business supply chain is analogous to a software supply chain.
In similar ways, a software supply chain involves the following components of value addition:
The above components add value to the software in one stage or the other during product development. All these can be entrapped in a software bill of materials, which is a tool to track all your resources during product development.
A single weak link is all it takes to open a backdoor for attackers to crawl into your network. In simple terms, a supply chain attack is a type of cyberattack executed by threat actors where they enter an organization's network by exploiting vulnerabilities in the software supply chain. It also provides the threat actor with an extended attack surface, exposing the various avenues for further attacks. A supply chain attack is the starting point of a chain of cyberattacks, making it one of the most dangerous forms of next-gen cyberattacks.
Let's understand this better with an attack scenario.
Dexter Inc. is a gaming software development firm. Looney Codes is a platform provider for software development. Dexter and Looney have been business partners for quite some time. All Dexter games are developed on Looney's platform, which makes Looney one of the major dependencies in Dexter's supply chain. One day, the following happened:
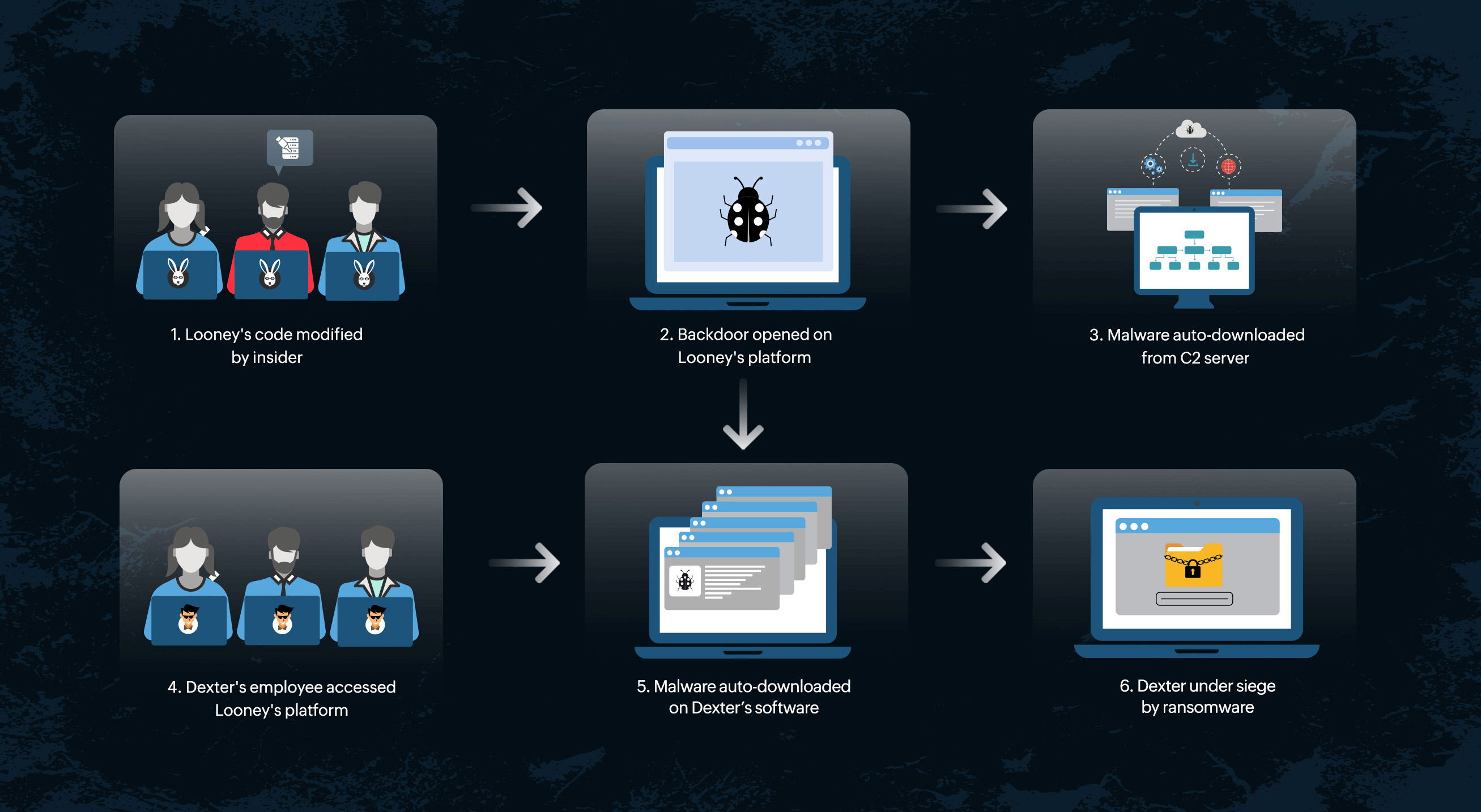 Figure 1. Supply chain attack
Figure 1. Supply chain attack
From the above attack scenario, it is obvious that one weak link in the supply chain is all it takes to fall prey to massive attacks like ransomware attacks.
Supply chain attacks originate from various sources that can be broadly classified under three main categories. They are as follows:
Commercial software vendors and external business partners are potential targets for adversaries who cannot infiltrate security-conscious firms. By installing malicious code into third-party software, attackers gain easy access to customers' networks and access internal data. For instance, organizations depend on penetration testing tools from security solution providers for security testing, and these tools themselves can be used as vectors of malware to sabotage the security of the organization. With the predominance of third-party software in supply chain attacks, these attacks have also been termed as third-party attacks.
Not all software is written from scratch. Most businesses rely on open-source software to develop their proprietary code. GitHub, a popular open-source software development platform, has reported that more than 90% of Fortune 100 companies use its platform to build their software. These open-source communities thereby provide free access to all users, which include potential adversaries. This provides threat actors easy access to introduce malicious scripts and create vulnerabilities in the existing open-source software. When legitimate users deploy such tampered-with source codes in their scripts, the infection spreads to their software and compromises vulnerable resources in their network.
Some countries sanction the deployment of malicious components into legitimate vendor software purchased by other countries. This type of supply chain attack serves as a means of cyber terrorism, causing a great threat to the victim country. In 2019, the United States (US) government was subjected to Chinese infiltration into a state-critical network through compromised Chinese electronics. To counteract the incident, the US government enacted the Microchips Act of 2019.
Take this quick poll to find out the most vulnerable component of a software supply chain.
Which of the following do you think is the most vulnerable component of
your software supply chain?
Supply chain attacks can further be classified into different types, which we will be covering in the second part of this blog series.
Stay tuned for the upcoming blogs to learn more about the types of supply chain attacks, real-time supply chain attack use cases, and the measures you can take to detect and prevent supply chain attacks.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.